63 data breaches of 500 or more records were reported to the HHS’ Office for Civil Rights in September, bringing an end to the downward trend in data breaches seen over the previous three months. September’s total was above the 12-month average of 59 breaches a month, with data breaches being reported at a rate of more than 2 per day. In 2017, data breaches were being reported at a rate of one per day.

While the number of reported data breaches increased by 28.6% month-over-month, for the third consecutive month the number of breached records decreased, with 2,440,434 records breached across the 63 reported incidents. September’s total was well below the 12-month average of 3,481,033 breached records a month. 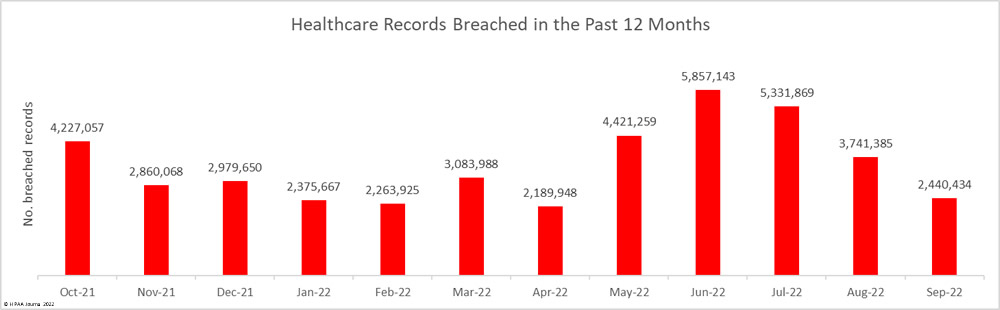
So far in 2022, 31,705,618 patient records have been exposed or impermissibly disclosed.
The Largest Healthcare Data Breaches Reported in September
30 data breaches of 10,000 or more patient records were reported to the HHS’ Office for Civil Rights in September 2022, all but one of which were hacking/IT incidents. The largest data breach involved the records of more than 542,000 patients of the Wolfe Clinic in Iowa and occurred at its electronic health record provider Eye Care Leaders. The attack saw database and system configuration files deleted. More than 3.6 million individuals were affected by the data breach.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Cause of Breach |
| Wolfe Clinic, P.C. |
IA |
Healthcare Provider |
542,776 |
Hacking incident at its EHR provider (Eye Care Leaders) |
| Empress Ambulance Service LLC |
NY |
Healthcare Provider |
318,558 |
Ransomware attack |
| Cytometry Specialists, Inc. d/b/a CSI Laboratories |
GA |
Healthcare Provider |
244,850 |
Business email compromise (BEC) attack |
| FMC Services, LLC |
TX |
Healthcare Provider |
233,948 |
Hacked network server |
| Physician’s Business Office, Inc. |
WV |
Business Associate |
196,673 |
Hacked network server |
| Providence WA Anesthesia Services PC |
NY |
Healthcare Provider |
98,643 |
Hacked network server at management company |
| Medical Associates of the Lehigh Valley |
PA |
Healthcare Provider |
75,628 |
Ransomware attack |
| Dyersburg Family Walk-In Clinic, LLC (Reelfoot Family Walk-In Clinic) |
TN |
Healthcare Provider |
58,562 |
Hacked network server (data theft confirmed) |
| Palm Springs Anesthesia Services PC |
NY |
Healthcare Provider |
58,513 |
Hacked network server at management company |
| Reiter Affiliated Companies, LLC |
CA |
Business Associate |
48,000 |
Ransomware attack at a business associate |
| Reiter Affiliated Health and Welfare Plan |
CA |
Health Plan |
45,000 |
Ransomware attack |
| Anesthesia Services of San Joaquin PC |
NY |
Healthcare Provider |
44,015 |
Hacked network server at management company |
| Anesthesia Associates of El Paso PA |
NY |
Healthcare Provider |
43,168 |
Hacked network server at management company |
| The Physicians’ Spine and Rehabilitation Specialists of Georgia, P.C. |
GA |
Healthcare Provider |
38,765 |
Hacked network server |
| Country Doctor Community Clinic |
WA |
Healthcare Provider |
38,751 |
Hacked network server |
| Resource Anesthesiology Associates PC |
NY |
Healthcare Provider |
37,697 |
Hacked network server at management company |
| Lubbock Heart & Surgical Hospital |
TX |
Healthcare Provider |
23,379 |
Hacked network server |
| Genesis Health Care, Inc. |
SC |
Healthcare Provider |
21,226 |
Hacked network server |
| Resource Anesthesiology Associates of IL PC |
NY |
Healthcare Provider |
18,321 |
Hacked network server at management company |
| Bronx Anesthesia Services PC |
NY |
Healthcare Provider |
17,802 |
Hacked network server at management company |
| Resource Anesthesiology Associates of CA A Medical Corporation |
CA |
Healthcare Provider |
16,001 |
Hacked network server at management company |
| Monroe Ear Nose and Throat Associates, PC |
MI |
Healthcare Provider |
14,500 |
Hacked network server hosting EHRs |
| Magellan Rx Management |
MD |
Business Associate |
13,663 |
Hacked network server |
| Hazleton Anesthesia Services PC |
NY |
Healthcare Provider |
13,607 |
Hacked network server at management company |
| Riverside Medical Group |
NJ |
Healthcare Provider |
12,499 |
Hacked legacy server containing EHRs |
| Anesthesia Associates of Maryland LLC |
MD |
Healthcare Provider |
12,403 |
Hacked network server at management company |
| Northern California Fertility Medical Center |
CA |
Healthcare Provider |
12,145 |
Ransomware attack |
| Neurology Center of Nevada |
NV |
Healthcare Provider |
11,700 |
Hacking incident involving EHRs |
| Dr. Alexander J. Richardson, DPM |
OH |
Healthcare Provider |
11,300 |
Hacking incident involving EHRs |
| WellMed Medical Management |
TX |
Healthcare Provider |
10,506 |
A physician took records to his new practice |
Causes of September 2022 Data Breaches
As is now the norm, the majority of the month’s data breaches were categorized as hacking/IT incidents, which include hacking, ransomware and malware attacks, phishing attacks, and misconfigured databases and cloud resources.
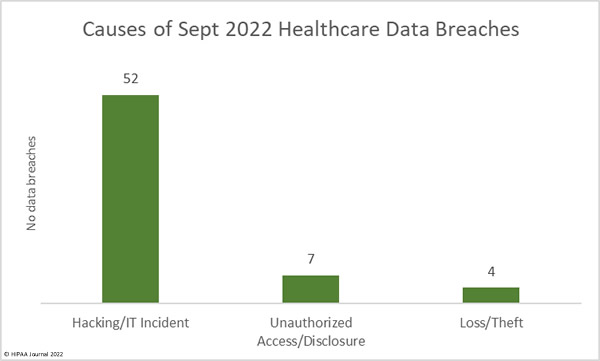
52 breaches – 82% of the month’s total – were hacking/IT incidents, which resulted in the exposure and/or theft of the records of 2,410,654 individuals. The average breach size was 46,359 records and the median breach size was 12,274 records. These incidents accounted for 98.78% of all records breached in September.
Ransomware is commonly used in attacks on hospitals to prevent access to business-critical files and patient records. These attacks typically involve data theft prior to file encryption with the attackers threatening to sell or publish the stolen data if the ransom is not paid. Several threat actors have now dispensed with the file encryption and are just stealing data and demanding payment to prevent its sale or release. That makes the attacks quicker and easier for the attackers and ransoms are still often paid. These extortion-only attacks have been increasing in recent months.
There were 7 reported unauthorized access/disclosure incidents reported, which include unauthorized access by employees, misdirected emails, and mailing errors. Across the 7 breaches, the records of 24,639 individuals were impermissibly disclosed. The average breach size was 3,250 records and the median breach size was 1,359 records.
There were 4 data breaches reported that involved the loss or theft of electronic devices that contained individually identifiable protected health information. Those devices contained 5,141 records. The average breach size was 1,285 records and the median breach size was 1,207 records. These incidents could have been avoided had data on the devices been encrypted.
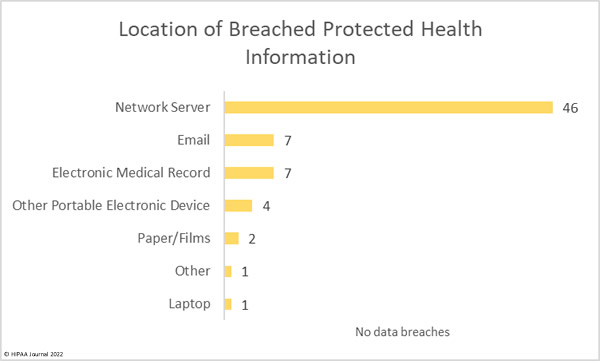
The number of email-related data breaches is below the levels normally seen, with just 7 email data breaches reported. However, data from the ransomware remediation firm Coveware suggests email is still the most common way that threat actors gain access to networks in ransomware attacks. One of the largest data breaches reported this month – at CSI Laboratories – saw threat actors gain access to email accounts containing the records of almost 245,000 individuals. The email account was then used in a business email compromise attack to try to reroute CSI customer healthcare provider payments.
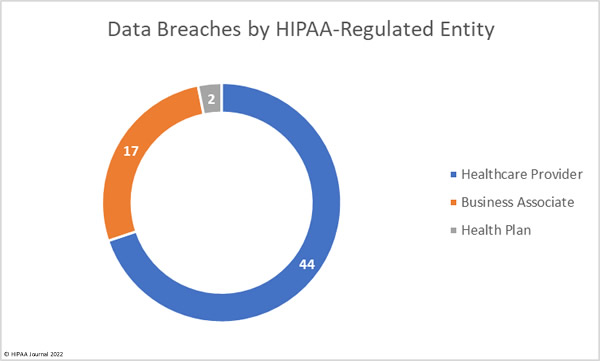
HIPAA-Regulated Entities Affected by Data Breaches
Healthcare providers were the worst affected entity in September with 46 data breaches reported, with 10 breaches reported by business associates and 7 breaches reported by health plans. Healthcare providers and health plans often choose to report breaches at business associates themselves, as was the case in 7 data breaches at business associates in September. The pie chart below reflects this and shows where the data breaches actually occurred.
Healthcare Data Breaches by State
HIPAA-regulated entities in 22 states reported data breaches in September. New York was the worst affected state with 15 breaches reported. 13 of the breaches were reported by providers of anesthesia services – The breach actually occurred at their management company.
| State |
Breaches |
| New York |
15 |
| California |
8 |
| Tennessee & Washington |
5 |
| Florida & Texas |
4 |
| Georgia |
3 |
| Indiana, Maryland, New Jersey, & Pennsylvania |
2 |
| Colorado, Connecticut, Iowa, Michigan, Montana, Nebraska, Nevada, Ohio, Rhode Island, South Carolina, & Wisconsin |
1 |
HIPAA Enforcement Activity in September
The HHS’ Office for Civil Rights agreed to settle HIPAA violations with three healthcare providers in September. All three of the settlements resolved violations of the HIPAA Right of Access, where patients were not provided with timely access to their medical records. All three cases were investigated by OCR after patients filed complaints that they had not been provided with their requested medical records. Great Expressions Dental Center of Georgia was also discovered to have overcharged a patient for providing a copy of her medical records.
Great Expressions Dental Center of Georgia, P.C. settled its case for $80,000, Family Dental Care, P.C. settled its case for $30,000, and B. Steven L. Hardy, D.D.S., LTD, dba Paradise Family Dental, settled its care for $25,000, All three settlements involved a corrective action plan to address the areas of non-compliance.
OCR has now imposed 20 financial penalties on HIPAA-regulated entities to resolve HIPAA violations so far this year – more than any year to date.
The post September 2022 Healthcare Data Breach Report appeared first on HIPAA Journal.




