TigerConnect has released its 2019 State of Healthcare Communications Report, which shows that continuing reliance on decades-old, inefficient communications technology is negatively impacting patients and is contributing to the increasing cost of healthcare provision.
For the report, TigerConnect surveyed more than 2,000 patients and 200 healthcare employees to assess the current state of communications in healthcare and gain insights into areas where communication inefficiencies are causing problems.
The responses clearly show that communication in healthcare is broken. 52% of healthcare organizations are experiencing communication disconnects that impact patients on a daily basis or several times a week. Those communication inefficiencies are proving frustrating for healthcare employees and patients alike.
The report reveals most hospitals are still heavily reliant on communications technology from the 1970s. 89% of hospitals still use faxes and 39% are still using pagers in some departments, roles, or even across the entire organization. The world may have moved on, but healthcare hasn’t, even though healthcare is the industry that stands to benefit most from the adoption of mobile technology.
The HHS’ Centers for Medicaid and Medicare Services (CMS) is pushing for fax machines to be eliminated by the end of 2020 and for healthcare organizations to instead use more secure, reliable, and efficient communications methods. Given the extensive use of fax machines, that target may be difficult to achieve.
“Adoption of modern communication solutions has occurred in every other industry but healthcare,” said Brad Brooks, chief executive officer and co-founder of TigerConnect. “Despite the fact that quality healthcare is vital to the well-being and functioning of a society, the shocking lack of communication innovation comes at a steep price, resulting in chronic delays, increased operational costs that are often passed down to the public, preventable medical errors, physician burnout, and in the worst cases, can even lead to death.”
The cost of communication inefficiencies in healthcare is considerable. According to NCBI, a 500-bed hospital loses more than $4 million each year as a result of communication inefficiencies and communication errors are the root cause of 70% of all medical error deaths.
The communication problems are certainly felt by healthcare employees, who waste valuable time battling with inefficient systems. The report reveals 55% of healthcare organizations believe the healthcare industry is behind the times in terms of communication technology compared to other consumer industries.
One of the main issues faced by healthcare professionals is not being able to get in touch with members of the care team when they need to. 39% of healthcare professionals said it was difficult or very difficult communicating with one or more groups of care team members.
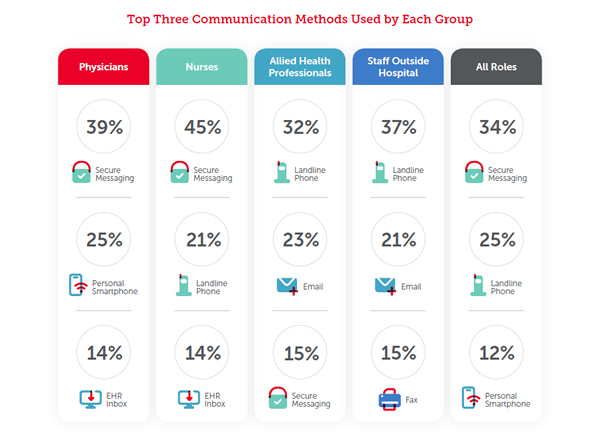
Fast communication is critical for providing high quality care to patients and improvements are being made, albeit slowly. Secure messaging is now the primary method of communication overall for nurses (45%) and physicians (39%), although landlines are the main form of communication for allied health professionals (32%) and staff outside hospitals (37%), even though secure messaging platforms can be used by all groups in all locations.
Even though there is an increasing mobile workforce in healthcare, healthcare organizations are still heavily reliant on landlines. Landlines are still the top method of communication when secure messaging is not available. Landlines are also used 25% of the time at organizations that have implemented secure messaging.
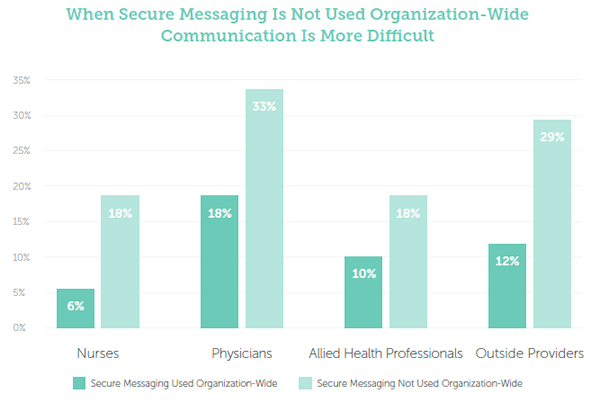
Healthcare organizations that have taken steps to improve communication and have implemented secure messaging platforms are failing to get the full benefits of the technology. All too often, secure messaging technology is implemented in silos, with different groups using different methods and tools to communicate with each other. When secure messaging is not used, such as when the platform is only used by certain roles, communication is much more difficult.
The communications problems are also felt by patients. Nearly three quarters (74%) of surveyed patients who had spent at least some time in hospital in the past two years, either receiving treatment or visiting an immediate family member, said they were frustrated by inefficient processes.
The most common complaints were slow discharge/transfer times (31%), ED time with doctors (22%), long waiting room times (22%), the ability to communicate with a doctor (22%), and the length of time it takes to get lab test results back (15%). Many of these issues could be eased through improved communication between members of the care team. The survey also revealed hospital staff tend to underestimate the level of frustration that patients experience.
Communication problems play a large part in the bottlenecks that often occur in healthcare. Communication problems were cited as causing delayed discharges (50%), consult delays (40%), long ED wait times (38%), transport delays (33%) and slow inter-facility transfers (30%). There is a 50% greater chance of daily communication disconnects negatively impacting patients when secure messaging is not used.
Hospitals that communicate with patients by SMS/text or messaging apps are far more likely to rate their communication methods as effective or extremely effective. 75% of hospitals that use text/SMS and 73% that use messaging apps rate communication with patients as effective or very effective, compared to 62% that primarily use the telephone and 53% whose primary method of communicating with patients is patient portals. The survey also showed that only 20% of patients want to communicate via patient portals.
It has been established that secure messaging can improve communication and the quality of healthcare delivery, but healthcare communication is often not a strategic priority. 69% of surveyed healthcare professionals that are not using a secure messaging platform said this was due to budget constraints, 38% said money was spent on other IT priorities, and 34% cited concerns about patient data security, even though secure messaging platforms offer afar greater security than legacy communications systems.
TigerConnect has made several recommendations on how communication in healthcare needs to be improved.
- Prioritize communication as a strategy
- Focus on improving communication to ease major bottlenecks
- Integrate communication platforms with EHRs to get the greatest value
- Standardize communication across the entire organization
- Include clinical leadership in solution design
- Stop using patient portals to communicate with patients and start using patient messaging in the overall communication strategy.
The survey provides valuable insights into the state of communication in healthcare and clearly shows where improvements need to be made. The full TigerConnect 2019 State of Communication in Healthcare Report is available free of charge on this link (registration required).
The post TigerConnect Survey Finds 89% of Healthcare Providers Still Use Fax Machines and 39% are Still Using Pagers appeared first on HIPAA Journal.