March 2020 saw a 7.69% month-over-month decrease in the number of reported healthcare data breaches and a 45.88% reduction in the number of breached records.
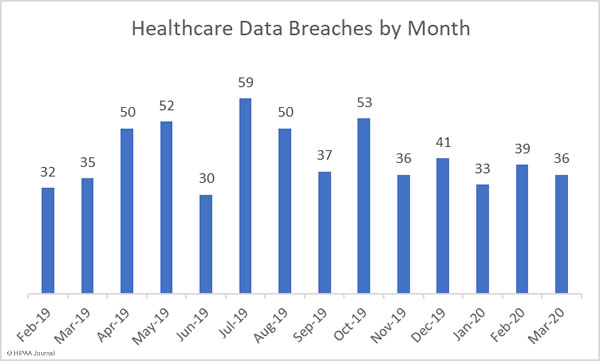
In March, 36 healthcare data breaches of 500 or more records were reported to the HHS’ Office for Civil Rights (OCR), which is more than 16% fewer than the average number of monthly breaches over the past 12 months. 828,921 healthcare records were breached in March, which is 194% higher than the monthly average number of breached records.
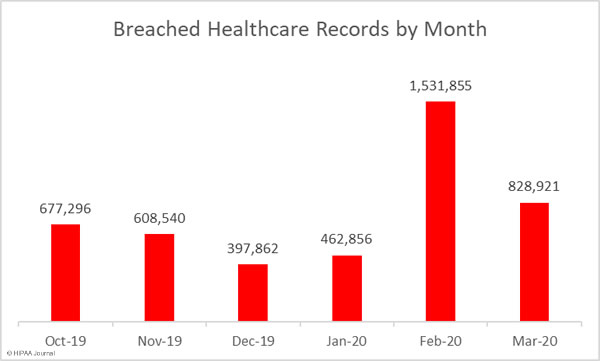
Largest Healthcare Data Breaches in March 2020
The largest healthcare data breach of the month was reported by the genetic testing company, Ambry Genetics Corporation. An unauthorized individual gained access to an employee’s email account that contained the data of 232,772 patients.
A major phishing attack was reported by the medical device manufacturer Tandem Diabetes Care. Several employees’ email accounts were compromised and the protected health information of 140,781 patients was exposed.
The third largest data breach of the month was reported by Brandywine Urology Consultants, which experienced a ransomware attack in which the data of 131,825 patients was potentially compromised. Affordacare Urgent Care Clinics and the Randleman Eye Center were also attacked with ransomware.
The data breaches reported by Golden Valley Health Centers, the Otis R. Bowen Center for Human Services, and Washington University School of Medicine were due to phishing attacks, the Stephan C Dean breach was an email hacking incident not believed to be a phishing attack, and the OneDigital Health and Benefits breach involved the theft of a laptop computer.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| Ambry Genetics Corporation |
Healthcare Provider |
232772 |
Hacking/IT Incident |
| Tandem Diabetes Care, Inc. |
Healthcare Provider |
140781 |
Hacking/IT Incident |
| Brandywine Urology Consultants, PA |
Healthcare Provider |
131825 |
Hacking/IT Incident |
| Stephan C Dean |
Business Associate |
70000 |
Hacking/IT Incident |
| Affordacare Urgent Care Clinics |
Healthcare Provider |
57411 |
Hacking/IT Incident |
| Golden Valley Health Centers |
Healthcare Provider |
39700 |
Hacking/IT Incident |
| Otis R. Bowen Center for Human Services |
Healthcare Provider |
35804 |
Hacking/IT Incident |
| OneDigital Health and Benefits |
Business Associate |
22894 |
Theft |
| Randleman Eye Center |
Healthcare Provider |
19556 |
Hacking/IT Incident |
| Washington University School of Medicine |
Healthcare Provider |
14795 |
Hacking/IT Incident |
Causes of March 2020 Healthcare Data Breaches
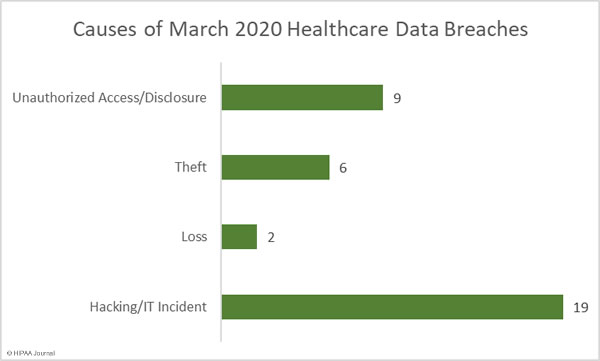
Hacking/IT incidents dominated the breach reports once again, accounting for 52.78% of the month’s breaches (19 incidents) and 94.38% of all records breached in March (782,407 records). The average breach size was 41,179 records and the median breach size was 10,700 records.
Unauthorized access/disclosure incidents accounted for 25% of the month’s breaches (9 incidents) and 1.81% of breached records (15,071 records). The average breach size was 1,674 records and the median breach size was 910 records.
16.66% of the month’s breaches were due to the theft of paperwork/electronic devices (6 incidents). 30,107 patient records were stolen in those incidents, which account for 3.63% of the breached records in March. The average breach size was 5,017 records and the median breach size was 1,595 records. There were two loss incidents reported in March involving 1,336 records.
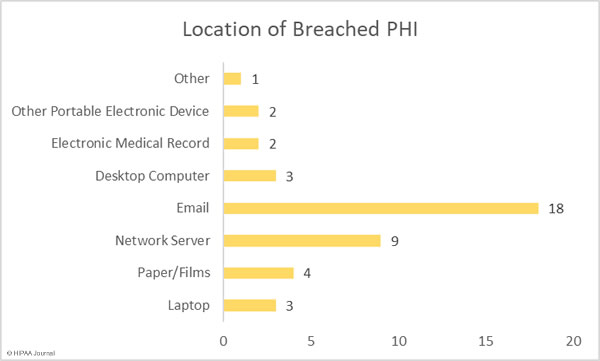
The bar chart below shows the location of the breached protected health information and clearly indicates the biggest problem area for healthcare providers – Securing email accounts and preventing phishing attacks. 50% of the breaches in March saw email accounts breached, the vast majority of which were the result of responses to phishing emails.
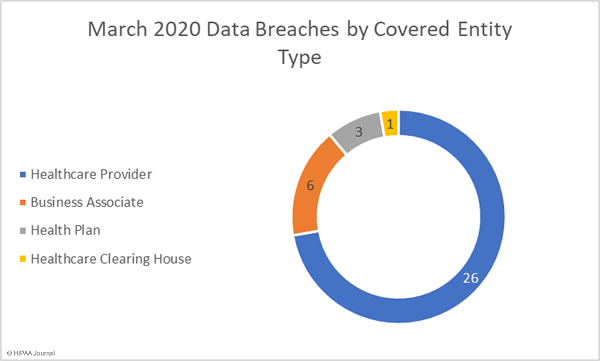
March 2020 Data Breaches by Covered Entity Type
Healthcare providers were the worst affected covered entity type with 26 reported breaches. There were 3 breaches reported by health plans and a rare breach at a healthcare clearinghouse.
Business associates of HIPAA covered entities reported 6 breaches and a further two breaches were reported by the covered entity but had some business associate involvement.
States Affected by March 2020 Data Breaches
March’s 36 data breaches were spread across 22 states. California was the worst affected with 7 reported breaches. There were three breaches in Georgia and Minnesota, two in each of Hawaii, North Carolina, Pennsylvania, and Texas, and one breach in each of Arizona, Colorado, Delaware, Florida, Illinois, Indiana, Massachusetts, Maryland, Missouri, Montana, New Jersey, Nevada, Ohio, Utah, and Virginia.
HIPAA Enforcement in March 2020
There were no reported enforcement actions by the HHS’ Office for Civil Rights or state attorneys general in March 2020 but there was some major news on the HIPAA enforcement front.
In response to the SARS-CoV-2 Novel Coronavirus pandemic, OCR announced it is exercising enforcement discretion and will not be imposing financial penalties on covered entities and business associates for noncompliance with certain aspects of HIPAA Rules.
Three Notices of Enforcement Discretion were announced by OCR in March related to the good faith provision of telehealth services, uses and disclosures of PHI by business associates to public health authorities, and good faith participation in the operation of COVID-19 testing centers.
Further information on the Notices of Enforcement Discretion, HIPAA, and COVID-19 can be found on this link.
The post March 2020 Healthcare Data Breach Report appeared first on HIPAA Journal.




