The penalties for HIPAA violations include civil monetary penalties ranging from $141 to $2,134,831 per violation, depending on the level of culpability. Criminal penalties can also be imposed for intentional HIPAA violations, leading to fines and potential imprisonment.
In addition to financial penalties, corrective action plans may be required to address compliance deficiencies. State attorneys general can also bring civil actions, resulting in monetary damages. Plus, covered entities may be required to adopt a corrective action plan to bring policies and procedures up to the standards demanded by HIPAA.
 In this article, we provide a detailed explanation of penalties for HIPAA violations.
In this article, we provide a detailed explanation of penalties for HIPAA violations.
You can also use the article in conjunction with our free HIPAA Violations Checklist to understand what is required to ensure full compliance. Please use the form on this page to arrange for your copy.
HIPAA, PHI & HITECH
The Health Insurance Portability and Accountability Act of 1996 placed a number of requirements on HIPAA-covered entities to safeguard the Protected Health Information (PHI) of patients, and to strictly control when PHI can be divulged, and to whom.
Since the Enforcement Final Rule of 2006, OCR has had the power to issue financial penalties (and/or corrective action plans) to HIPAA-covered entities that fail to comply with HIPAA Rules.
Financial penalties for HIPAA violations were updated by the HIPAA Omnibus Rule, which introduced charges in line with the Health Information Technology for Economic and Clinical Health Act (HITECH). The Omnibus Rule took effect on March 26, 2013.
Since the introduction of the Omnibus Rule, the new penalties for HIPAA violations apply to healthcare providers, health plans, healthcare clearinghouses, and all other covered entities, as well as to business associates (BAs) of covered entities that are found to have violated HIPAA Rules.
Financial penalties are intended to act as a deterrent to prevent the violation of HIPAA laws, while also ensuring covered entities are held accountable for their actions – or lack of them – when it comes to protecting the privacy of patients and the confidentiality of health data and providing patients with access to their health records on request.
The penalty structure for a violation of HIPAA laws is tiered, based on the knowledge a covered entity had of the violation. The OCR sets the penalty based on a number of “general factors” and the seriousness of the HIPAA violation.
Ignorance of HIPAA Rules is no excuse for failing to comply with HIPAA Rules. It is the responsibility of each covered entity to ensure that HIPAA Rules are understood and followed. In cases when a covered entity is discovered to have committed a willful violation of HIPAA laws, the maximum fines may apply.
What Constitutes a HIPAA Violation?
There is much talk of HIPAA violations in the media, but what constitutes a HIPAA violation? A HIPAA violation is when a HIPAA-covered entity or a business associate fails to comply with one or more of the provisions of the HIPAA Rules, most commonly, the HIPAA Privacy, Security, or Breach Notification Rules.
A violation may be deliberate or unintentional. An example of an unintentional HIPAA violation is when too much PHI is disclosed and the minimum necessary information standard is violated. When PHI is disclosed, it must be limited to the minimum necessary information to achieve the purpose for which it is disclosed. Financial penalties for HIPAA violations can be issued for unintentional HIPAA violations, although the penalties will be at a lower rate for willful violations of HIPAA Rules.
An example of a deliberate violation is unnecessarily delaying the issuing of breach notification letters to patients and exceeding the maximum timeframe of 60 days following the discovery of a breach to issue notifications – A violation of the HIPAA Breach Notification Rule.
Many HIPAA violations are the result of negligence, such as the failure to perform an organization-wide risk analysis. Financial penalties for HIPAA violations have frequently been issued for risk analysis failures as it is one of the most commonly identified HIPAA violations. The HHS’ Office for Civil Rights has launched an enforcement initiative targeting noncompliance with the risk analysis requirement of the HIPAA Security Rule.
Penalties for HIPAA violations can potentially be issued for all HIPAA violations, although OCR typically resolves most cases through voluntary HIPAA compliance, issuing technical guidance, or accepting a covered entity or business associate’s plan to address the violations and change policies and procedures to prevent future violations from occurring. Financial penalties for HIPAA violations are reserved for the most serious violations of HIPAA Rules, when OCR targets a specific violation such as the HIPAA Right of Access, or wants to “send a message” to the industry about specific violation types.
What Happens if You Violate HIPAA? – HIPAA Violation Classifications
What happens if you violate HIPAA? That depends on the severity of the violation. OCR prefers to resolve HIPAA violations using non-punitive measures, such as voluntary compliance or issuing technical guidance to help covered entities address areas of non-compliance. However, if the violations are serious, have been allowed to persist for a long time, or if there are multiple areas of noncompliance, financial penalties may be appropriate.
The four categories used for the penalty structure are as follows:
- Tier 1: A violation that the covered entity was unaware of and could not have realistically avoided, had a reasonable amount of care been taken to abide by HIPAA Rules
- Tier 2: A violation that the covered entity should have been aware of but could not have avoided even with a reasonable amount of care. (but falling short of willful neglect of HIPAA Rules)
- Tier 3: A violation suffered as a direct result of “willful neglect” of HIPAA Rules, in cases where an attempt has been made to correct the violation
- Tier 4: A violation of HIPAA Rules constituting willful neglect, where no attempt has been made to correct the violation within 30 days
In the case of unknown violations, where the covered entity could not have been expected to avoid a data breach, it may seem unreasonable for a covered entity to be issued with a fine. OCR appreciates this and has the discretion to waive a financial penalty. The penalty cannot be waived if the violation involves willful neglect of the Privacy, Security, and Breach Notification Rules.
HIPAA Violation Penalty Structure
Each category of violation carries a separate HIPAA penalty. It is up to OCR to determine a financial penalty within the appropriate range. OCR considers a number of factors when determining penalties, such as the length of time a violation was allowed to persist, the number of people affected, and the nature of the data exposed. An organization’s willingness to assist with an OCR investigation is also taken into account. The general factors that can affect the amount of the financial penalty also include prior history, the organization’s financial condition, and the level of harm caused by the violation.
- Tier 1: Minimum fine of $100 per violation up to $50,000
- Tier 2: Minimum fine of $1,000 per violation up to $50,000
- Tier 3: Minimum fine of $10,000 per violation up to $50,000
- Tier 4: Minimum fine of $50,000 per violation up to $1,500,000
The above fines for HIPAA violations are those stipulated by the HITECH Act, and those figures are adjusted annually to factor in cost-of-living increases to ensure that the civil monetary penalties continue to serve as an effective deterrent. Under the Federal Civil Penalties Inflation Adjustment Act of 1990, later amended by the Federal Civil Penalties Inflation Adjustment Act Improvements Act of 2015, cost-of-living increases are stipulated by the Office of Management and Budget (OMB). On January 15 each year, the multiplier set by OMB should be applied by all federal agencies to their CMPs. In 2024, the HHS published its annual increases in the Federal Register on August 8, which is also the effective date for the updated civil monetary penalties. The inflation multiplier for 2025 has been set by OMB as 1.02598.
All civil monetary penalties assessed by OCR on or after August 8, 2024, will use the 2024 rates for HIPAA violations as detailed in the table below. These will be applied to all violations that occurred on or after November 2, 2015. These penalty amounts will be used until the HHS publishes a final rule in the Federal Register that applies the 2025 inflation adjustment.
Current HIPAA Penalty Structure
| Penalty Tier |
Culpability |
Minimum Penalty per Violation – Inflation
Adjusted |
Max Penalty per Violation – Inflation Adjusted |
Maximum Penalty Per Year (cap) – Inflation Adjusted |
| Tier 1 |
Lack of Knowledge |
$141 |
$71,162 |
$2,134,831 |
| Tier 2 |
Reasonable Cause |
$1,424 |
$71,162 |
$2,134,831 |
| Tier 3 |
Willful Neglect |
$14,232 |
$71,162 |
$2,134,831 |
| Tier 4 |
Willful Neglect (not corrected within 30 days) |
$71,162 |
$2,134,831 |
$2,134,831 |
Penalties for pre-February 18, 2009, violations of the HIPAA administrative simplification provisions will be applied at a rate of $193 per violation with a calendar year cap of $48,586 for violations of an identical provision.
OCR 2019 Notice of Enforcement Discretion Applies New Maximum Annual Penalties for HIPAA Violations
The above table of penalties is still officially in force; however, in 2019, the HHS reviewed the language of the HITECH Act with respect to the required increases for HIPAA violations and determined that the language of the HITECH Act had been misinterpreted and that it did not call for the same maximum annual penalty cap to be applied equally across all four penalty tiers. Instead, the HHS determined that the maximum annual penalty of $1.5 million ($2,134,831 in 2024) should only apply to the most serious Tier 4 violation category.
Rather than issue further rulemaking, which would see the new penalty structure changed in the Federal Register, the HHS announced that OCR would be exercising enforcement discretion and would be applying a different penalty structure where each tier had a separate annual penalty cap. A Notice of Enforcement Discretion (NED) was issued in April 2019 which states that OCR will apply penalties according to the table below. These have been adjusted by The HIPAA Journal based on the annual inflation multipliers set by OMB.
The penalty structure OCR is using is not legally binding, and further rulemaking is required before its new interpretation is set in stone. The NED is still in effect and will remain so indefinitely. Since the NED only applied caps to the annual penalties, this creates an anomaly, as the maximum penalty per violation in Tier 1 is still technically $71,162 which is higher than the annual penalty cap. Due to this anomaly, the annual penalty cap is shown as the maximum penalty per violation in the table below for tier 1.
| Penalty Tier |
Culpability |
Minimum Penalty per Violation |
Maximum Penalty per Violation |
Annual Penalty Cap |
| Tier 1 |
Lack of Knowledge |
$141 |
$35,581 |
$35,581 |
| Tier 2 |
Reasonable Cause |
$1,424 |
$71,162 |
$142,355 |
| Tier 3 |
Willful Neglect |
$14,232 |
$71,162 |
$355,808 |
| Tier 4 |
Willful neglect (not corrected within 30 days |
$71,162 |
$2,134,831 |
$2,134,831 |
*This table was last updated on August 10, 2024, and includes the inflationary updates for 2024.
Attorneys General Can Also Issue HIPAA Violation Fines
Since the introduction of the HITECH Act (Section 13410(e) (1)) in February 2009, state attorneys general have the authority to hold HIPAA-covered entities accountable for the unauthorized use or disclosure of PHI of state residents and can file civil actions with the federal district courts. HIPAA violation fines can be issued up to a maximum level of $25,000 per violation category, per calendar year. The minimum fine applicable is $100 per violation. As with OCR penalties, these too are adjusted annually for inflation.
A covered entity suffering a data breach affecting residents in multiple states may be ordered to pay HIPAA violation fines to several different attorneys general. Attorneys General HIPAA penalties are independent of those issued by OCR. Relatively few states have taken action against HIPAA-regulated entities for violations of the HIPAA Rules – California, Connecticut, Indiana, Massachusetts, Minnesota, New Jersey, New York, Oregon, Utah, Pennsylvania, Vermont, and the District of Columbia – although all have participated in at least one multi-state action.
Multi-state actions are now common, where Attorneys General in multiple states pool their resources and share any settlements or civil monetary penalties. These are common in large-scale data breaches that have affected individuals across the entire United States, such as the data breach suffered by Blackbaud and the healthcare clearinghouse Inmediata. While only a small number of states have exercised their authority to issue fines for HIPAA violations, that does not mean HIPAA violations are going unpunished. Many states have pursued financial penalties for equivalent violations of state laws.
Can HIPAA Violations be Criminal?
When a HIPAA-covered entity or business associate violates HIPAA Rules, civil penalties can be imposed. When healthcare professionals violate HIPAA, it is usually their employer that receives the penalty, but not always. If healthcare professionals knowingly obtain or use protected health information for reasons that are not permitted by the HIPAA Privacy Rule, they may be found to be criminally liable for the HIPAA violation under the criminal enforcement provision of the Social Security Act.
Criminal HIPAA violations are prosecuted by the Department of Justice, which is increasingly taking action against individuals who have knowingly violated HIPAA Rules. There have been several cases that have resulted in substantial fines and prison sentences. Criminal HIPAA violations include theft of patient information for financial gain and wrongful disclosures with intent to cause harm. A lack of understanding of HIPAA requirements may not be a valid defense. When an individual “knowingly” violates HIPAA, knowingly means that they have some knowledge of the facts that constitute the offense, not that they definitely know that they are violating HIPAA Rules.
Criminal Penalties for HIPAA Violations
Criminal penalties for HIPAA violations are divided into three separate tiers, with the term – and an accompanying fine – decided by a judge based on the facts of each individual case. As with OCR, a number of general factors are considered that will affect the penalty issued. If an individual has profited from the theft, access, or disclosure of PHI, it may be necessary for all money received to be refunded, in addition to the payment of a fine.
The tiers of criminal penalties for HIPAA violations are:
Tier 1: Reasonable cause or no knowledge of violation – Up to 1 year in jail
Tier 2: Obtaining PHI under false pretenses – Up to 5 years in jail
Tier 3: Obtaining PHI for personal gain or with malicious intent – Up to 10 years in jail
In recent years, the number of employees discovered to be accessing or stealing PHI – for various reasons – has increased. The value of PHI on the black market is considerable, and this can be a big temptation for some individuals. It is essential that controls are put in place to limit the opportunity for individuals to steal patient data, and for systems and policies to be put in place to ensure improper access and theft of PHI is identified promptly.
All staff likely to come into contact with PHI as part of their work duties should be informed of the HIPAA criminal penalties and that violations will not only result in loss of employment but also potentially a lengthy jail term and a heavy fine. State attorneys general are cracking down on data theft and are keen to make examples out of individuals found to have violated HIPAA Privacy Rules. A jail term for the theft of HIPAA data is now highly likely, especially if the data is stolen for financial gain.
Convictions and Jail Time for HIPAA Violations
Organ Transplant Coordinator Gets 2-Year Jail Term for Illegally Accessing Health Records of Supreme Court Judge
Arizona Man Sentenced to 54 Months in Criminal HIPAA Violation Case
Former Methodist Hospital Employees Plead Guilty to Criminal HIPAA Violations
Pharma Sales Rep Pleads Guilty to Healthcare Fraud and Criminal HIPAA Violations
Florida Medical Clinic Worker Sentenced to 48 Months in Jail over Theft of PHI
3-Year Jail Term for VA Employee Who Stole Patient Data
Former New York Dental Practice Receptionist Sentenced to 2-6 years for HIPAA Violation
UPMC Patient Care Coordinator Gets 1 Year Jail Term for HIPAA Violation
Employee Sanctions for HIPAA Violations
Not all HIPAA violations are a result of insider theft, and many Covered Entities and Business Associates apply a scale of employee sanctions for HIPAA violations depending on factors such as whether the violation was intentional or accidental, whether it was reported by the employee as soon as the violation was realized, and the magnitude of the breach. Some Covered Entities also apply employee sanctions for HIPAA violations on employees who were aware that a violation (by another employee) had occurred but failed to report it.
Employee sanctions for HIPAA violations vary in severity from further training to dismissal. The decision should be taken in consultation with HIPAA Privacy and Security Officers, who may have to conduct interviews with the employee, investigate audit trails, and review telephone logs, including the telephone logs of the employee´s mobile phone. Because of the expense and disruption attributable to applying employee sanctions for HIPAA violations, it is worthwhile dedicating more resources to initial employee HIPAA training in order to prevent HIPAA violations, whether intentional or accidental, from occurring.
Receiving a Civil Penalty for Unknowingly Violating HIPAA
Although it was mentioned above that OCR has the discretion to waive a civil penalty for unknowingly violating HIPAA, ignorance of HIPAA regulations is not regarded as a justifiable excuse for failing to implement the appropriate safeguards. In April 2017, the remote cardiac monitoring service CardioNet was fined $2.5 million for failing to fully understand the HIPAA requirements and subsequently failing to conduct a complete risk assessment.
As a result of the incomplete risk assessment, the PHI of 1,391 individuals was potentially disclosed without authorization when a laptop containing the data was stolen from a car parked outside an employee´s home. Speaking after details of the fine had been announced, OCR Director Roger Severino described the civil penalty for unknowingly violating HIPAA as a penalty for disregarding security.
It may also be possible for a CE or BA to receive a civil penalty for unknowingly violating HIPAA if the state in which the violation occurs allows individuals to bring legal action against the person(s) responsible for the violation. Although HIPAA lacks a private right of action, individuals can still use state regulations to establish a standard of care under common law. Several cases of this nature are currently in progress.
Penalties for Non-Compliance with HIPAA
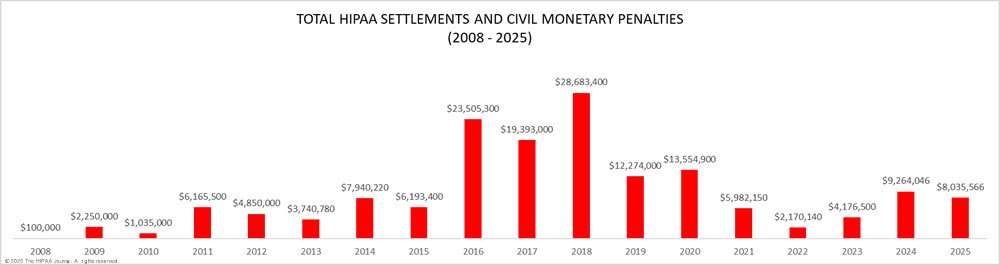
As the graph below shows, OCR has increased its HIPAA enforcement activities in recent years and is now imposing more financial penalties for HIPAA violations. OCR has launched two enforcement initiatives in recent years – the enforcement initiative targeting noncompliance with the HIPAA Right of Access (launched in 2019) that has resulted in more than 50 financial penalties, and the more recent initiative targeting noncompliance with the risk analysis provision of the HIPAA Security Rule. OCR Director Melanie Fontes Rainer confirmed that 22 enforcement actions were closed by OCR in 2024 with either settlements or civil monetary penalties, although there was a delay in announcing some of those enforcement actions, which rolled over into 2025. This year has also started with a large number of financial penalties, with a further 10 announced by the end of May 2025, largely due to OCR’s new HIPAA risk analysis enforcement initiative.

When deciding on an appropriate settlement, OCR considers the severity of the violation, the extent of non-compliance with HIPAA Rules, the number of individuals impacted, and the impact a breach has had on those individuals. OCR also considers the financial position of the covered entity. Punitive measures may be necessary, but penalties for HIPAA violations should not result in a covered entity being forced out of business.
The purpose of these penalties for HIPAA violations is, in part, to punish covered entities for serious violations of HIPAA Rules, but also to send a message to other healthcare organizations that noncompliance with HIPAA Rules is not acceptable.
2025 HIPAA Fines and Settlements
2025 HIPAA Civil Monetary Penalties
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Oregon Health & Science University |
Failure to provide a patient with timely access to their medical records. |
1 |
$200,000 |
| Warby Parker, Inc. |
Multiple HIPAA Security Rule failures: Failure to conduct a HIPAA-compliant risk analysis, failure to reduce risks to ePHI, failure to monitor activity in information systems containing ePHI |
198,470 |
$1,500,000 |
2025 HIPAA Settlements
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| BST & Co. CPAs, LLP |
Risk analysis failure |
170,000 |
$175,000 |
| Syracuse ASC (Specialty Surgery Center of Central New York) |
Risk analysis failure, breach notification failures (HHS, individuals) |
24,891 |
$250,000 |
| Deer Oaks – The Behavioral Health Solution |
Risk analysis failure, impermissible disclosure of ePHI |
171,871 |
$225,000 |
| Comstar LLC |
Risk analysis failure |
585,621 |
$75,000 |
| BayCare Health System |
Information access management (minimum necessary standard), risk management, information system activity review |
1 |
$800,000 |
| Vision Upright MRI |
Failure to conduct a HIPAA-compliant risk analysis, failure to issue breach notifications |
21,788 |
$5,000 |
| Comprehensive Neurology |
Failure to conduct a HIPAA-compliant risk analysis |
6,800 |
$25,000 |
| PIH Health, Inc. |
Failure to conduct a HIPAA-compliant risk analysis, impermissible disclosure of ePHI, failure to issue prompt breach notices to OCR and the affected individuals, and failure to issue a media breach notice |
189,763 |
$600,000 |
| Guam Memorial Hospital Authority |
Failure to conduct a HIPAA-compliant risk analysis |
5,000 |
$25,000 |
| Northeast Radiology |
Failure to conduct a HIPAA-compliant risk analysis |
298,532 |
$350,000 |
| Health Fitness Corporation |
Failure to conduct a HIPAA-compliant risk analysis |
4,304 |
$227,816 |
| Northeast Surgical Group |
Risk analysis failure |
10,840 |
$10,000 |
| Memorial Health System |
HIPAA Right of Access failure |
1 |
$60,000 |
| Solara Medical Supplies |
Risk analysis and risk management failure, failure to issue timely notifications, and an impermissible disclosure of ePHI on two occasions |
114,007 and 1,531 |
$3,000,000 |
| USR Holdings |
Risk analysis failure, failure to record activity in information systems, lack of procedures for creating and maintaining retrievable exact copies of ePHI, and an impermissible disclosure of 2,903 individuals’ PHI |
2,903 |
$337,750 |
| Virtual Private Network Solutions |
Risk analysis failure |
At least 23,868 |
$90,000 |
| Elgon Information Systems |
Risk analysis failure |
31,248 |
$80,000 |
2024 HIPAA Fines and Settlements
OCR was expected to step up HIPAA enforcement in 2024 after a year of relatively few financial penalties, and on December 31, 2024, confirmed that 22 enforcement actions resulted in settlements or civil monetary penalties. One of the problems OCR has faced is a lack of funding, which has hampered its ability to enforce HIPAA compliance. OCR’s budget has remained flat for years, but its workload has increased, and Congress has failed to provide additional funds, despite funding increases being requested annually. For instance, OCR investigates all large data breaches; however, the number of breaches has increased substantially. In 2018, 369 data breaches of 500 or more records were reported. More than twice that number were reported in 2023 (747), and similar numbers of breaches have been reported in 2024. OCR is also having to investigate record numbers of complaints from individuals about potential HIPAA violations.
In 2023, OCR underwent restructuring to improve efficiency and make better use of its resources, which has helped the department start to clear the backlog of investigations of data breaches and complaints. In December 2023, OCR confirmed that steps were being taken to improve cybersecurity in healthcare and reduce the number of data breaches, and in January 2024, OCR published voluntary cybersecurity performance goals and has been encouraging healthcare organizations to work toward achieving those goals. OCR intends to make funds available to help healthcare organizations achieve those goals and provide incentives for maturing their cybersecurity programs.
In December 2024, OCR proposed an update to the HIPAA Security Rule to add new cybersecurity requirements, including several of the measures recommended in its essential cybersecurity goals. If signed into law, these new requirements should help reduce the number of data breaches. It will take months before the Security Rule updates are finalized, and there will be a grace period before OCR enforces the new requirements. How long that will take will depend on the incoming Trump administration.
The proposed HIPAA Security Rule update also includes changes to address legal issues the HHS has had with enforcing HIPAA compliance. For instance, in 2018, OCR announced an enforcement action against the University of Texas MD Anderson Cancer Center for a data breach and lack of encryption, but the penalty was overturned on appeal. On January 14, 2021, a three-member panel for the Fifth Circuit Court of Appeals unanimously vacated the $4,348,000 penalty, and since that date, most penalties have been imposed for HIPAA Right of Access failures.
The decision by the Court of Appeals was widely thought to have affected OCR’s willingness to pursue financial penalties for certain HIPAA violations, but in 2022, multiple financial penalties were imposed for other HIPAA violations, and these continued to increase in 2023. In 2024, many of the financial penalties have been imposed for HIPAA Security Rule violations, and OCR has recently launched a HIPAA Security Rule risk analysis enforcement initiative that has already resulted in multiple financial penalties.
While OCR has stated that 22 settlements and civil monetary penalties were agreed in 2024, 6 of those enforcement actions were not announced until January 2025.
2024 HIPAA Civil Monetary Penalties
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Children’s Hospital Colorado Health System |
Failure to provide HIPAA Privacy Rule training to 6,666 workforce members; failure to conduct a thorough and accurate risk analysis; impermissible disclosure of ePHI of 10,840 individuals |
10,840 |
$548,265 |
| Gulf Coast Pain Consultants, dba Clearway Pain Solutions Institute |
HIPAA Security Rule failures: Risk analysis; review logs of information systems; termination of access rights of former workforce members; policies and procedures for modifying access rights |
34,310 |
$1,190,000 |
| Rio Hondo Community Mental Health Center |
HIPAA Right of Access failure |
1 |
$100,000 |
| Gums Dental Care |
HIPAA Right of Access failure |
1 |
$70,000 |
| Providence Medical Institute |
HIPAA Security Rule Failures – Restrict access to PHI; Business associate agreement |
85,000 |
$240,000 |
| American Medical Response |
HIPAA Right of Access failure |
1 |
$115,200 |
| Essex Residential Care (Hackensack Meridian Health, West Caldwell Care Center) |
HIPAA Right of Access failure |
1 |
$100,000 |
2024 HIPAA Settlements
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Inmediata Health Group |
Risk analysis failure, failure to monitor activity in information systems, impermissible disclosure of the ePHI of 1,565,338 individuals |
1,565,338 |
$250,000 |
| Holy Redeemer Family Medicine |
Impermissible disclosure of a patient’s medical records |
1 |
$35,581 |
| Bryan County Ambulance Authority |
Has never conducted a risk analysis |
14,273 |
$90,000 |
| Plastic Surgery Associates of South Dakota |
Multiple HIPAA Security Rule Failures |
10,229 |
$500,000 |
| Cascade Eye and Skin Centers |
Risk analysis failure; failure to monitor logs of activity in information systems. |
unknown |
$250,000 |
| Heritage Valley Health System |
Multiple HIPAA Security Rule Failures |
unknown |
$950,000 |
| Phoenix Healthcare |
HIPAA Right of Access failure |
1 |
$35,000 |
| Green Ridge Behavioral Health |
Multiple HIPAA Privacy and Security Rule Failures |
14,000 |
$40,000 |
| Montefiore Medical Center |
Multiple HIPAA Security Rule Failures |
12,517 |
$4,750,000 |
2023 HIPAA Fines and Settlements
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Optum Medical Care |
HIPAA Right of Access failure |
6 |
$160,000 |
| St. Joseph’s Medical Center |
Disclosure of PHI to a reporter |
3 |
$80,000 |
| Doctors’ Management Services |
Multiple HIPAA Security Rule failures |
206,695 |
$100,000 |
| LA Care Health Plan |
Multiple HIPAA Security Rule failures |
1,498 |
$1,300,000 |
| UnitedHealthcare |
HIPAA Right of Access failure |
1 |
$80,000 |
| iHealth Solutions (dba Advantum Health) |
Unsecured server – Impermissible disclosure of ePHI; risk analysis failure. |
267 |
$75,000 |
| Yakima Valley Memorial Hospital |
Snooping by security guards – Lack of policies and procedures identified. |
419 |
$240,000 |
| Manasa Health Center, LLC |
Impermissible disclosure of PHI on an Internet platform, Privacy Rule and Breach Notification Rule policies and procedures |
4 |
$30,000 |
| MedEvolve Inc. |
Impermissible disclosure, business associate agreement failure, risk analysis incomplete |
230,572 |
$350,000 |
| David Mente, MA, LPC |
HIPAA Right of Access failure |
1 |
$15,000 |
| Banner Health |
HIPAA Security Rule Violations |
2.81 million |
$1,250,000 |
| Life Hope Labs, LLC |
HIPAA Right of Access failure |
1 |
$16,500 |
2022 HIPAA Fines and Settlements
22 HIPAA enforcement actions in 2022 resulted in financial penalties being imposed. OCR has continued with its 2019 HIPAA enforcement initiative targeting noncompliance with the HIPAA Right of Access, with the 2022 total bringing the number of enforcement actions under this initiative up to 42. Financial penalties were also imposed for impermissible disclosures of patient information on social media websites, inadequate security safeguards to ensure the confidentiality, integrity, and availability of ePHI, inadequate notices of privacy practices, and risk analysis failures.
In January 2021, the HITECH Act was amended to incentivize HIPAA-regulated entities to adopt ‘recognized security practices’ to better protect patient data. While it is not mandatory for recognized security practices to be implemented and maintained, HIPAA-regulated entities that demonstrate that they have implemented recognized security practices that have been in place continuously for the 12 months preceding a data breach will benefit from lower financial penalties, and shorter HIPAA audits and investigations.
2022 HIPAA Settlements
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Health Specialists of Central Florida Inc |
HIPAA Right of Access failure |
1 |
$20,000 |
| New Vision Dental |
Impermissible disclosure of ePHI on Yelp, and notice of privacy practices failure |
<20 |
$23,000 |
| Great Expressions Dental Center of Georgia, P.C. |
HIPAA Right of Access failure (delay + fee) |
1 |
$80,000 |
| Family Dental Care, P.C. |
HIPAA Right of Access failure |
1 |
$30,000 |
| B. Steven L. Hardy, D.D.S., LTD, dba Paradise Family Dental |
HIPAA Right of Access failure |
1 |
$25,000 |
| New England Dermatology and Laser Center |
Improper disposal of PHI, failure to maintain appropriate safeguards |
58,106 |
$300,640 |
| Memorial Hermann Health System |
HIPAA Right of Access failure |
1 |
$240,000 |
| Southwest Surgical Associates |
HIPAA Right of Access failure |
1 |
$65,000 |
| Hillcrest Nursing and Rehabilitation |
HIPAA Right of Access failure |
1 |
$55,000 |
| MelroseWakefield Healthcare |
HIPAA Right of Access failure |
1 |
$55,000 |
| Erie County Medical Center Corporation |
HIPAA Right of Access failure |
1 |
$50,000 |
| Fallbrook Family Health Center |
HIPAA Right of Access failure |
1 |
$30,000 |
| Associated Retina Specialists |
HIPAA Right of Access failure |
1 |
$22,500 |
| Coastal Ear, Nose, and Throat |
HIPAA Right of Access failure |
1 |
$20,000 |
| Lawrence Bell, Jr. D.D.S |
HIPAA Right of Access failure |
1 |
$5,000 |
| Danbury Psychiatric Consultants |
HIPAA Right of Access failure |
1 |
$3,500 |
| Oklahoma State University – Center for Health Sciences |
Risk analysis, security incident response and reporting, evaluation, audit controls, breach notifications & an unauthorized disclosure |
279,865 |
$875,000 |
| Dr. Brockley |
HIPAA Right of Access |
1 |
$30,000 |
| Jacob & Associates |
HIPAA Right of Access, notice of privacy practices, HIPAA Privacy Officer |
1 |
$28,000 |
| Northcutt Dental-Fairhope |
Impermissible disclosure for marketing, notice of privacy practices, HIPAA Privacy Officer |
5,385 |
$62,500 |
2022 Civil Monetary Penalties for HIPAA Violations
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| ACPM Podiatry |
HIPAA Right of Access failure |
1 |
$100,000 |
| Dr. U. Phillip Igbinadolor, D.M.D. & Associates, P.A |
Impermissible disclosure on social media |
1 |
$50,000 |
OCR HIPAA Fines 2021
There was a reduction in the number of financial penalties for HIPAA violations in 2021 from the record number of penalties in 2020, with OCR’s decision to finalize penalties potentially being affected by the COVID-19 pandemic. That said, penalties have continued to be imposed at relatively high levels, with most of the recent HIPAA violation cases in 2021 imposed for violations of the HIPAA Right of Access. Out of the 14 HIPAA violation cases in 2021 that have resulted in financial penalties, 12 have been for HIPAA Right of Access violations.
In January 2021, one of the largest ever HIPAA fines was imposed on Excellus Health Plan. The settlement resolved a HIPAA case that stemmed from an investigation of a breach of the PHI of 9,358,891 individuals that was reported to OCR in 2015. Aside from that penalty, most of the settlements and civil monetary penalties have been for relatively small amounts and have resulted from investigations of complaints from patients rather than reports of data breaches. As well as the 2021 HIPAA fines being lower, there was a much higher percentage of financial penalties imposed on small healthcare providers than in previous years. That trend is likely to continue in 2023.
2021 HIPAA Settlements
| HIPAA Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Advanced Spine & Pain Management |
HIPAA Right of Access failure |
1 |
$32,150 |
| Denver Retina Center |
HIPAA Right of Access failure |
1 |
$30,000 |
| Rainrock Treatment Center LLC (dba monte Nido Rainrock) |
HIPAA Right of Access failure |
1 |
$160,000 |
| Wake Health Medical Group |
HIPAA Right of Access failure |
1 |
$10,000 |
| Children’s Hospital & Medical Center |
HIPAA Right of Access failure |
1 |
$80,000 |
| The Diabetes, Endocrinology & Lipidology Center, Inc. |
HIPAA Right of Access failure |
1 |
$5,000 |
| AEON Clinical Laboratories (Peachstate) |
HIPAA Security Rule failures (risk assessment, risk management, audit controls, and documentation of HIPAA Security Rule policies and procedures) |
Unknown |
$25,000 |
| Village Plastic Surgery |
HIPAA Right of Access failure |
1 |
$30,000 |
| Arbour Hospital |
HIPAA Right of Access failure |
1 |
$65,000 |
| Sharpe Healthcare |
HIPAA Right of Access failure |
1 |
$70,000 |
| Renown Health |
HIPAA Right of Access failure |
1 |
$75,000 |
| Excellus Health Plan |
Multiple HIPAA Violations: Risk analysis, risk management, information system activity reviews, technical policies to prevent unauthorized ePHI access, breach of 9,358,891 records. |
9,358,891 |
$5,100,000 |
| Banner Health |
HIPAA Right of Access failure |
2 |
$200,000 |
2021 Civil Monetary Penalties for HIPAA Violations
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Dr. Robert Glaser |
HIPAA Right of Access failure |
1 |
$100,000 |
OCR HIPAA Fines 2020
2020 saw more financial penalties imposed on HIPAA-covered entities and business associates than in any other year since OCR started enforcing HIPAA compliance. 19 settlements were reached to resolve potential violations of the HIPAA Rules. OCR continued with its HIPAA Right of Access enforcement initiative that commenced in late 2019 and by year-end had settled 11 cases where patients had not been provided with timely access to their medical records for a reasonable cost-based fee.
2020 saw the second-largest settlement to resolve HIPAA violations. The health insurer Premera Blue Cross paid OCR $6,850,000 to resolve potential HIPAA violations discovered during the investigation of its 2015 breach of the ePHI of 10,466,692 individuals.
2020 OCR HIPAA Settlements
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Peter Wrobel, M.D., P.C., dba Elite Primary Care |
HIPAA Right of Access failure |
2 |
$36,000 |
| University of Cincinnati Medical Center |
HIPAA Right of Access failure |
1 |
$65,000 |
| Dr. Rajendra Bhayani |
HIPAA Right of Access failure |
1 |
$15,000 |
| Riverside Psychiatric Medical Group |
HIPAA Right of Access failure |
1 |
$25,000 |
| City of New Haven, CT |
Failure to terminate access rights; risk analysis failure; failure to implement Privacy Rule policies; failure to issue unique IDs to allow system activity to be tracked; impermissible disclosure of the PHI of 498 individuals |
498 |
$202,400 |
| Aetna |
Lack of technical and nontechnical evaluation in response to environmental or operational changes; identity check failure; minimum necessary information failure; impermissible disclosure of 18,849 records; lack of administrative, technical, and physical safeguards |
18,849 |
$1,000,000 |
| NY Spine |
HIPAA Right of Access failure |
1 |
$100,000 |
| Dignity Health, dba St. Joseph’s Hospital and Medical Center |
HIPAA Right of Access failure |
1 |
$160,000 |
| Premera Blue Cross |
Risk assessment failure; risk management failure; insufficient hardware and software controls; unauthorized access to the PHI of 10,466,692 individuals |
10,466,692 |
$6,850,000 |
| CHSPSC LLC |
Failure to conduct a risk analysis; failures to implement information system activity reviews, security incident procedures, and access controls, and a breach of the ePHI of more than 6 million individuals |
6,121,158 |
$2,300,000 |
| Athens Orthopedic Clinic PA |
Failure to conduct a risk analysis; lack of risk management and audit controls; failure to maintain HIPAA policies and procedures; business associate agreement failure; and the failure to provide HIPAA Privacy Rule training to the workforce. |
208,557 |
$1,500,000 |
| Housing Works, Inc. |
HIPAA Right of Access failure |
1 |
$38,000 |
| All Inclusive Medical Services, Inc. |
HIPAA Right of Access failure |
1 |
$15,000 |
| Beth Israel Lahey Health Behavioral Services |
HIPAA Right of Access failure |
1 |
$70,000 |
| King MD |
HIPAA Right of Access failure |
1 |
$3,500 |
| Wise Psychiatry, PC |
HIPAA Right of Access failure |
1 |
$10,000 |
| Lifespan Health System Affiliated Covered Entity |
Lack of encryption; insufficient device and media controls; lack of business associate agreements; impermissible disclosure of 20,431 patients’ ePHI |
20,431 |
$1,040,000 |
| Metropolitan Community Health Services dba Agape Health Services |
Longstanding, systemic noncompliance with the HIPAA Security Rule |
1,263 |
$25,000 |
OCR HIPAA Fines 2019
HIPAA enforcement continued at a high level in 2019. Eight settlements were reached with HIPAA-covered entities and business associates to resolve HIPAA violations and two civil monetary penalties were issued. The financial penalties were imposed to resolve similar violations of HIPAA Rules as in previous years, but 2019 also saw the first financial penalties issued under OCR’s new HIPAA Right of Access initiative. Two covered entities settled cases over the failure to provide patients with a copy of their medical records, in the requested format, in a reasonable time frame.
2019 OCR HIPAA Settlements
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| West Georgia Ambulance |
Risk analysis failure; no security awareness training program; failure to implement HIPAA Security Rule policies and procedures. |
500 |
$65,000 |
| Korunda Medical, LLC |
HIPAA Right of Access failure. |
1 or more |
$85,000 |
| Sentara Hospitals |
Breach notification failure; business associate agreement failure |
577 |
$2,175,000 |
| University of Rochester Medical Center |
Loss of flash drive/laptop; no encryption; risk analysis failure; risk management failure; lack of device media controls. |
43 |
$3,000,000 |
| Elite Dental Associates |
Social media disclosure; notice of privacy practices; impermissible PHI disclosure. |
Unconfirmed |
$10,000 |
| Bayfront Health St Petersburg |
HIPAA Right of Access failure |
1 |
$85,000 |
| Medical Informatics Engineering |
Risk analysis failure; impermissible disclosure of 3.5 million records |
3,500,000 |
$100,000 |
| Touchstone Medical imaging |
No BAAs; insufficient access rights; risk analysis failure; failure to respond to a security incident; breach notification failure; media notification failure; impermissible disclosure of 307,839 individuals’ PHI. |
307,839 |
$3,000,000 |
2019 OCR Civil Monetary Penalties
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Texas Department of Aging and Disability Services |
Risk analysis failure; access control failure; information system activity monitoring failure; impermissible disclosure of 6,617 patients ePHI |
6,617 |
$1,600,000 |
| Jackson Health System |
Multiple Privacy Rule, Security Rule, and Breach Notification Rule violations |
25,661 |
$2,154,000 |
OCR HIPAA Fines 2018
There was a year-over-year increase in HIPAA violation penalties in 2018. 11 financial penalties were agreed in 2018: 10 settlements and one civil monetary penalty. Two records were broken in 2018. 2018 saw the largest ever HIPAA settlement agreed – A $16 million financial penalty for Anthem Inc., to resolve HIPAA violations discovered during the investigation of its 78.8 million record breach in 2015. HIPAA-covered entities also paid more in fines than in any other year since OCR started enforcing compliance with HIPAA Rules: $28,683,400.
2018 OCR HIPAA Settlements
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| Cottage Health |
Risk analysis and risk management failures; No BAA |
62,500 |
$3,000,000 |
| Pagosa Springs Medical Center |
Failure to terminate employee access; No BAA |
557+ |
$111,400 |
| Advanced Care Hospitalists |
Impermissible PHI Disclosure; No BAA; Insufficient security measures; No HIPAA compliance efforts prior to April 1, 2014 |
9,255 |
$500,000 |
| Allergy Associates of Hartford |
PHI disclosure to a reporter; No sanctions against employees |
1 |
$125,000 |
| Anthem Inc |
Risk analysis failure; Insufficient reviews of system activity; Failure to respond to a detected breach; Insufficient technical controls to prevent unauthorized ePHI access |
78,800,000 |
$16,000,000 |
| Boston Medical Center |
Filming patients without consent |
Unspecified |
$100,000 |
| Brigham and Women’s Hospital |
Filming patients without consent |
Unspecified |
$384,000 |
| Massachusetts General Hospital |
Filming patients without consent |
Unspecified |
$515,000 |
| Filefax, Inc. |
Impermissible disclosure of physical PHI – Left unprotected in truck |
2,150 |
$100,000 |
| Fresenius Medical Care North America |
5 breaches: Investigation revealed risk analysis failures; Impermissible disclosure of ePHI; Lack of policies covering electronic devices; Lack of encryption; Insufficient security policies; Insufficient physical safeguards |
521 |
$3,500,000 |
2018 Civil Monetary Penalties for HIPAA Violations
| HIPAA-Regulated Entity |
Reason |
Individuals Impacted |
Amount |
| University of Texas MD Anderson Cancer Center |
3 breaches resulting in an impermissible disclosure of ePHI; No Encryption |
34,883 |
$4,348,000 |
OCR HIPAA Fines 2017
A summary of the 2017 OCR penalties for HIPAA violations.
2017 OCR HIPAA Settlements
| HIPAA-Regulated Entity |
Breach Summary |
Individuals Impacted |
Settlement Amount |
| Memorial Healthcare System |
Impermissible access of PHI by employees; Impermissible disclosure of PHI to affiliated physicians’ offices |
115,143 |
$5,500,000 |
| Cardionet |
Theft of an unencrypted laptop computer |
1,391 |
$2,500,000 |
| Memorial Hermann Health System |
Disclosure of patient’s PHI to the media |
1 |
$2,400,000 |
| 21st Century Oncology |
Multiple HIPAA violations |
2,213,597 |
$2,300,000 |
| MAPFRE Life Insurance Company of Puerto Rico |
Theft of an unencrypted USB storage device |
2,209 |
$2,200,000 |
| Presense Health |
Delayed breach notifications |
836 |
$475,000 |
| Metro Community Provider Network |
Lack of a security management process to safeguard ePHI |
3,200 |
$400,000 |
| Luke’s-Roosevelt Hospital Center Inc. |
Impermissible disclosure of PHI to the patient’s employer |
1 |
$387,000 |
| The Center for Children’s Digestive Health |
Lack of a business associate agreement |
N/A |
$31,000 |
2017 Civil Monetary Penalties for HIPAA Violations
| HIPAA-Regulated Entity |
Breach Summary |
Individuals Impacted |
Penalty Amount |
| Children’s Medical Center of Dallas |
Theft of unencrypted devices |
6,262 |
$3,200,000 |
OCR HIPAA Fines 2016
2016 was a record year for financial penalties to resolve violations of HIPAA Rules. 2016 saw 12 settlements agreed and one civil monetary penalty issued by OCR.
2016 OCR HIPAA Settlements
| HIPAA-Regulated Entity |
Breach Summary |
Individuals Impacted |
Settlement Amount |
| Feinstein Institute for Medical Research |
Improper disclosure of research participants’ PHI |
13,000 |
$3,900,000 |
| Advocate Health Care Network |
Theft of desktop computers; Loss of laptop; Improper accessing of data at a business associate |
3,994,175 |
$5,550,000 |
| University of Mississippi Medical Center |
Unprotected network drive |
10,000 |
$2,750,000 |
| Oregon Health & Science University |
Loss of unencrypted laptop; Storage on a cloud server without BAA |
4,361 |
$2,700,000 |
| New York Presbyterian Hospital |
Filming of patients by a TV crew |
Unconfirmed |
$2,200,000 |
| North Memorial Health Care of Minnesota |
Theft of laptop computer; Improper disclosure to a business associate |
299,401 |
$1,550,000 |
| St. Joseph Health |
PHI made available through search engines |
31,800 |
$2,140,500 |
| Raleigh Orthopaedic Clinic, P.A. of North Carolina |
Improper disclosure to a business associate |
17,300 |
$750,000 |
| University of Massachusetts Amherst (UMass) |
Malware infection |
1,670 |
$650,000 |
| Catholic Health Care Services of the Archdiocese of Philadelphia |
Theft of mobile device |
412 |
$650,000 |
| Care New England Health System |
Loss of two unencrypted backup tapes |
14,000 |
$400,000 |
| Complete P.T., Pool & Land Physical Therapy, Inc. |
Improper disclosure of PHI (website testimonials) |
Unconfirmed |
$25,000 |
2016 Civil Monetary Penalties for HIPAA Violations
| HIPAA-Regulated Entity |
Breach Summary |
Individuals Impacted |
Penalty Amount |
| Lincare, Inc. |
Improper disclosure (unprotected documents) |
278 |
$239,800 |
What are the Penalties for HIPAA Violations? FAQs
What is the maximum penalty for violating HIPAA?
The maximum penalty for violating HIPAA per violation is currently $71,162. However, it is rare that an event that results in the maximum penalty being issued is attributable to a single violation. For example, a data breach could be attributable to the failure to conduct a risk analysis, the failure to provide a security awareness training program, and a failure to prevent password sharing.
What are the consequences of a HIPAA violation?
The consequences of a HIPAA violation depend on the nature of the violation, the reason(s) behind it, the amount of harm it causes, and the organization´s previous history of compliance. In most cases, HIPAA violations are not attributable to willful neglect and HHS´ Office for Civil Rights will try to resolve first-time HIPAA violations via technical assistance or a corrective action plan.
What is the civil penalty for unknowingly violating HIPAA?
The civil penalty for unknowingly violating HIPAA is no different from knowingly violating HIPAA. The Privacy and Security Rules have been in existence for more than twenty years; and, to quote OCR Director Roger Severino “the civil penalty for unknowingly violating HIPAA is a penalty for disregarding security”. There is no excuse for unknowingly violating HIPAA.
What are the categories for punishing violations of federal health care laws?
The categories for punishing violations of federal health care laws vary considerably depending on which law is being violated or which section of which law is being violated. For example, with regard to the penalties for HIPAA violations, there are four civil categories for punishing violations and three criminal categories. However, in other federal healthcare laws (for example, the Social Security Act), there can be dozens of categories for punishing violations of federal healthcare laws.
What criminal consequences are possible with a Tier 3 violation?
The criminal consequences possible with a Tier 3 violation – wrongfully and knowingly obtaining PHI for personal gain, commercial advantage, or with malicious intent – are up to ten years in jail and/or a fine of up to $250,000. These penalties are pursued by the Department of Justice rather than HHS´ Office for Civil Rights.
What are the fines for HIPAA violations?
The fines for HIPAA violations (per violation – as of August 2024) are:
Tier 1 – from $141 to $35,581
Tier 2 – from $1,424 to $71,162
Tier 3 – from $14,232 to $71,162
Tier 4 – $71,162 to $2,134,831
It is important to be aware that, in addition to the fines for HIPAA violations issued by HHS’ Office for Civil Rights, State Attorneys General can issue additional fines for HIPAA violations. Depending on the nature of the violation(s) and state laws, it may be possible for affected individuals to bring a class action lawsuit against an organization guilty of a HIPAA violation.
What does a corrective action plan consist of?
A corrective action plan consists of measures to address the underlying issue(s) that led to a HIPAA violation(s). What the action plan will consist of will be relevant to the nature of the violation(s). Typically, Covered Entities and Business Associates will be required to develop or revise policies to fill gaps in their compliance; and, when new or revised policies affect the functions of the workforce, provide training on the new or revised policies.
Are penalties for HIPAA violations always related to data breaches?
Penalties for HIPAA violations are not always related to data breaches. As you will see from the tables above, several Covered Entities have been fined or reached settlement resolutions for failing to provide patients with access to healthcare records within the permitted 30 days. One Covered Entity was fined for failing to have a Business Associate Agreement in place before disclosing ePHI to a Business Associate. None of these penalties for HIPAA violations involved a breach of unsecured PHI.
How does the Office for Civil Rights find out about HIPAA violations?
The Office for Civil Rights finds out about HIPAA violations in a number of ways. For example, Covered Entities are required to report breaches of unsecured PHI within 60 days (or annually if the breach involves fewer than 500 patients), patients can use the OCR complaints portal to report a delay or refusal to access health information, and members of Covered Entities’ workforces are granted whistleblower protection for reporting non-compliance.
What if a violation occurs due to a common non-compliant practice?
If a HIPAA violation occurs due to a common non-compliant practice, the penalty will depend on the nature of the violation, the consequences of the violation, and the perpetrator’s previous compliance history. Most often, a penalty will consist of refresher training and a compliance monitoring program – potentially by a third-party organization at the organization´s own cost.
Are HIPAA violations criminal?
HIPAA violations are criminal when an individual knowingly and wrongfully discloses individually identifiable health information. In such cases, a violation can be referred to the Department of Justice for criminal investigation. If the individual is found guilty of a criminal offense under § 1320d-6 of the Social Security Act, they can be fined up to $250,000 and sentenced to up to ten years in jail.
Has anybody ever received a custodial sentence for violating HIPAA?
A custodial sentence for violating HIPAA is rare, but it has happened – for example, when an employee has been found guilty of stealing PHI to commit identity theft or to sell for personal gain. Even when a violation does not result in a custodial sentence, the offending employee will likely be fined, lose their job, and have their license to practice withdrawn. Depending on how the employee accessed the data, Covered Entities, and Business Associates can also be fined for the same violation.
Who issues HIPAA violation fines?
HIPAA violation fines are most often issued by the Department of Health and Human Services’ Office for Civil Rights. However, fines for HIPAA violations can also be issued by State Attorneys General and the Federal Trade Commission; and – when the violation is criminal in nature – the Department of Justice can pursue criminal prosecutions against the perpetrators, which can also result in fines.
The Centers for Medicare and Medicaid Services (CMS) also have the authority to issue fines for violations of the HIPAA Administrative Requirements (45 CFR Part 162). To date, CMS has not exercised this option – preferring instead to resolve violations of Part 162 with technical assistance and corrective action plans.
Are HIPAA breach penalties always financial?
HIPAA breach penalties are not always financial. In fact, HHS’ Office for Civil Rights has only issued financial penalties in around 2% of cases it has investigated for HIPAA breaches – and penalties issued by State Attorneys General and the FTC are even rarer. The majority of HIPAA breaches are resolved via voluntary compliance, technical assistance, or a corrective action plan.
What HIPAA penalties are imposed by the State Attorneys General?
HIPAA penalties can be imposed by state Attorneys General when there is reason to believe residents of the state have been adversely affected by a violation of HIPAA. In such cases, state Attorneys General can bring a civil action on behalf of residents of the state, with penalties ranging from $100 per violation (per affected resident) to $25,000 per violation type (per affected resident).
Can CMS issue fines for HIPAA violations?
CMS can issue fines for HIPAA violations when the violation relates to the HIPAA Administrative Requirements (45 CFR Part 162). As yet, CMS has not exercised its authority to issue fines for HIPAA violations – instead resolving Part 162 complaints via voluntary compliance, technical assistance, and corrective action plans.
When can the FTC issue HIPAA violation penalties?
The FTC can issue HIPAA violation penalties when an individual or organization not covered by HIPAA experiences a data breach of unsecured PHI or fails to notify individuals following a data breach. Typically, organizations that create or maintain health data that is not covered by HIPAA include vendors of personal health appliances and wearables that transmit data to/from the vendor’s servers.
What is the penalty for a HIPAA violation by a hospital volunteer?
The penalty for a HIPAA violation by a hospital volunteer is the same as if the violation was committed by a paid member of the workforce. Similarly, if a patient complains to HHS’ Office for Civil Rights – and the complaint is investigated – the investigation will not consider the employed status of the violator because Covered Entities are required to train all members of the workforce on HIPAA policies and procedures regardless of whether they are volunteers, students, or employees.
How much is a HIPAA violation penalty?
How much a HIPAA violation penalty is depends on the nature of the violation, the consequences of the violation, the perpetrator’s prior compliance history, their willingness to assist any investigation into the violation, and the speed at which measures are put in place to prevent the violation from happening again. It can also be the case that HHS’ Office for Civil Rights uses a HIPAA violation penalty to “send a message” to other Covered Entities.
What are the HIPAA violation consequences for a medical student?
The HIPAA violation consequences for a medical student will depend on the sanctions policy at the healthcare facility where they are working. Usually – unless the HIPAA violation has serious consequences – the medical student will receive a verbal warning. However, the verbal warning will be recorded in their HR file and may affect future employment opportunities.
Who sets HIPAA fines and penalties?
HIPAA fines and penalties actually existed before HIPAA and were originally related to fraudulent claims for treatment made by healthcare providers to federal agencies (i.e., Medicare). The fines and penalties were increased in the text of HIPAA and applied to violations of the Privacy and Security Rules in 2005 when the Department for Health and Human Services (HHS) published the Enforcement Rule.
The HIPAA fines and penalties were subsequently increased by Congress via the HITECH Act 2009, since 2015, the fines and penalties issued by HHS’ Office for Civil Rights have been adjusted annually to account for inflation. There have been no increases in the HIPAA fines and penalties that can be imposed by State Attorneys General since the passage of HITECH nor in the fines and penalties for criminal violations of HIPAA.
Are HIPAA breach fines always the same for each type of violation?
HIPAA breach fines can be the same for each type of violation but – under §160.408 of the Administrative Simplification provisions – the Secretary for Health and Human Services is required to take a number of factors into account when determining the amount of a HIPAA breach fine.
What is the cost of a HIPAA violation?
The cost of a HIPAA violation varies according to the nature of the violation, who is responsible for it, and what the consequences are. For example, a disclosure of more than the minimum necessary PHI by a member of a Covered Entity’s workforce who with no previous record of non-compliance will likely receive a verbal warning and may have to undergo further training.
Conversely, a healthcare organization that willfully and knowingly neglects to implement the Security Rule safeguards, and experiences a data breach affecting thousands of patients as a result of its negligence, will likely receive a multi-million dollar fine. Between the two extremes, most violations incur some degree of cost – whether it is reported internally or notified to HHS’ Office for Civil Rights. It is in the interest of Covered Entities to protect their reputation by avoiding HIPAA breaches and subsequent HIPAA fines. Covered entities can promote their HIPAA compliance to patients using a HIPAA logo.
Can patients claim monetary damages for a HIPAA violation?
Patients cannot claim monetary damages for a HIPAA violation under HIPAA law, but many states have privacy, security, and/or breach notification laws that do have a private right of action depending on the nature of the violation and the degree of harm suffered. If individuals feel they have suffered harm due to the negligence of a HIPAA Covered Entity or Business Associate, they should seek independent legal advice from an attorney.
What are HIPAA penalties for non-compliance?
HIPAA penalties for non-compliance vary according to the nature of the violation, which section of HIPAA has been violated, and the consequences of the violation. The HIPAA penalties for non-compliance also vary according to who the non-compliant party is. For example, the penalties for non-compliance by a member of the workforce will likely be a verbal or written warning, while the penalties for non-compliance by a Covered Entity will range from technical assistance to a fine.
What is the fine described by HIPAA/HITECH for companies that accidentally release PHI but perform due diligence?
The fine described by HIPAA/HITECH for companies that accidentally release PHI but perform due diligence is a Tier 1 fine for the “Lack of Knowledge” level of culpability. At present (December 2023), the amount of the fine is between $137 per violation to $34,464 per violation – but these amounts will be adjusted for inflation during 2024.
What is the maximum fine per HIPAA violation according to the Final Omnibus Rule?
The maximum fine per HIPAA violation according to the Final Omnibus Rule is $1.5 million. However, it is important to be aware that the tiered HIPAA penalty structure with the $1.5 million penalty cap was introduced by the HITECH Act in 2009 and adopted by the Final Omnibus Rule in 2013. Since 2015, the maximum fine per HIPAA violation has been increased each year to account for inflation.
What are the criminal penalties for HIPAA violations?
The criminal penalties for HIPAA violations vary according to the motive for the offense. According to §1177 of the Social Security Act, a person who obtains, discloses, uses – or causes to be used – individually identifiable health information maintained by a Covered Entity can be fined up to $50,000 and/or imprisoned for up to a year.
However, if the offense is committed under false pretenses, the fine increases up to $100,000 and the prison term up to five years; and, if the offense is committed with the intent to sell, transfer, or use individually identifiable health information for commercial advantage, personal gain, or malicious harm, the fine increases up to $250,000 and the jail term up to ten years.
What are the consequences of violating HIPAA for a nurse?
The consequences of violating HIPAA for a nurse most often depend on the nature of the violation, the impact of the violation, the nurse’s previous compliance record, and the content of the Covered Entity’s sanctions policy. Typically, a first offense with a minor impact will result in a verbal warning and/or refresher training. However, the consequences of violating HIPAA for a nurse could escalate for a serious or repeated offense to a written warning, a suspension, or termination of employment.
Are there HIPAA violation fines for individuals?
There are no HIPAA violation fines for individuals unless an individual qualifies as a HIPAA Covered Entity or Business Associate (i.e., a freelance counselor) and they violate HIPAA in their role as such. Individuals employed by Covered Entities or Business Associates cannot be fined for civil violations but could be fined if a violation is considered criminal and referred to the Department of Justice.
What is the minimum fine for intentional and uncorrected release of PHI?
The minimum fine for intentional and uncorrected release of PHI is currently $68,928 if the offender is a Covered Entity or Business Associate. If the offender is a member of a Covered Entity’s or Business Associate’s workforce, and they violate HIPAA intentionally with criminal intent, there is no set minimum fine. The Courts can decide on a fine of up to $250,000.
What are HIPAA civil monetary penalties?
HIPAA civil monetary penalties are fines sometimes imposed on HIPAA Covered Entities and Business Associates for violations of HIPAA. The term can sometimes be shortened to HIPAA penalties, or HIPAA settlements when the perpetrator negotiates a settlement with HHS’ Office for Civil Rights to avoid a lengthy – and potentially costly – dispute over how the civil monetary penalties should be.
Are HIPAA violations sanctioned differently in different states?
HIPAA violations are not sanctioned differently in different states; although, in some areas, State Attorneys General are more willing to pursue HIPAA violation sanctions against a Covered Entity than in other states. This may be because the state has more stringent privacy or data security regulations than HIPAA, or because a significant number of state residents are impacted by HIPAA violations.
The post What are the Penalties for HIPAA Violations? appeared first on The HIPAA Journal.
 In this article, we provide a detailed explanation of penalties for HIPAA violations.
In this article, we provide a detailed explanation of penalties for HIPAA violations.

 This is not surprising, as there are times when the same information can be both protected and non-protected depending on how it is maintained.
This is not surprising, as there are times when the same information can be both protected and non-protected depending on how it is maintained. The Protected Health Information definition is similar to that for individually identifiable health information when maintained or transmitted by a Covered Entity other than PHI excludes health information maintained in students´ educational records (as these are protected by the Family Educational Rights and Privacy Act) and health information maintained by a Covered Entity in its role as an employer (i.e., health information relating to an employee´s absence from work).
The Protected Health Information definition is similar to that for individually identifiable health information when maintained or transmitted by a Covered Entity other than PHI excludes health information maintained in students´ educational records (as these are protected by the Family Educational Rights and Privacy Act) and health information maintained by a Covered Entity in its role as an employer (i.e., health information relating to an employee´s absence from work). The definition of designated record sets appears in the introduction to the Privacy Rule in
The definition of designated record sets appears in the introduction to the Privacy Rule in 

 The Health Insurance Portability and Accountability Act of 1996 (HIPAA) was introduced primarily to ensure employees could maintain healthcare coverage between jobs and not be discriminated against for pre-existing conditions. To prevent insurance carriers passing on the cost of compliance to plan members and employers, Congress added a second Title to the Act to simplify the administration of healthcare, eliminate wastage, and prevent healthcare fraud.
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) was introduced primarily to ensure employees could maintain healthcare coverage between jobs and not be discriminated against for pre-existing conditions. To prevent insurance carriers passing on the cost of compliance to plan members and employers, Congress added a second Title to the Act to simplify the administration of healthcare, eliminate wastage, and prevent healthcare fraud. Many HIPAA violations are discovered by HIPAA-covered entities through internal audits. Supervisors may identify employees who have violated HIPAA Rules and employees often self-report HIPAA violations and potential violations by co-workers.
Many HIPAA violations are discovered by HIPAA-covered entities through internal audits. Supervisors may identify employees who have violated HIPAA Rules and employees often self-report HIPAA violations and potential violations by co-workers. Organizations subject to HIPAA can use our HIPAA and Social Media Checklist to understand how to avoid HIPAA violations due to misuse of social media by employees.
Organizations subject to HIPAA can use our HIPAA and Social Media Checklist to understand how to avoid HIPAA violations due to misuse of social media by employees. If no PHI is disclosed – and the FTC Rules (see below) are complied with – the Privacy Rule does not apply, and Covered Entities and Business Associates can freely use social media networks to promote healthy lifestyles, market health insurance products, and promote B2B services.
If no PHI is disclosed – and the FTC Rules (see below) are complied with – the Privacy Rule does not apply, and Covered Entities and Business Associates can freely use social media networks to promote healthy lifestyles, market health insurance products, and promote B2B services. In addition to understanding what is considered PHI under HIPAA, it is also important to understand the patient authorization rules which must be part of any HIPAA social media policy.
In addition to understanding what is considered PHI under HIPAA, it is also important to understand the patient authorization rules which must be part of any HIPAA social media policy. Sharing too much information on social media platforms can have devastating effects on both healthcare organizations and employees if patient-specific information is shared.
Sharing too much information on social media platforms can have devastating effects on both healthcare organizations and employees if patient-specific information is shared. For individual members of the workforce, HIPAA certification can help foster patient trust, support applications for promotion, and increase prospects in the job market. However, it is what workforce members learn during a certification program that can have the biggest impact on their professional lives, as this can help prevent unintentional violations that can have significant consequences.
For individual members of the workforce, HIPAA certification can help foster patient trust, support applications for promotion, and increase prospects in the job market. However, it is what workforce members learn during a certification program that can have the biggest impact on their professional lives, as this can help prevent unintentional violations that can have significant consequences.