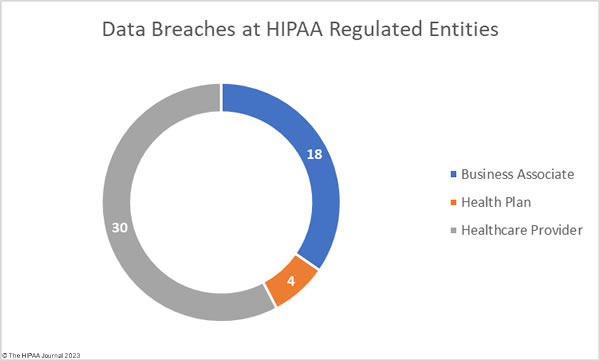
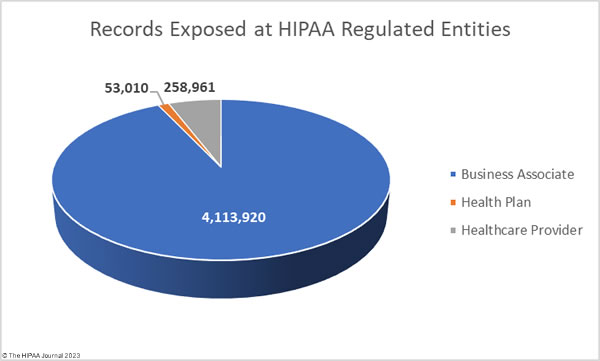
In a healthcare environment, you are likely to hear health information referred to as protected health information or PHI, but what is considered PHI under HIPAA? PHI is defined as different things by different sources. Some define PHI as patient health data (it isn´t), as the 18 HIPAA identifiers (it´s not those either), or as a phrase coined by the HIPAA Act of 1996 to describe identifiable information in medical records (close – except the term Protected Health Information was not used in relation to HIPAA until 1999).
What is Really Considered PHI Under HIPAA Rules?
To best explain what is really considered PHI under HIPAA compliance rules, it is necessary to review the definitions section of the Administrative Simplification Regulations (§160.103) starting with health information. According to this section, health information means any information, including genetic information, whether oral or recorded in any form or medium, that:
“Is created or received by a health care provider, health plan, public health authority, employer, life insurer, school or university, or health care clearinghouse; and relates to the past, present, or future physical or mental health or condition of an individual; the provision of health care to an individual; or the past, present, or future payment for the provision of health care to an individual.”
From here, we need to progress to the definition of individually identifiable health information which states “individually identifiable health information […] is a subset of health information, including demographic information collected from an individual [that] is created or received by a health care provider, health plan, employer, or health care clearinghouse […] and that identifies the individual or […] can be used to identify the individual.”
Finally, we move onto the definition of protected health information, which states “protected health information means individually identifiable health information transmitted by electronic media, maintained in electronic media, or transmitted or maintained in any other form or medium”.
More about what is Considered PHI under HIPAA
To simplify a definition of what is considered PHI under HIPAA: health information is any information relating a patient´s condition, the past, present, or future provision of healthcare, or payment thereof. It becomes individually identifiable health information when identifiers are included in the same record set, and it becomes protected when it is transmitted or maintained in any form (by a covered entity).
Generally, HIPAA covered entities are limited to health plans, health care clearinghouses, and healthcare providers that conduct electronic transactions for which the Department of Health and Human Services (HHS) has published standards. The standards can be found in Subparts I to S of the HIPAA Administrative Data Standards. Therefore:
- “A broken leg” is health information.
- “Mr. Jones has a broken leg” is individually identifiable health information.
- If a covered entity records “Mr. Jones has a broken leg” the health information is protected.
Where do Business Associates Enter the Equation?
As well as covered entities having to understand what is considered PHI under HIPAA, it is also important that business associates are aware of how PHI is defined. This is because any individually identifiable health information created, received, maintained, or transmitted by a business associate in the provision of a service for or on behalf of a covered entity is also protected.
Business associates are required to comply with the Security and Breach Notification Rules when providing a service to or on behalf of a covered entity. However, depending on the nature of service being provided, business associates may also need to comply with parts of the Administrative Requirements and the Privacy Rule depending on the content of the Business Associate Agreement.
When is PHI not PHI?
There is a common misconception that all health information is considered PHI under HIPAA, but this is not the case.
First, it depends on whether an identifier is included in the same record set. Under HIPAA, PHI ceases to be PHI if it is stripped of all identifiers that can tie the information to an individual. If identifiers are removed, the health information is referred to as de-identified PHI. HIPAA does not apply to de-identified PHI, and the information can be used or disclosed without violating any HIPAA Rules.
Health information is also not PHI when it is created, received, maintained, or transmitted by an entity not subject to the HIPAA Rules. For example, even though schools and colleges may have medical facilities, health information relating to students is covered by the Family Educational Rights and Privacy Act (FERPA) which classifies students´ health information as part of their educational records.
Health information maintained by employers as part of an employee´s employment record is not considered PHI under HIPAA. However, employers that administer a self-funded health plan do have to meet certain requirements with regards to keeping employment records separate from health plan records in order to avoid impermissible disclosures of PHI.
It is important to be aware that exceptions to these examples exist. One of the most complicated examples relates to developers, vendors, and service providers for personal health devices that create, collect, maintain, or transmit health information. Entities related to personal health devices are not covered entities or business associates under HIPAA unless they are contracted to provide a service for or on behalf of a covered entity or business associate.
However, entities related to personal health devices are required to comply with the Breach Notification Rule under Section 5 of the Federal Trade Commission Act if a breach of unsecured PHI occurs. This means that, although entities related to personal health devices do not have to comply with the Privacy and Security Rules, it is necessary for these entities to know what is considered PHI under HIPAA in order to comply with the Breach Notification Rule.
The complexity of determining if information is considered PHI under HIPAA implies that both medical and non-medical workforce members should receive HIPAA training on the definition of PHI. It is also important for all members of the workforce to know which standards apply when state laws offer greater protections to PHI or have more individual rights than HIPAA, as these laws will preempt HIPAA.
What is Considered PHI Under HIPAA FAQs
What are the 18 HIPAA Identifiers?
The 18 HIPAA identifiers are the identifiers that must be removed from a record set before any remaining health information is considered to be de-identified under the “safe harbor” method of de-identification (see §164.514). However, due to the age of the list, it is no longer a reliable guide. Since the list was first published in 1999, there are now many more ways to identify an individual,
Importantly, if a Covered Entity removes all the listed identifiers from a designated record set, the subject of the health information might be able to be identified through other identifiers not included on the list – for example, social media aliases, LBGTQ statuses, details about an emotional support animal, etc. Therefore, Covered Entities should ensure no further identifiers remain in a record set before disclosing health information to a third party (i.e., to researchers).
Also, because the list of 18 HIPAA identifiers is more than two decades out of date, the list should not be used to explain what is considered PHI under HIPAA – notwithstanding that any of these identifiers maintained separately from individually identifiable health information are not PHI in most circumstances and do not assume the Privacy Rule protections.
What is PHI under HIPAA?
PHI under HIPAA is individually identifiable health information that is collected or maintained by an organization that qualifies as a HIPAA Covered Entity or Business Associate. Additionally, any information maintained in the same designated record set that identifies – or could be used with other information to identify – the subject of the health information is also PHI under HIPAA.
What does PHI include?
PHI includes information about an individual´s physical or mental health condition, the treatment of that condition, or the payment for the treatment. Additionally, PHI includes any information maintained in the same record set that identifies – or that could be used to identify – the subject of the health, treatment, or payment information.
What are examples of PHI?
Examples of PHI include test results, x-rays, scans, physician’s notes, diagnoses, treatments, eligibility approvals, claims, and remittances. When combined with this information, PHI also includes names, phone numbers, email addresses, Medicare Beneficiary Numbers, biometric identifiers, emotional support animals, and any other identifying information.
Which format of PHI records is covered by HIPAA?
All formats of PHI records are covered by HIPAA. These include (but are not limited to) spoken PHI, PHI written on paper, electronic PHI, and physical or digital images that could identify the subject of health information. It is important to remember that PHI records are only covered by HIPAA when they are in the possession of a covered entity or business associate.
What is the difference between PHI and ePHI?
The different between PHI and ePHI is that ePHI refers to Protected Health Information that is created, used, shared, or stored electronically – for example on an Electronic Health Record, in the content of an email, or in a cloud database. Both PHI and ePHI are subject to the same protections under the HIPAA Privacy Rule, while the HIPAA Security Rule mostly relates to ePHI.
Does the Privacy Rule apply to both paper and electronic health information?
The Privacy Rule applies to both paper and electronic health information despite the language used in the original Health Insurance Portability and Accountability Act leading to a misconception that HIPAA only applies to electronic health records. While the protection of electronic health records was addressed in the HIPAA Security Rule, the Privacy Rule applies to all types of health information regardless of whether it is stored on paper or electronically, or communicated orally.
If an individual calls a dental surgery to make an appointment and leaves their name and telephone number, is that PHI?
If an individual calls a dental surgery to make an appointment and leaves their name and telephone number, the name and telephone number are not PHI at that time because there is no health information associated with them. Only once the individual undergoes treatment, and their name and telephone number are added to the treatment record, does that information become Protected Health Information.
How can future health information about medical conditions be considered “protected”?
Future health information about medical conditions can be considered protected if it includes prognoses, treatment plans, and rehabilitation plans that – if altered, deleted, or accessed without authorization – could have significant implications for a patient. For this reason, future health information must be protected in the same way as past or present health information.
Does the Privacy Rule apply when medical professionals are discussing a patient´s healthcare?
The Privacy Rule does apply when medical professionals are discussing a patient’s healthcare because, although PHI can be shared without authorization for the provision of treatment, when medical professionals discuss a patient´s healthcare, it must be done in private (i.e. not within earshot of the general public) and the Minimum Necessary Standard applies – the rule that limits the sharing of PHI to the minimum necessary to accomplish the intended purpose.
If a medical professional discusses a patient´s treatment with the patient´s employer, is that information protected?
If a medical professional discusses a patient’s treatment with the patient’s employer whether or not the information is protected depends on the circumstances. Usually, a patient will have to give their consent for a medical professional to discuss their treatment with an employer unless the discussion concerns payment for treatment or the employer is acting as an intermediary between the patient and a health plan.
However, disclosures of PHI to employers are permitted under the Privacy Rule if the information being discussed relates to a workplace injury or illness. In such circumstances, a medical professional is permitted to disclose the information required by the employer to fulfil state or OSHA reporting requirements. In these circumstances, medical professionals can discuss a patient’s treatment with the patient’s employer without an authorization.
Is an email PHI?
Whether or not an email is PHI depends on who the email is sent by, what the email contains, and where it is stored. To be PHI, an email has to be sent by a Covered Entity or Business Associate, contain individually identifiable health information, and be stored by a Covered Entity or Business Associate in a designated record set with an identifier (if the email does not already include one).
What is PHI is healthcare?
PHI in healthcare stands for Protected Health Information – information protected by the HIPAA Privacy Rule to ensure it remains private. PHI in healthcare can only be used or disclosed for permitted purposes without a patient´s authorization, and patients have the right to complain to HHS’ Office for Civil Rights if they believe a healthcare provider is failing to protect the privacy of their PHI.
What are HIPAA identifiers?
HIPAA identifiers are pieces of information that can be used – either separately or with other pieces of information – to identify an individual whose health information is protected by the HIPAA Privacy Rule. Several sources confuse HIPAA identifiers with PHI, but it is important to be aware identifiers not maintained with an individual´s health information do not have the same protection as PHI.
What qualifies as PHI?
What qualifies as PHI is individually identifiable health information and any identifying non-health information stored in the same designated record set. Please note that a Covered Entity can maintain multiple designated record sets about the same individual and that a designated record set can consist of a single item (i.e., a picture of a baby on a pediatrician’s baby wall qualifies as PHI).
Is a medical record number PHI?
A medical record number is PHI is it can identify the individual in receipt of medical treatment. However, a seemingly random alpha-numeric code by itself (which medical record numbers often are) does not necessarily identify an individual if the code is not proceeded with “medical record number”, or accompanied by a name or any other information that could be used to identify the individual.
What does PHI include?
PHI includes individually identifiable health information maintained by a Covered Entity or Business Associate that relates to an individual’s past, present, or future physical or mental health condition, treatment for the condition, or payment for the treatment. It can also include any non-health information that could be used to identify the subject of the PHI.
Is a person’s gender PHI?
A person’s gender is PHI if it is maintained in the same designated record set as individually identifiable health information by a HIPAA Covered Entity or Business Associate as it could be used with other information to identify the subject of the individually identifiable health information. However, if a person’s gender is maintained in a data set that does not include individually identifiable health information (i.e., a transportation directory), it is not PHI.
Is a patient’s name alone considered PHI?
A patient’s name alone is not considered PHI. Only when a patient’s name is included in a designated record set with individually identifiable health information by a Covered Entity or Business Associate is it considered PHI under HIPAA.
Under the Privacy Rule which information should be considered PHI?
Under the Privacy Rule, the information that should be considered PHI relates to any identifiers that can be used to identify the subject of individually identifiable health information. However, where several sources mistake what is considered PHI under HIPAA is by ignoring the definitions of PHI in the General Provisions at the start of the Administrative Simplification Regulations (45 CFR Part 160).
Is there a list of PHI identifiers?
There is no list of PHI identifiers in HIPAA – only an out-of-date list of identifiers that have to be removed from a designated record set under the safe harbor method before any PHI remaining in the designated record set is deidentified. Because the list is so out-of-date and excludes many ways in which individuals can now be identified, Covered Entities and Business Associates are advised to have a full understanding of what is considered PHI under HIPAA before developing staff policies.
Is a phone number PHI?
A phone number is PHI if it is maintained in a designated record set by a HIPAA Covered Entity or Business Associate because it could be used to identify the subject of any individually identifiable health information maintained in the same record set. However, if a phone number is maintained in a database that does not include individually identifiable health information, it is not PHI.
The post What is Considered PHI Under HIPAA? appeared first on HIPAA Journal.