The number of reported healthcare data breaches has increased for the third successive month, with November seeing 68 data breaches of 500 or more records reported to the HHS’ Office for Civil Rights – a 15.25% increase from October and well above the 12-month average of 56 data breaches a month. From January 1 to November 30, 614 data breaches were reported to the Office for Civil Rights. It is looking increasingly likely that this year will be the worst ever year for healthcare data breaches.
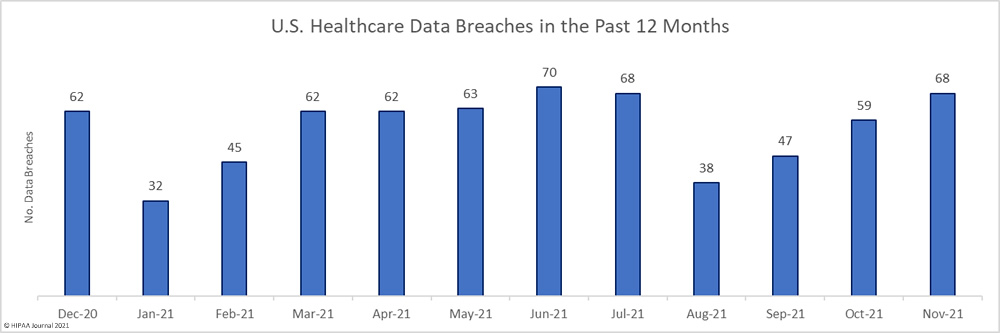
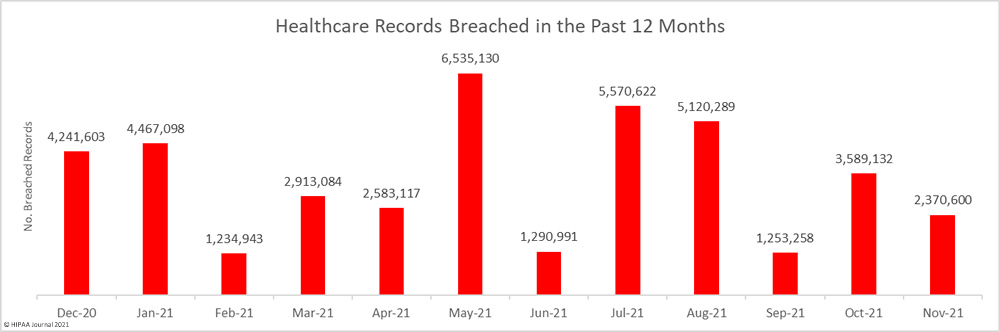
The number of data breaches increased, but there was a sizable reduction in the number of breached records. Across the 68 reported breaches, 2,370,600 healthcare records were exposed, stolen, or impermissibly disclosed – a 33.95% decrease from the previous month and well below the 12-month average of 3,430,822 breached records per month.
Largest Healthcare Data Breaches Reported in November 2021
In November, 30 data breaches of 10,000 or more records were reported to the HHS’ Office for Civil Rights, and 4 of those breaches resulted in the exposure/theft of more than 100,000 records. The average breach size in November was 34,862 records and the median breach size was 5,403 records.
The worst breach of the month saw the protected health information of 582,170 individuals exposed when hackers gained access to the network of Utah Imaging Associates. Planned Parenthood also suffered a major data breach, with hackers gaining access to its network and exfiltrating data before using ransomware to encrypt files.
Sound Generations, a non-profit that helps older adults and adults with disabilities obtain low-cost healthcare services, notified patients about two ransomware attacks that had occurred in 2021, which together resulted in the exposure and potential theft of the PHI of 103,576 individuals.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Location of Breached PHI |
Cause of Breach |
| Utah Imaging Associates, Inc. |
Healthcare Provider |
582,170 |
Hacking/IT Incident |
Network Server |
Unspecified hacking incident |
| Planned Parenthood Los Angeles |
Healthcare Provider |
409,759 |
Hacking/IT Incident |
Network Server |
Ransomware attack |
| The Urology Center of Colorado |
Healthcare Provider |
137,820 |
Hacking/IT Incident |
Network Server |
Unspecified hacking incident |
| Sound Generations |
Business Associate |
103,576 |
Hacking/IT Incident |
Network Server |
Two ransomware attacks |
| Mowery Clinic LLC |
Healthcare Provider |
96,000 |
Hacking/IT Incident |
Network Server |
Malware infection |
| Howard University College of Dentistry |
Healthcare Provider |
80,915 |
Hacking/IT Incident |
Electronic Medical Record, Network Server |
Ransomware attack |
| Sentara Healthcare |
Healthcare Provider |
72,121 |
Hacking/IT Incident |
Network Server |
Unspecified hacking incident at a business associate |
| Ophthalmology Associates |
Healthcare Provider |
67,000 |
Hacking/IT Incident |
Electronic Medical Record, Network Server |
Unspecified hacking incident |
| Maxim Healthcare Group |
Healthcare Provider |
65,267 |
Hacking/IT Incident |
Email |
Phishing attack |
| True Health New Mexico |
Health Plan |
62,983 |
Hacking/IT Incident |
Network Server |
Unspecified hacking incident |
| TriValley Primary Care |
Healthcare Provider |
57,468 |
Hacking/IT Incident |
Network Server |
Ransomware attack |
| Broward County Public Schools |
Health Plan |
48,684 |
Hacking/IT Incident |
Network Server |
Ransomware attack |
| Consociate, Inc. |
Business Associate |
48,583 |
Hacking/IT Incident |
Network Server |
|
| Doctors Health Group, Inc. |
Healthcare Provider |
47,660 |
Hacking/IT Incident |
Network Server |
Patient portal breach at business associate (QRS Healthcare Solutions) |
| Baywood Medical Associates, PLC dba Desert Pain Institute |
Healthcare Provider |
45,262 |
Hacking/IT Incident |
Network Server |
Unspecified hacking incident |
| Medsurant Holdings, LLC |
Healthcare Provider |
45,000 |
Hacking/IT Incident |
Network Server |
Ransomware attack |
| One Community Health |
Healthcare Provider |
39,865 |
Hacking/IT Incident |
Network Server |
Unspecified hacking incident |
| Educators Mutual Insurance Association |
Business Associate |
39,317 |
Hacking/IT Incident |
Network Server |
Malware infection |
| Victory Health Partners |
Healthcare Provider |
30,000 |
Hacking/IT Incident |
Network Server |
Ransomware attack |
| Commission on Economic Opportunity |
Business Associate |
29,454 |
Hacking/IT Incident |
Network Server |
Hacked public claimant portal |
Causes of November 20021 Healthcare Data Breaches
Hacking/IT incidents dominated the breach reports in November, accounting for 50 of the reported breaches. Ransomware continues to be extensively used in attacks on healthcare providers and their business associates, with the attacks often seeing sensitive patient data stolen and posted on data leak sites. The theft of patient data in these attacks also makes lawsuits more likely. Planned Parenthood, for example, was hit with a class action lawsuit a few days after mailing notification letters to affected patients.
2,327,353 healthcare records were exposed or stolen across those hacking incidents, which is 98.18% of all records breached in November. The average breach size for those incidents was 42,316 records and the median breach size was 11,603 records.
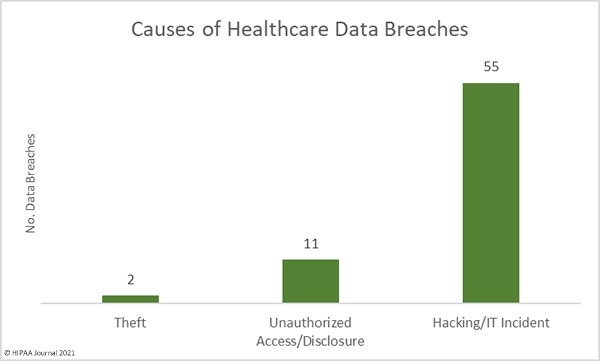
There were 11 unauthorized access/disclosure breaches in November – half the number of unauthorized access/disclosure breaches reported in October. Across those breaches, 37,646 records were impermissibly accessed or disclosed. The average breach size was 3,422 records and the median breach size was 1,553 records. There were also two reported cases of theft of portable electronic devices containing the electronic protected health information of 5,601 individuals.

November Healthcare Data Breaches by Covered Entity Type
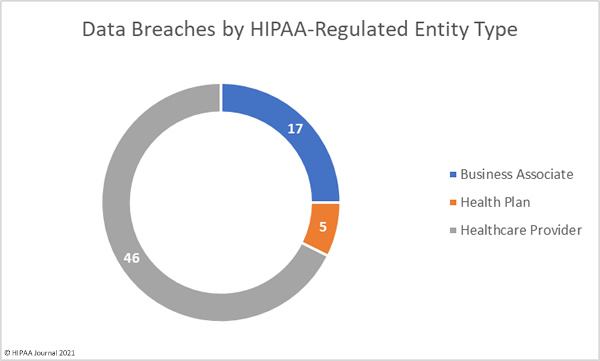
Healthcare providers were the worst affected covered entity type with 50 reported breaches, with four of those breaches occurring at business associates but were reported by the healthcare provider. 8 data breaches were reported by health plans, 3 of which occurred at business associates, and business associates self-reported 10 data breaches. The pie chart below shows the breakdown of breaches based on where the breach occurred.
Geographic Distribution of November Healthcare Data Breaches
Healthcare data breaches of 500 or more records were reported by HIPAA-regulated entities in 32 states and the District of Columbia.
| State |
Number of Reported Data Breaches |
| California & New York |
7 |
| Maryland & Pennsylvania |
4 |
| Colorado, Kentucky, Ohio, & Utah |
3 |
| Illinois, Indiana, Michigan, Minnesota, New Mexico, Tennessee, Texas, Virginia, and the District of Columbia |
2 |
| Alabama, Arizona, Arkansas, Florida, Georgia, Idaho, Kansas, Massachusetts, Missouri, Nebraska, New Hampshire, New Jersey, North Carolina, Oregon, South Carolina, and Washington |
1 |
HIPAA Enforcement Activity in November 2021
There was a flurry of HIPAA enforcement activity in November with financial penalties imposed by federal and state regulators. The HHS’ Office for Civil Rights announced a further 5 financial penalties to resolve alleged violations of the HIPAA Right of Access. In all cases, the healthcare providers had failed to provide patients with a copy of their requested PHI within a reasonable period of time after a request was received.
| Covered Entity |
Penalty |
Penalty Type |
Alleged Violation |
| Rainrock Treatment Center LLC (dba Monte Nido Rainrock)
|
$160,000
|
Settlement |
HIPAA Right of Access |
| Advanced Spine & Pain Management |
$32,150
|
Settlement |
HIPAA Right of Access |
| Denver Retina Center |
$30,000
|
Settlement |
HIPAA Right of Access |
| Wake Health Medical Group
|
$10,000
|
Settlement |
HIPAA Right of Access |
| Dr. Robert Glaser
|
$100,000 |
Civil Monetary Penalty |
HIPAA Right of Access |
The New Jersey Attorney General and the Division of Consumer Affairs announced in November that a settlement had been reached with two New jersey printing firms – Command Marketing Innovations, LLC and Strategic Content Imaging LLC – to resolve violations of HIPAA and the New Jersey Consumer Fraud Act. The violations were uncovered during an investigation into a data breach involving the PHI of 55,715 New Jersey residents.
The breach was due to a printing error that saw the last page of one individual’s benefit statement being attached to the benefit statement of another individual. The Division of Consumer Affairs determined the companies failed to ensure confidentiality of PHI, did not implement sufficient PHI safeguards and failed to review security measures following changes to procedures. A financial penalty of $130,000 was imposed on the two firms, and $65,000 was suspended and will not be payable provided the companies address all the security failures identified during the investigation.
The post November 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.




