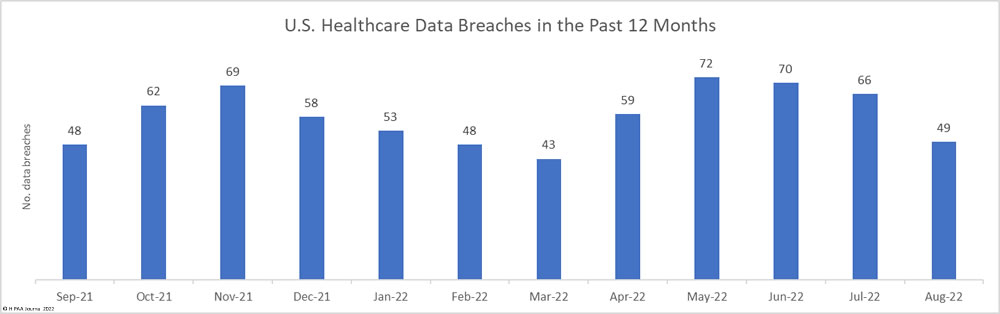
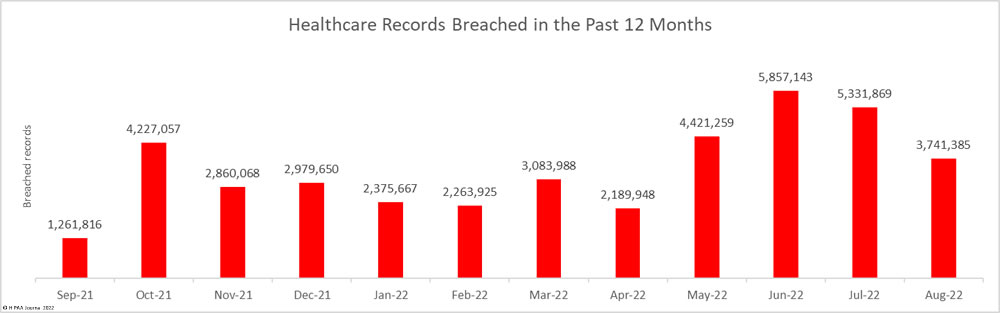
For the third successive month, the number of healthcare data breaches reported to the Department of Health and Human Services’ Office for Civil Rights has fallen, with 49 breaches of 500 or more records reported in August– well below the 12-month average of 58 breaches per month. The 25.75% percentage decrease from July 2022 was accompanied by a significant reduction in breached records, which dropped almost 30% month over month.
Across the 45 data breaches, 3,741,385 healthcare records were exposed or impermissibly disclosed – well below the 5,135,953 records that were breached in August 2021, although slightly more than the 12-month average of 3,382,815 breached healthcare records per month.
Largest Healthcare Data Breaches Reported in August 2022
18 healthcare data breaches of 10,000 or more records were reported to the HHS’ Office for Civil Rights in August 2022, which have been summarized in the table below. It should be noted that the exact nature of the data breach is not always reported by the breached entity, such as if ransomware was used to encrypt files.
As the table below shows, the largest reported data breach of the month occurred at Novant Health and was due to the use of the third-party JavaScript code snippet – Meta Pixel on the healthcare provider’s website. The code snippet is used on websites to track visitor activity but can send PHI to Meta (Facebook), which can then be used to serve targeted ads. Novant Health said there had been a misconfiguration that saw the code added behind the login on the patient portal.
So far, Novant Health is the only healthcare provider to report such a breach, even though investigations have revealed many other healthcare organizations have used the code snippet on their websites, several of which added the code to their patient portals. Multiple lawsuits have been filed over these privacy breaches.
| Name of Covered Entity | State | Covered Entity Type | Individuals Affected | Location of Breached Information | Business Associate Present |
| Novant Health Inc. on behalf of Novant Health ACE & as contractor for NMG Services Inc. | NC | Business Associate | 1,362,296 | Electronic Medical Record | Unauthorized disclosure to Meta through Meta Pixel code snippet on website |
| Practice Resources, LLC | NY | Business Associate | 942,138 | Network Server | Ransomware attack |
| Warner Norcross and Judd, LLP | MI | Business Associate | 255,160 | Network Server | Hacking and data theft incident |
| California Department of Corrections and Rehabilitation | CA | Healthcare Provider | 236,000 | Network Server | Hacking incident |
| Conifer Revenue Cycle Solutions, LLC | TX | Business Associate | 134,948 | Hacking of Microsoft 365 Environment | |
| Common Ground Healthcare Cooperative | WI | Health Plan | 133,714 | Network Server | Ransomware attack on a business associate (OneTouchPoint) |
| Methodist McKinney Hospital | TX | Healthcare Provider | 110,244 | Network Server | Hacking and data theft incident |
| First Choice Community Health Care, Inc. | NM | Healthcare Provider | 101,541 | Network Server | Hacking incident |
| Onyx Technology LLC | MD | Business Associate | 96,814 | Network Server | Hacking incident |
| EmergeOrtho | NC | Healthcare Provider | 68,661 | Network Server | Ransomware attack |
| Lamoille Health Partners | VT | Healthcare Provider | 59,381 | Network Server | Ransomware attack |
| Henderson & Walton Women’s Center, P.C. | AL | Healthcare Provider | 34,306 | Hacking incident | |
| St. Luke’s Health System, Ltd. | ID | Healthcare Provider | 31,573 | Network Server | Hacking incident at billing vendor |
| San Diego American Indian Health Center | CA | Healthcare Provider | 27,367 | Network Server | Hacking and data theft incident |
| Rock County Human Services Department | WI | Healthcare Provider | 25,610 | Unauthorized access to email accounts | |
| NorthStar HealthCare Consulting LLC | GA | Business Associate | 18,354 | Unauthorized access to email accounts | |
| Methodist Craig Ranch Surgical Center | TX | Healthcare Provider | 15,157 | Network Server | Hacking and data theft incident (Methodist McKinney) |
| Valley Baptist Medical Center – Harlingen | TX | Healthcare Provider | 11,137 | Network Server | Ransomware attack (Practice Resources) |
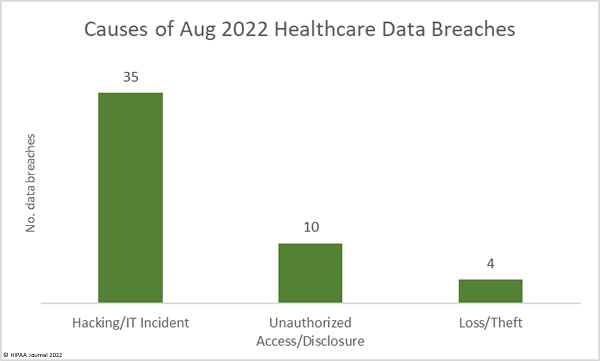
Causes of August 2022 Data Breaches
The above table shows hacking incidents continue to be a major problem for the healthcare industry, with ransomware often used in the attacks. There has been a growing trend for attackers to conduct data theft and extortion attacks, without using ransomware. While the consequences for patients may still be severe, the failure to encrypt files causes less disruption; however, a recent study by Proofpoint suggests that patient safety issues are still experienced after cyberattacks when ransomware is not used. Around 22% of healthcare providers reported seeing an increase in mortality rate following a major cyberattack and 57% reported poorer patient outcomes.
Healthcare organizations are vulnerable to email attacks, with phishing attacks a common cause of data breaches. There has also been an increase in the use of reverse proxies in attacks, which allow threat actors to steal credentials and bypass multifactor authentication to gain access to Microsoft (Office) 365 environments.
35 of the month’s breaches (71.4%) were attributed to hacking/IT incidents and involved the exposure or theft of 2,337,485 healthcare records – 62.48% of the month’s reported breached records. The mean breach size was 66,785 records and the median breach size was 7,496 records.
There were 10 reported unauthorized access/disclosure incidents involving 1,398,595 records – 37.38% of the month’s breached records. The mean breach size was 139,860 records and the median breach size was 1,375 records. 1,362,296 of those records were breached in the Novant Health incident. There were 4 loss/theft incidents (2 losses; 2 theft) involving 5,305 records. The mean breach size was 1,326 records and the median breach size was 1,357 records.
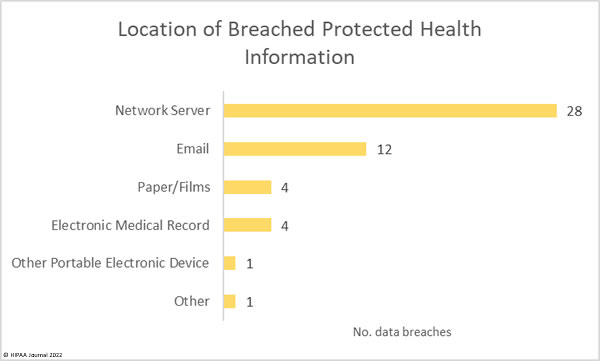
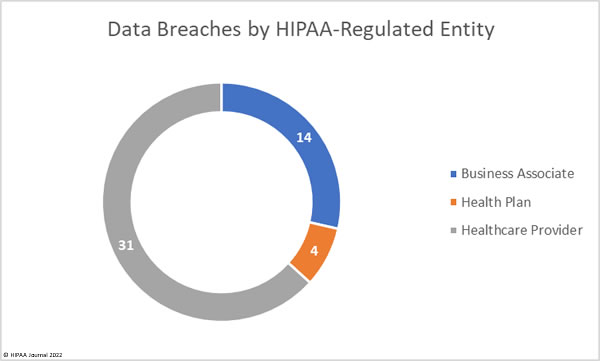
The number of hacking incidents is reflected in the location of breached PHI, as shown in the chart below.
Data Breached by HIPAA Regulated Entity
Health plans were the worst affected HIPAA-regulated entity, with 35 data breaches reported. 9 breaches were reported by business associates, and 5 breaches were reported by health plans. Data breaches are not always reported by business associates directly, with some HIPAA-covered entities choosing to report breaches at their business associates. The chart below takes this into account and shows data breaches based on where they occurred. While 14 data breaches occurred at business associates in August, this is a notable reduction from the previous few months. In July there were 36 data breaches at business associates, and 40 in June.
Geographic Distribution of Data Breaches
Healthcare data breaches of 500 or more records were reported to the HHS’ Office for Civil Rights in August by HIPAA-regulated entities in 26 states, with Texas the worst affected with 8 reported data breaches.
| State | Breaches |
| Texas | 8 |
| North Carolina | 4 |
| Arkansas, California, & Michigan | 3 |
| Colorado, Florida, Illinois, New York, Vermont, Washington, & Wisconsin | 2 |
| Alabama, Arizona, Georgia, Idaho, Indiana, Louisiana, Maryland, Mississippi, New Hampshire, New Jersey, New Mexico, Ohio, Pennsylvania, & Virginia | 1 |
HIPAA Enforcement Activity in August 2022
There was one HIPAA enforcement activity announced by OCR in August, and somewhat unusually given the focus on the HIPAA Right of Access over the past three years, it related to the improper disposal of PHI. Out of the past 25 enforcement actions that have resulted in financial penalties, only 5 have been for non-HIPAA Right of Access violations.
OCR launched an investigation of New England Dermatology and Laser Center after receiving a report on March 11, 2021, about the improper disposal of the PHI of 58,106 patients. In addition to failing to render PHI unreadable and indecipherable, OCR determined there was a failure to maintain appropriate administrative safeguards. The improper disposal of empty specimen containers with patient labels spanned from 2011 to 2021. New England Dermatology and Laser Center agreed to settle the case and paid a $300,640 penalty.
Lisa J Pino stepped down as OCR Director in July 2022 and has now been replaced by Melanie Fontes Rainer. It remains to be seen where she will lead the department regarding the enforcement of HIPAA compliance, although HHS Secretary Xavier Becerra has stated that HIPAA Privacy Rule violations with respect to unauthorized disclosures of PHI related to abortion care and other forms of sexual and reproductive health care will be an enforcement priority of OCR.
The post August 2022 Healthcare Data Breach Report appeared first on HIPAA Journal.