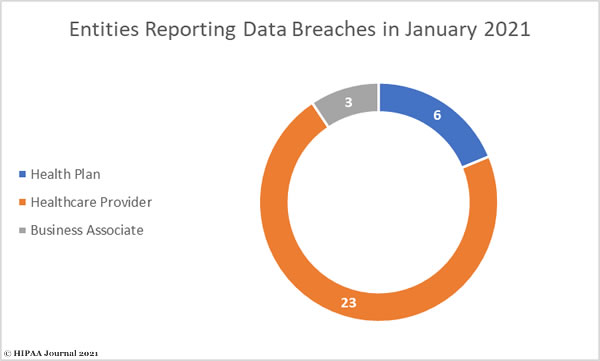
More large healthcare data breaches were reported in 2020 than in any other year since the HITECH Act called for the U.S. Department of Health and Human Services’ Office for Civil Rights to start publishing healthcare data breach figures on its website.
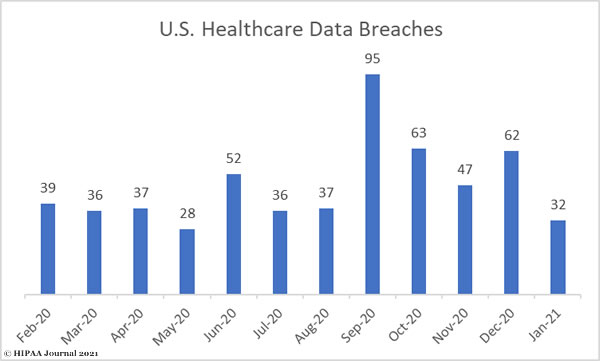
In 2020, healthcare data breaches of 500 or more records were reported at a rate of more than 1.76 per day. 2020 saw 642 large data breaches reported by healthcare providers, health plans, healthcare clearing houses and business associates of those entities – 25% more than 2019, which was also a record-breaking year.
More than twice the number of data breaches are now being reported than 6 years ago and three times the number of data breaches that occurred in 2010.
Key Takeaways
- 25% year-over-year increase in healthcare data breaches.
- Healthcare data breaches have doubled since 2014.
- 642 healthcare data breaches of 500 or more records were reported in 2020.
- 76 data breaches of 500 or more healthcare records were reported each day in 2020.
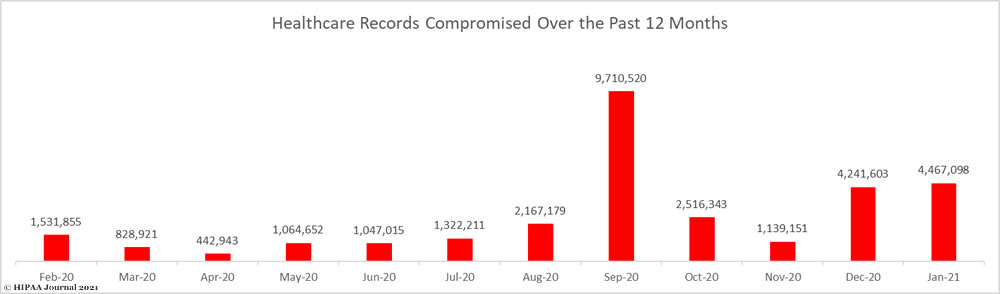
- 2020 saw more than 29 million healthcare records breached.
- One breach involved more than 10 million records and 63 saw more than 100K records breached.
- Hacking/IT incidents accounted for 67% of data breaches and 92% of breached records.
- 3,705 data breaches of 500 or more records have been reported since October 2009.
- 78 million healthcare records have been breached since October 2009.
2020 was the third worst year in terms of the number of breached healthcare records, with 29,298,012 records reported as having been exposed or impermissibly disclosed in 2020. While that is an alarming number of records, it is 29.71% fewer than in 2019. 266.78 million healthcare records have been breached since October 2009 across 3,705 reported data breaches of 500 or more records.

The Largest Healthcare Data Breaches in 2020
The largest healthcare data breach of 2020 was a ransomware attack on the cloud service provider Blackbaud Inc. The actual number of records exposed and obtained by the hackers has not been made public, but more than 100 of Blackbaud’s healthcare clients were affected and more than 10 million records are known to have been compromised. The breach does not appear on the OCR breach portal, as each entity affected has reported the breach separately.
Prior to deploying ransomware, the hackers stole the fundraising and donor databases of many of its clients which included information such as names, contact information, dates of birth, and some clinical information. Victims included Trinity Health (3.3 million records), Inova Health System (1 million records), and Northern Light Health Foundation (657,392 records).
The Florida-based business associate MEDNAX Services Inc, a provider of revenue cycle management and other administrative services to its affiliated physician practice groups, experienced the largest phishing attack of the year. Hackers gained access to its Office 365 environment and potentially obtained the ePHI of 1,670 individuals, including Social Security numbers, driver’s license numbers, and health insurance and financial information.
Magellan Health’s million-record data breach also started with a phishing email but and ended with ransomware being deployed. The breach affected several of its affiliated entities and potentially saw patient information stolen.
Dental Care Alliance, a dental support organization with more than 320 affiliated dental practices across 20 states, had its systems hacked and the dental records of more than 1 million individuals were potentially stolen.
63 security incidents were reported in 2020 by HIPAA-covered entities and business associates that involved 100,000 or more healthcare records.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| Trinity Health |
Business Associate |
3,320,726 |
Hacking/IT Incident |
| MEDNAX Services, Inc. |
Business Associate |
1,290,670 |
Hacking/IT Incident |
| Inova Health System |
Healthcare Provider |
1,045,270 |
Hacking/IT Incident |
| Magellan Health Inc. |
Health Plan |
1,013,956 |
Hacking/IT Incident |
| Dental Care Alliance, LLC |
Business Associate |
1,004,304 |
Hacking/IT Incident |
| Luxottica of America Inc. |
Business Associate |
829,454 |
Hacking/IT Incident |
| Northern Light Health |
Business Associate |
657,392 |
Hacking/IT Incident |
| Health Share of Oregon |
Health Plan |
654,362 |
Theft |
| Florida Orthopaedic Institute |
Healthcare Provider |
640,000 |
Hacking/IT Incident |
| Elkhart Emergency Physicians, Inc. |
Healthcare Provider |
550,000 |
Improper Disposal |
| Aetna ACE |
Health Plan |
484,157 |
Hacking/IT Incident |
| Saint Luke’s Foundation |
Healthcare Provider |
360,212 |
Hacking/IT Incident |
| NorthShore University HealthSystem |
Healthcare Provider |
348,746 |
Hacking/IT Incident |
| SCL Health – Colorado |
Healthcare Provider |
343,493 |
Hacking/IT Incident |
| AdventHealth |
Healthcare Provider |
315,811 |
Hacking/IT Incident |
| Nuvance Health |
Healthcare Provider |
314,829 |
Hacking/IT Incident |
| Magellan Rx Management |
Business Associate |
314,704 |
Hacking/IT Incident |
| The Baton Rouge Clinic |
Healthcare Provider |
308,169 |
Hacking/IT Incident |
| Allegheny Health Network |
Healthcare Provider |
299,507 |
Hacking/IT Incident |
| Northeast Radiology |
Healthcare Provider |
298,532 |
Hacking/IT Incident |
Main Causes of 2020 Healthcare Data Breaches
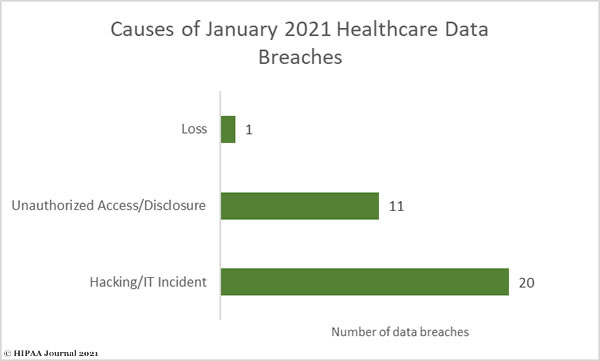
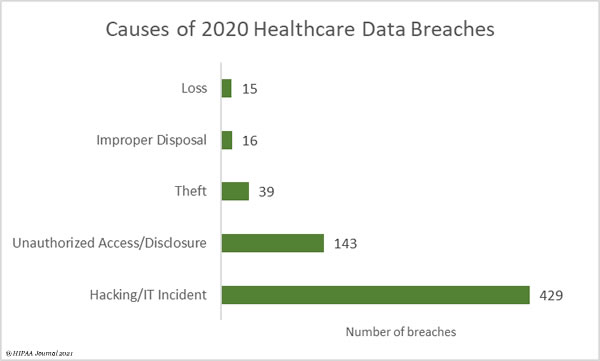
Hacking and other IT incidents dominated the healthcare data breach reports in 2020. 429 hacking/IT-related data breaches were reported in 2020, which account for 66.82% of all reported breaches and 91.99% of all breached records. These incidents include exploitation of vulnerabilities and phishing, malware, and ransomware attacks, with the latter having increased considerably in recent months.
A recent report from Check Point revealed there was a 71% increase in ransomware attacks on healthcare providers in October, and a further 45% increase in healthcare cyberattacks in the last two months of 2020. Some of the year’s largest and most damaging breaches to affect the healthcare industry in 2020 involved ransomware. In many cases, systems were taken out of action for weeks and patient services were affected. Ryuk, Sodinokibi (REvil), Conti, and Egregor ransomware have been the main culprits, with the healthcare industry heavily targeted during the pandemic.
Unauthorized access/disclosure incidents accounted for 22.27% of the year’s breaches and 2.69% of breached records. These incidents include the accessing of healthcare records my malicious insiders, snooping on medical records by healthcare workers, accidental disclosures of PHI to unauthorised individuals, and human error that exposes patient data.
| Breach Type |
Number of breaches |
Records breached |
Mean Records Breached
|
Median Records Breached |
| Hacking/IT Incident |
429 |
26,949,956 |
62,820 |
8,000 |
| Unauthorized Access/Disclosure |
143 |
787,015 |
5,504 |
1,713 |
| Theft |
39 |
806,552 |
20,681 |
1,319 |
| Improper Disposal |
16 |
584,980 |
36,561 |
1,038 |
| Loss |
15 |
169,509 |
11,301 |
2,298 |
Location of Breached Protected Health Information
The increased use of encryption and cloud services for storing data have helped to reduce the number of loss/theft incidents, which used to account for the majority of reported breaches. Phishing attacks are still a leading cause of data breaches in healthcare and are often the first step in a multi-stage attack that sees malware or ransomware deployed.
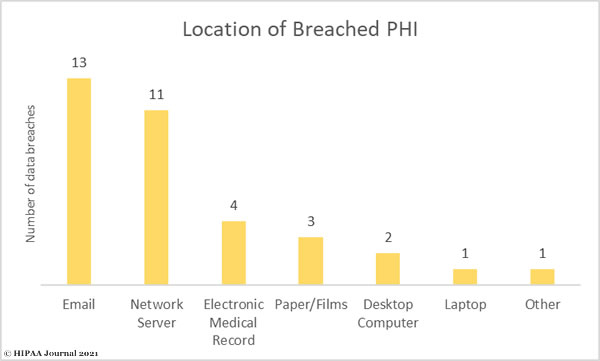
Email account breaches were reported at a rate of more than 1 every two days in 2020, but email-related breaches took second spot this year behind breaches of network servers. Network servers often store large amounts of patient data and are a prime target for hackers and ransomware gangs.
While the majority of healthcare data breaches have involved electronic protected health information, a significant percentage of breaches in 2020 involved paper/film copies of protected health information which were obtained by unauthorized individuals, lost, or disposed of in an insecure manner.

Which Entities Suffered the Most Data Breaches in 2020?
The pie chart below shows the breakdown of HIPAA covered entities affected by data breaches of 500 or more records in 2020. Healthcare providers suffered the most breaches with 497 reported incidents. Business associates reported 73 data breaches, but it should be noted that in many cases a breach was experienced at the business associate, but the incident was reported by the covered entities affected. In total, 258 of the year’s breaches had some business associate involvement, which is 40.19% of all breaches. There were 70 breaches reported by health plans, and 2 breaches reported by healthcare clearinghouses.
2020 Healthcare Data Breaches by State
South Dakota, Vermont, Wyoming residents survived 2020 without experiencing any healthcare data breaches, but there were breaches reported by entities based in all other states and the District of Columbia.
California was the worst affected state with 51 breaches, followed by Florida and Texas with 44, New York with 43, and Pennsylvania with 39.
| State |
No. Breaches |
State |
No. Breaches |
State |
No. Breaches |
State |
No. Breaches |
| California |
51 |
Virginia |
18 |
New Jersey |
9 |
Kansas |
3 |
| Florida |
44 |
Indiana |
17 |
South Carolina |
9 |
Nebraska |
3 |
| Texas |
44 |
Massachusetts |
17 |
Washington |
9 |
West Virginia |
3 |
| New York |
43 |
Maryland |
16 |
Delaware |
8 |
District of Columbia |
2 |
| Pennsylvania |
39 |
North Carolina |
16 |
Utah |
8 |
Idaho |
2 |
| Ohio |
27 |
Colorado |
14 |
Louisiana |
6 |
Nevada |
2 |
| Iowa |
26 |
Missouri |
14 |
Maine |
6 |
Oklahoma |
2 |
| Michigan |
21 |
Arizona |
12 |
New Mexico |
6 |
Mississippi |
1 |
| Georgia |
20 |
Arkansas |
12 |
Oregon |
5 |
Montana |
1 |
| Illinois |
20 |
Kentucky |
12 |
Hawaii |
4 |
New Hampshire |
1 |
| Minnesota |
20 |
Wisconsin |
12 |
Alabama |
3 |
North Dakota |
1 |
| Connecticut |
19 |
Tennessee |
10 |
Alaska |
3 |
Rhode Island |
1 |
HHS HIPAA Enforcement in 2020
2020 was a busy year in terms of HIPAA enforcement. The HHS’ Office for Civil Rights, the main enforcer of HIPAA compliance, conducted 19 HIPAA compliance investigations that resulted in financial penalties. More penalties were agreed with HIPAA covered entities and business associates in 2020 than in any other year since OCR started enforcing HIPAA compliance. $13,554,900 was paid in penalties across the 19 cases.
It can take several years from the start of an investigation before a financial penalty is levied. Some of the largest settlements of the year date back to breaches that were experienced in 2015 or earlier; however, the large increase in financial penalties in 2020 is largely due to a HIPAA enforcement drive launched by OCR in late 2019 to tackle noncompliance with the HIPAA Right of Access. There were 11 settlements reached with healthcare providers in 2020 to resolve cases where individuals were not provided with timely access to their medical records.
You can view a summary of OCR’s 2020 HIPAA enforcement actions in this post.
State AG HIPAA Enforcement in 2020
OCR is not the only enforcer of HIPAA compliance. State attorney generals also have the authority to take action against entities found not to be in compliance with the HIPAA Rules. There has been a trend for state attorneys general to work together and pool resources in their legal actions for noncompliance with the HIPAA Rules. In 2020, two multi-state actions were settled with HIPAA covered entities/business associates to resolve violations of the HIPAA Rules.
The health insurer Anthem Inc. settled a case that stemmed from its 78.8 million-record data breach in 2015 and paid financial penalties totalling $48.2 million to resolve multiple potential violations of HIPAA and state laws.
CHSPSC LLC, a Tennessee-based management company that provides services to subsidiary hospital operator companies and other affiliates of Community Health Systems, also settled a multi-state action and paid a financial penalty of $5 million to resolve alleged HIPAA violations. The case stemmed from a 2014 data breach that saw the ePHI of 6,121,158 individuals stolen by hackers.
About This Report
The Health Insurance Portability and Accountability Act (HIPAA) requires all healthcare data breaches to be reported to the HHS’ Office for Civil Rights. A summary of breaches of 500 or more records is published by the HHS Office for Civil Rights. This report was compiled using data on the HHS website on 01/19/21 and includes data breaches currently under investigation and archived cases.
The post 2020 Healthcare Data Breach Report: 25% Increase in Breaches in 2020 appeared first on HIPAA Journal.