HIPAA updates and HIPAA changes happen more frequently than many people are aware of because of the nature of the update or because of their minor impact on HIPAA compliance. A major update to HIPAA is long overdue, and steps were taken in December 2020 to address the need for HIPAA changes and HIPAA updates when HHS’ Office for Civil Rights (OCR) issued a Notice of Proposed Rulemaking that proposed multiple changes to the HIPAA Privacy Rule.
In addition, there has also been a proposed update to align 42 CFR Part 2 – the Confidentiality of Substance Use Disorder Patient Records regulations – more closely with HIPAA, and proposals to change the conditions under which PHI relating to reproductive healthcare can be used or disclosed. The Part 2 and reproductive health changes are expected to be finalized in 2024, while new proposed Security Rule standards for cybersecurity should be announced in 2024 and implemented in 2025.
We discuss all the HIPAA updates since the inception of HIPAA and this information can be used in conjunction with our HIPAA checklist to understand what is required to ensure compliance.
Please use the form on this page to arrange your free copy of the checklist.
Major HIPAA Updates in the Past 25 Years
Since HIPAA was signed into law there have been a few major HIPAA updates. The HIPAA Privacy and Security Rules were introduced which limited uses and disclosures of protected health information, gave patients new rights over their healthcare data, and introduced a set of minimum security standards.
Those HIPAA updates were followed by the incorporation of the Health Information Technology for Economic and Clinical Health (HITECH) Act, which saw the introduction of the Breach Notification Rule in 2009 and the Omnibus Final Rule in 2013. Such major HIPAA updates placed a significant burden on HIPAA-covered entities and considerable time and effort were required to introduce new policies and procedures to ensure continued HIPAA compliance.
There have been two minor HIPAA Privacy Rule changes since 2013 – the first, in 2014, allowed patients to have access to test reports to align the Privacy Rule with the Clinical Laboratory Improvement Amendments. The second HIPAA Privacy Rule change, in 2016, allowed covered entities to disclose PHI to the National Instant Criminal Background Check System.
The most commonly updated section of HIPAA is Part 162 of the Administrative Simplification Regulations. Part 162 HIPAA updates are most often made by CMS to existing standards – for example, the 2020 change relating to Schedule II drug refills. However, a proposed Part 162 HIPAA change expected to be finalized in 2024 could have wider implications.
HIPAA Changes in 2024
 Over the past few years, there have been increasing calls for HIPAA changes to decrease the administrative burden on HIPAA-covered entities, but the HIPAA 2024 rules and regulations are currently much the same as they were in 2013. OCR responded to feedback from healthcare industry stakeholders by issuing a request for information (RFI) in December 2018 on potential changes to the HIPAA Rules. OCR sought comments from HIPAA-covered entities about possible changes to HIPAA Rules in 2019 and beyond, which are mostly concerned with the easing of certain administrative requirements and the removal of certain provisions of the HIPAA Privacy Rule that have been limiting or discouraging the coordination of care. The comment period closed on February 12, 2019.
Over the past few years, there have been increasing calls for HIPAA changes to decrease the administrative burden on HIPAA-covered entities, but the HIPAA 2024 rules and regulations are currently much the same as they were in 2013. OCR responded to feedback from healthcare industry stakeholders by issuing a request for information (RFI) in December 2018 on potential changes to the HIPAA Rules. OCR sought comments from HIPAA-covered entities about possible changes to HIPAA Rules in 2019 and beyond, which are mostly concerned with the easing of certain administrative requirements and the removal of certain provisions of the HIPAA Privacy Rule that have been limiting or discouraging the coordination of care. The comment period closed on February 12, 2019.
OCR asked 54 different questions in its RFI. Some of the main aspects that were under consideration were:
- Patients’ right to access and obtain copies of their protected health information and the time frame for responding to those requests (Currently 30 days)
- Removing the requirement to obtain written confirmation of receipt of an organization’s notice of privacy practices
- Promotion of parent and caregiver roles in care
- Easing of restrictions on disclosures of PHI without authorization
- Possible exceptions to the minimum necessary standard for disclosures of PHI
- Changes to HITECH Act requirements for the accounting of disclosures of PHI for treatment, payment, and healthcare operations
- Encouragement of information sharing for treatment and care coordination
- Changing the Privacy Rule to make sharing PHI with other providers mandatory rather than permissible.
- Expansion of healthcare clearinghouses’ access to PHI
- Addressing the opioid crisis and serious mental illness
In 2019, then OCR Director, Roger Severino, said, “We are committed to pursuing the changes needed to improve quality of care and eliminate undue burdens on covered entities while maintaining robust privacy and security protections for individuals’ health information.”
The aim of the HHS is to implement changes that will make compliance less of a burden without negatively affecting patient privacy or decreasing the security of individuals’ protected health information (PHI). There are no planned changes to the HIPAA Security Rule in this RFI, but several HIPAA Privacy Rule changes have been proposed.
It has been suggested that in many of the areas covered by the RFI, the best solution may not be HIPAA rule changes. Guidance was issued in 2022 and 2023, and it is likely further HIPAA guidance will be issued in 2024 to tackle some of the issues currently experienced with HIPAA compliance by clearing up misconceptions and correcting false interpretations of the HIPAA requirements. However, changes to HIPAA in 2024 are now likely to be implemented, although it may take until 2025 for all the changes to become effective.
Proposed HIPAA Privacy Rule Changes in 2024
OCR issued a Notice of Proposed Rulemaking on December 10, 2020, that detailed the HIPAA changes to the Privacy Rule due to be implemented, based on the responses to its December 2018 RFI. The proposed changes are limited, and several HIPAA Privacy Rule changes that healthcare industry stakeholders have been campaigning for have not been included. Most of the proposed HIPAA changes are relatively minor tweaks to strengthen patient access to PHI, facilitate data sharing, and ease the administrative burden on HIPAA-covered entities.
In 2021, OCR sought feedback on the proposed HIPAA changes for 60 days from the date of publication in the Federal Register, with the comment period extended for a further 45 days to give healthcare industry stakeholders more time to review the proposed changes and provide their feedback. OCR has read the comments and the publication of the Final Rule is now imminent.
The proposed updates to the HIPAA Privacy Rule are as follows:
- Allowing patients to inspect PHI in person and take notes or photographs of their PHI.
- Changing the maximum time to provide access to PHI from 30 days to 15 days.
- Restricting the right of individuals to transfer ePHI to a third party to only ePHI that is maintained in an EHR.
- Confirming that an individual is permitted to direct a covered entity to send their ePHI to a personal health application if requested by the individual.
- Stating when individuals should be provided with ePHI without charge.
- Requiring covered entities to inform individuals that they have the right to obtain or direct copies of their PHI to a third party when a summary of PHI is offered instead of a copy.
- The Armed Forces’ permission to use or disclose PHI to all uniformed services has been expanded.
- A definition has been added for electronic health records.
- Wording change to expand the ability of a covered entity to disclose PHI to avert a threat to health or safety when harm is “seriously and reasonably foreseeable.” (currently it is when harm is “serious and imminent.”)
- A pathway has been created for individuals to direct the sharing of PHI maintained in an EHR among covered entities.
- Covered entities will not be required to obtain a written acknowledgment from an individual that they have received a Notice of Privacy Practices.
- HIPAA-covered entities will be required to post estimated fee schedules on their websites for PHI access and disclosures.
- HIPAA-covered entities will be required to provide individualized estimates of the fees for providing an individual with a copy of their own PHI.
- The definition of healthcare operations has been broadened to cover care coordination and case management.
- Covered healthcare providers and health plans will be required to respond to certain records requests from other covered healthcare providers and health plans when individuals direct those entities to do so when they exercise the HIPAA right of access.
- Covered entities will be permitted to make certain uses and disclosures of PHI based on their good faith belief that it is in the best interest of the individual.
- The addition of a minimum necessary standard exception for individual-level care coordination and case management uses and disclosures, regardless of whether the activities constitute treatment or health care operations.
The Proposed HIPAA Changes Will Create Challenges for Healthcare Providers
 The pending HIPAA updates are intended to ease the administration burden on HIPAA-covered entities, although in the short term, the burden will be increased. Updates will need to be made to policies and procedures and changes will be required for notices of privacy practices, although there will not, at least, be the requirement to obtain written acknowledgment that updated NPPs have been received.
The pending HIPAA updates are intended to ease the administration burden on HIPAA-covered entities, although in the short term, the burden will be increased. Updates will need to be made to policies and procedures and changes will be required for notices of privacy practices, although there will not, at least, be the requirement to obtain written acknowledgment that updated NPPs have been received.
What is certain is HIPAA officers and other compliance staff will have a busy few months when the Final Rule is published. OCR will provide sufficient notice before the 2024 HIPAA changes take effect and become enforceable, but there will likely be a lot of work to be done. It will be important to create a plan for making all of the required changes to ensure they are fully implemented ahead of the compliance deadline.
When the Final Rule is published, there will be a requirement to change policies and procedures where necessary, and that will require retraining of employees. HIPAA requires training to be provided to the workforce during or soon after onboarding, and after any material change in policies and procedures. HIPAA training may not need to be provided to the entire workforce, but a significant number of employees will need to be trained, and that is likely to place a considerable burden on covered entities and has the potential to cause workflow disruptions.
Improved access to medical records could pose problems for healthcare providers, who will need to ensure they have sufficient staffing and efficient procedures for verifying identities and providing copies of records – especially as the time frame for providing those records will be shortened from 30 days to 15 days. The extension will also be shortened to 15 days, giving healthcare organizations a maximum of 30 days to provide the requested records.
The definition of EHRs has also been updated to include billing records, and these will need to be provided to patients who request a copy of their PHI. That has the potential to make it more time-consuming to provide copies, as billing records are often kept in different systems than healthcare records. It may be necessary to access two different systems in order to provide patients with a copy of their records.
It will be easy for bottlenecks to occur and important not to get into a situation where 15 day extensions are regularly required. There could well be a need to prioritize requests to make sure patients who urgently need a copy of their records get them in a timely manner. Bear in mind that OCR is laser-focused on healthcare providers that fail to provide patients with timely access to their medical records.
Another of the changes related to patient access is the requirement to allow patients to take notes and photographs of their PHI. There will need to be designated places where patients can inspect PHI privately and, if required, take photographs. Healthcare providers will need to implement safeguards to ensure patients are not taking photographs of PHI they are not authorized to see.
The proposed HIPAA changes prohibit covered entities from imposing unreasonable measures on individuals exercising their right of access, including unreasonable identity verification requirements. That has the potential to cause problems for healthcare providers.
A definition has also been proposed for a personal health application. If finalized, patients must be allowed to have their records sent to a personal health application of their choosing. However, there may be privacy risks associated with doing so, and patients will need to be made aware of those risks. That will add an additional burden on healthcare providers, who may not necessarily have the required information to determine whether there is a privacy and security risk.
Proposed Part 2 and HIPAA Changes in 2024
In November 2022, OCR and the Substance Abuse and Mental Health Services Administration (SAMHSA) issued a Notice of Proposed Rulemaking (NPRM) which sees both Part 2 and HIPAA changes to better align these regulations.
Part 2 protects patient privacy and records related to treatment for substance use disorder (SUD) with HIPAA applying to protected health information. SUD records are treated differently as they are highly sensitive and require greater protection and restrictions than other health information covered by the HIPAA Privacy Rule. While these additional protections are important, they can hamper care coordination due to the barriers that they put in the way of information sharing.
The proposed changes are intended to ease the complexity of compliance with HIPAA and Part 2, break down barriers to information sharing, and improve care coordination, without removing protections for patients. The update expands patient rights regarding the uses and disclosures of their SUD records.
The key changes that were proposed are:
- Single patient consent for all future uses and disclosures of SUD records for treatment, payment, and healthcare operations.
- Permitted to redisclose SUD records in accordance with the HIPAA Privacy Rule
- Patients will be able to obtain an accounting of disclosures of their SUD records and request restrictions on certain disclosures
- Expansion of prohibitions on the use and disclosure of Part 2 records in civil, criminal, administrative, and legislative proceedings
- Part 2 programs must establish a complaints process about Part 2 violations and must not require patients to waive the right to file a complaint as a condition of providing treatment, enrollment, payment, or eligibility for services.
- The breach notification requirements will apply to Part 2 records, which will be covered by the HIPAA Breach Notification Rule.
- The HIPAA Privacy Rule Notice of Privacy Practices requirements have been updated to address uses and disclosures of Part 2 records and individual rights with respect to those records.
- The HHS will be able to impose civil money penalties for violations of Part 2, in line with HIPAA and the HITECH Act
The NPRM was issued in November 2022 and there is a 60-day comment period, so it is highly likely that the final rule will be issued in 2024. Covered entities will then be given time to implement the changes before they become enforceable.
HITECH Act Updated in 2021 Regarding Recognized Security Practices
Many healthcare industry stakeholders had been campaigning for the addition of a safe harbor for HIPAA-covered entities and business associates that have adopted a common security framework and have implemented industry-standard security best practices, yet still experienced a data breach. It is not possible to prevent all cyberattacks and data breaches, and it is unfair to punish HIPAA-regulated entities for impermissible disclosures of ePHI when they have made all reasonable efforts to secure their systems.
A bill was proposed in 2020 that called for the HHS to consider the recognized security practices that have been adopted by HIPAA-regulated entities, that have been in place for the 12 months prior to a data breach occurring when deciding on financial penalties and other sanctions. The bill, HR 7898, was signed into law by President Trump on January 5, 2021.
The purpose of the bill is to encourage healthcare organizations to invest in security and adopt a recognized security framework by providing an incentive. The HITECH Act update has not created a safe harbor for HIPAA-regulated entities that have adopted a security framework and have implemented industry-standard security best practices, but OCR will consider the efforts made with respect to security when making determinations in its investigations of complaints and data breaches.
HIPAA-regulated entities that are able to demonstrate they have adopted recognized security practices will benefit from a decrease in the length and extent of audits and investigations of data breaches, and OCR will consider recognized security practices as a mitigating factor to reduce any financial penalties that would otherwise have been applied.
In 2022, in response to another request for information, OCR published a video that explains what recognized security practices are and the evidence that can be submitted to prove they have been in place. OCR said that when investigations are launched, OCR will write to the HIPAA-regulated entity and provide an opportunity for evidence of recognized security practices to be submitted.
HIPAA Fines and Settlements Due to be Shared with Victims of HIPAA Violations
In addition to requesting information on recognized security practices, OCR sought comments on how to implement a requirement of the HITECH Act regarding financial penalties and settlements for HIPAA violations. Section 13410(c)(1) of the HITECH Act requires OCR to share a portion of the funds it receives from its HIPAA enforcement activities with the victims of HIPAA violations. This is important, as there is no private cause of action in HIPAA, which means individuals cannot sue HIPAA-regulated entities for HIPAA violations that have resulted in harm being caused.
The problem for OCR – which is why this requirement has not been implemented to date – is the difficulty in implementing a fair method of determining what victims should receive. In its April 6, 2022, RFI, OCR requested comments to help OCR with establishing a methodology under which an individual who is harmed by an offense punishable under HIPAA may receive a percentage of any civil money penalty or monetary settlement collected with respect to the offense.
The Government Accountability Office (GAO) has shared a methodology for sharing funds, but OCR is seeking comment on any alternative methodologies. The main problem, however, is identifying the types of harms that should be considered in the distribution of CMPs and monetary settlements to harmed individuals, as “harm” is not defined by statute.
No timescale has been provided on when a Notice of Proposed Rulemaking will be issued in this regard, or when funds will start to be shared with victims of HIPAA violations. These HIPAA changes could occur in 2024, but it may be some years before this HITECH Act requirement is implemented.
HIPAA Changes Due to the 2019 Novel Coronavirus (SARS-CoV-2) and COVID-19
 In response to the 2019 Novel Coronavirus pandemic, the HHS announced major changes to the enforcement of HIPAA compliance in 2020, which will remain in place for the duration of the nationwide COVID-19 public health emergency or until the Secretary of the HHS declares the public health emergency is over. These “unprecedented HIPAA flexibilities” were announced in March and April by means of Notices of Enforcement Discretion and are intended to ease the burden on healthcare organizations and business associates that are having to overcome major challenges testing and treating COVID-19 patients. The changes to HIPAA enforcement have been introduced to ensure that HIPAA compliance does not get in the way of the provision of high-quality patient care.
In response to the 2019 Novel Coronavirus pandemic, the HHS announced major changes to the enforcement of HIPAA compliance in 2020, which will remain in place for the duration of the nationwide COVID-19 public health emergency or until the Secretary of the HHS declares the public health emergency is over. These “unprecedented HIPAA flexibilities” were announced in March and April by means of Notices of Enforcement Discretion and are intended to ease the burden on healthcare organizations and business associates that are having to overcome major challenges testing and treating COVID-19 patients. The changes to HIPAA enforcement have been introduced to ensure that HIPAA compliance does not get in the way of the provision of high-quality patient care.
On April 11, 2023, OCR announced that the Secretary of the Department of Health and Human Services will not be renewing the COVID-19 Public Health Emergency, which is due to expire on May 11, 2023. That means the flexibilities introduced through the following Notifications of Enforcement Discretion will come to an end at 11:59 pm on May 11, 2023. From that date and time there will be no further flexibilities and non-compliance will be penalized in the same manner as before the COVID-19 pandemic. There is one exception concerning telehealth. OCR will implement a 90-day transition period, where the flexibilities will continue until 11:59 pm on August 11, 2023, and fines will not be issued with regard to the good faith provision of telehealth services up to that date.
Notification of Enforcement Discretion for Telehealth Remote Communications
The first Notice of Enforcement Discretion was announced by OCR on March 17, 2020. The coronavirus pandemic has seen social distancing measures introduced, and with hospitals dealing with huge numbers of cases, Americans are being encouraged to remain indoors. In order to continue to provide quality care to patients while reducing the risk of patients transmitting or contracting COVID-19, telehealth services have been expanded. The CMS has also expanded telehealth to include all Medicare and Medicaid beneficiaries.
To help ensure that patients receive the care they need, OCR has announced that it will not impose sanctions and penalties on healthcare providers in association with the good faith provision of telehealth services for the purpose of diagnosis and treatment, regardless of whether the telehealth services are directly related to COVID-19. OCR will not impose penalties on healthcare providers in relation to the use of everyday communication technologies for providing those services, even if the platforms used are not completely compliant with HIPAA. For instance, it is permissible to use Skype (rather than Skype for Business), FaceTime, Google Hangouts Video, and Zoom. It is not permitted to use public-facing platforms to provide these services, such as Facebook Live and TikTok.
“We are empowering medical providers to serve patients wherever they are during this national public health emergency,” said Roger Severino, OCR Director. “We are especially concerned about reaching those most at risk, including older persons and persons with disabilities.”
This Notification of Enforcement Discretion will end at 11:59 pm on May 11, 2023. The ‘grace period’ will last for 90 days, so the hard date for compliance is 11:59 pm on August 11, 2023.
Notification of Enforcement Discretion to Allow Uses and Disclosures of Protected Health Information by Business Associates for Public Health and Health Oversight Activities
The second Notice of Enforcement Discretion was announced by OCR on April 2, 2020, and concerns uses and disclosures of PHI by business associates of HIPAA-covered entities for reasons related to public health and health oversight activities. HIPAA does not permit business associates to disclose PHI for public health and health oversight activities unless it is stated that they can do so in their business associate agreement (BAA) with a HIPAA-covered entity.
Under the Notice of Enforcement Discretion, OCR will not impose sanctions and penalties on business associates or their covered entities for these uses and disclosures to the likes of Federal public health authorities and health oversight agencies, such as the Centers for Disease Control and Prevention (CDC) and Centers for Medicare and Medicaid Services (CMS), state and local health departments, and state emergency operations centers. Should such a use or disclosure occur, the business associate must notify the covered entity within 10 days of the use or disclosure.
“The CDC, CMS, and state and local health departments need quick access to COVID-19 related health data to fight this pandemic,” said Roger Severino. “Granting HIPAA business associates greater freedom to cooperate and exchange information with public health and oversight agencies can help flatten the curve and potentially save lives.”
This Notification of Enforcement Discretion will end at 11:59 pm on May 11, 2023.
Notification of Enforcement Discretion for Community-Based Testing Sites
The third Notice of Enforcement Discretion was announced by OCR on April 9, 2020 – backdated to March 13, 2020 – and concerns the good faith participation in the operation of COVID-19 testing centers. OCR will be exercising enforcement discretion and will not impose sanctions and penalties on healthcare providers, including pharmacies, and business associates that participate in the operation of COVID-19 testing sites such as mobile testing centers, walk-up facilities, and drive-through testing centers that only provide COVID-19 specimen collection or testing services to the public.
“We are taking extraordinary action to help the growth of mobile testing sites so more people can get tested quickly and safely,” said Roger Severino. “President Trump has ordered the federal government to use every tool available to help save lives during this crisis, and this announcement is another concrete example of putting the President’s directive into action.”
This Notification of Enforcement Discretion will end at 11:59 pm on May 11, 2023.
Notice of Enforcement Discretion Regarding Online or Web-Based Scheduling Applications for Scheduling of COVID-19 Vaccination Appointments
OCR announced a further Notice of Enforcement Discretion on January 19, 2021, that concerns the scheduling of appointments for COVID-19 vaccinations. OCR said financial penalties and sanctions would not be imposed on HIPAA-covered entities or their business associates for violations of the HIPAA Rules in relation to the good faith use of online or web-based scheduling applications (WBSAs) for scheduling appointments for COVID-19 vaccinations.
WBSAs that would not be fully compliant with the HIPAA Rules under normal circumstances can be used for scheduling COVID-19 vaccination appointments without penalty, although it is not permitted to use a WBSA that does not incorporate reasonable security safeguards to ensure the privacy and security of ePHI and the Notice of Enforcement Discretion does not apply if the solution provider has prohibited the use of the WBSA for scheduling healthcare appointments.
OCR explained that the Notice of Enforcement Discretion does not apply to the use of a WBSA for anything other than scheduling COVID-19 vaccination appointments, such as arranging appointments for other medical services or for screening individuals for COVID-19 prior to arranging an in-person healthcare visit.
OCR encourages HIPAA-covered entities and their business associates to implement reasonable safeguards to ensure the privacy and security of healthcare data, such as adhering to the minimum necessary standard when inputting data, using encryption if available, and ensuring all privacy settings in the WBSA are activated.
OCR will be exercising enforcement discretion retroactive to December 11, 2020. This Notification of Enforcement Discretion will end at 11:59 pm on May 11, 2023.
HIPAA Penalties Could Officially Change in 2024
A HIPAA change occurred in 2019 concerning the penalties for HIPAA violations. OCR issued a Notice of Enforcement Discretion in 2019 which stated that OCR has adopted a new penalty structure for non-compliance with HIPAA Rules after a reevaluation of the requirements of the HITECH Act.
The HITECH Act called for penalties for HIPAA violations to be increased and, in 2013, the HHS implemented a new HIPAA penalty structure with minimum and maximum penalties set for the four penalty tiers, based on the level of culpability. In each category, a maximum penalty of $1.5 million, per violation category, per year was set. The HHS reviewed the language of the HITECH Act in 2019 and interpreted the requirements of the HITECH Act differently. “Upon further review of the statute by the HHS Office of the General Counsel, HHS has determined that the better reading of the HITECH Act is to apply annual limits.”
Rather than a maximum penalty of $1.5 million per year in all four categories, the maximum fine was reduced in the first three tiers. The current minimum and maximum penalties, adjusted for inflation, can be found here.
Currently, OCR is using the new penalty structure, as detailed in the Notice of Enforcement Discretion published in the Federal Register. While that remains in effect indefinitely, the new penalty structure is not legally binding and can be changed at any time. It is possible that this change to HIPAA will be made official in 2024, although first, a Notice of Proposed Rulemaking will need to be issued. OCR is more likely to continue to use its new interpretation under its Notice of Enforcement Discretion without making it official.
OCR has been pushing Congress to increase the maximum penalties for HIPAA violations as the total funds from OCR’s enforcement actions decreased significantly when the new penalty structure was introduced. OCR’s budget is extremely stretched as funding for the department has remained flat for years despite increasing numbers of hacking incidents and data breaches which has significantly increased OCR’s workload.
As well as the expected HIPAA updates in 2024, OCR will continue to issue HIPAA guidance in 2024 to explain how HIPAA applies in certain situations and to clear up confusion about the requirements of HIPAA. However, what originally starts as guidance could evolve into new HIPAA rulemaking. An example of this is OCR’s response to the Supreme Court decision in Dobbs v. Jackson Women’s Health Organization and the overturning of Roe v Wade, which removed the federal right to an abortion. OCR originally confirmed, through guidance, how the HIPAA Privacy Rule applies to disclosures of reproductive health information, but has since published an NPRM to tackle evolving issues related to this case.
Proposed Changes to Privacy Rule for Reproductive Health Care
According to the NPRM, issues relating to currently permissible uses and disclosures of PHI have evolved due to an increasing number of women in anti-abortion states travelling to other states to have “legal” terminations. Under §164.512(e) of the Privacy Rule, covered entities are permitted to disclose PHI for civil, criminal, or administrative proceedings.
Some states have enacted anti-abortion legislation that criminalizes the facilitation of a termination regardless of where it takes place. Courts in these states could subpoena PHI from covered entities in neighboring “legal” states in pursuit of a criminal conviction against any person who has assisted an individual in obtaining an abortion – including the covered entity.
OCR is concerned that the fear of PHI being disclosed for a procedure considered legal in the location where the procedure was administered could discourage patients from sharing important information with their healthcare providers and dissuade some healthcare providers from performing terminations for out-of-state citizens.
To address these concerns, OCR is proposing changes to the HIPAA Privacy Rule that include the creation of a new category of PHI – “reproductive health care” – and placing limitations on how it can be used and disclosed. These limitations are similar to those for genetic information inasmuch as it will not be possible to disclose reproductive health care records without an attestation it will not be used impermissibly.
The proposals will not only cover terminations, but other reproductive healthcare information, such as the provision of contraceptives (or the provision of contraception advice), fertility treatments, and pregnancy screening. Miscarriage management will also be included in the new category of PHI, as will diagnoses and treatments of conditions related to the reproductive system – even if the recipient of the diagnoses and treatments is not of reproductive age.
Other measures proposed in the NPRM include a new category of uses and disclosures – “Attested uses and disclosures” – which may well be used to align the HIPAA Privacy Rule with Part 2 privacy requirements. Under the new category, recipients of PHI will have to attest that it will not be further used or disclosed for prohibited purposes – i.e., in the case of reproductive health care, to support a civil, criminal, or administrative investigation or proceeding.
Covered entities are already being alerted to the fact that, if the proposals are finalized, any false attestations will be considered notifiable data breaches, while the person(s) that further disclose attested PHI will be in violation of §1177 of the Social Security Act for the wrongful disclosure of individually identifiable health information. Violations of this section are considered to be criminal violations carrying a maximum penalty of up to ten years in jail and a fine of up to $250,000.
HIPAA Security Rule Changes Proposed in Concept Paper
In December 2023, HHS published a Healthcare Sector Cybersecurity Strategy which proposes a framework to help the healthcare sector address cybersecurity threats. The framework is built on the development of cybersecurity goals for the healthcare sector, the incentivization of hospitals to adopt cybersecurity practices, and penalties for those that fail to meet cybersecurity goals.
The penalties will consist of disbarment from Medicare and Medicaid programs for any hospital CMS considers not to have complied with the yet-to-be-produced goals, and civil monetary penalties imposed by HHS’ Office for Civil Rights for any covered entity or business associate that fails to comply with yet-to-be-published Security Rule standards.
In a document outlining the Strategy, HHS states it will begin updating HIPAA Security Rule standards in the Spring of 2024, while working with Congress to increase the civil monetary penalties for HIPAA violations and increase the resource available to investigate potential violations and conduct “proactive audits”. This implies there could also be a 2024 HIPAA audit program on the horizon.
Other HIPAA Rule Changes May Lead to Future Updates
HIPAA rule changes are not exclusive to the Privacy, Security, and Breach Notification Rules. There have been a number of HIPAA rule changes relating to transaction code sets and identifiers (Part 162 of the HIPAA Administrative Simplification Regulations). Usually, these rule changes have a limited impact on covered entities and business associates; however, a proposed HIPAA rule change published in December 2022 could have implications for many day-to-day healthcare operations.
The proposed HIPAA rule change was published by CMS to resolve an issue concerning healthcare attachment transactions. These transactions occur when a health plan needs further information from a healthcare provider to authorize a treatment or pay a bill. Healthcare providers can also provide further information when submitting an authorization request or bill to accelerate treatment and/or payment.
The issue exists because further information cannot be “attached” to an existing transaction and has to be faxed or mailed separately. To resolve the issue, CMS is proposing three new transaction codes. However, in order to authenticate users, ensure the integrity of the attachment, and guarantee nonrepudiation, attachments transmitted using the new codes will have to be digitally signed. To address this issue, CMS has proposed a standard for acceptable e-signatures.
Compliance with the e-signature standard is only necessary when covered entities use the transaction codes to submit attachments electronically. There is no requirement to digitally sign attachments when they are faxed or sent through the mail. It is considered that, like most previous Part 162 HIPAA rule changes, the proposals will have a limited impact on covered entities and business associates.
However, the possibility exists that the proposed standard may be extended to other transactions in the future, and then to day-to-day healthcare operations. As this article discusses, there are a number of ways in which e-signatures are used in day-to-day healthcare operations; and, if the e-signature requirements are rolled out across the rest of the Administrative Simplification Regulations, covered entities and business associates may have to make some significant procedural changes.
FAQs
If HIPAA settlement sharing is introduced, will that result in more fines being issued?
If HIPAA settlement sharing is introduced, it is unlikely to result in more fines being issued by HHS’ Office for Civil Rights. Although the agency may come under pressure to pursue more settlements, there has been no indication that the current policy of voluntary compliance wherever possible will be reviewed.
How was HIPAA updated by the Omnibus Final Rule in 2013?
When HIPAA was updated by the Omnibus Final Rule in 2013, the major changes included further limiting permissible uses and disclosures of PHI, expanding patients’ rights, and making business associates directly liable for HIPAA violations attributable to their non-compliance. The Omnibus Final Rule also confirmed the new violation penalty structure imposed by the HITECH Act.
When was HIPAA last updated?
HIPAA was last updated in 2020 when the Centers for Medicare and Medicaid Services (CMS) published the Interoperability and Patient Access Final Rule. Although some provisions of this Final Rule have since been rescinded or delayed, or are subject to review, CMS is pushing forward with giving patients more choices about how they access PHI despite concerns about security risks.
What were the changes in 2017 that impacted HIPAA compliance?
The changes in 2017 that impacted HIPAA compliance relate to changes in 42 CFR Part 2 of the Public Welfare Code. These changes placed stricter conditions on the uses and disclosures of PHI when a patient is suffering a substance abuse disorder (SUD) and impact HIPAA compliance for providers in this field of healthcare who may have to have a three-tier structure for protecting SUD-related PHI, other PHI, and non-protected personal information.
Where is the best place to find changes to the HIPAA standards?
The best place to find changes to the HIPAA standards in the Administrative Simplification Regulations is the HHS’ Office for Civil Rights website. The website provides the opportunity for visitors to register for a “Weekly News Digest” that will deliver new about Proposed Rules, Interim Rules, and Final Rules straight to your email inbox.
How will HHS announce HIPAA changes in 2024?
HHS will announce HIPAA changes in 2024 via one or more Final Rules published in the Federal Register. Once a Final Rule is published in the Federal Register, HHS will publish a News Release on its website. HHS News Releases are usually widely reported in trade publications and on compliance websites, so it is unlikely that a major change to HIPAA in 2024 will go unnoticed.
Where can compliance officers find the latest version of HIPAA?
Compliance officers can find the latest version of the HIPAA Administrative Simplification Regulations on the eCFR website (https://www.ecfr.gov/). The Administrative Simplification Regulations are in three Parts – 45 CFR 160, 162, and 164. Part 164 includes the Security Rule (Subpart C), the Breach Notification Rule (Subpart D), and the Privacy Rule (Subpart E), but compliance officers should not omit to review other Parts of the Title to identify any other standards that apply.
Will There be an Omnibus HIPAA Final Rule 2024?
It is unlikely there will be an Omnibus Final Rule 2024 due to the volume and variety of new regulations being proposed. While it may be possible that proposed changes to the HIPAA Privacy Rule are amalgamated with proposed changes to 42 CFR Part 2, other proposals – such as electronic signatures, attestations, and interoperability – may be introduced separately and then expanded to other areas of HIPAA in subsequent rule making.
The post HIPAA Updates and HIPAA Changes in 2023-2024 appeared first on HIPAA Journal.
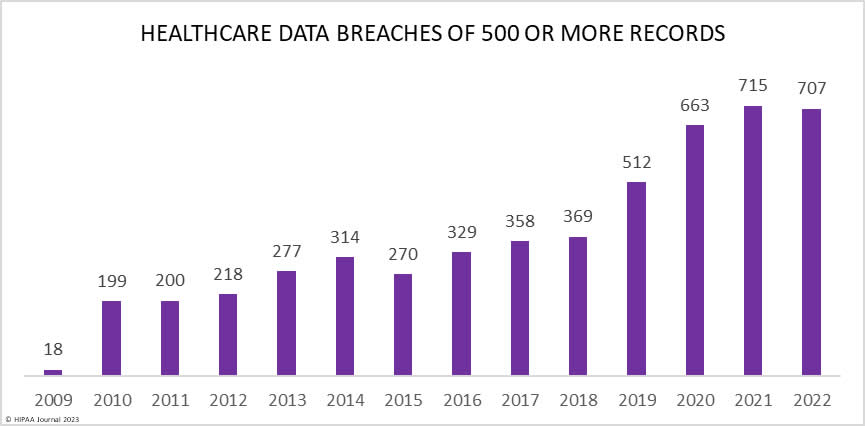
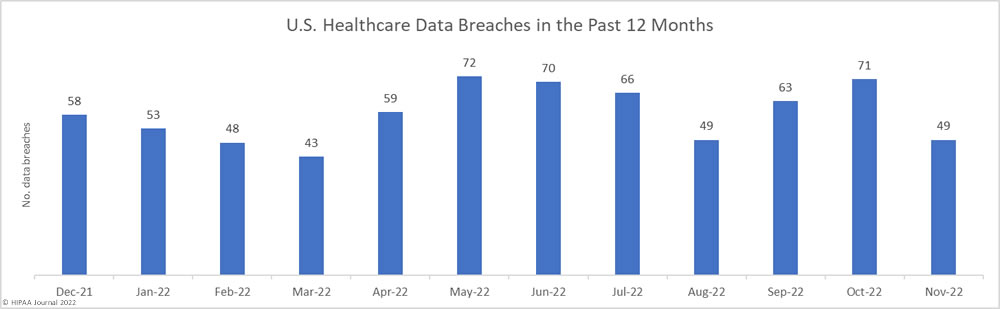
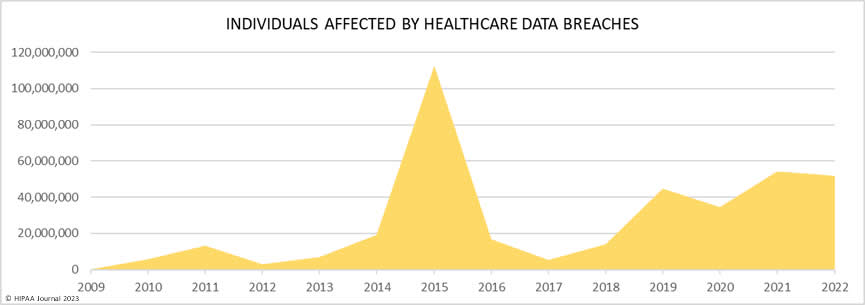
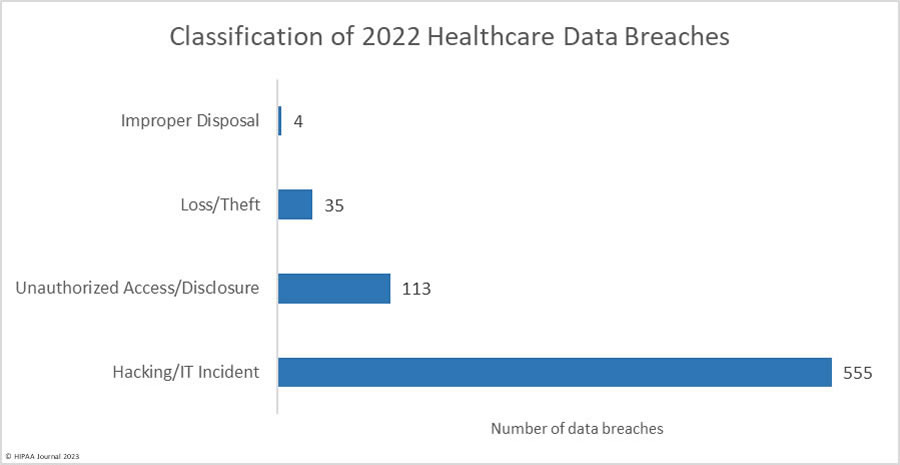
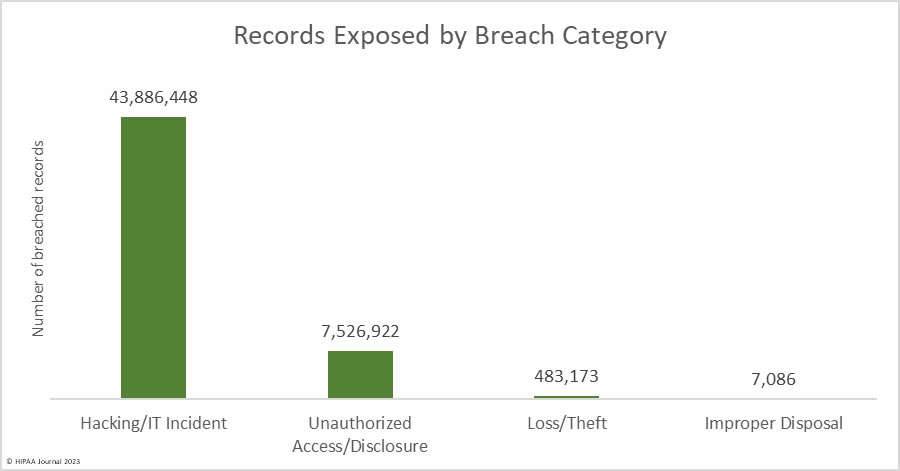
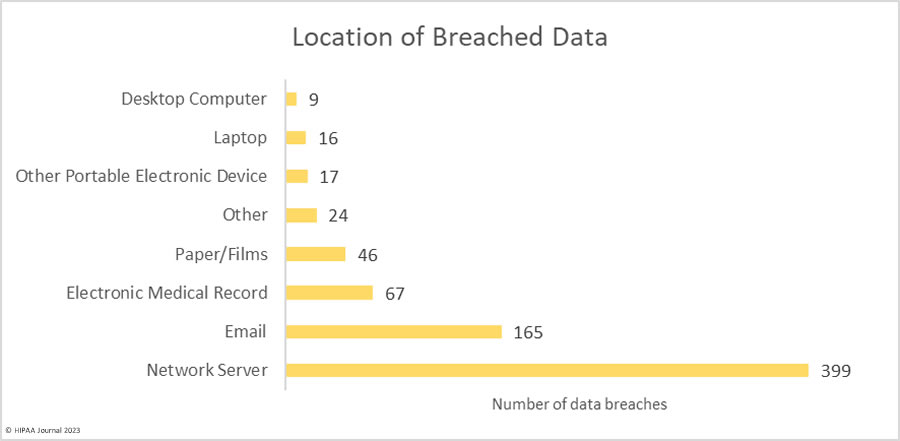

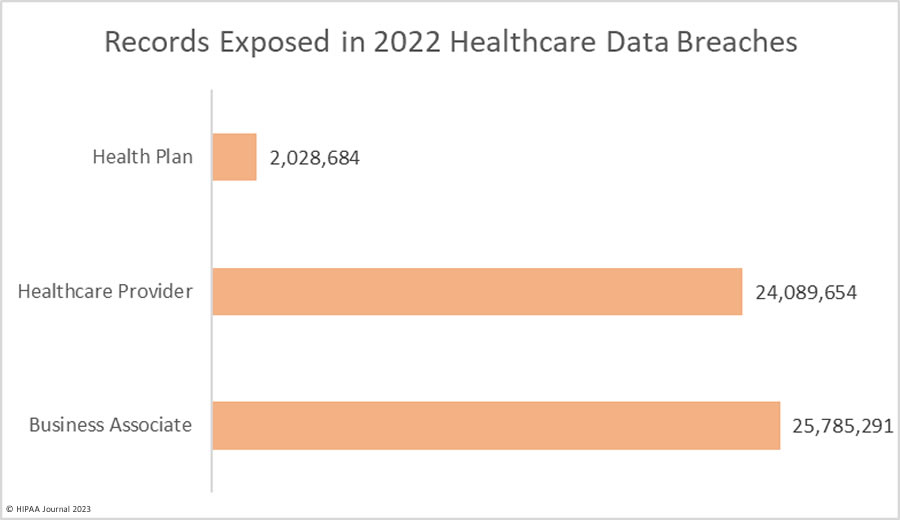
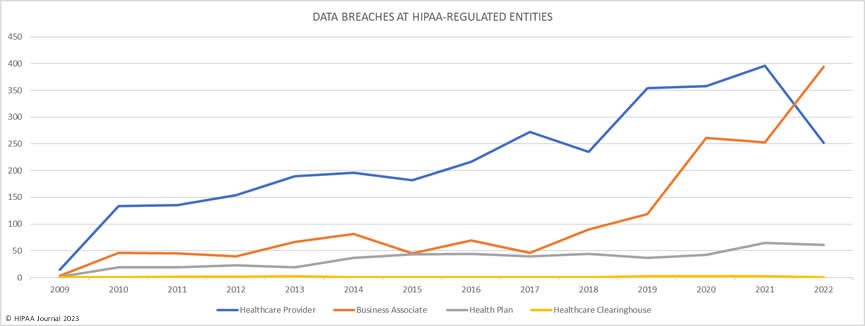
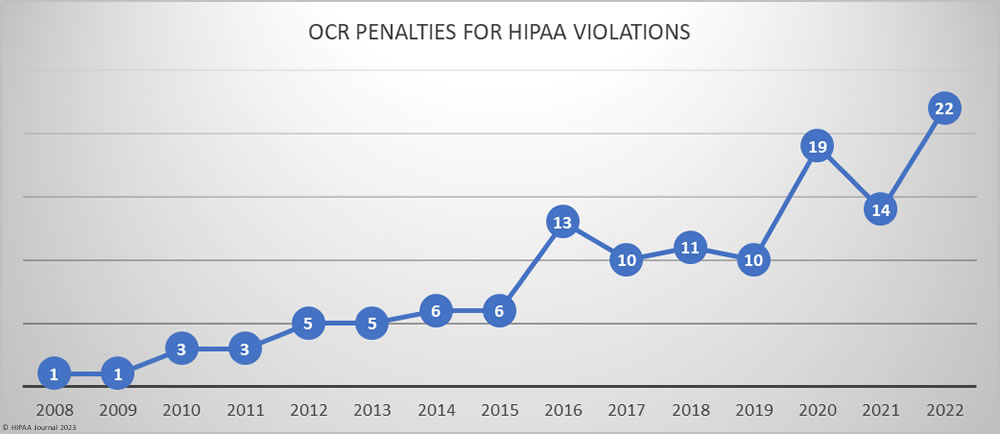
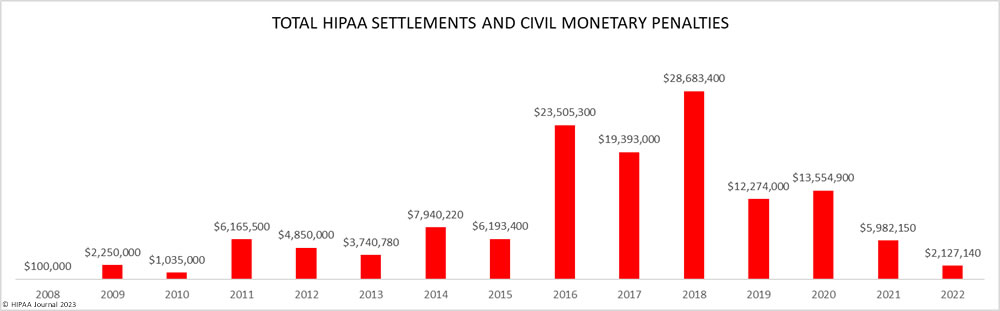
 Over the past few years, there have been increasing calls for HIPAA changes to decrease the administrative burden on HIPAA-covered entities, but the HIPAA 2024 rules and regulations are currently much the same as they were in 2013. OCR responded to feedback from healthcare industry stakeholders by issuing a request for information (RFI) in December 2018 on potential changes to the HIPAA Rules. OCR sought comments from HIPAA-covered entities about possible changes to HIPAA Rules in 2019 and beyond, which are mostly concerned with the easing of certain administrative requirements and the removal of certain provisions of the HIPAA Privacy Rule that have been limiting or discouraging the coordination of care. The comment period closed on February 12, 2019.
Over the past few years, there have been increasing calls for HIPAA changes to decrease the administrative burden on HIPAA-covered entities, but the HIPAA 2024 rules and regulations are currently much the same as they were in 2013. OCR responded to feedback from healthcare industry stakeholders by issuing a request for information (RFI) in December 2018 on potential changes to the HIPAA Rules. OCR sought comments from HIPAA-covered entities about possible changes to HIPAA Rules in 2019 and beyond, which are mostly concerned with the easing of certain administrative requirements and the removal of certain provisions of the HIPAA Privacy Rule that have been limiting or discouraging the coordination of care. The comment period closed on February 12, 2019. The pending HIPAA updates are intended to ease the administration burden on HIPAA-covered entities, although in the short term, the burden will be increased. Updates will need to be made to policies and procedures and changes will be required for notices of privacy practices, although there will not, at least, be the requirement to obtain written acknowledgment that updated NPPs have been received.
The pending HIPAA updates are intended to ease the administration burden on HIPAA-covered entities, although in the short term, the burden will be increased. Updates will need to be made to policies and procedures and changes will be required for notices of privacy practices, although there will not, at least, be the requirement to obtain written acknowledgment that updated NPPs have been received. In response to the 2019 Novel Coronavirus pandemic, the HHS announced major changes to the enforcement of HIPAA compliance in 2020, which will remain in place for the duration of the nationwide COVID-19 public health emergency or until the Secretary of the HHS declares the public health emergency is over. These “unprecedented HIPAA flexibilities” were announced in March and April by means of Notices of Enforcement Discretion and are intended to ease the burden on healthcare organizations and business associates that are having to overcome major challenges testing and treating COVID-19 patients. The changes to HIPAA enforcement have been introduced to ensure that HIPAA compliance does not get in the way of the provision of high-quality patient care.
In response to the 2019 Novel Coronavirus pandemic, the HHS announced major changes to the enforcement of HIPAA compliance in 2020, which will remain in place for the duration of the nationwide COVID-19 public health emergency or until the Secretary of the HHS declares the public health emergency is over. These “unprecedented HIPAA flexibilities” were announced in March and April by means of Notices of Enforcement Discretion and are intended to ease the burden on healthcare organizations and business associates that are having to overcome major challenges testing and treating COVID-19 patients. The changes to HIPAA enforcement have been introduced to ensure that HIPAA compliance does not get in the way of the provision of high-quality patient care.