There were 38 healthcare data breaches of 500 or more records reported to the Department of Health and Human Services’ Office for Civil Rights in December 2019, an increase of 8.57% from November 2019.
While the number of breaches increased, there was a major reduction in the number of exposed healthcare records, falling from 607,728 records in November 2019 to 393,189 records in December 2019 – A drop of 35.30%. In December the mean breach size was 10,347 records and the median breach size was 3,650 records.
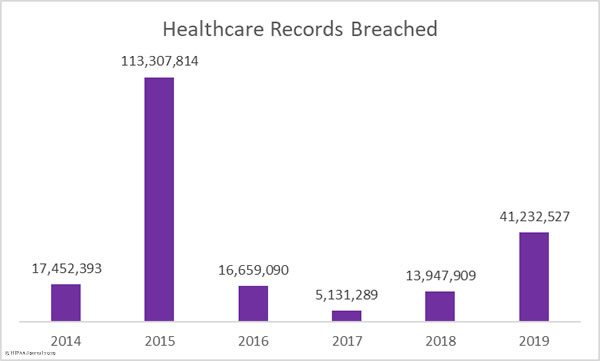
It has been a particularly bad year for healthcare data breaches. 2019 was the second worst ever year for healthcare data breaches in terms of the number of patients impacted by breaches. 41,232,527 healthcare records were exposed, stolen, or impermissibly disclosed in 2019. That’s 195.61% more than 2018. More healthcare records were breached in 2019 than in the previous three years combined.
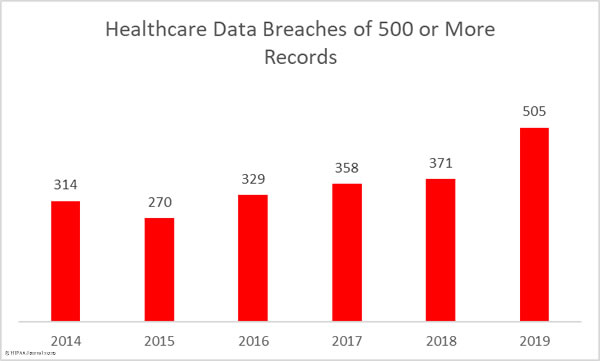
The number of reported data breaches also increased 36.12% year-over-year, from 371 breaches in 2018 to 505 breaches in 2019. That makes 2019 the worst every year in terms of the number of reported healthcare data breaches.
Largest Healthcare Data Breaches in December 2019
The largest healthcare data breach reported in December affected Truman Medical Center in Kansas City, MO and involved the protected health information of 114,466 patients. The records were stored on a company-owned laptop computer that was stolen from the vehicle of an employee. The laptop was password-protected but was not encrypted.
8 of the top 10 breaches in December were hacking/IT incidents. The Adventist Health Simi Valley, Healthcare Administrative Partners, Cheyenne Regional Medical Center, SEES Group, and Sinai Health System breaches were due to phishing attacks. Roosevelt General Hospital discovered malware on an imaging server and Children’s Choice Pediatrics experienced a ransomware attack.
The Colorado Department of Human Services breach was due to a coding error on a mailing and Texas Family Psychology Associates discovered an unauthorized individual had accessed its electronic medical record system.
| Name of Covered Entity |
Covered Entity Type |
Type of Breach |
Individuals Affected |
| Truman Medical Center, Incorporated |
Healthcare Provider |
Theft |
114,466 |
| Adventist Health Simi Valley |
Healthcare Provider |
Hacking/IT Incident |
62,000 |
| Roosevelt General Hospital |
Healthcare Provider |
Hacking/IT Incident |
28,847 |
| Healthcare Administrative Partners |
Business Associate |
Hacking/IT Incident |
17,693 |
| Cheyenne Regional Medical Center |
Healthcare Provider |
Hacking/IT Incident |
17,549 |
| SEES Group, LLC |
Healthcare Provider |
Hacking/IT Incident |
13,000 |
| PediHEalth, PLLC, dba Children’s Choice Pediatrics |
Healthcare Provider |
Hacking/IT Incident |
12,689 |
| Sinai Health System |
Healthcare Provider |
Hacking/IT Incident |
12,578 |
| Colorado Department of Human Services |
Healthcare Provider |
Hacking/IT Incident |
12,230 |
| Texas Family Psychology Associates, P.C. |
Healthcare Provider |
Unauthorized Access/Disclosure |
12,000 |
Entities Affected by December 2019 Healthcare Data Breaches
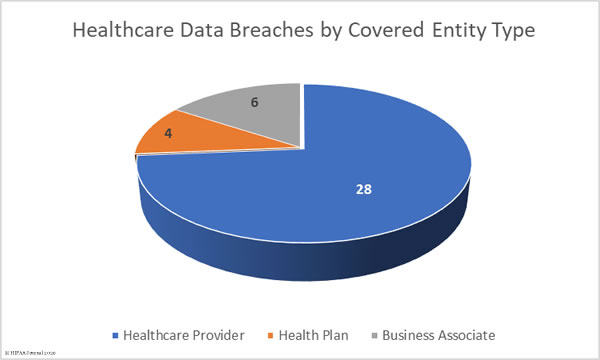
28 healthcare providers reported breaches of 500 or more healthcare records in December. Four health plans were affected by data breaches and 6 business associates of covered entities reported a breach. One additional breach had some business associate involvement, but the breach was reported by the covered entity.
Causes of December 2019 Healthcare Data Breaches
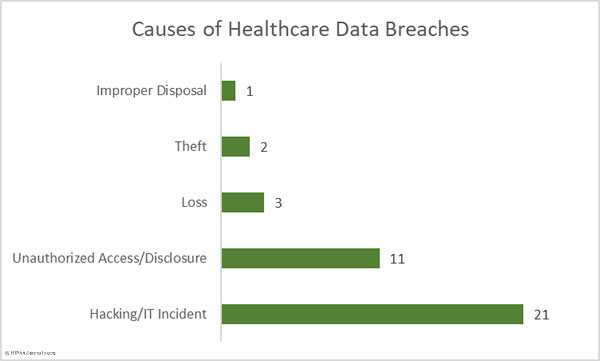
There were 21 hacking/IT incidents reported by HIPAA-covered entities and business associates in December. 226,774 healthcare records were exposed or stolen in those incidents. The mean breach size was 10,798 records and the median breach size was 5,991 records. The incidents mostly consisted of phishing attacks, ransomware and malware infections, and coding errors.
There were 11 cases of unauthorized accessing of healthcare data and impermissible disclosures of protected health information due to a mix of insider errors and malicious actions by employees. These incidents involved 46,364 healthcare records. The mean breach size was 4,214 records and the median breach size was 3,500 records.
There were two theft incidents reported and three incidents involving lost electronic devices and paperwork containing protected health information. 118,877 records were lost or stolen in those incidents. The mean breach size was 23,775 records and the median breach size was 1,100 records. There was also one case of incorrect disposal of paperwork involving documents containing the PHI of 1,174 patients.
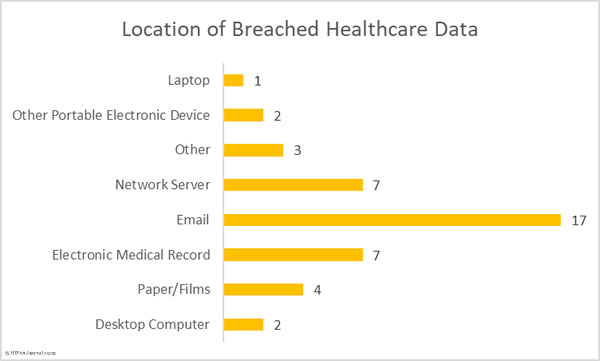
Location of Breached Protected Health Information
The chart below clearly indicates the difficulty healthcare organizations have securing their email systems and protecting them against unauthorized access. The majority of the email incidents in December 2019 were phishing attacks in which unauthorized individuals obtained the login credentials of employees and used them to remotely access their email accounts.
Email security solutions can block the majority of phishing and malware-laced emails, but some phishing emails will slip through the net. It is therefore important – and a requirement of HIPAA – to provide regular security awareness training to employees to help them identify malicious emails. Multi-factor authentication should also be implemented. In the event to email credentials being obtained by unauthorized individuals, in the vast majority of cases, MFA will prevent those credentials from being used to remotely access email accounts.
December 2019 Healthcare Data Breaches by State
December data breaches were reported by HIPAA-covered entities and business associates in 22 states and the District of Columbia. Texas was the worst affected with 4 breaches, 4 breaches were reported by entities based in California and Illinois, Florida experienced 3 breaches, and two breaches were reported by entities based in Colorado, Georgia, and Tennessee.
A single breach was reported by entities based in Alaska, Connecticut, Louisiana, Maryland, Michigan, Missouri, New Mexico, New York, Ohio, Oklahoma, Pennsylvania, North Carolina, South Carolina, Washington, Wyoming, and District of Columbia.
HIPAA Enforcement Activity in December 2019
The Department of Health and Human Services’ Office for Civil Right closed December with two further enforcement actions against covered entities that were discovered to have violated the HIPAA Rules.
The first financial penalty of the month to be announced was a settlement with Korunda Medical LLC. This was the second financial penalty imposed on a HIPAA-covered entity under OCR’s HIPAA Right of Access Initiative. OCR investigated Korunda Medical following receipt of a complaint from a patient who had not been provided with a copy of her medical records. OCR issued technical assistance, but a further patient submitted a similar complaint a few days later and a financial penalty was determined to be appropriate. Korunda Medical settled the case for $85,000.
The second penalty was imposed on West Georgia Ambulance for multiple violations of HIPAA Rules. OCR launched an investigation following receipt of a breach notification about the loss of an unencrypted laptop computer. OCR discovered longstanding noncompliance with several aspects of the HIPAA Rules. A risk analysis had not been conducted, there was no security awareness training program for employees, and West Georgia Ambulance had failed to implement HIPAA Security Rule policies and procedures. West Georgia Ambulance settled the case for $65,000.
2019 HIPAA Enforcement Actions
In total, there were 10 financial penalties were imposed on covered entities and business associates in 2019, comprising 2 Civil Monetary Penalties and 8 settlements totaling $12,274,000.
| Entity |
Penalty |
Penalty Type |
| West Georgia Ambulance |
$65,000 |
Settlement |
| Korunda Medical, LLC |
$85,000 |
Settlement |
| Sentara Hospitals |
$2,175,000 |
Settlement |
| Texas Department of Aging and Disability Services |
$1,600,000 |
Civil Monetary Penalty |
| University of Rochester Medical Center |
$3,000,000 |
Settlement |
| Jackson Health System |
$2,154,000 |
Civil Monetary Penalty |
| Elite Dental Associates |
$10,000 |
Settlement |
| Bayfront Health St Petersburg |
$85,000 |
Settlement |
| Medical Informatics Engineering |
$100,000 |
Settlement |
| Touchstone Medical imaging |
$3,000,000 |
Settlement |
Figures for this report were calculated from the U.S. Department of Health and Human Services’ Office for Civil Rights Research Report on January 21, 2020.
The post December 2019 Healthcare Data Breach Report appeared first on HIPAA Journal.




