The Health Insurance Portability and Accountability Act is now 25 years old. How effective has this healthcare law been and what is the future of HIPAA?
It is now exactly 25 years to the day since the Health Insurance Portability and Accountability Act (HIPAA) was signed into law by President Clinton. On August 21, 1996, when President Clinton added his signature to the legislation, few people would have realized how HIPAA would evolve and grow into the comprehensive national health privacy law that it is today.
It is difficult to argue that HIPAA has not been an overall success, but the legislation has attracted a fair amount of criticism over the years, especially initially due to the considerable administrative burden it placed on healthcare organizations. On balance, the improvements to healthcare that have come from compliance with HIPAA more than outweigh the negatives.
The biggest successes are the improvements to patient privacy and data security, the rights given to patients with respect to their healthcare data, greater efficiency in the healthcare system, and changes that have helped to reduce waste and healthcare fraud. The improvements have generally been made for relatively little cost.
HIPAA certainly has its strengths, but there are also limitations that have become increasingly apparent in recent years and even now, 25 years after the legislation was first introduced, there is still confusion about what compliance entails.
In this article we will explore the strengths and limitations of HIPAA, assess how effective HIPAA has been, and will explore the future of HIPAA and what can be expected in terms of updates to the legislation. First, however, it is useful to provide a brief recap of the history of HIPAA and how the legislation has evolved over the years.
A Brief History of HIPAA
HIPAA was initially introduced to improve the portability of health insurance coverage for employees between jobs, to combat waste, fraud and abuse in health insurance and healthcare delivery, to promote the use of medical savings accounts by introducing tax breaks, and to simplify the administration of health insurance. The legislation was later augmented with new Rules covering the privacy and security of healthcare data.
Initially, HIPAA only applied to a limited number of entities in the healthcare industry – healthcare providers, health plans, and healthcare clearinghouses, and only those that transmit healthcare data in electronic form for certain transactions for which the HHS maintains standards. The Health Information Technology for Economic and Clinical Health (HITECH) Act expanded the scope of HIPAA to cover business associates of HIPAA covered entities – third-party firms that require access to protected health information (PHI) to provide services or products to covered entities.
Important updates to HIPAA are detailed below:
- HIPAA Signed into Law by President Bill Clinton – August 1996
- Effective Date of the HIPAA Privacy Rule – April 2003
- Effective Date of the HIPAA Security Rule – April 2005
- Effective Date of the HIPAA Enforcement Rule – March 2006
- Effective date of HITECH and the Breach Notification Rule – September 2009
- Effective Date of the Final Omnibus Rule – March 2013
HIPAA’s Strengths and Weaknesses
There are many positives that have come from HIPAA, the best known of which are improving privacy protections for patients and improving the security of healthcare data. HIPAA limits the uses and disclosures of patient data to those related to treatment, payment, or healthcare operations and all covered entities and business associates must implement appropriate administrative, physical, and technical safeguards to ensure patient data are appropriately protected from internal and external threats.
Importantly, HIPAA gave individuals new rights with respect to their healthcare data. Prior to the introduction of the HIPAA Privacy Rule, patients were not even permitted to see their medical files. HIPAA gave individuals the right to obtain and inspect a copy of their healthcare data and request errors be corrected. HIPAA made sure patients are informed about how their healthcare data will be used and disclosed, gave patients the right to further limit disclosures of their health data, and also allowed them to view an “accounting of disclosures” to see who has been provided with their healthcare data.
HIPAA has improved the portability of health insurance for employees between jobs and has helped to prevent discrimination against people with pre-existing conditions when receiving health insurance coverage. Efficiency in healthcare has been improved by standardizing transactions through the use of standard code sets and has helped to significantly reduce waste and fraud in healthcare.
However, it has not all been plain sailing. One of the initial requirements of HIPAA was to create a national patient identifier system, but 25 years on and that requirement has still failed to be implemented. Without a national patient identifier system, it can be difficult identifying patients which can result in medical record mismatching. One ONC study in 2014 suggested between 50% and 60% of records are mismatched when shared between different healthcare providers.
Another weakness of HIPAA is its coverage of healthcare data, which is limited to healthcare data collected, held, processed, stored, or transmitted by HIPAA-covered entities and business associates. If a non-HIPAA-covered entity or non-business associate collects the exact same data, HIPAA protections do not apply.
The HIPAA Rules are not clear in places due to the flexibility built into the legislation, so there is potential for misinterpretation of the requirements and there is still confusion among some HIPAA covered entities and business associates when it comes to compliance.
One criticism often made by patients is the lack of a private cause of action. It is not possible to sue for a HIPAA violation, even if the HIPAA Rules have clearly been violated and harm has been suffered. Legal action can only be taken under state laws.
Has HIPAA Been Effective?
In the early years following the introduction of the HIPAA Privacy and Security Rules, questions were asked about how effective the legislation has been. HIPAA certainly looked good on paper but was less effective in practice and noncompliance was widespread. Even the introduction of the HIPAA Enforcement Rule in 2006, which gave the HHS’ Office for Civil Rights the authority to impose financial penalties and sanctions for noncompliance, failed to have a major effect at spurring covered entities into compliance. Enforcement was also very slow at first. It took until 2008 for the first enforcement action to result in a financial penalty, then there was only one financial penalty in 2009 and just two in 2010.
The first phase of HIPAA compliance audits conducted in 2011/2012 highlighted just how many covered entities had ineffective HIPAA compliance programs. The audits uncovered many violations of both the HIPAA Privacy and Security Rules. Even those violations, some of which were serious, did not result in any financial penalties. Some of the fiercest criticism of HIPAA in the early years was it was all bark and no bite.
The introduction of the HITECH Act was a major turning point in the history of HIPAA. Prior to the HITECH Act, business associates were not covered to a large extent by HIPAA, even though they were frequently provided with PHI. The HITECH Act made the HIPAA Rules directly applicable to business associates, which could then be fined directly if they did not also comply with the HIPAA Rules. Business associates include a huge range of third-party companies such as accountants, attorneys, billing companies, collection agencies, consultants, data analysts, and IT firms, so the HITECH Act, and subsequent Omnibus Rule, addressed that major gap.
The introduction of the HITECH Act also saw the penalties for noncompliance significantly increased and OCR also increased its HIPAA enforcement activities. With major fines issued for HIPAA violations, HIPAA compliance became a major focus for HIPAA-covered entities and business associates.
Enforcement of compliance has been critical to the success of HIPAA and while there are still many cases each year of noncompliance, on the whole the requirements of HIPAA have been largely implemented and the benefits of HIPAA are being realized.
Issues with Patient Access to PHI
Since the 2000 HIPAA Privacy Rule was introduced, patients have been given the right to obtain a copy of their own healthcare data, or to have that data sent to their nominated representative. The HITECH Act updated that right and helped individuals obtain a copy of their health data in electronic form, due to the increasing use of electronic health record systems.
While healthcare organizations have implemented policies that allow patients to exercise their access rights, many patients have experienced problems obtaining a copy of their healthcare data. They have either been refused access, requests have been delayed, and patients have been charged excessive fees for exercising their access rights – HIPAA only permits covered entities to charge a reasonable, cost-based fee for providing records.
One of the requirements of the 21st Century Cures Act, introduced in 2016, was to call on the Government Accountability Office to report on the barriers to patient medical record access and following assessments the HHS’ Office for Civil Rights launched a new HIPAA enforcement initiative targeting violations of the HIPAA Right of Access of the HIPAA Privacy Rule in the fall of 2019. That enforcement initiative is still active and, up until the end of July 2021, OCR has imposed 19 financial penalties on healthcare providers found to have been in violation of the HIPAA Right of Access.
Prior to the OCR enforcement initiative, only one financial penalty had been imposed for violations of this important right and that was the $4,300,000 financial penalty imposed on Cignet Health of Prince George’s County in 2011 for denying 741 patients access to their medical records.
HIPAA has Improved Healthcare Data Security
Prior to the introduction of the HIPAA Security Rule, healthcare organizations only had to comply with state laws covering data security. The Security Rule set new minimum standards for data security to ensure the confidentiality, integrity, and availability of electronic PHI. The Security Rule requires risk analyses to be conducted and risks reduced to a reasonable and acceptable level. Access controls are required to prevent unauthorized access to healthcare data, logs must be maintained and checked to identify unauthorized access, backups of data must be made, measures must be implemented to protect against reasonably anticipated, impermissible uses or disclosures, and staff must be provided with security awareness training.
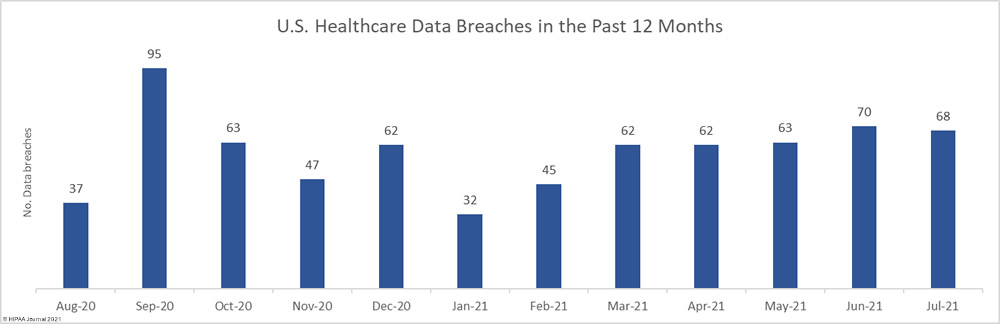
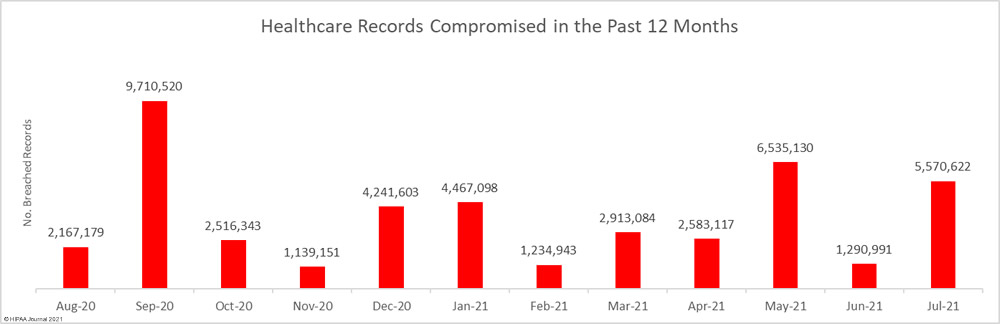
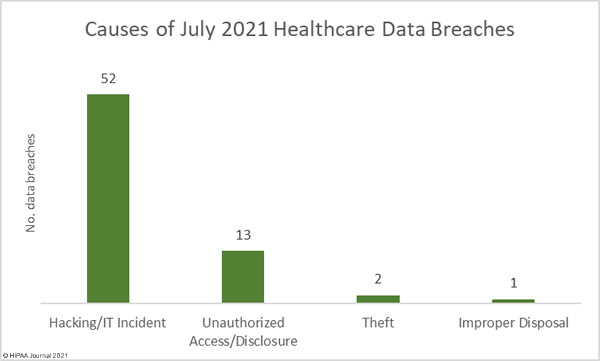
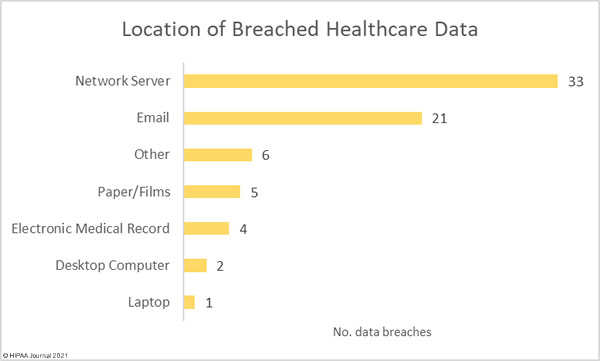
Data security has improved, but data breaches are now occurring at records levels. For the past 5 months, data breaches have been reported by healthcare organizations and business associates at a rate of over 2 per day, but without the Security Rule requirements, far more breaches would be likely to occur.
The HIPAA Security Rule does have weaknesses. To remain relevant the HIPAA Security Rule had to be technology agnostic, so specific measures for security are generally not stipulated. It is left to the discretion of each entity to determine what constitutes “reasonable” protections. If the Security Rule was more specific with regard to required security protections, many more data breaches could be prevented.
The Security Rule also only applies to HIPAA covered entities and business associates, not to any other entity. It therefore has limited reach, and does not cover health data collected by health apps, or the huge volumes of data collected and sold by data brokers. There is therefore considerable scope for improvement to better protect all health data.
The HIPAA Security Rule also calls for security awareness training for staff but does not stipulate how frequently it should be provided. With the threat landscape constantly changing, regular training must be provided to the workforce to ensure employees are kept aware of the latest threats and are taught how to avoid them. Many covered entities and business associates are compliant with this requirement yet fail to provide training regularly enough to prevent cyberattacks and the associated privacy violations.
How Has HIPAA Fared with Changing Technology?
No legislative act will be able to maintain pace with the pace at which technology has evolved, especially one covering the healthcare industry. This is why HIPAA provided a framework rather than specifics and incorporated flexibility to accommodate for changes to healthcare technology and evolving privacy and security best practices.
Updates have been made over the years which have amended HIPAA to maintain relevance, such as the 2008 Genetic Information Non-discrimination Act (GINA) which restricts the use of individuals’ genetic data by health insurers and employers and the American Recovery and Reinvestment Act, of which the HITECH Act was part, which strengthened HIPAA in relation to the adoption of EHRs.
However, many new technologies have emerged over the years that are not covered by HIPAA. Personal electronic devices are extensively used which can collect huge amounts of personal and health data, such as fitness trackers and other wearable devices and smartphones have made it much easier for individuals to obtain, use, and share healthcare data.
Many of these devices collect data that would fall under the category of PHI if created or collected by a HIPAA-covered entity but are not within the scope of HIPAA, even though the same data are often collected by those devices. The extent to which these devices are now being used, and the sheer volume of digital health and wellness data being generated outside the healthcare system by individuals, is a growing cause of concern. Without the protections of HIPAA, healthcare data may not be properly protected and could be shared extensively or sold on with ease.
The HIPAA Privacy Rule does not adequately cover the collection of healthcare data, as it only covers uses and disclosures by certain entities. It does not apply to health data itself, and this could be argued is one of the biggest failures of HIPAA. The same is true of the HIPAA Security Rule, which also has a restrictive scope and only calls for administrative, physical, and technical safeguards for the healthcare data held, received, or transmitted by HIPAA-covered entities and their business associates.
Healthcare data is extremely valuable, and not only to bad actors such as cybercriminals. Cybercriminals can use healthcare data for fraud and identity theft, but it also has tremendous value to a wide range of businesses. Healthcare and wellness data can be used by insurers to gauge risk – which can affect insurance premiums. Employers can use health data to make decisions about potential new hires, and all manner of other businesses can use the data to make decisions about individuals that could have significant consequences for the data subjects.
The question about whether HIPAA should be updated to cover all healthcare data has yet to be fully answered. Many attempts have been made to introduce legislation to cover all healthcare data, but each has failed to make it through the Senate.
The scope of HIPAA could be expanded to include individually identifiable health information collected, used, transmitted, or maintained by non-HIPAA covered entities and non-business associates. Alternatively, new separate legislation is required to cover healthcare data not currently regulated by HIPAA. The solution could well be to leave HIPAA as it is and to instead introduce a national privacy law akin to the EU’s General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA).
HIPAA Training and Education Need to Improve
HIPAA is not perfect and there are still significant gaps in the legislation, something that the coronavirus pandemic has highlighted. HIPAA doesn’t extend to the army of contact tracers and the data they collect, nor does it adequately cover exposure notification apps and may disclosures of COVID-19 related data. This is an area, like personal health apps, that needs to be addressed as there is considerable potential for privacy violations.
Vaccination programs have highlighted several areas where education needs to be improved. There have been many cases of HIPAA being cited as a reason not to disclose or share vaccination data, when HIPAA does not place restrictions on disclosures of vaccination information by individuals to employers or others.
Training remains a key issue with HIPAA and is often a much bigger weakness than technology or the HIPAA text itself. It is often uninformed people, and not healthcare technology and privacy and security controls, that are the reason for security breaches and privacy violations. While updates to HIPAA are needed, improvements need to be made to training programs to ensure all individuals with access to PHI or systems containing PHI are aware of their responsibilities and are trained how to be HIPAA-compliant employees.
Training needs to be appropriate to the role of each individual and training needs to be reinforced. Regular training sessions need to be provided to the workforce to make sure that the requirements of HIPAA are fully understood and are not forgotten over time. At many covered entities and business associates, employee training on HIPAA is not provided frequently enough.
Proposed Updates to the HIPAA Privacy Rule
Ahead of the 25-year anniversary of the HIPAA Privacy Rule, a significant update was proposed by the HHS. The proposed update published by the HHS in 2020 is intended to address several aspects of the Privacy Rule that are hampering care coordination and adding an unnecessary administrative burden on healthcare providers.
One of the main reasons for the update, according to then HHS Secretary Alex Azar, was to “break down barriers that have stood in the way of common sense care coordination and value-based arrangements for far too long.” The proposed update will improve care coordination and case management for patients, allow families and caregivers to become more involved in the provision of care to individuals, improve patients’ access to their health data, and will introduce new flexibilities covering disclosures of PHI in emergency and threatening situations, while also reducing the administrative burden on healthcare organizations. These updates have been long overdue but there has been criticism that the updates do not go far enough, and that some of the suggested updates are ill-advised.
One of the aspects addressed in the update will make it easier for patients to obtain a copy of their electronic healthcare data, but there are potential privacy and security risks with the change. Patients will be given the “right to direct the transmission of certain protected health information in an electronic format to a third party.” This right will help patients share their healthcare data with research organizations, but there are concerns that this change could have a negative impact on patients. Patients could request their health data be sent to anyone they choose, when the transmission of data to an entity not covered by the protections of HIPAA carries a security risk. The new right will certainly give patients much greater access and control over their personal data, but potentially it increases the risks that PHI may fall into the hands of bad actors.
The Future of HIPAA
HIPAA has been a great success, but it is far from perfect. There are still areas that require tweaking to improve usability and remove some of the administrative burden placed on HIPAA-covered entities. Proposed updates to the HIPAA Privacy Rule go some way to addressing some of the issues, but for many, the new HIPAA regulations that have been proposed do not go nearly far enough and some of the proposed changes have potential to cause privacy issues.
Overall, for legislation that is 25 years old, HIPAA has, with its various amendments, survived the test of time and is even more relevant and useful now than it was when it was first signed into law in 1996. HIPAA should be viewed as a work in progress though, and as far as the Future of HIPAA is concerned, there are likely to need to be further updates to ensure it remains relevant and effective.
Future of HIPAA FAQs
Does HIPAA cover all healthcare data?
HIPAA covers identifiable healthcare data, which is any healthcare data created, collected, transmitted, or maintained by a HIPAA-covered entity or business associate for treatment, payment for healthcare, or healthcare operations relating to the past, present, or future health status of an individual. Health data is not covered by HIPAA if it is created, stored, or transmitted by a non-HIPAA-covered entity or non-business associate.
Who does HIPAA apply to?
HIPAA applies to HIPAA-covered entities and their business associates. HIPAA-covered entities are healthcare providers, health plans, and healthcare clearinghouses that conduct electronic transactions involving PHI for which the HHS has developed standards. Business associates are vendors that provide products or services to HIPAA-covered entities that requires contact with PHI. HIPAA does not apply to other entities such as reporters, senators, individuals, and most employers.
Are there privacy risks associated with health apps?
Health apps, fitness trackers, and other wearable devices are not generally covered by HIPAA, nor are the data they collect or transmit. Without the protection of HIPAA, health app developers may use, disclose, or sell health data collected through the apps, and the security measures implemented may not meet HIPAA standards. There may be privacy and security risks associated with the use of these apps and devices.
Does HIPAA prevent disclosures of COVID-19 vaccination information?
Many people hide behind HIPAA and use the regulation as an excuse not to answer questions. One of the most notable recent examples, of which there are many, came from Marjorie Taylor Greene when asked about her vaccination status and cited HIPAA as the reason she could not disclose the information. HIPAA does not prevent such discloses. It only places restrictions on uses and disclosures by healthcare providers, health plans, healthcare clearinghouses, and business associates of those entities.
How often does HIPAA training need to be provided?
HIPAA training must be provided to all healthcare employees within a reasonable period of time after the person joins the covered entity’s workforce, as well as when functions are affected by a material change in policies or procedures and following any updates to the HIPAA Rules. HIPAA refresher training should also be provided at least annually, and no later than every two years. Annual training is the best practice.
The post Future of HIPAA: Reflections at the 25th Anniversary of HIPAA appeared first on HIPAA Journal.