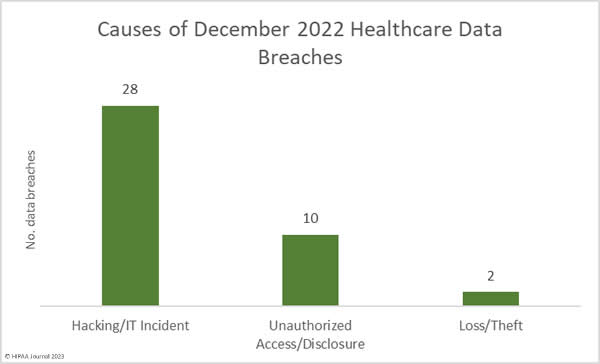
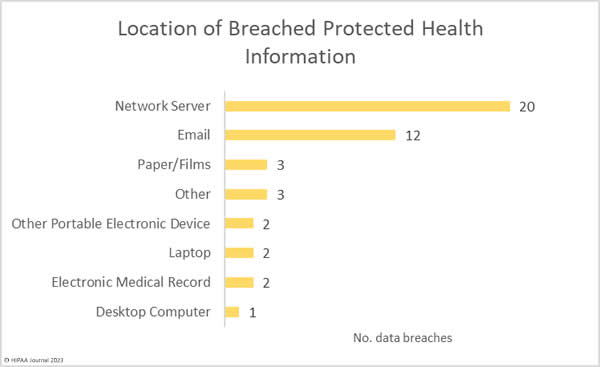
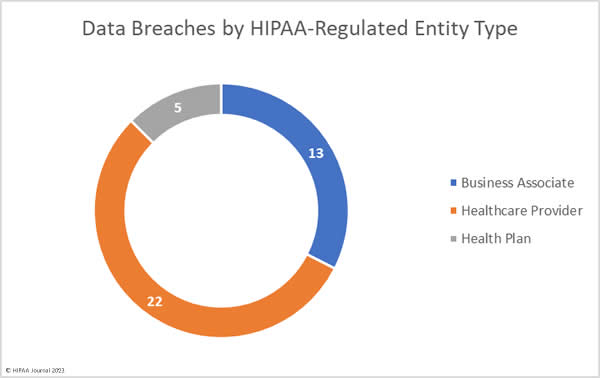
West Oaks Eyecare – Ransomware Attack
West Oaks Eyecare in Texas has notified 1,045 Texas residents that a malicious actor gained access to its network and installed malware that rendered files inaccessible. The attack was detected on November 7, 2022, and steps were taken to contain the attack and secure its systems. The affected system contained billing information that was potentially accessed and obtained in the attack. The files included patients’ names along with one or more of the following types of information: address, date of birth, email address, phone number, patient ID number, Social Security number, optical scan images, exam results, insurance information, and billing information.
Notification letters were mailed to affected individuals on January 6, 2022. Complimentary credit monitoring and identity protection services have been offered to individuals whose Social Security numbers were involved.
The Kelberman Center – Email Account Breach
The Kelberman Center, a Utica, NY-based provider of services to individuals with autism, has notified 3,501 patients about a breach of employee email accounts. Suspicious activity was detected within its email environment on November 1, 2022, with the investigation confirming that a single email account had been accessed by an unauthorized individual between October 21 and November 3, during which time emails and attachments may have been accessed or acquired.
A third-party digital forensics expert was engaged to investigate the breach and review system security and confirmed that no other systems had been accessed. A review of the email account confirmed the following types of information had been exposed: names, dates of birth, diagnoses, treatment information, and provider information. A very limited number of individuals had other information exposed and were notified if that was the case. Notifications were mailed to affected individuals on December 30, 2022.
Quality Behavioral Health – Hacked Network Server
Quality Behavioral Health in Washington has recently reported a hacking incident to the HHS’ Office for Civil Rights that has affected 500 individuals – a number often used as a placeholder until the full extent of a data breach is known in order to meet the HIPAA Breach Notification Rule reporting requirements.
The cyberattack was detected on November 26, 2022, and steps were immediately taken to secure its network and prevent further unauthorized access. An investigation was launched to determine the nature and scope of the breach and the extent to which patient data was involved. That investigation and file review are ongoing, but it has been confirmed that its network was subject to unauthorized access between November 24 and November 26, 2022.
The exposed information included names, contact information, demographic information, Social Security numbers, driver’s license numbers, state identification card numbers, financial account information, birth dates, student, military, or passport identification numbers, health insurance information, medical histories, mental or physical conditions, medical diagnoses, and treatment information.
St. Rose Hospital – Hacking Incident with Data Theft Confirmed
St. Rose Hospital in Hayward, CA, has recently confirmed that a malicious actor gained access to its network and exfiltrated files containing patient information. Suspicious activity was detected in its computer systems on November 29, 2022, and third-party digital forensics specialists were engaged to investigate the breach. The investigation confirmed that its network was first accessed on November 18, 2022, and data theft occurred around that time.
The review of all files potentially accessed or copied revealed they contained names, Social Security numbers, dates of birth, e-mail addresses, and home addresses. St. Rose Hospital said it is unaware of any misuse of patient information, although databreaches.net has reported that data potentially related to the attack has been included in a dataset on a hacking forum. St. Rose Hospital has offered complimentary credit monitoring services to affected individuals.
Mindpath Health – Email System Breach
Community Psychiatry Management, doing business as Mindpath Health, has recently notified certain patients about a breach of its email system. Suspicious activity was identified within its email environment during a routine security audit. Third-party forensics experts were engaged to investigate the security breach and confirmed that two employee email accounts had been compromised, one in March 2022 and the other in June 2022. The forensic investigation concluded on November 15, 2022, and confirmed that protected health information may have been accessed, including patient names, addresses, Social Security numbers, dates of birth, medical diagnoses, treatment information, health insurance information, and prescription information. Mindpath health said it is unaware of any actual or attempted misuse of patient data.
Notification letters were sent to affected individuals on December 30, 2022. It is currently unclear how many individuals were affected.
Bay Bridge Administrators – Hacking Incident
Bay Bridge Administrators, an Austin, TX-based third-party administrator of insurance products, has recently announced that unauthorized individuals gained access to its network on or before August 25, 2022, and exfiltrated files on September 3, 2022.
The security breach was detected on September 5, 2022, when network disruption was experienced. Prompt action was taken to secure its network and investigate the breach, which revealed on December 5, 2022, that the stolen files included the personal information of individuals enrolled in certain employment insurance benefits that were administered by BBA for calendar year 2022. That information included names, addresses, Social Security numbers, driver’s license numbers, state identification card numbers, medical information, health insurance information, and/or dates of birth.
Affected individuals were notified on January 10, 2022, and have been offered 24 months of complimentary credit monitoring and identity protection services.
The post Round Up of Recent Hacking Incidents and Email Account Breaches appeared first on HIPAA Journal.