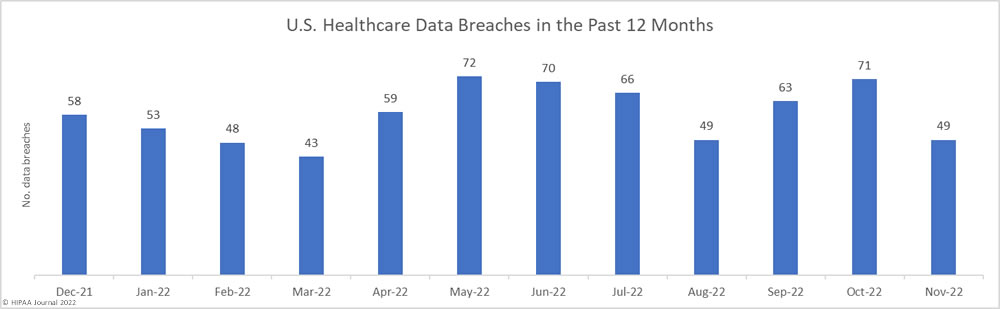
It has been another bad year for healthcare data breaches, with some of the biggest HIPAA breaches of 2022 resulting in the impermissible disclosure of well over a million records. While it does not currently look like last year’s record of 714 data breaches of 500+ records will be exceeded this year, with 674 data breaches reported up until December 22, 2022, any reduction is likely to be minimal. In addition to the high number of data breaches, 2022 stands out for the sheer number of healthcare records breached, which currently stands at 49.8 million records. That’s more than any other year to date apart from 2015 when Anthem Inc reported its 78.8 million-record data breach. In 2022, 12 data breaches were reported that exposed more than 1 million records, and a further 13 data breaches exposed between 500,000 and 1 million records.
The Biggest HIPAA Breaches of 2022
One notable observation from the biggest HIPAA breaches of 2022 is the number that occurred at business associates of HIPAA-covered entities. Many of these business associate data breaches affected dozens of healthcare clients, with one notable branch in the list below affecting 657 HIPAA-covered entities. Out of the 25 data breaches of 500,000 or more records, 52% occurred at business associates, including 60% of the 10 largest data breaches. The 12 biggest HIPAA breaches of 2022 affected almost 22.66 million patients and health plan members.
OneTouch Point – Ransomware Attack Involving 4.11 Million Records
On July 27, the mailing and printing vendor, OneTouchPoint (OTP), reported a hacking incident to the HHS’ Office for Civil Rights that affected more than one million individuals; however, as the investigation progressed it was determined that the breach was much more extensive than first thought, and had involved the protected health information of 4,112,892 individuals. Hackers had gained access to its network and used ransomware to encrypt files, with that information also potentially stolen in the attack. The compromised data included names, contact IDs, and information provided during health assessments. More than 35 of the company’s clients were affected, many of which were health plans.
Eye Care Leaders – Hacking Incident Involving at least 3.65 Million Records
Eye Care Leaders is a North Carolina provider of an electronic health record solution (myCare Integrity) to ophthalmology practices across the country. Affected providers started to be notified in March that hackers had gained access to its databases in December 2021. The databases contained extensive patient information, such as contact information, health insurance information, medical record numbers, Social Security numbers, driver’s license numbers, and medical information. As is relatively common in business associate data breaches, each affected healthcare provider reported the breach separately. Texas Tech University Health Sciences Center was one of the worst affected healthcare providers, with 1,290,104 records exposed. HIPAA Journal has tracked the reported data breaches and at least 41 eye care providers and 3,649,470 patients were affected.
Advocate Aurora Health – Impermissible Disclosure of up to 3 Million Records
On October 14, Wisconsin-based Advocate Aurora Health notified OCR about an impermissible disclosure of the protected health information of up to 3,000,000 patients. The disclosure occurred due to the addition of third-party tracking code on its websites, patient portals, and applications. The tracking code was used to gain insights into the use of its patient-facing digital services to improve the patient experience; however, the tracking code transmitted patient information to the developers of that code, including Meta (Facebook) and Google. The information transmitted was based on each user’s interactions and may have included health information that could be tied to individuals. The transmitted information may have included names, appointment dates/times, provider names, procedure types, insurance information, and communications through the MyChart patient portal. Advocate Aurora Health was not alone. Several health systems had used the code on their websites and transferred patient data to third parties without consent or a business associate agreement in place.
Connexin Software – Hacking Incident Involving 2.2 Million Records
Connexin Software is a Wisconsin-based provider of an electronic health record solution to pediatric practices across the country, operating as Office Practicum. A breach of its network was detected in August 2022, with the investigation confirming the hackers accessed and exfiltrated an offline set of data used for data conversion and troubleshooting. That data set included names, Social Security numbers, health insurance information, billing and/or claims data, and clinical information such as treatment information, procedures, diagnoses, and prescriptions. The breach was reported to OCR on November 11, as affecting 2,216,365 individuals. 119 pediatric practices were affected by the data breach.
Shields Health Care Group – Hacking Incident Involving 2 Million Records
Shields Healthcare Group is a Massachusetts-based vendor that provides MRI, PET/CT, radiation oncology, and surgical services. On May 27, Shields notified OCR about a breach that affected up to 2,000,000 patients from 60 healthcare practices. Hackers had gained access to its network, with the investigation confirming files containing patient data were exfiltrated over two weeks in March. The stolen data included names, contact information Social Security numbers, insurance information, billing information, and clinical information such as diagnoses and treatment information.
Professional Finance Company – Ransomware Attack Involving 1.92 Million Records
Professional Finance Company is a Colorado-based vendor that provides debt recovery services. On February 26, the company detected and stopped what it described as a sophisticated ransomware attack, in which certain systems were accessed by the attackers and disabled. The forensic investigation revealed the attackers had access to files containing names, addresses, accounts receivable balances, information regarding payments made to accounts, Social Security numbers, health insurance information, and medical treatment information. The breach was reported to OCR on July 1 as affecting 1,918,941 patients at 657 of its healthcare provider clients.
Baptist Medical Center – Malware Infection Involving 1.6 Million Records
Baptist Medical Center and Resolute Health Hospital in Texas were affected by a security breach that was detected on April 20. Malicious code was detected on its network that allowed hackers to exfiltrate patient data. The investigation into the breach determined the hackers first gained access to its network in late March. The analysis of the affected files revealed they contained protected health information such as names, Social Security numbers, health insurance information, medical record numbers, diagnosis information, and billing and claims information. The breach was reported to OCR on June 15 as affecting 1,608,549 patients of Baptist Medical Center and 54,209 Resolute Health Hospital patients.
Community Health Network – Impermissible Disclosure of up to 1.5 Million Records
The Indiana-based healthcare provider, Community Health Network, notified OCR on November 18 about the impermissible disclosure of the protected health information of up to 1,500,000 individuals. Third-party tracking code from Meta and Google had been added to its websites to provide insights that would allow the improvement of access to information about critical care services and its patient-facing websites. Community Health Network was unaware that adding the code to its websites would result in identifiable health information being transmitted to Meta and Google. The data transferred included IP addresses, appointment information, patient, portal communications, procedure types, and other information based on the interactions of users on its website.
Novant Health – Impermissible Disclosure of up to 1.36 Million records
The North Carolina-based healthcare provider, Novant Health, notified OCR on August 14 about an impermissible disclosure of the protected health information of 1,362,296 individuals. The notification was issued on behalf of Novant Health ACE, a contractor for NMG Services Inc. Novant Health was the first HIPAA-regulated entity to notify OCR about a HIPAA violation related to the use of third-party tracking technologies on its website. Novant Health said the tracking code had been misconfigured, which allowed patient information to be sent to Meta such as names, appointment types and dates, provider names, button/menu selection details that may have included information about health conditions, and information submitted by patients in free text boxes.
Broward Health – Hacking Incident Involving 1.35 Million Records
The Florida-based healthcare provider, Broward Health, reported a breach of the PHI of 1,351,431 patients to OCR on January 2, which was the result of hackers gaining access to its network in October 2021. The delay in reporting was at the request of the Department of Justice, so as not to interfere with the investigation. The network was breached via a connected third-party vendor and the hackers had access to the network for 4 days during which time employee and patient information was exfiltrated including names, Social Security numbers, driver’s license numbers, financial information, medical histories, and medical record numbers.
Doctors’ Center Hospital – Ransomware Attack Involving 1.2 Million Records
On November 9, Doctor’s Center Hospital in Puerto Rico reported a hacking incident to OCR involving the protected health information of 1,195,220 patients. Hackers gained access to its network and deployed ransomware on or around October 17. A ransomware group called Project Relic was behind the attack and claimed to have exfiltrated 211 GB of data prior to encrypting files, including employee data and patient information such as names, medical record numbers, and medical notes.
MCG Health – Hacking Incident Involving 1.1 Million Records
The Seattle, WA-based software company, MCG Health, which provides patient care guidelines to healthcare providers and health plans, notified OCR on June 10 about a cyberattack on its network. The investigation suggested the hackers gained access to its network as early as February 2020, but the security breach was not detected until March 2022. The hackers exfiltrated files that contained patient and plan member data such as names, addresses, phone numbers, dates of birth, medical codes, and Social Security numbers. The breach was reported to OCR by MCG Health as affecting 793,283 individuals, but some health plan and healthcare provider clients reported the breach separately. More than 10 U.S. healthcare providers and health plans were affected and 1.1 million individuals are understood to have been affected.
Lessons Learned from the Biggest HIPAA Breaches of 2022
All of these breaches are being investigated by the HHS’ Office for Rights to determine if these organizations were fully compliant with HIPAA and if non-compliance with the requirements of HIPAA caused the data breach, and in some cases, state attorneys general have opened investigations. Class action lawsuits have also been filed against these entities seeking damages and reimbursement of out-of-pocket expenses and losses suffered as a result of misuse of patient and health plan member data. The investigations will uncover whether there have been any HIPAA violations or violations of state law and whether compliance with these regulations would have likely prevented these breaches. While specific information about HIPAA violations is not yet known, there are lessons to be learned by other healthcare providers, health plans, and business associates from these data breaches.
Business Associate Risks Must be Managed
What is clear from the largest HIPAA breaches of 2022 is cyberattacks on business associates can be particularly damaging, often affecting many HIPAA-covered entities. Business associates provide important services to healthcare organizations that are difficult or too costly to perform in-house, but providing patient information to any third-party increases the risk that the information will be exposed, and the more business associates that are used, the greater the risk to patient and plan member data.
Healthcare organizations cannot operate efficiently without third-party vendors, but prior to using any vendor their security measures and protocols should be assessed. HIPAA-covered entities must ensure that a signed business associate agreement (BAA) is obtained, but a BAA alone is not sufficient. The BAA should specify the responsibilities of the business associate with respect to cybersecurity, incident response, and breach reporting, and it may be necessary to enter into a service level agreement with the vendor. HIPAA-covered entities should review their relationships with vendors and their BAAs regularly, conduct annual audits of their vendors to check the cybersecurity measures they have in place, and they should stipulate that vendors must conduct annual risk assessments. It is also worth considering consolidating vendors, where possible.
Care Must be Taken with Tracking Technologies
The use of tracking technologies has come under the spotlight in 2022. These tracking technologies are usually provided by third parties such as big tech firms and are commonly used for website analytics. These tools can be incredibly useful but in healthcare, there is considerable potential for privacy violations. It should be noted that there is no problem with the tools themselves, the problem comes with how they are used and their potential to collect and transmit patient information based on the interactions of individuals.
Due to the potential for disclosures of PHI, HIPAA-compliant patient authorizations may be required and it may be necessary to enter into a business associate agreement with the developer of the code. So far, only a handful of healthcare organizations have reported data breaches associated with tracking technologies, but many hospitals and health systems have used these tracking technologies and may have violated HIPAA and patient privacy. A study by The Markup earlier this year indicated one-third of the top 100 hospitals in the United States had added tracking technologies such as Meta Pixel to their websites. These breaches have highlighted the risks associated with these tools and the importance of conducting a careful assessment of any third-party code prior to adding it to a website or application to verify that it is not transferring data to third parties. If it does, business associate agreements must be in place and patient authorizations may need tobe obtained. OCR has recently issued guidance on the use of these tracking technologies and the requirements for HIPAA compliance.
Develop and Test an Incident Response Plan for Ransomware Attacks
The healthcare industry continues to be targeted by ransomware gangs, who steal sensitive data and encrypt files for extortion. Stolen records are published or sold to other cybercriminal gangs, placing victims at a very real risk of identity theft and fraud, but these attacks also put patient safety at risk. Patients often have to be redirected to other facilities, the lack of access to EHRs requires appointments to be canceled, and the attacks delay diagnosis and essential medical care. In many attacks, electronic systems are taken out of action for several weeks and studies suggest mortality rates increase following a ransomware attack and patient outcomes are affected.
Protecting against ransomware attacks can be a challenge, as ransomware gangs use multiple attack vectors to gain initial access to healthcare networks. Healthcare organizations should keep up to date on the latest threat intelligence and adopt a defense-in-depth approach covering all potential attack vectors. Regaining access to patient data quickly can help to limit the harm caused, and in this regard, it is vital to follow best practices for backups and ensure multiple copies of backups are created with at least one copy stored securely off-site. The key to a fast recovery is contingency planning and implementing a comprehensive incident response plan. Those plans must also be regularly tested with tabletop exercises involving members of all teams involved in the breach response. Some of the most damaging ransomware attacks and hacking incidents were due to contingency and incident response planning failures.
Adopting Recognized Security Practices is Strongly Advisable
An update to the HITECH Act in January 2021 required OCR to consider the recognized security practices an organization has implemented continuously for the 12 months prior to a data breach when making determinations about penalties and sanctions. While HIPAA Security Rule compliance is mandatory, HIPAA-regulated entities are not required by law to implement recognized security practices, but it is strongly advisable. Not only will following recognized security practices reduce the risk of a cyberattack and limit the harm caused, OCR will reduce the length of audits and investigations and the financial penalties imposed.
Issue Breach Notifications Promptly
Several of the biggest HIPAA breaches of 2022 involved delays in issuing breach notifications to OCR and the individuals affected. HIPAA is clear about the maximum time frame for reporting breaches of protected health information, which is 60 days of the discovery of a data breach; however, branch notifications should be issued to OCR and affected individuals without necessary delay. Prompt notification is important as it allows the individuals affected by the breach to take steps to protect themselves against identity theft and fraud. OCR recently issued a reminder about the requirements for responding to security incidents, in which the breach notification requirements of HIPAA were confirmed. This could indicate OCR may be looking at enforcing this aspect of HIPAA compliance more rigorously in the future, as unnecessary delays in issuing breach notifications are common.
Steve Alder
Editor-in-Chief, HIPAA Journal
The post Editorial: Lessons from Biggest HIPAA Breaches of 2022 appeared first on HIPAA Journal.