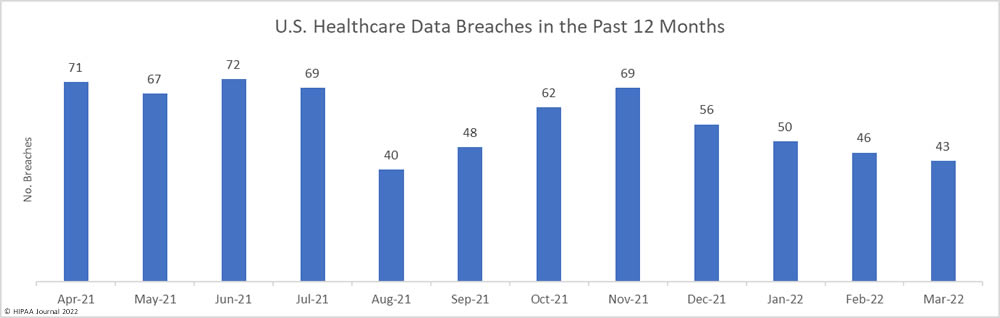
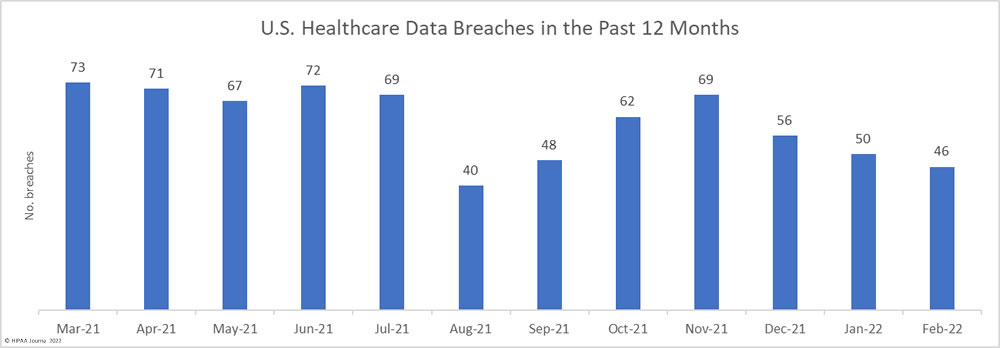
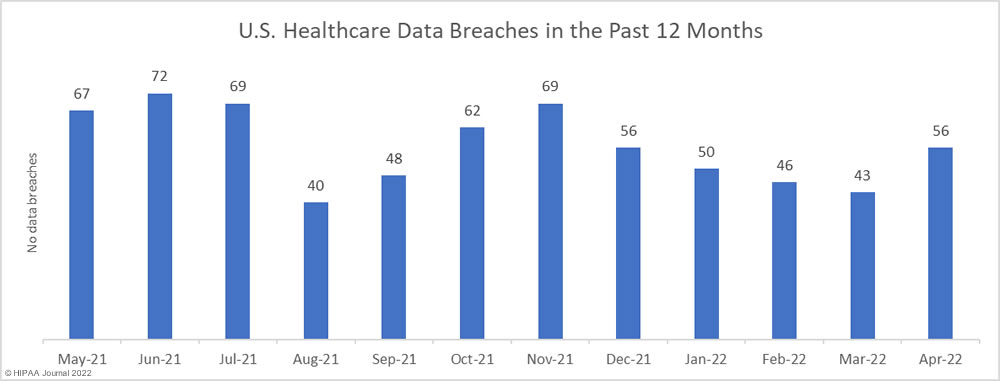
After four successive months of declining numbers of data breaches, there was a 30.2% increase in reported data breaches. In April 2022, 56 data breaches of 500 or more records were reported to the Department of Health and Human Services’ Office for Civil Rights (OCR).
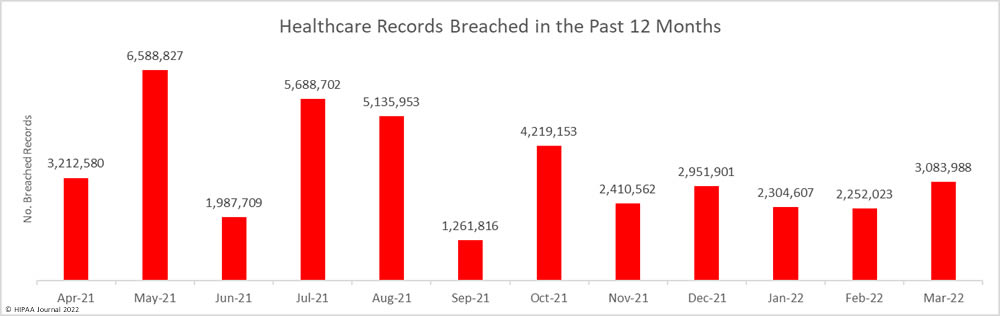
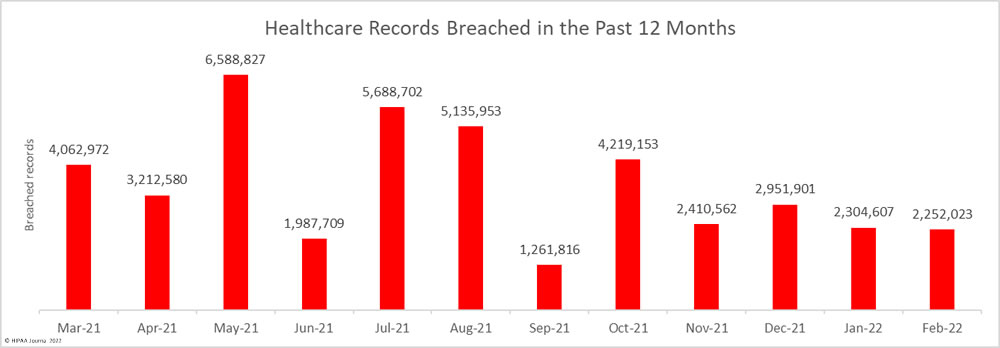
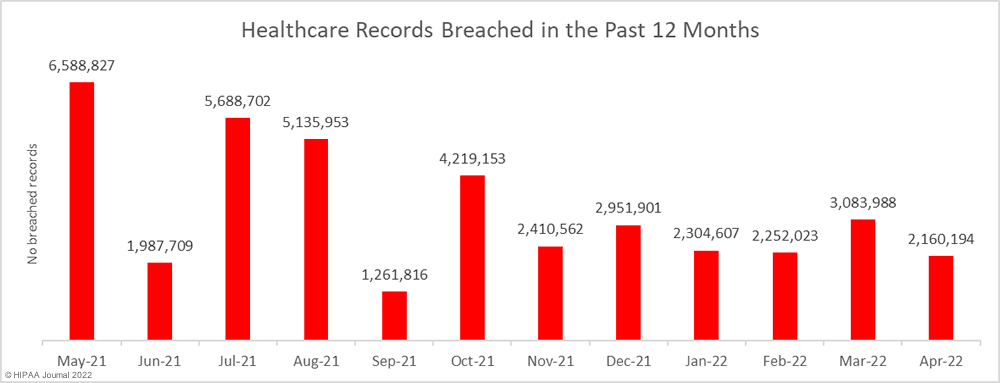
While the number of reported breaches increased month-over-month, the number of healthcare records that were exposed or impermissibly disclosed decreased by 30% to 2,160,194 – the lowest monthly number since October 2021. The average breach size in April 2022 was 38,575 records, and the median breach size was 6,546 records.
Largest Healthcare Data Breaches in April 2022
22 healthcare data breaches were reported in April 2022 that affected 10,000 or more individuals. The worst breach was a hacking incident reported by Adaptive Health Integrations, a provider of software and billing/revenue services to laboratories, physician offices, and other healthcare companies. More than half a million healthcare individuals were affected. The Arkansas healthcare provider ARcare suffered a malware attack that disrupted its systems and potentially allowed hackers to access the records of 345,353 individuals. Refuah Health Center reported a hacking and data theft incident in April, which had occurred almost a year previously in May 2021 and affected up to 260,740 patients.
Illinois Gastroenterology Group, PLLC reported a hacking incident where the attackers had access to the records of 227,943 individuals, and Regional Eye Associates, Inc. & Surgical Eye Center of Morgantown were affected by a data breach at the cloud-EHR vendor Eye Care Leaders (ECL), which exposed the records of 194,035 individuals. The ECL cyberattack saw the attackers delete databases and system configuration files of one of its cloud services. The cyberattack affected close to a dozen eye care providers and resulted in the exposure of more than 342,000 records.
| Name of Covered Entity | State | Covered Entity Type | Individuals Affected | Cause of Breach |
| Adaptive Health Integrations | ND | Healthcare Provider | 510,574 | Hacking incident with potential data theft |
| ARcare | AR | Healthcare Provider | 345,353 | Malware infection |
| Refuah Health Center | NY | Healthcare Provider | 260,740 | Hacking incident and data theft incident |
| Illinois Gastroenterology Group, PLLC | IL | Healthcare Provider | 227,943 | Hacking incident with potential data theft |
| Regional Eye Associates, Inc. & Surgical Eye Center of Morgantown | WV | Healthcare Provider | 194,035 | Hacking incident at EHR provider |
| Healthplex, Inc. | NY | Health Plan | 89,955 | Email account breach |
| Optima Dermatology Holdings, LLC | NH | Healthcare Provider | 59,872 | Unspecified email incident |
| SUMMIT EYE ASSOCIATES P.C. | TN | Healthcare Provider | 53,818 | Hacking incident at EHR provider |
| Newman Regional Health | KS | Healthcare Provider | 52,224 | Email account breach |
| WellStar Health System, Inc. | GA | Healthcare Provider | 30,417 | WellStar Health System |
| Central Vermont Eye Care | VT | Healthcare Provider | 30,000 | Unspecified hacking incident |
| Frank Eye Center, P.A. | KS | Healthcare Provider | 26,333 | Hacking incident at EHR provider |
| New Creation Counseling Center | OH | Healthcare Provider | 24,029 | Ransomware attack |
| Georgia Pines CSB | GA | Healthcare Provider | 24,000 | Theft of laptop computers |
| The Guidance Center, Inc. | AZ | Healthcare Provider | 23,104 | Email account breach |
| Allied Eye Physicians and Surgeons, Inc. | OH | Healthcare Provider | 20,651 | Hacking incident at EHR provider |
| King County Public Hospital District No. 2 d/b/a EvergreenHealth | WA | Healthcare Provider | 20,533 | Hacking incident at EHR provider |
| Onehome Health Solutions | FL | Healthcare Provider | 15,401 | Theft of laptop computers |
| Southern Ohio Medical Center | OH | Healthcare Provider | 15,136 | Hacking incident with potential data theft |
| Arkfeld, Parson, and Goldstein, P.C. doing business as ilumin | NE | Healthcare Provider | 14,984 | Hacking incident at EHR provider |
| Pediatric Associates, P.C. | VA | Healthcare Provider | 13,000 | Hacking incident at EHR provider |
| Fairfield County Implants and Periodontics, LLC | CT | Healthcare Provider | 10,502 | Email account breach |
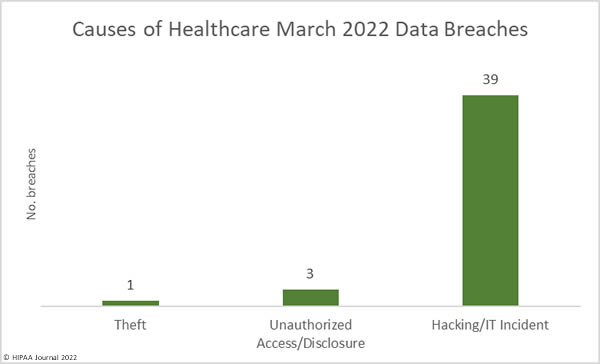
Causes of April 2022 Healthcare Data Breaches
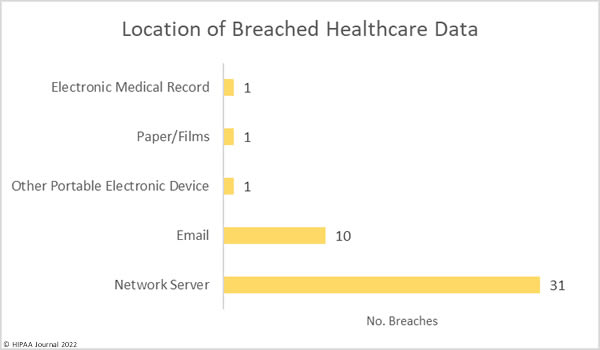
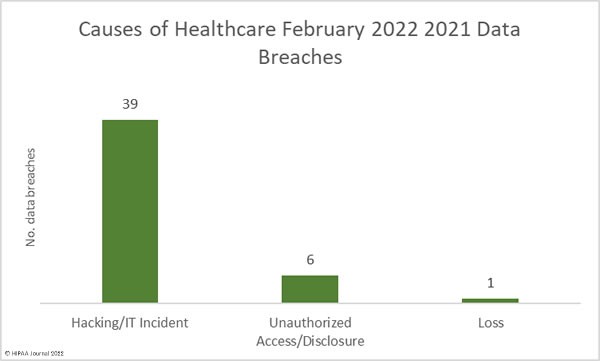
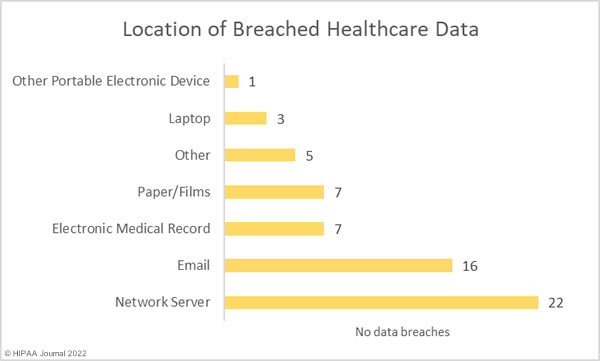
Hacking and IT incidents accounted for 73.2% of the healthcare data breaches reported in April 2022 and 97.1% of the month’s breached healthcare records. 2,098,390 individuals were affected by those hacking incidents and may have had their protected health information stolen. The average breach size was 51,180 records and the median breach size was 9,969 records. 16 of the hacking incidents involved unauthorized individuals gaining access to employee email accounts, and there were 7 breaches of electronic health records, due to the hacking incident at the EHR vendor Eye Care Leaders.

There were just breaches reported as unauthorized access/disclosure incidents which involved a total of 20,391 records. The average breach size was 1,854 records and the median breach size was 820 records. There were two theft incidents reported involving laptop computers and one loss incident involving an ‘other portable electronic device’. Across the three loss/theft incidents, the records of 40,298 individuals were potentially compromised. All three breaches could have been prevented if data had been encrypted. There was also one improper disposal incident reported, involving 1,115 paper records.
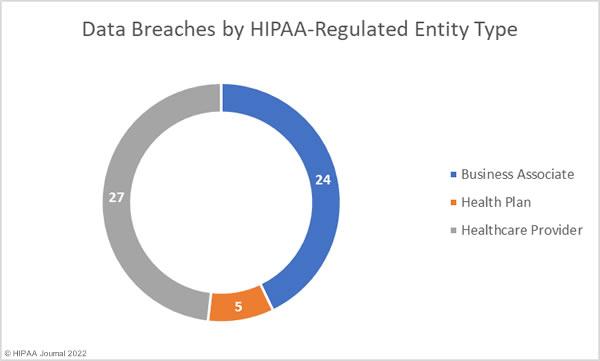
Healthcare Data Breaches by Covered Entity Type
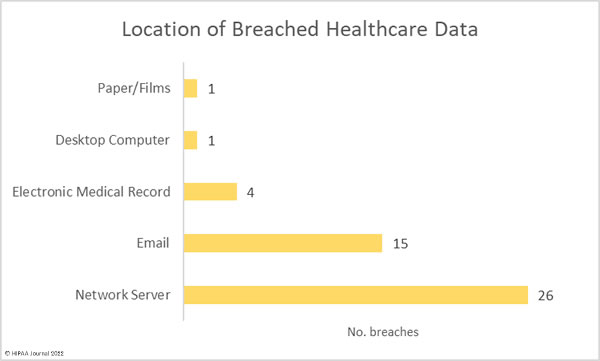
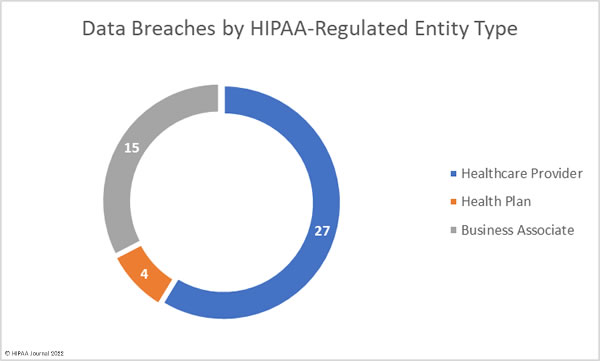
Healthcare providers were the worst affected HIPAA-covered entity, with 39 reporting breaches in April. 7 data breaches were reported by health plans, and 10 data breaches were reported by business associates. However, a further 17 data breaches occurred at business associates but were reported by the respective covered entity. The chart below shows the month’s data breaches adjusted to reflect where the breaches occurred.
Healthcare Data Breaches by State
In April 2022, HIPAA-regulated entities in 26 states reported breaches. New York and Ohio were the worst affected states in April, with 7 & 6 data breaches reported respectively.
| State | Number of Data Breaches |
| New York | 7 |
| Ohio | 6 |
| California | 4 |
| Arizona, Georgia, Kansas, Michigan, Tennessee, & Virginia | 3 |
| Florida, Maryland, North Carolina & New Hampshire | 2 |
| Alabama, Arkansas, Colorado, Connecticut, Illinois, Nebraska, North Dakota, Pennsylvania, South Carolina, Utah, Vermont, Washington & West Virginia | 1 |
HIPAA Enforcement Activity in April 2022
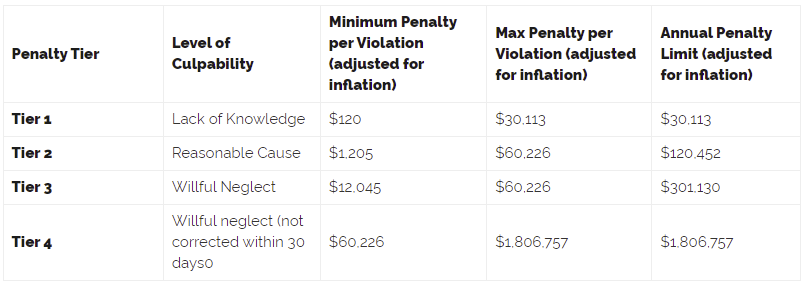
There were no HIPAA enforcement activities announced by the HHS’ Office for Civil Rights or State Attorneys General in April 2022. So far this year, 4 financial penalties have been imposed to resolve HIPAA violations.
The post April 2022 Healthcare Data Breach Report appeared first on HIPAA Journal.