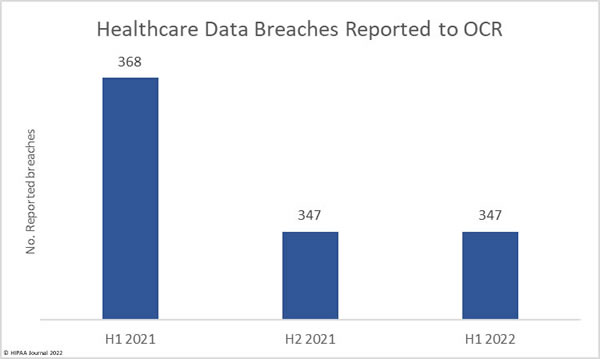
Ransomware attacks are rife, hacking incidents are being reported at high levels, and there have been several very large healthcare data breaches reported so far in 2022; however, our analysis of healthcare data breaches reported in 1H 2022, shows that while data breaches are certainly being reported in high numbers, there has been a fall in the number of reported breaches compared to 1H 2021.
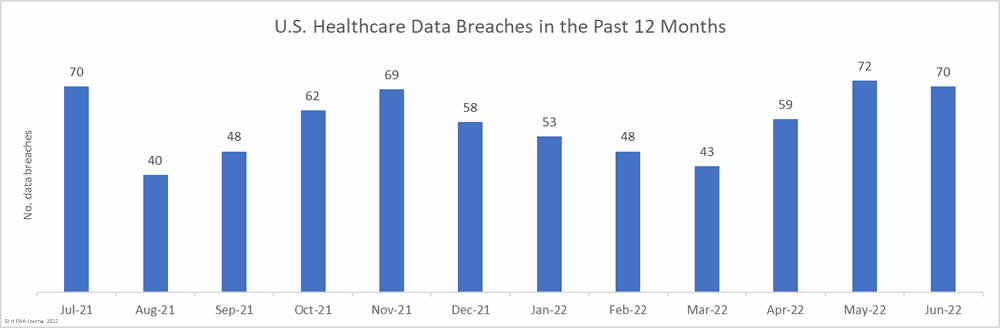
Between January 1, 2022, and June 30, 2022, 347 healthcare data breaches of 500 or more records were reported to the Department of Health and Human Services’ Office for Civil Rights (OCR) – the same number of data breaches reported in 2H, 2021. In 1H, 2021, 368 healthcare data breaches were reported to OCR, 21 fewer breaches than the corresponding period this year. That represents a 5.71% reduction in reported breaches.
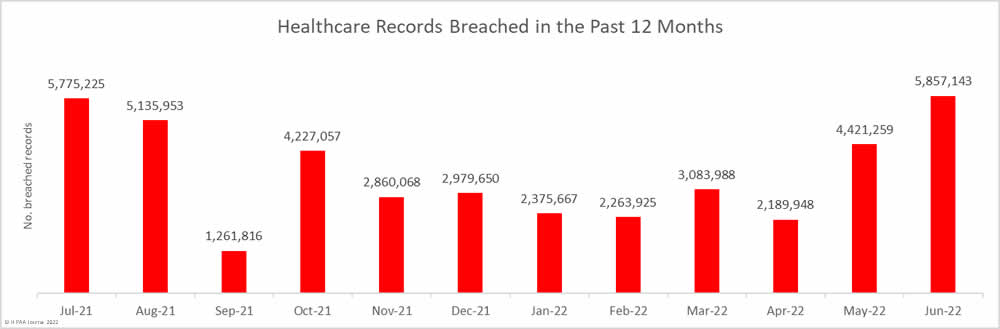
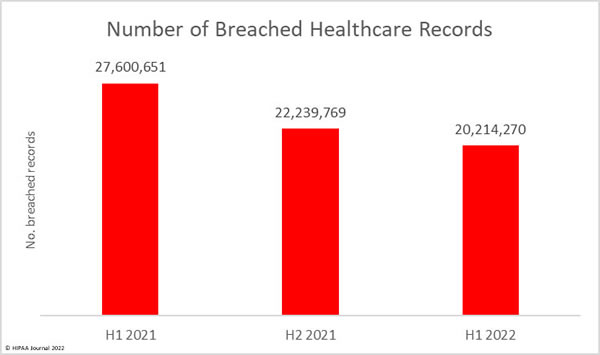
The number of healthcare records breached has continued to fall. In 1H, 2021, 27.6 million healthcare records were breached. In 2H, 2021, the number of breached records fell to 22.2 million, and the fall continued in 1H, 2022, when 20.2 million records were breached. That is a 9.1% fall from 2H, 2021, and a 26.8% reduction from 1H, 2021.
While it is certainly good news that data breaches and the number of breached records are falling, the data should be treated with caution, as there have been some major data breaches reported that are not yet reflected in this breach report – Data breaches at business associates where only a handful of affected entities have reported the data breaches so far.
One notable breach is a ransomware attack on the HIPAA business associate, Professional Finance Company. That one breach alone affected 657 HIPAA-covered entities, and only a few of those entities have reported the breach so far. Another major business associate breach, at Avamere Health Services, affected 96 senior living and healthcare facilities. The end-of-year breach report could tell a different story.
Largest Healthcare Data Breaches in 1H 2022
| 1H 2022 Healthcare Data Breaches of 500 or More Records |
| 500-1,000 Records |
1,001-9,999 Records |
10,000- 99,000 Records |
100,000-249,999 Records |
250,000-499,999 Records |
500,000 – 999,999 Records |
1,000,000+ Records |
| 61 |
132 |
117 |
20 |
7 |
6 |
4 |
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Business Associate Data Breach |
Cause of Data Breach |
| Shields Health Care Group, Inc. |
MA |
Business Associate |
2,000,000 |
Hacking/IT Incident |
Yes |
Unspecified cyberattack |
| North Broward Hospital District (Broward Health) |
FL |
Healthcare Provider |
1,351,431 |
Hacking/IT Incident |
No |
Cyberattack through the office of 3rd party medical provider |
| Texas Tech University Health Sciences Center |
TX |
Healthcare Provider |
1,290,104 |
Hacking/IT Incident |
Yes |
Ransomware attack on EHR provider (Eye Care Leaders) |
| Baptist Medical Center |
TX |
Healthcare Provider |
1,243,031 |
Hacking/IT Incident |
No |
Unspecified cyberattack |
| Partnership HealthPlan of California |
CA |
Health Plan |
854,913 |
Hacking/IT Incident |
No |
Ransomware attack |
| MCG Health, LLC |
WA |
Business Associate |
793,283 |
Hacking/IT Incident |
Yes |
Unspecified hacking and data theft incident |
| Yuma Regional Medical Center |
AZ |
Healthcare Provider |
737,448 |
Hacking/IT Incident |
No |
Ransomware attack |
| Morley Companies, Inc. |
MI |
Business Associate |
521,046 |
Hacking/IT Incident |
Yes |
Unspecified hacking and data theft incident |
| Adaptive Health Integrations |
ND |
Healthcare Provider |
510,574 |
Hacking/IT Incident |
No |
Unspecified hacking incident |
| Christie Business Holdings Company, P.C. |
IL |
Healthcare Provider |
502,869 |
Hacking/IT Incident |
No |
Unauthorized access to email accounts |
| Monongalia Health System, Inc. |
WV |
Healthcare Provider |
492,861 |
Hacking/IT Incident |
No |
Unspecified hacking incident |
| ARcare |
AR |
Healthcare Provider |
345,353 |
Hacking/IT Incident |
No |
Malware infection |
| Super Care, Inc. dba SuperCare Health |
CA |
Healthcare Provider |
318,379 |
Hacking/IT Incident |
No |
Unspecified hacking incident |
| Cytometry Specialists, Inc. (CSI Laboratories) |
GA |
Healthcare Provider |
312,000 |
Hacking/IT Incident |
No |
Ransomware attack |
| South Denver Cardiology Associates, PC |
CO |
Healthcare Provider |
287,652 |
Hacking/IT Incident |
No |
Unspecified hacking incident |
| Stokes Regional Eye Centers |
SC |
Healthcare Provider |
266,170 |
Hacking/IT Incident |
Yes |
Ransomware attack on EHR provider (Eye Care Leaders) |
| Refuah Health Center |
NY |
Healthcare Provider |
260,740 |
Hacking/IT Incident |
No |
Ransomware attack |
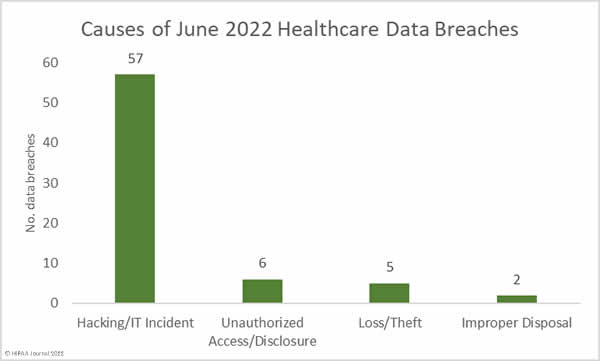
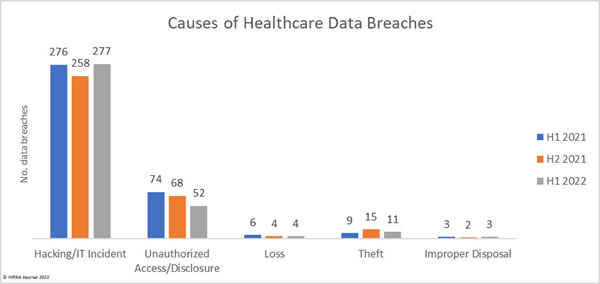
Causes of 1H 2022 Healthcare Data Breaches
Hacking and other IT incidents dominated the breach reports in 1H 2022, accounting for 277 data breaches or 79.83% of all breaches reported in 1H. That represents a 7.36% increase from 2H, 2021, and a 6.44% increase from 1H, 2021. Across the hacking incidents in 1H, 2022, the protected health information of 19,654,129 individuals was exposed or compromised – 97.22% of all records breached in 1H, 2022.
That represents a 6.51% reduction in breached records from 2H, 2021, and a 26.56% reduction in breached records from 1H, 2021, showing that while hacking incidents are being conducted in very high numbers compared to previous years, the severity of those incidents has reduced.
The average hacking/IT incident breach size was 70,954 records in 1H, 2022 and the median breach size was 10,324 records. In 2H, 2022, the average breach size was 81,487 records with a median breach size of 5,989 records, and in 1H, 2021, the average breach size was 96,658 records and the median breach size was 6,635 records.
In 1H, 2022, there were 52 unauthorized access/disclosure breaches reported – 14.99% of all breaches in 1H, 2022. These incidents resulted in the impermissible disclosure of 278,034 healthcare records, 72.33% fewer records than in 2H, 2021, and 61.37% fewer records than in 1H, 2021. In 1H, 2022, the average breach size was 5,347 records and the median breach size was 1,421 records. In 1H, 2021, the average breach size was 14,778 records and the median was 1,946 records. In 1H, 2021, the average breach size was 9,725 records, and the median breach size was 1,848 records.
The number of loss, theft, and improper disposal incidents has remained fairly constant over the past 18 months, although the number of records exposed in these incidents increased in 1H, 2022 to 279,266 records, up 217.33% from 2H, 2021, and 422.53% from 1H, 2021.
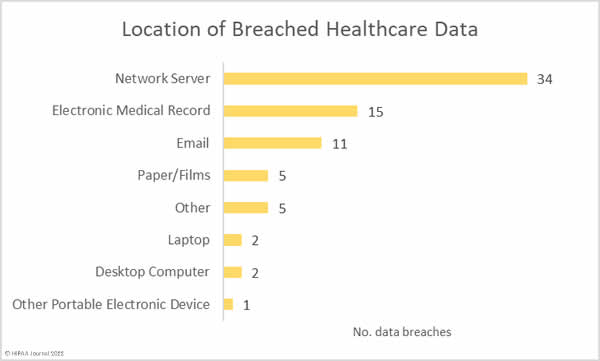
Location of Breached Protected Health Information
Protected health information is stored in many different locations. Medical records are housed in electronic medical record systems, but a great deal of PHI is included in documents, spreadsheets, billing systems, email accounts, and many other locations. The chart below shows the locations where PHI was stored. In several security breaches, PHI was breached in several locations.
The data shows that by far the most common location of breached data is network servers, which is unsurprising given the high number of hacking incidents and ransomware attacks. Most data breaches do not involve electronic medical record systems; however, there have been breaches at electronic medical record providers this year, hence the increase in data breaches involving EHRs. The chart below also shows the extent to which email accounts are compromised. These incidents include phishing attacks and brute force attacks to guess weak passwords. HIPAA-regulated entities can reduce the risk of email data breaches by implementing multifactor authentication and having robust password policies and enforcing those policies. A password manager is recommended to make it easier for healthcare employees to set unique, complex passwords. It is also important not to neglect security awareness training for the workforce – a requirement for compliance with the HIPAA Security Rule.
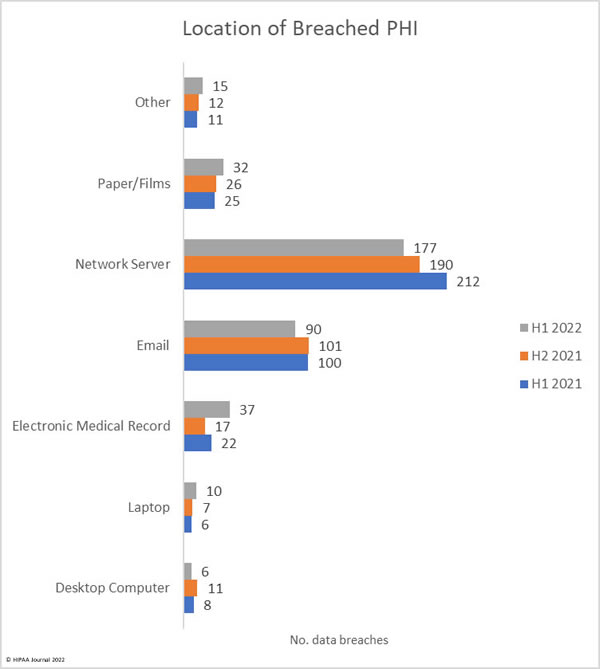
Where are the Data Breaches Occurring?
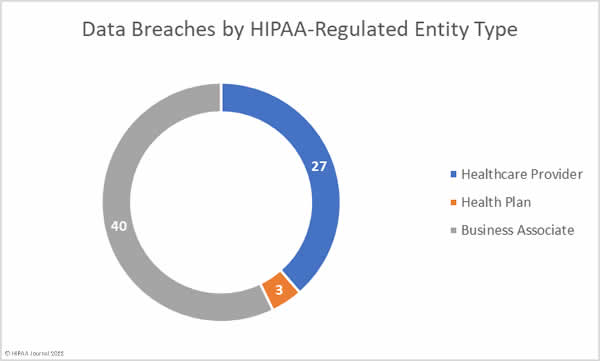
Healthcare providers are consistently the worst affected type of HIPAA-covered entity; however, the number of data breaches occurring at business associates has increased. Data breaches at business associates often affect multiple HIPAA-covered entities. These data breaches are shown on the OCR breach portal; however, they are not clearly reflected as, oftentimes, a breach at a business associate is self-reported by each HIPAA-covered entity. Simply tallying up the reported breaches by the reporting entity does not reflect the extent to which business associate data breaches are occurring.
This has always been reflected in the HIPAA Journal data breach reports, and since June 2021, the reporting of data breaches by covered entity type was adjusted further to make business associate data breaches clearer by showing graphs of where the breach occurred, rather than the entity reporting the data breach. The HIPAA Journal data analysis shows the rising number of healthcare data breaches at business associates.
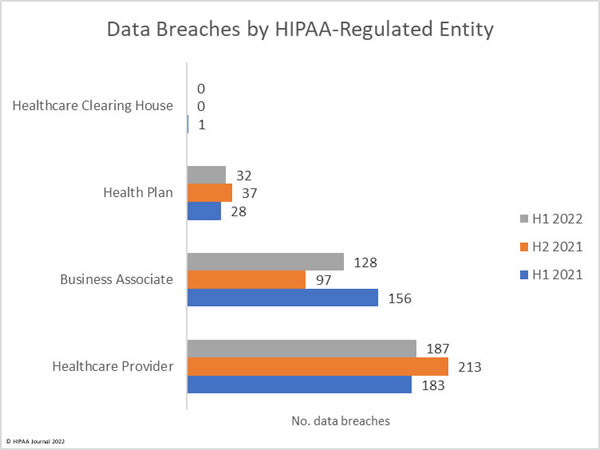
1H 2022 Data Breaches by State
As a general rule of thumb, U.S. states with the highest populations tend to be the worst affected by data breaches, so California, Texas, Florida, New York, and Pennsylvania tend to experience more breaches than sparsely populated states such as Alaska, Vermont, and Wyoming; however, data breaches are being reported all across the United States.
The data from 1H 2022, shows data breaches occurred in 43 states, D.C. and Puerto Rico, with healthcare data safest in Alaska, Iowa, Louisiana, Maine, New Mexico, South Dakota, & Wyoming, where no data breaches were reported in the first half of the year.
| State |
Number of Breaches |
| New York |
29 |
| California |
23 |
| New Jersey & Texas |
18 |
| Florida & Ohio |
17 |
| Michigan & Pennsylvania |
15 |
| Georgia |
14 |
| Virginia |
13 |
| Illinois & Washington |
12 |
| Massachusetts & North Carolina |
10 |
| Colorado, Missouri, & Tennessee |
9 |
| Alabama, Arizona, & Kansas |
8 |
| Maryland |
7 |
| Connecticut & South Carolina |
6 |
| Oklahoma, Utah, & West Virginia |
5 |
| Indiana, Minnesota, Nebraska, & New Hampshire |
4 |
| Wisconsin |
3 |
| Arkansas, Delaware, Mississippi, Montana, Nevada, & the District of Columbia |
2 |
| Hawaii, Idaho, Kentucky, North Dakota, Oregon, Rhode Island, Vermont, and Puerto Rico |
1 |
HIPAA Enforcement Activity in 1H 2022
HIPAA Journal tracks HIPAA enforcement activity by OCR and state attorneys general in the monthly and annual healthcare data breach reports. In 2016, OCR started taking a harder line on HIPAA-regulated entities that were discovered to have violated the HIPAA Rules and increased the number of financial penalties imposed, with peak enforcement occurring in 2019 when 19 financial penalties were imposed.
2022 has started slowly in terms of HIPAA enforcement actions, with just 4 financial penalties imposed by OCR in 1H, 2022. However, that should not be seen as OCR going easy on HIPAA violators. In July 2022, OCR announced 12 financial penalties to resolve HIPAA violations, bringing the annual total up to 16. HIPAA Journal records show only one enforcement action taken by state attorneys general so far in 2022.
Limitations of this Report
The nature of breach reporting makes generating accurate data breach reports challenging. HIPAA-regulated entities are required to report data breaches to OCR within 60 days of a data breach occurring; however, the number of individuals affected may not be known at that point. As such, data breaches are often reported with an interim figure, which may be adjusted up or down when the investigation is completed. Many HIPAA-regulated entities report data breaches using a placeholder of 500 records, and then submit an amendment, so the final totals may not be reflected in this report. Data for this report was compiled on August 10, 2022.
While data breaches should be reported within 60 days of discovery, there has been a trend in recent years for data breaches to be reported within 60 days of the date when the investigation has confirmed how many individuals have been affected, even though the HIPAA Breach Notification Rule states that the date of discovery is the date the breach is discovered, not the date when investigations have been completed. Data breaches may have occurred and been discovered several months ago, but have not yet been reported. These will naturally not be reflected in this report.
This report is based on data breaches at HIPAA-regulated entities – healthcare providers, health plans, healthcare clearinghouses, and business associates of those entities. If an entity is not subject to HIPAA, they are not included in this report, even if they operate in the healthcare industry.
The post 1H 2022 Healthcare Data Breach Report appeared first on HIPAA Journal.