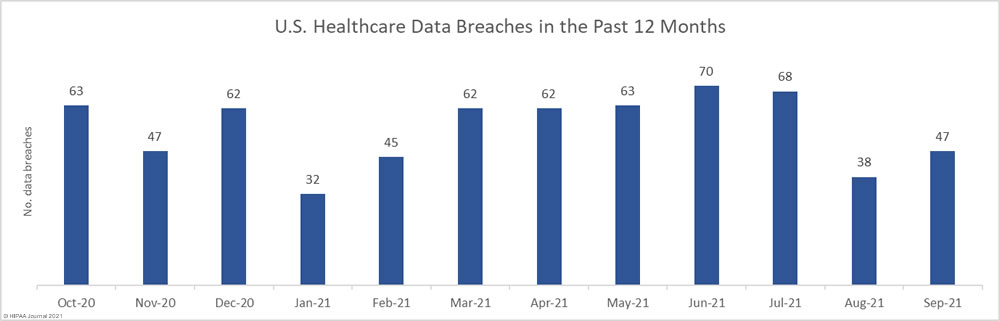
There was a 23.7% month-over-month increase in reported healthcare data breaches in September, which saw 47 data breaches of 500 or more records reported to the Department of Health and Human Services’ Office for Civil Rights. While that is more than 1.5 breaches a day, it is under the average of 55.5 breaches per month over the past 12 months.
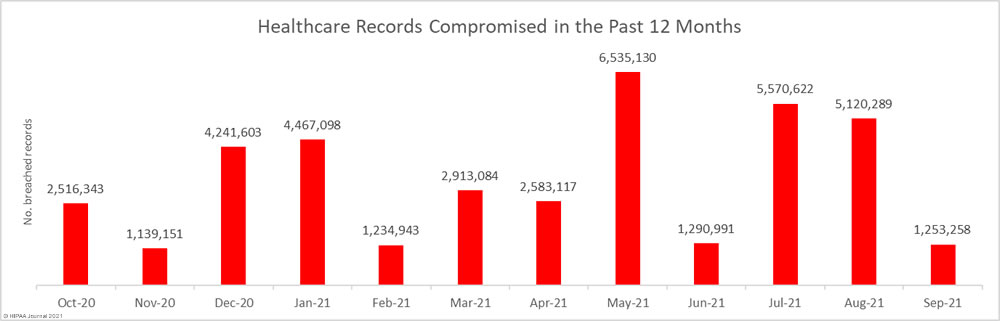
While data breaches increased, there was a major decrease in the number of breached healthcare records, dropping 75.5% from August to 1,253,258 records across the 47 reported data breaches, which is the third-lowest total over the past 12 months.
Largest Healthcare Data Breaches Reported in September 2021
16 healthcare data breaches were reported in September 2021 that involved the exposure, theft, or impermissible disclosure of more than 10,000 healthcare records.
The largest breach of the month was reported by the State of Alaska Department of Health & Social Services. The breach was initially thought to have resulted in the theft of the personal and protected health information (PHI) of all state residents, although the breach was reported to the HHS as affecting 500,000 individuals. The cyberattack is believed to have been conducted by a nation-state hacking group.
Two major data breaches were reported by eye care providers: A hacking incident at U.S. Vision Optical resulted in the exposure of the PHI of 180,000 individuals, and a phishing incident at Simon Eye Management gave the attackers access to email accounts containing the PHI of 144,373 individuals. The breaches are not believed to be related, but they are two of a handful of recent incidents affecting eye care providers.
Ransomware continues to be extensively used in attacks on the healthcare industry. 6 of the top 16 attacks in September involved ransomware and potentially saw PHI stolen. Several ransomware gangs have targeted the healthcare sector, with the FIN12 group one of the most active. A recent analysis of FIN12 attacks by Mandiant revealed 20% of the gang’s attacks have been on the healthcare industry, with the attacks accounting for around 20% of all incidents Mandiant responds to.
Hackers have been targeting the healthcare industry, but data breaches can also be caused by insiders with privileged access to PHI. One notable ‘insider’ breach was reported by Premier Management Company and involved data being accessed by a former employee after termination. The incident highlights the importance of ensuring access to PHI (and IT systems) is blocked immediately when an employee is terminated, leaves the company, or when job functions change that no longer require an employee to have access to PHI.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Cause of Breach |
| State of Alaska Department of Health & Social Services |
AK |
Health Plan |
500,000 |
Nation-state hacking Incident |
| U.S. Vision Optical |
NJ |
Healthcare Provider |
180,000 |
Unspecified hacking incident |
| Simon Eye Management |
DE |
Healthcare Provider |
144,373 |
Email account breach (phishing) |
| Navistar, Inc. Health Plan and the Navistar, Inc. Retiree Health Benefit and Life Insurance Plan |
IL |
Health Plan |
49,000 |
Ransomware attack |
| Talbert House |
OH |
Healthcare Provider |
45,000 |
Unspecified hacking incident (data exfiltration) |
| Premier Management Company |
TX |
Healthcare Provider |
37,636 |
PHI accessed by an employee after termination |
| Central Texas Medical Specialists, PLLC dba Austin Cancer Centers |
TX |
Healthcare Provider |
36,503 |
Malware |
| Orlick & Kasper, M.D.’s, P.A. |
FL |
Healthcare Provider |
30,000 |
Theft of electronic devices containing PHI |
| McAllen Surgical Specialty Center, Ltd. |
TX |
Healthcare Provider |
29,227 |
Ransomware attack |
| Asarco Health, Dental, Vision, Flexible Spending, Non-Union Employee Benefits, and Retiree Medical Plans |
AZ |
Health Plan |
28,000 |
Ransomware attack |
| Horizon House, Inc. |
PA |
Healthcare Provider |
27,823 |
Ransomware attack |
| Rehabilitation Support Services, Inc. |
NY |
Healthcare Provider |
23,907 |
Unspecified hacking incident (data exfiltration) |
| Samaritan Center of Puget Sound |
WA |
Healthcare Provider |
20,866 |
Theft of electronic devices containing PHI |
| Directions for Living |
FL |
Healthcare Provider |
19,494 |
Ransomware attack |
| Buddhist Tzu Chi Medical Foundation |
CA |
Healthcare Provider |
18,968 |
Ransomware attack |
| Eastern Los Angeles Regional Center |
CA |
Business Associate |
12,921 |
Email account breach (phishing) |
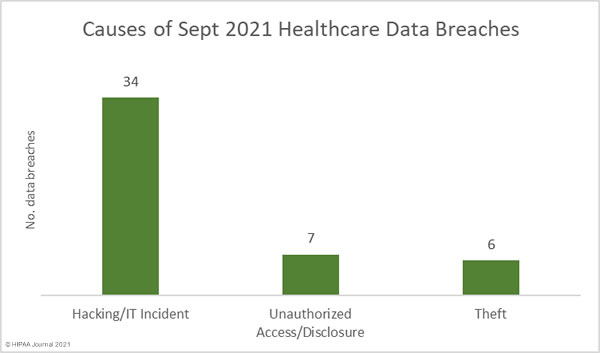
Causes of September 2021 Healthcare Data Breaches
Hacking and other IT incidents continue to dominate the breach reports, accounting for 53.2% of all breaches reported in the month and 91.6% of all breached records. 1,147,383 healthcare records were exposed or stolen in those incidents, with an average breach size of 33,747 records and a median breach size of 2,453 records.
The number of incidents involving the theft of physical records or electronic equipment containing PHI increased month-over-month. September saw 6 theft incidents reported and 60,236 records compromised. The mean breach size was 10,039 records and the median breach size was 3,918 records. 4 of those breaches involved electronic equipment and could have been prevented had encryption been used.
There were 7 data breaches reported that involved unauthorized access or disclosures of data by insiders. 45,639 records were breached across those incidents, 37,636 of which were obtained in a single incident. The average breach size was 6,520 records and the median breach size was 1,738 records.
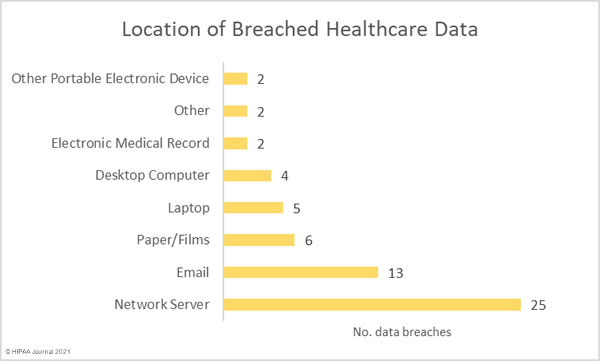
Given the high number of hacking and ransomware incidents reported, it is no surprise that the most common location of breached PHI is network servers. Email accounts continue to be targeted in phishing attacks, with 13 incidents in September involving PHI stored in email accounts. The number of devices containing PHI that were stolen highlights the importance of using encryption to protect stored data.
September 2021 Data Breaches by HIPAA-Regulated Entity
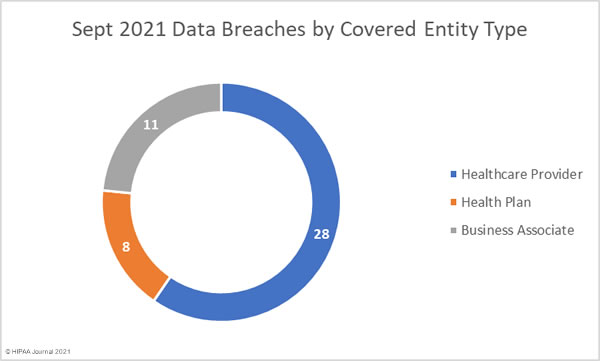
Healthcare providers were the worst affected covered entity with 30 reported breaches. 10 breaches were reported by health plans, 6 breaches were reported by business associates, and one breach was reported by a healthcare clearinghouse.
5 breaches of those breaches were reported by a HIPAA-covered entity but occurred at a business associate. The adjusted figures are shown in the pie chart below.
September 2021 Healthcare Data Breaches by State
Data breaches were reported by HIPAA-regulated entities based in 25 states. Texas was the worst affected state with 6 reported breaches of 500 or more records, followed by California with 5 breaches and Connecticut with 4.
| State |
Breaches |
| Texas |
6 |
| California |
5 |
| Connecticut |
4 |
| Florida & Washington |
3 |
| Arizona, Georgia, Illinois, New York, Ohio, & Pennsylvania |
2 |
| Alaska, Delaware, Indiana, Kentucky, Maryland, Minnesota, Missouri, New Jersey, New Mexico, Oregon, Rhode Island, Tennessee, Virginia, & Wisconsin |
1 |
HIPAA Enforcement Activity in September 2021
The Department of Health and Human Services’ Office for Civil Rights now has a new director, and it is currently unclear what direction she will take in the department’s HIPAA enforcement actions.
Since the fall of 2019 OCR has been targeting HIPAA-regulated entities that fail to comply with the HIPAA Right of Access and September saw the 20th financial penalty imposed under this initiative for the failure to provide individuals with access to their healthcare records.
Children’s Hospital & Medical Center in Omaha, NE, settled its HIPAA Right of Access case with OCR and paid an $80,000 financial penalty. This was the ninth OCR case this year to have resulted in a financial penalty for non-compliance with the HIPAA Rules.
There were no reported enforcement activities by state attorneys general in September.
The post September 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.




