In January, healthcare data breaches of 500 or more records were reported to the Department of Health and Human Services’ Office for Civil Rights at a rate of more than one a day.
As our 2019 Healthcare Data Breach Report showed, 2019 was a particularly bad year for healthcare data breaches with 510 data breaches reported by HIPAA-covered entities and their business associates. That equates to a rate of 42.5 data breaches per month. January’s figures are an improvement, with a reporting rate of 1.03 breaches per day. There was also a 15.78% decrease in reported breaches compared to December 2019.
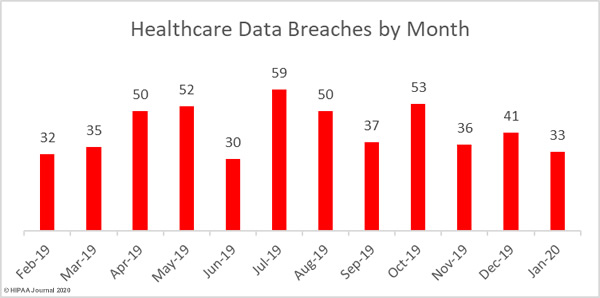
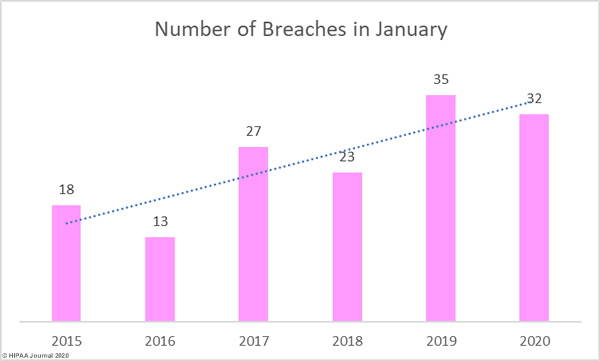
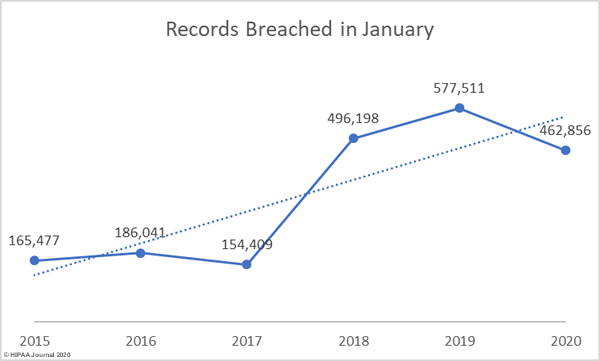
While the number of breaches was down, the number of breached records increased by 17.71% month-over-month. 462,856 healthcare records were exposed, stolen, or impermissibly disclosed across 32 reported data breaches. As the graph below shows, the severity of data breaches has increased in recent years.
Largest Healthcare Data Breaches in January 2020
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Location of Breached Information |
| PIH Health |
CA |
Healthcare Provider |
199,548 |
Hacking/IT Incident |
Email |
| Douglas County Hospital d/b/a Alomere Health |
MN |
Healthcare Provider |
49,351 |
Hacking/IT Incident |
Email |
| InterMed, PA |
ME |
Healthcare Provider |
33,000 |
Hacking/IT Incident |
Email |
| Fondren Orthopedic Group L.L.P. |
TX |
Healthcare Provider |
30,049 |
Hacking/IT Incident |
Network Server |
| Native American Rehabilitation Association of the Northwest, Inc. |
OR |
Healthcare Provider |
25,187 |
Hacking/IT Incident |
Email |
| Central Kansas Orthopedic Group, LLC |
KS |
Healthcare Provider |
17,214 |
Hacking/IT Incident |
Network Server |
| Hospital Sisters Health System |
IL |
Healthcare Provider |
16,167 |
Hacking/IT Incident |
Email |
| Spectrum Healthcare Partners |
ME |
Healthcare Provider |
11,308 |
Hacking/IT Incident |
Email |
| Original Medicare |
MD |
Health Plan |
9,965 |
Unauthorized Access/Disclosure |
Other |
| Lawrenceville Internal Medicine Assoc, LLC |
NJ |
Healthcare Provider |
8,031 |
Unauthorized Access/Disclosure |
Email |
Causes of January 2020 Healthcare Data Breaches
2019 saw a major increase in healthcare data breaches caused by hacking/IT incidents. In 2019, more than 59% of data breaches reported to the HHS’ Office for Civil Rights were the result of hacking, malware, ransomware, phishing attacks, and other IT security breaches.
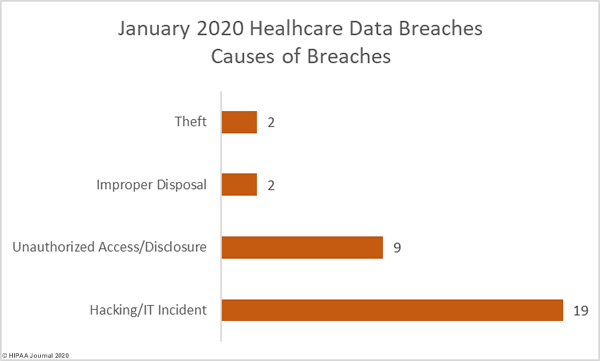
Hacking/IT incidents continued to dominate the breach reports in January and accounted for 59.38% of all breaches reported (19 incidents). 28.13% of reported breaches were classified as unauthorized access/disclosure data breaches (9 incidents), there were two reported theft incidents, both involving physical records, and 2 cases of improper disposal of physical records. Ransomware attacks continue to plague the healthcare industry, but phishing attacks are by far the biggest cause of healthcare data breaches. As the above table shows, these attacks can see the PHI of tens of thousands or even hundreds of thousands of patients exposed or stolen.
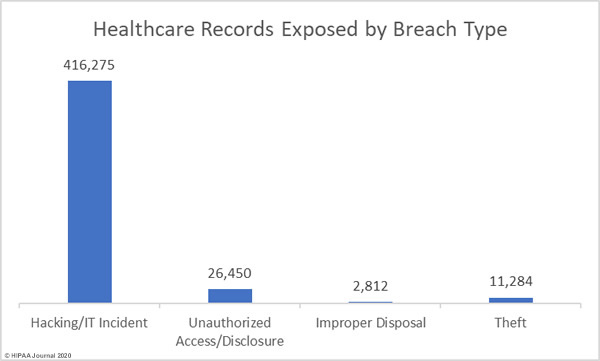
Hacking/IT incidents tend to be the most damaging type of breach and involve more healthcare records than other breach types. In January, 416,275 records were breached in hacking/IT incidents. The average breach size was 21,909 records and the median breach size was 6,524 records. 26,450 records were breaches as a result of unauthorized access/disclosure incidents. The average breach size was 26,450 records and the median breach size was 2,939 records.
11,284 records were stolen in theft incidents with an average breach size of 5,642 records. The two improper disposal incidents saw 2,812 records discarded without first rendering documents unreadable and undecipherable. The average breach size was 1,406 records.
Regular security awareness training for employees has been shown to reduce susceptibility to phishing attacks, but threat actors are conducting increasingly sophisticated attacks. It is often hard to distinguish a phishing email from a genuine message, especially in the case of business email compromise scams.
What is needed to block these attacks is a defense in depth approach and no one technical solution will be effective at blocking all phishing attacks. Defenses should include an advanced spam filter to block phishing messages at source, a web filter to block access to websites hosting phishing kits, DMARC to identify email impersonation attacks, and multi-factor authentication to prevent compromised credentials from being used to access email accounts.
Healthcare Data Breaches by Covered Entity
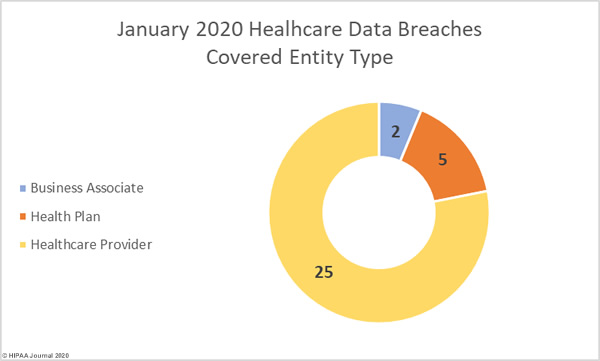
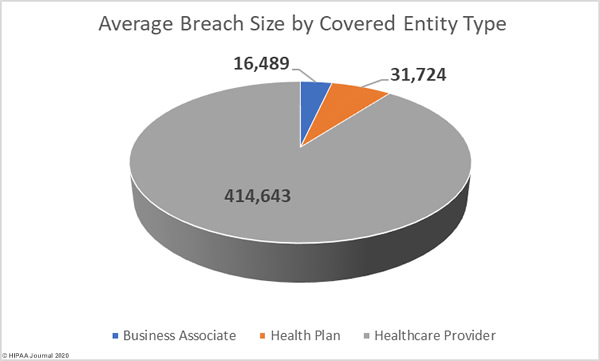
Healthcare providers were the worst affected by data breaches in January with 25 reported breaches of 500 or more healthcare records. Five breaches were reported by health plans, and two breaches were reported by business associates of HIPAA-covered entities. There were a further three data breaches reported by covered entities that had some business associate involvement.
Healthcare Data Breaches by State
HIPAA covered entities and business associates in 23 states reported data breaches in January. California and Texas were the worst affected with three reported breaches in each state. There were two breaches reported in each of Florida, Illinois, Maine, Minnesota, and New York, and one breach was reported in each of Alabama, Arizona, Colorado, Connecticut, Georgia, Iowa, Indiana, Kansas, Maryland, Michigan, North Carolina, New Jersey, Oregon, Pennsylvania, South Carolina, and Virginia.
HIPAA Enforcement in January 2020
There were no financial penalties imposed on HIPAA covered entities or business associates by the HHS’ Office for Civil Rights or state attorneys general in January.
There was a notable increase in the number of lawsuits filed against healthcare organizations that have experienced data breaches related to phishing and ransomware attacks.
January saw a lawsuit filed against Health Quest over a July 2018 phishing attack, Tidelands Health is being sued over a December 2019 ransomware attack, and a second lawsuit was filed against DCH Health System over a malware attack involving the Emotet and TrickBot Trojans that occurred in October 2019. These lawsuits follow legal action against Kalispell Regional Healthcare and Solara Medical Supplies in December.
The trend has continued in February with several law firms racing to be the first to file lawsuits against PIH Health in California over a 2019 phishing attack that exposed the data of more than 200,000 individuals.
These lawsuits may cite HIPAA violations, but since there is no private cause of action under HIPAA, legal action is taken over violations of state laws.
The post January 2020 Healthcare Data Breach Report appeared first on HIPAA Journal.







