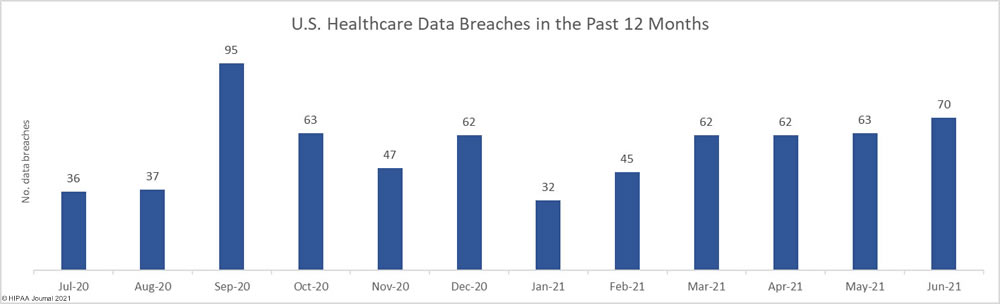
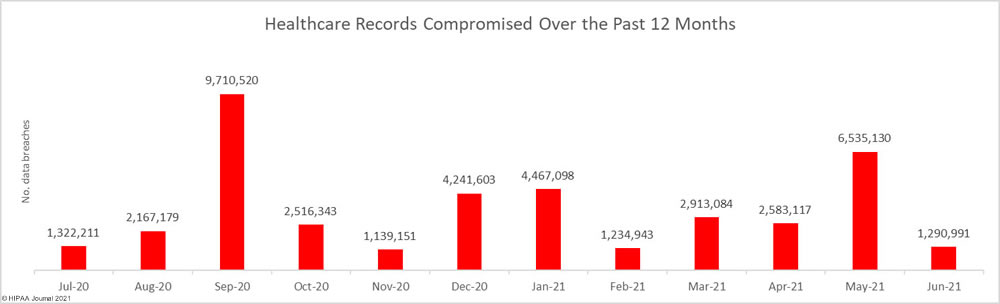
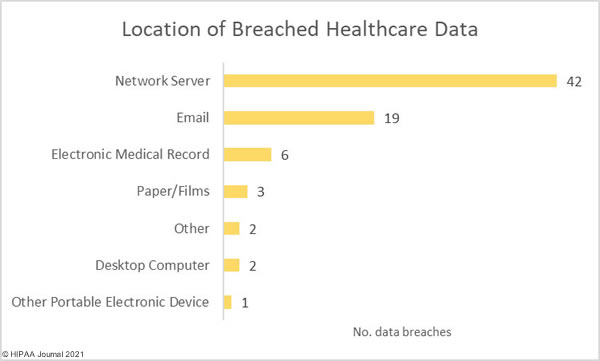
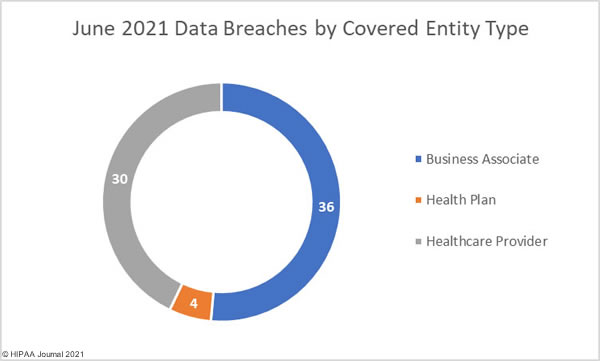
Overlake Hospital Medical Center in Bellevue, WA has proposed a settlement to resolve a class action lawsuit filed by victims of a December 2019 data breach that exposed patients’ demographic information, health insurance information, and health data.
The breach in question was a phishing attack that was discovered on December 9, 2019. The investigation revealed unauthorized individuals gained access to the email accounts of several employees, with one of the email accounts compromised between December 6, 2019 and December 9, 2019, and the others compromised for several hours on December 9.
The investigation did not uncover evidence of data theft or misuse of patient data, but it was not possible to rule unauthorized access to protected health information (PHI) and the exfiltration of data. The PHI of up to 109,000 patients was contained in the compromised email accounts.
Affected individuals were notified starting on February 4, 2020 and Overlake Hospital Medical Center took several steps to improve security, including implementing multi-factor authentication, changing email retention policies, and providing further training to employees. Overlake Hospital Medical Center has spent $148,590 on improvements to bolster security since the breach and has committed to further enhancements totalling $168,000 per year for the next 3 years.
The lawsuit – Richardson V. Overlake Hospital Medical Center – was filed in the Superior Court of King County in Washington, and alleged Overlake Hospital was negligent for failing to prevent unauthorized individuals from gaining access to its systems. The lawsuit also alleged intrusion upon seclusion/invasion of privacy, breach of fiduciary duty, breach of confidence, breach of express contract, and breach of implied contract. While 109,000 individuals were notified about the breach, only 24,000 individuals are included in the class as all other patients did not have their PHI exposed.
The lawsuit alleged the hospital failed to implement reasonable safeguards to ensure the privacy of HIPAA-covered data and failed to provide adequate notice about the data breach. Overlake Hospital Medical Center has denied all claims made in the lawsuit and all charges of wrongdoing. The decision was made to settle the lawsuit with no admission of liability.
Under the terms of the settlement, two types of claims can be submitted. Class members are entitled to claim up to $250 for certain out-of-pocket expenses incurred as a result of the breach, including bank fees, phone calls, postage costs, fuel for local travel, and up to three hours of documented time at $20 per hour, provided at least one full hour was spent on mitigations. It is also possible to recover the cost of credit report fees, and credit monitoring and identity theft protection services taken out between February 4, 2020 and the date of the Court’s preliminary approval of the settlement.
Claims for extraordinary expense reimbursement may be submitted for up to $2,500. These claims must include evidence of losses that were more likely than not suffered as a result of the breach between December 1, 2019 and the end of the claim period.
A fairness hearing has been scheduled for Sept. 10, 2021.
The post Overlake Hospital Medical Center Proposes Settlement to Resolve Data Breach Case appeared first on HIPAA Journal.