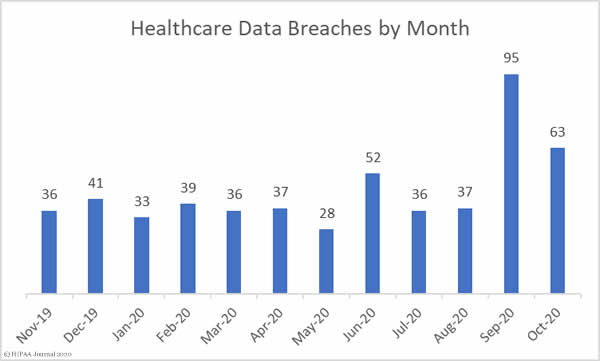
October saw well above average numbers of data breaches reported the HHS’ Office for Civil Rights. There were 63 reported breaches of 500 or more records, which is a 33.68% reduction from September but still 41.82% more breaches than the monthly average over the last 12 months. The elevated numbers of breaches can be partly explained by continued reports from healthcare organizations that were impacted by the ransomware attack on the cloud software firm Blackbaud.
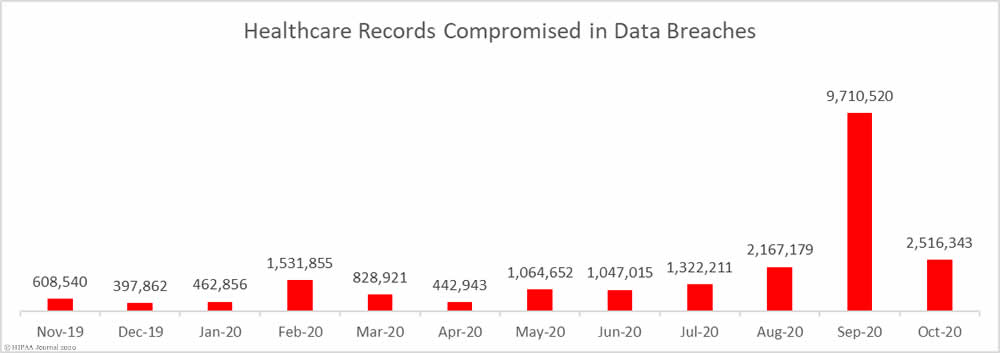
The protected health information of more than 2.5 million individuals were exposed or compromised in those 63 breaches, which is 74.08% fewer records than September, but still 26.81% more than the monthly average number of breached records over the past 12 months.
Largest Healthcare Data Breaches Reported in October 2020
| Name of Covered Entity |
Covered Entity Type |
Type of Breach |
Individuals Affected |
Breach Cause |
| Luxottica of America Inc. |
Business Associate |
Hacking/IT Incident |
829,454 |
Ransomware Attack |
| AdventHealth Orlando |
Healthcare Provider |
Hacking/IT Incident |
315,811 |
Blackbaud Ransomware |
| Presbyterian Healthcare Services |
Healthcare Provider |
Hacking/IT Incident |
193,223 |
Phishing Attack |
| Sisters of Charity of St. Augustine Health System |
Healthcare Provider |
Hacking/IT Incident |
118,874 |
Blackbaud Ransomware |
| Timberline Billing Service, LLC |
Business Associate |
Hacking/IT Incident |
116,131 |
Ransomware Attack |
| Greenwich Hospital |
Healthcare Provider |
Hacking/IT Incident |
95,000 |
Blackbaud Ransomware |
| OSF HealthCare System |
Healthcare Provider |
Hacking/IT Incident |
94,171 |
Blackbaud Ransomware |
| Geisinger |
Healthcare Provider |
Hacking/IT Incident |
86,412 |
Blackbaud Ransomware |
| CCPOA Benefit Trust Fund |
Health Plan |
Hacking/IT Incident |
80,000 |
Ransomware Attack |
| Ascend Clinical, LLC |
Healthcare Provider |
Hacking/IT Incident |
77,443 |
Phishing and Ransomware Attack |
| Centerstone of Tennessee, Inc. |
Healthcare Provider |
Hacking/IT Incident |
50,965 |
Phishing Attack |
| Georgia Department of Human Services |
Healthcare Clearing House |
Hacking/IT Incident |
45,732 |
Phishing Attack |
| Connecticut Department of Social Services |
Health Plan |
Hacking/IT Incident |
37,000 |
Phishing Attack |
| State of North Dakota |
Healthcare Provider |
Hacking/IT Incident |
35,416 |
Phishing Attack |
| AdventHealth Shawnee Mission |
Healthcare Provider |
Hacking/IT Incident |
28,766 |
Blackbaud Ransomware |
Causes of October 2020 Healthcare Data Breaches
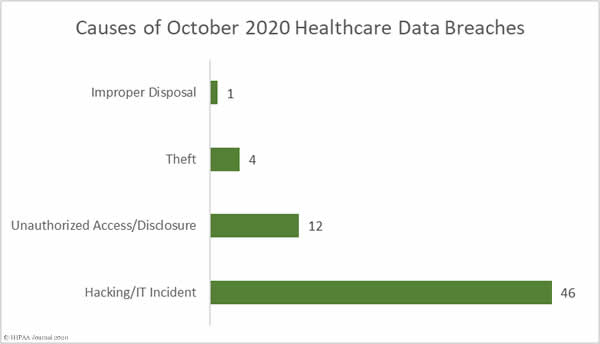
As the above table shows, the healthcare industry in the United States has faced a barrage of ransomware attacks. Two thirds of the largest 15 data breaches reported in October involved ransomware. CISA, the FBI, and the HHS issued a joint alert in October after credible evidence emerged indicating the Ryuk ransomware gang was targeting the healthcare industry, although that is not the only ransomware gang that is conducting attacks on the healthcare sector.
Phishing attacks continue to plague the healthcare industry. Phishing emails are often used to deliver Trojans such as Emotet and TrickBot, along with the Bazar Backdoor, which act as ransomware downloaders.
Phishing and ransomware attacks are classed as hacking/IT incidents on the HHS breach portal. In total there were 46 hacking/IT incidents reported to the HHS’ Office for Civil Rights in October – 73% of all reported breaches in October – and 2,450,645 records were breached in those incidents – 97.39% of all records breached in the month. The mean breach size was 53,275 records and the median breach size was 13,069 records.
There were 12 unauthorized access/disclosure incidents reported in October involving 54,862 healthcare records. The mean breach size was 4,572 records and the median breach size was 1,731 records. There were 4 reported cases of theft of paperwork or electronic devices containing PHI. The mean breach size was 4,290 records and the median breach size was 1,293 records. One incident was reported that involved the improper disposal of computer equipment that contained the ePHI of 4,290 individuals.
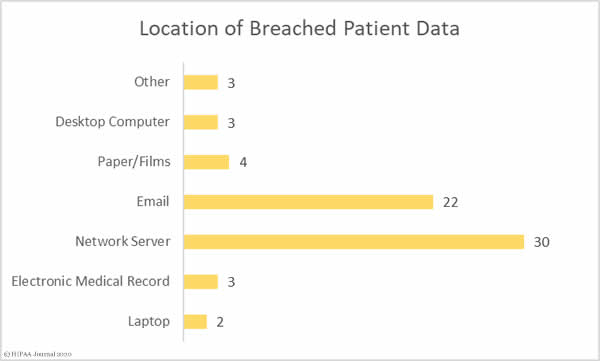
The graph below shows where the breached records were located. The high number of network server incidents shows the extent to which malware and ransomware was used in attacks. Almost a third of the attacks involved ePHI stored in email accounts, most of which were phishing attacks. Several breaches involved ePHI stored in more than one location.
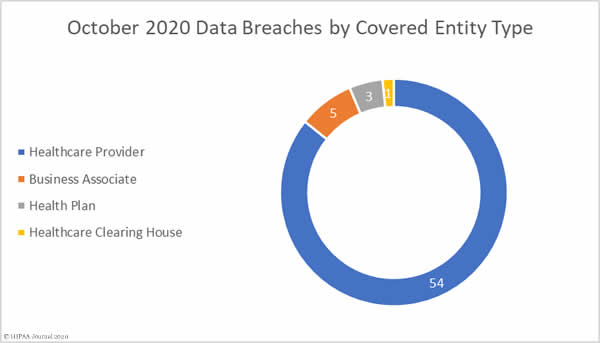
Healthcare Data Breaches by Covered Entity Type
Healthcare providers were the worst affected covered entity type in October with 54 breaches reported, followed by health plans with 3 breaches and one breach at a healthcare clearinghouse. While there were only 5 data breaches reported by business associates of covered entities, business associates were involved in 23 data breaches in October, with 18 of the incidents being reported by the affected covered entity.
Healthcare Data Breaches by State
October’s 63 data breaches were spread across 27 states. Connecticut was the worst affected state with 7 breaches, followed by California and Texas with 5 each, Florida, Ohio, Pennsylvania, and Virginia with 4 apiece, Iowa and Washington with 3, and Arkansas, Michigan, New Mexico, New York, Tennessee, and Wisconsin with 2. A single breach was reported in each of Georgia, Hawaii, Illinois, Indiana, Kansas, Louisiana, Maine, Minnesota, Missouri, North Dakota, New Jersey, and South Carolina.
HIPAA Enforcement Activity in October 2020
2020 has seen more financial penalties imposed on covered entities and business associates than any other year since the HIPAA Enforcement Rule gave OCR the authority to issue financial penalties for noncompliance. Up to October 30, 2020, OCR has announced 15 settlements to resolve HIPAA violation cases, including 4 financial penalties in October.
The health insurer Aetna paid a $1,000,000 penalty to resolve multiple HIPAA violations that contributed to the exposure of HIV medication information in a mailing. OCR investigators found issues with the technical and nontechnical evaluation in response to environmental or operational changes affecting the security of PHI, an identity check failure, a minimum necessary information failure, insufficient administrative, technical, and physical safeguards, and an impermissible disclosure of the PhI of 18,849 individuals.
The City of New Haven, CT paid a $202,400 penalty to resolve its HIPAA case with OCR that stemmed from a failure to promptly restrict access to systems containing ePHI following the termination of an employee. That failure resulted in an impermissible disclosure of the ePHI of 498 individuals. OCR also determined there had been a risk analysis failure and a failure to issue unique IDs to allow system activity to be tracked.
Two of the penalties were issued as part of OCR’s HIPAA Right of Access enforcement initiative, with the fines imposed for the failure to provide patients with timely access to their medical records at a reasonable cost. Dignity Health, dba St. Joseph’s Hospital and Medical Center, settled its case with OCR and paid a $160,000 penalty and NY Spine settled for $100,000.
State attorneys general also play a role in the enforcement of HIPAA compliance. October saw Franklin, TN-based Community Health Systems and its subsidiary CHSPCS LLC settle a multi-state action related to a breach of the ePHI of 6.1 million individuals in 2014. The investigators determined there had been a failure to implement and maintain reasonable security practices. The case was settled for $5 million.
The post October 2020 Healthcare Data Breach Report appeared first on HIPAA Journal.




