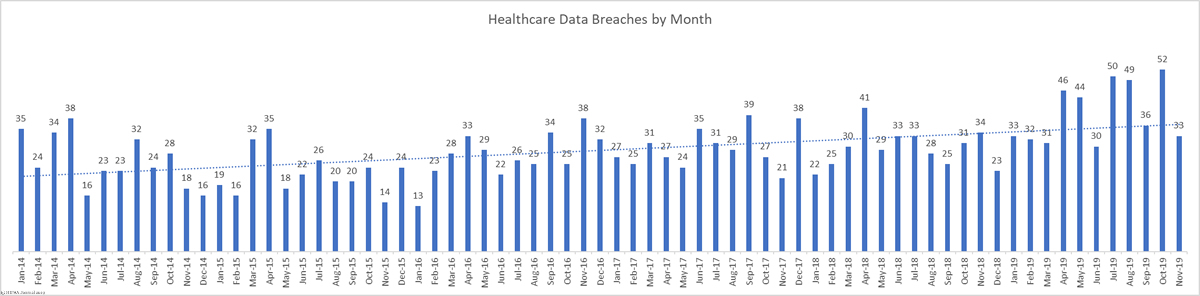
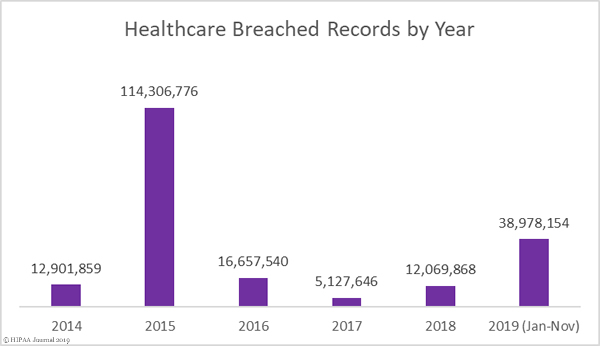
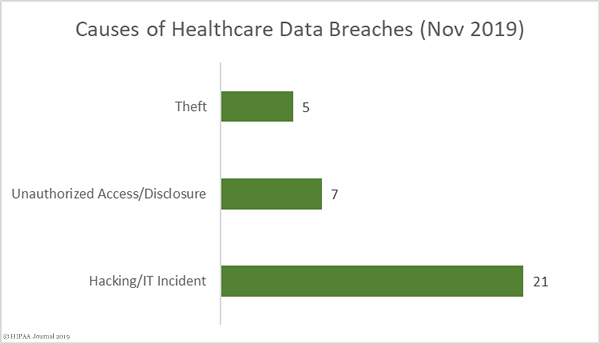
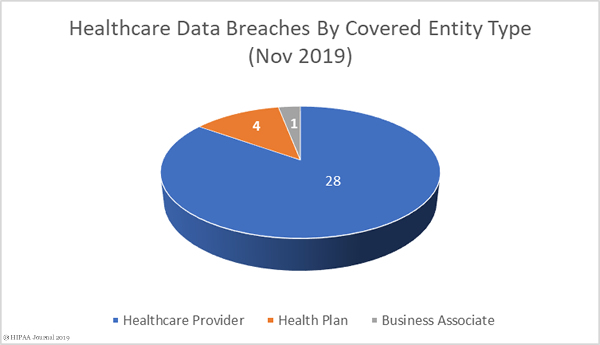
It is becoming increasingly common for threat actors to use ransomware to encrypt files to prevent data access, but also to steal data and threaten to publish or sell on the stolen data if the ransom is not paid. This new tactic is intended to increase the likelihood of victims paying the ransom.
The Center for Facial Restoration in Miramar, FL, is one of the latest healthcare providers to experience such an attack. Richard E. Davis MD FACS of The Center for Facial Restoration received a ransom demand on November 8, 2019 informing him that his clinic’s server had been breached and data had been stolen. The attacker said the data could be publicly exposed or traded with third parties if the ransom was not paid.
Dr. Davis filed a complaint with the FBI’s Cyber Crimes Center and met with the FBI agents investigating the attack. After the attack occurred, Dr. Davis was contacted by around 15-20 patients who had also been contacted by the attacker and issued with a ransom demand. The patients were told that their photographs and personal data would be published if the ransom demand was not paid.
According to Dr. Davis’s substitute breach notice, the compromised server contained the data of approximately 3,600 patients. While it is possible the attackers stole the files of all patients, there are reasons to suspect only a very small number of patient photographs and personal data may have been stolen.
It has taken some time to determine which patients have been affected as much of the information held on patients was stored as scanned patient intake forms rather than a database. Each file had to be opened and checked manually and that was a painstakingly slow and labor intensive process.
The types of data exposed was limited to photocopies of driver’s licenses or passports, home addresses, email addresses, telephone numbers, insurance policy numbers, and credit card numbers, most of which only showed the last 4 digits.
All patients potentially affected by the attack have now been notified and steps have been taken to improve security, including replacing all hard drives and implementing new firewalls and anti-malware software. The ransom demand was not paid.
Children’s Choice Pediatrics Ransomware Attack Impacts 12,689 Patients
Children’s Choice Pediatrics in McKinney, TX, is notifying 12,689 patents that some of their protected health information may have been accessed by unauthorized individuals who used ransomware to try to extort money from the practice.
The attack occurred on or around October 27, 2019 and resulted in the encryption of data on its network. Children’s Choice had backed up all data and attempts were made to recover all files encrypted by the ransomware. That process has been completed, but it was not possible to restore all patient data. Some patient records could not be recovered.
Affected patients have been advised to be alert to the possibility of data misuse and to monitor their account statements for signs of fraudulent activity. No reports have been received to suggest any patient data was stolen or has been misused. Children’s Choice has now strengthened security to prevent similar attacks from occurring in the future.
The post Ransomware Attacks Reported by Florida and Texas Healthcare Providers appeared first on HIPAA Journal.