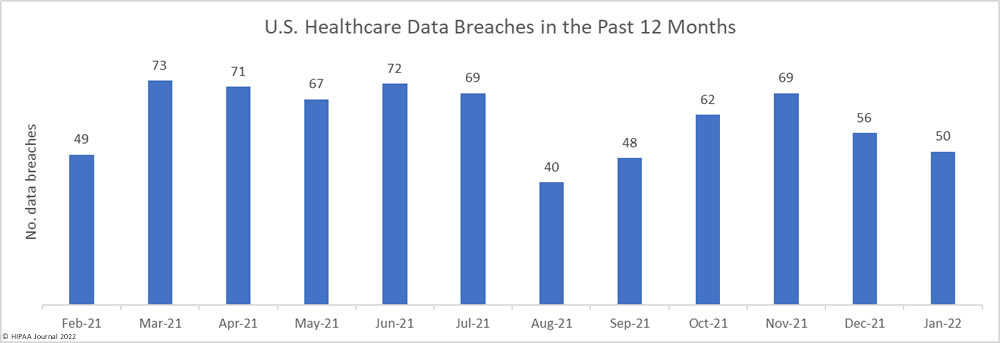
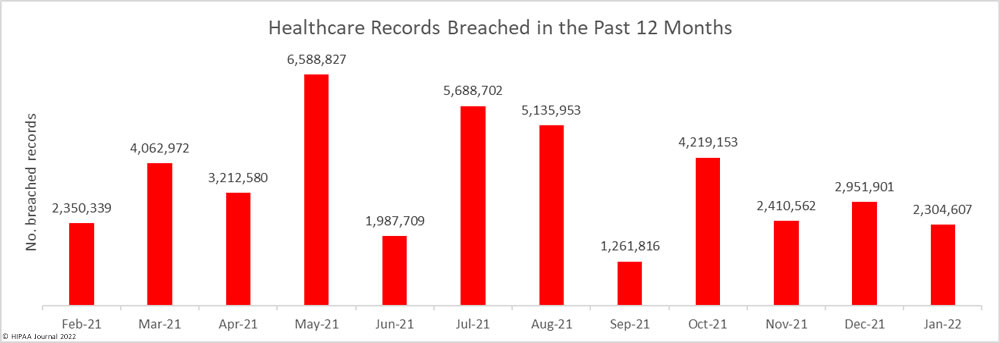
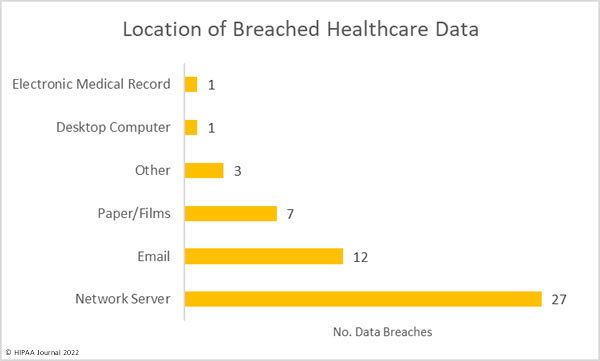
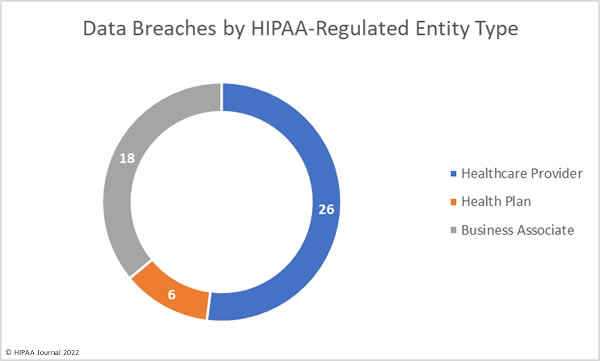
The Houston Health Department has recently announced that the personal information and COVID-19 test results of 10,291 individuals have been exposed online as a result of a technical issue with its portal. The issue allowed approximately 3,500 portal users to access the data of other individuals.
The Houston Health Department said it detected the issue on January 6, 2022, and the portal was deactivated within 48 hours. Notification letters had to be delayed for several weeks while the portal issue was investigated to determine the full nature and scope of the incident. The health department confirmed that this was not a hacking incident, and it does not appear that any exposed information has been misused.
The types of data that could have been viewed included names, addresses, dates of birth, email addresses, testing dates, and test results. While no Social Security numbers were compromised, affected individuals have been offered a complimentary 12-month membership to an identity theft protection service.
Priority Health Confirms Breach of Member Portal Accounts
The Michigan health insurer Priority Health has recently announced a breach of several member portal accounts. According to a recent breach notice, the security breach was detected on December 16, 2021. Prompt action was taken to prevent further unauthorized access, including placing a hold on all member accounts from December 16 to December 21 while the incident was investigated and the portal was secured.
Priority Health said information in the compromised accounts included names, dates of birth, addresses, phone numbers, insurance information, claims information, and limited medical information. Priority Health has been working with third-party security consultants to improve security and prevent further breaches. On January 18, 2022, multifactor authentication was added to the portal.
It is currently unclear how many individuals have been affected.
Hofmann Arthritis Institute and Hofmann Arthritis Institute of Nevada
Hofmann Arthritis Institute in Utah and Hofmann Arthritis Institute of Nevada (HAI) have recently announced they were both victims of a cyberattack on one of their vendors – Alta Medical Management and ECL Group (AMM) – which provides accounting and billing services.
The attack occurred on or around November 15, 2021, and prevented HAI from accessing certain information on AMM systems. The investigation confirmed the attack was limited to AMM systems and HAI systems were unaffected. HAI said AMM did not provide any details on the nature of the attack, but HAI was able to determine on December 7, 2021, that the prevention of access to AMM systems was due to a cyberattack. HAI said its investigation into the incident is ongoing, but so far it has not been possible to tell if any patient information was stolen in the attack.
A comprehensive review of all files provided to AMM was conducted to determine the types of patient information that may have been compromised. The review was completed on January 27, 2022, and confirmed the following types of information were contained in the files: names, addresses, Social Security numbers, dates of birth, driver’s license numbers, financial information, medical information, health insurance information, and billing information. HAI said it is unaware of any actual or attempted misuse of patient data.
HAI said it is reviewing its security policies and procedures related to vendors and will implement additional measures to protect against further security breaches.
The breach has been reported to the HHS’ Office for Civil Rights as affecting 5,338 individuals.
The post PHI of 10,000 Individuals Exposed Due to Houston Health Department Portal Glitch appeared first on HIPAA Journal.