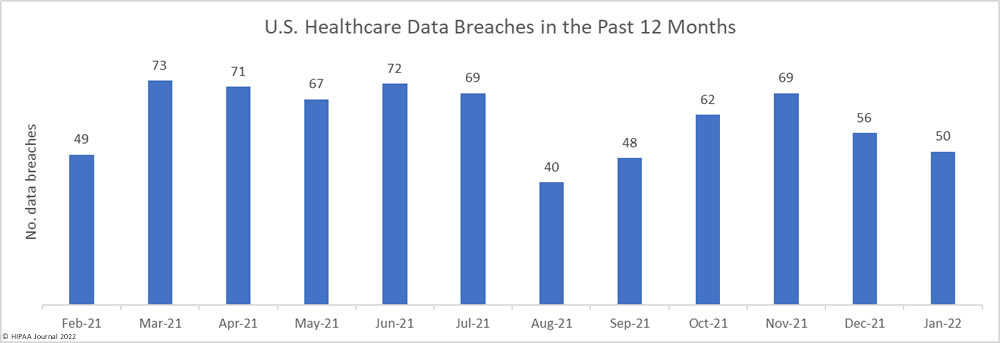
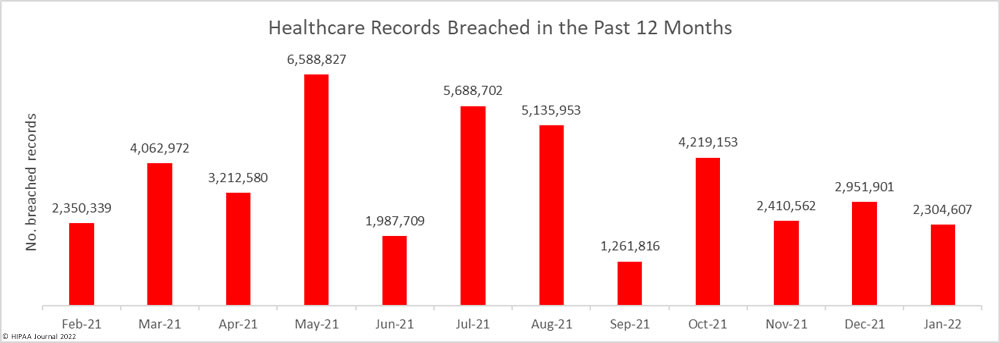
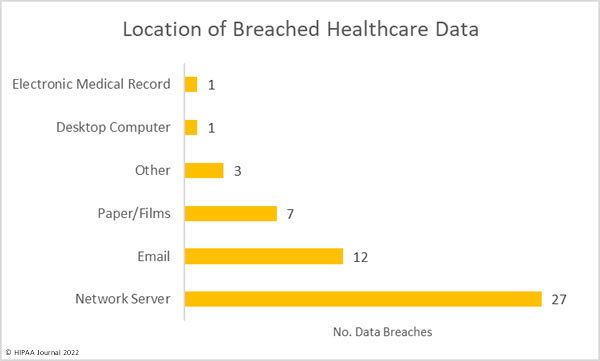
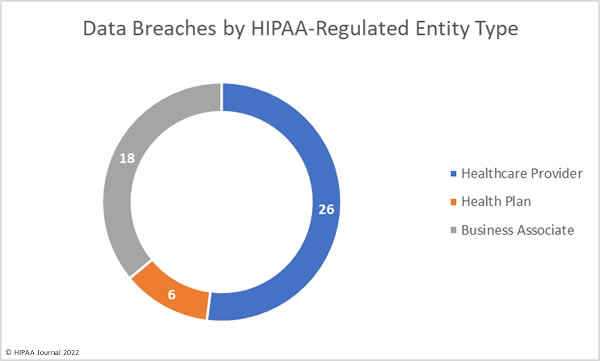
Many sources explaining why HIPAA compliance is important for healthcare professionals tend to focus on the purpose of HIPAA regulations rather than the benefits of compliance for healthcare professionals. The same sources also tend to focus on how noncompliance affects patients and employers, rather than the impact it can have on healthcare professionals´ lives.
This article discusses why HIPAA compliance is important for healthcare professionals from a healthcare professional´s perspective. It explains why healthcare professionals cannot avoid HIPAA; and that, by complying with HIPAA, healthcare professionals can foster patient trust, keep patients safer, and contribute towards better patient outcomes. This is turn raises morale, creates a more rewarding work experience, and enables healthcare professionals to get more from their vocation.
Conversely, the failure to comply with HIPAA can have significant professional and personal consequences. Yet the failure to comply with HIPAA is not always a healthcare professional´s fault. Sometimes it can be due to insufficient training or cultural norms. We look at why Covered Entities might not always be able to provide sufficient training or monitor HIPAA compliance, why they may not accept responsibility when an avoidable HIPAA violation occurs, and how you can avoid HIPAA violations due to a lack of knowledge.
Click here for free HIPAA training
Click here to view HIPAA training pricing
Why Healthcare Professionals Cannot Avoid HIPAA
One of the objectives of HIPAA is to provide a federal floor of privacy protections for individuals´ identifiable health information held by Covered Entities. To achieve this objective, the Privacy and Security Rules imposes standards Covered Entities must comply with in order to protect the privacy of “Protected Health Information” (PHI). The failure to comply with the HIPAA standards can result in substantial financial penalties – even when no data breach occurs and PHI is not compromised.
Most healthcare organizations are Covered Entities and, as such, are required to implement policies and procedures to comply with the Privacy and Security Rule standards. As employees of Covered Entities, healthcare professionals are required to comply with their employer´s policies and procedures. This is why healthcare professionals cannot avoid HIPAA. However, this is not the only reason why HIPAA compliance is important for healthcare professionals.
The Benefits of HIPAA Compliance for Healthcare Professionals
There is little doubt the most important element of a patient/healthcare professional relationship is trust. Patients trust their healthcare professionals with intimate details of their lives because they trust healthcare professionals work in their best interests to achieve optimal health outcomes. However, trust can be a fragile commodity. If their intimate details are exposed due to a HIPAA violation, patients may withhold information crucial to the delivery of care despite the potential long-lasting consequences for their health.
Healthcare professionals can mitigate the risk of trust being broken by complying with the policies and procedures implemented by their employer to prevent HIPAA violations. When patients are confident their privacy is being respected, this fosters trust – which contributes to the delivery of better care in order to achieve optimal health outcomes. Better patient outcomes raise the morale of healthcare professionals and result in a more rewarding work experience.
The Professional and Personal Consequences of Noncompliance
One of the policies a Covered Entity is required to implement is a sanctions policy for when members of its workforce do not comply with HIPAA policies and procedures. Covered Entities are required to enforce the sanctions policy and act on HIPAA violations by healthcare professionals because, if they don´t enforce the sanctions policy, the Covered Entity will be in violation of HIPAA. Furthermore, if the Covered Entity fails to act, noncompliance can deteriorate into a cultural norm.
Being sanctioned for a HIPAA violation can have professional and personal consequences for healthcare professionals. Penalties can range from verbal warnings to the loss of professional accreditation – which will make it difficult for a healthcare professional to get another job – and, if a criminal conviction results from the noncompliance, it will likely be reported in the media which will have repercussions for a healthcare professional´s personal reputation.
Who is Responsible for HIPAA Violations?
As mentioned previously, the failure to comply with HIPAA is not always the healthcare professional´s fault. Although Covered Entities are required to provide training on policies and procedures that relate to healthcare professionals´ functions, they may not have the resources to provide training on every conceivable scenario a healthcare professional may encounter, or to monitor compliance 24/7 in order to prevent the development of cultural norms.
Consequently, unintentional violations of HIPAA can occur due to a lack of knowledge. However, Covered Entities are not always willing to accept responsibility for unintentional violations due to a lack of knowledge because it implies they failed to conduct a thorough risk assessment, overlooked a threat to the privacy of PHI, and failed to provide “necessary and appropriate” training – or, when a cultural norm has developed, failed to monitor compliance with policies and procedures.
How You Can Avoid Unintentional Violations of HIPAA
The best way to avoid unintentional HIPAA violations and the professional and personal consequences of noncompliance – even when they are not your fault – is to ensure your knowledge of HIPAA covers every area of your role and the scenarios you may encounter. To achieve this level of knowledge, you should take advantage of third-party HIPAA training courses that provide you with an in-depth knowledge of HIPAA and its rules and regulations.
Taking responsibility for your own knowledge of HIPAA – and using that knowledge to work in a HIPAA-compliant manner – protects your career, improves your job prospects, and enables you to get more from your vocation. Given the choice, most healthcare professionals would prefer to work in an environment which operates compliantly to delivery better patient outcomes, in which morale is high, and in which the healthcare professional enjoys a more rewarding work experience.
Click here to view HIPAA training pricing
The post Video: Why HIPAA Compliance is Important for Healthcare Professionals appeared first on HIPAA Journal.