High numbers of healthcare data breaches continued to be reported by HIPAA-covered entities and their business associates. In July, there were 70 reported data breaches of 500 or more records, making it the fifth consecutive month where data breaches have been reported at a rate of 2 or more per day.
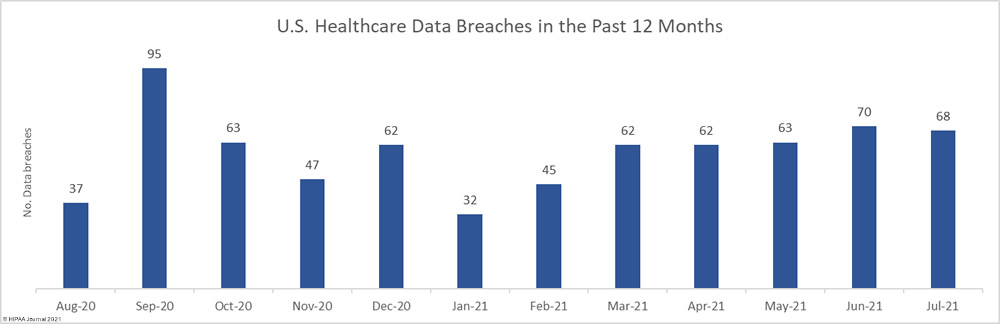
The number of breaches was slightly lower than June, but the number of records exposed or compromised in those breaches jumped sharply, increasing by 331.5% month-over-month to 5,570,662 records.
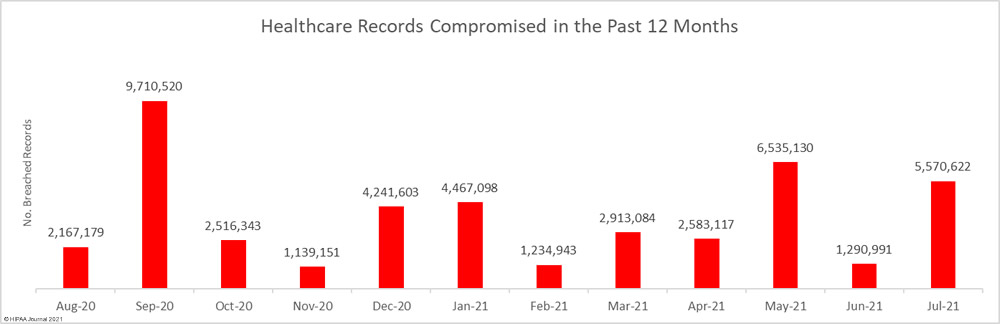
Over the past 12 months, from the start of August 2020 to the end of July 2021, there have been 706 reported healthcare data breaches of 500 or more records and the healthcare data of 44,369,781 individuals has been exposed or compromised. That’s an average of 58.8 data breaches and around 3.70 million records per month!
Largest Healthcare Data Breaches in July 2021
Two healthcare data breaches stand out due to the sheer number of healthcare records that were exposed – and potentially stolen. The largest healthcare data breach to be reported in July was a hacking/IT incident reported by the Wisconsin healthcare provider Forefront Dermatology. The exact nature of the attack was not disclosed so it is unclear if ransomware was used. Hackers gained access to parts of its network that contained the protected health information of 2.4 million individuals. The second largest data breach was reported by Practicefirst, a New York business associate of multiple HIPAA-covered entities. Ransomware was used in the attack and the healthcare data of 1.2 million individuals was potentially exfiltrated.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Breach Cause |
Business Associate Present |
| Forefront Dermatology, S.C. |
Healthcare Provider |
2,413,553 |
Hacking/IT Incident |
Unspecified hacking incident |
Yes |
| Professional Business Systems, Inc., d/b/a Practicefirst Medical Management Solutions/PBS Medcode Corp |
Business Associate |
1,210,688 |
Hacking/IT Incident |
Ransomware attack |
Yes |
| UF Health Central Florida |
Healthcare Provider |
700,981 |
Hacking/IT Incident |
Ransomware attack |
No |
| Orlando Family Physicians, LLC |
Healthcare Provider |
447,426 |
Hacking/IT Incident |
Phishing attack |
No |
| HealthReach Community Health Centers |
Healthcare Provider |
122,340 |
Improper Disposal |
Improper disposal of electronic medical records |
No |
| Guidehouse |
Business Associate |
84,220 |
Hacking/IT Incident |
Ransomware attack (Accellion FTA) |
Yes |
| Advocate Aurora Health |
Healthcare Provider |
68,707 |
Hacking/IT Incident |
Ransomware attack (Elekta) |
Yes |
| McLaren Health Care Corporation |
Healthcare Provider |
64,600 |
Hacking/IT Incident |
Ransomware attack (Elekta) |
Yes |
| Coastal Family Health Center, Inc |
Healthcare Provider |
62,342 |
Hacking/IT Incident |
Ransomware attack |
No |
| Florida Heart Associates |
Healthcare Provider |
45,148 |
Hacking/IT Incident |
Ransomware attack |
No |
| A2Z Diagnostics, LLC |
Healthcare Provider |
35,587 |
Hacking/IT Incident |
Phishing attack |
No |
| University of Maryland, Baltimore |
Business Associate |
30,468 |
Hacking/IT Incident |
Unspecified hacking incident |
Yes |
| Florida Blue |
Health Plan |
30,063 |
Hacking/IT Incident |
Brute force attack (Member portal) |
No |
| Intermountain Healthcare |
Healthcare Provider |
28,628 |
Hacking/IT Incident |
Ransomware attack (Elekta) |
Yes |
Causes of July 2021 Healthcare Data Breaches
As the table above shows, ransomware continues to be extensively used in cyberattacks on healthcare organizations and their business associates. Those attacks can easily result in the theft of large amounts of healthcare data. The majority of ransomware gangs (and their RaaS affiliates) are now exfiltrating sensitive data prior to using ransomware to encrypt files. Victims are required to pay to prevent the publication or sale of the stolen data as well as a payment to obtain the keys to decrypt files.
To help combat this rise in double extortion ransomware attacks, new guidance has been released by the Cybersecurity and Infrastructure Security Agency. The National Institute of Standards and Technology (NIST) has also updated its cybersecurity guidance on building resilient computer networks, with the emphasis now shifting away from perimeter defenses to assuming attackers have already gained access to the network. Mechanisms therefore need to be implemented to reduce the harm that can be caused.
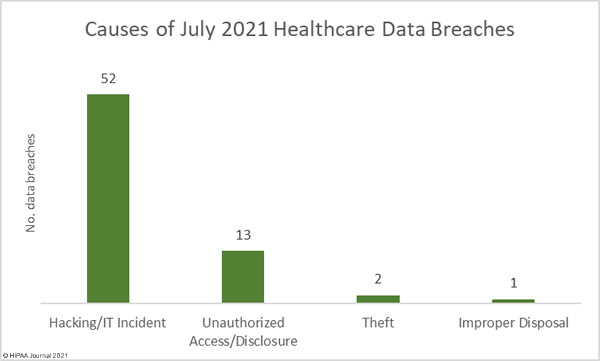
Hacking/IT incidents, of which ransomware accounts for a many, dominate the month’s breach reports. There were 52 reported hacking/IT incidents in which the protected health information of 5,393,331 individuals was potentially compromised. That’s 96.82% of all records breached in July. The mean breach size was 103,718 records and the median breach size was 4,185 records.
There were 13 reported unauthorized access/disclosure incidents, which include misdirected emails, mailing errors, and snooping by healthcare employees. 52,676 healthcare records were impermissibly viewed or disclosed to unauthorized individuals across those incidents. The mean breach size was 4,052 records and the median breach size was 1,038 records. There were two theft incidents reported involving a total of 2,275 records and one improper disposal incident involving 122,340 electronic health records.
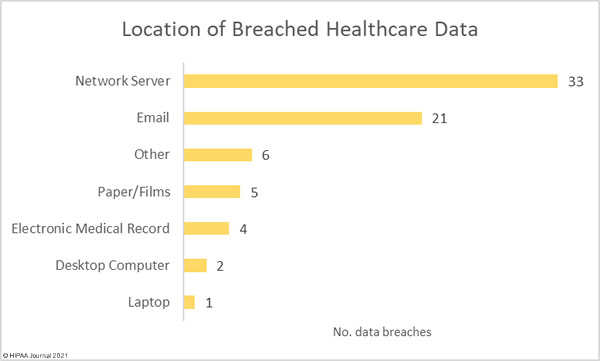
The vast majority of incidents involved the hacking of network servers; however, email accounts continue to be compromised at high rates. 21 breaches involved protected health information stored in email accounts. The majority of the email incidents involved the theft of employee credentials in phishing attacks.
Data Breaches by Covered Entity Type
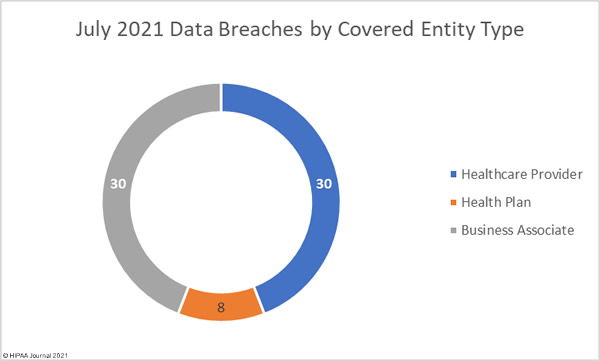
Healthcare providers reported 47 data breaches in July, with 11 breaches reported by business associates and 10 breaches reported by health plans; however, the reporting entity is not the best gauge of where these breaches occurred. In many cases, the breach was experienced at a business associate, but was reported by the covered entity.
When this is taken into account, the figures show that healthcare provider and business associate data breaches are on a par, with 30 breaches each for July 2021, as shown in the pie chart below.
July 2021 Healthcare Data Breaches by State
July saw healthcare data breaches reported by HIPAA-covered entities and business associates based in 32 states and the District of Columbia.
| State |
Number of Reported Healthcare Data Breaches |
| Florida |
6 |
| California, New York & Texas |
5 |
| Illinois & North Carolina |
4 |
| Connecticut, Minnesota, Nebraska & New Jersey |
3 |
| Mississippi, Oklahoma, Washington & Wisconsin |
2 |
| Alabama, Georgia, Iowa, Indiana, Kansas, Kentucky, Maine, Maryland, Massachusetts, Michigan, Missouri, Montana, Ohio, Pennsylvania, South Carolina, Utah, Virginia, West Virginia & the District of Columbia |
1 |
HIPAA Enforcement Activity in July 2021
The HHS’ Office for Civil Rights (OCR), the primary enforcer of HIPAA compliance, did not announce any new enforcement actions against HIPAA-covered entities or business associates in July, nor were there any enforcement actions announced by state Attorneys General.
The OCR year-to-date total still stands at 8 financial penalties totaling $5,570,100, with just the one financial penalty imposed by state attorneys general – A multi-state action that saw American Medical Collection Agency (AMCA) fined $21 million.
Data for this report came from the HHS’ Office for Civil Rights breach portal.
The post July 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.




