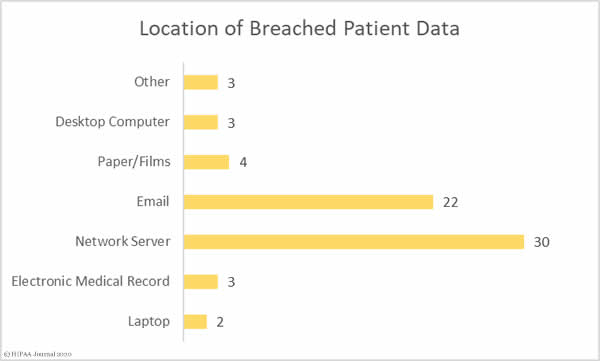
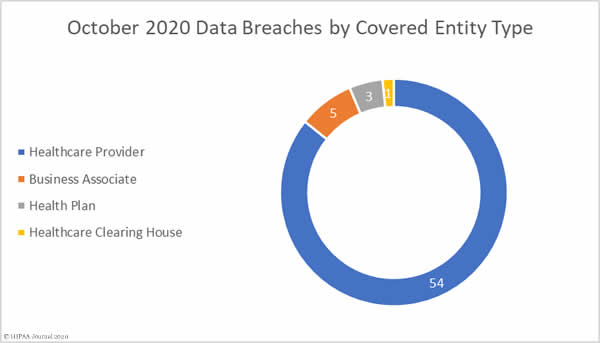
The Department of Health and Human Services’ Office for Civil Rights has published new guidance on the Health Insurance Portability and Accountability Act (HIPAA) Rules covering disclosures of protected health information (PHI) to health information exchanges (HIEs) for the public health activities of a public health authority (PHA).
An HIE is an organization that enables the sharing of electronic PHI (ePHI) between more than two unaffiliated entities such as healthcare providers, health plans, and their business associates. HIEs’ share ePHI for treatment, payment, or healthcare operations, for public health reporting to PHAs, and for providing other functions and services such as patient record location and data aggregation and analysis.
HIPAA supports the use of HIEs and the sharing of health data to improve public health, which has been especially important during the COVID-19 public health emergency. The HIPAA Privacy Rule permits HIPAA-covered entities and their business associates to disclose protected health information to an HIE for reporting to a PHA that is engaged in public health, without requiring prior individual authorization.
Such disclosures are permitted under the following circumstances:
- When disclosures are required by federal, state, local, or other laws that are enforceable in court
- When the HIE is acting under a grant of authority or contract with a PHA for a public health activity
- When the HIE is a business associate of the covered entity or another business associate, and wishes to provide ePHI to a PHA for public health purposes*
*The HIPAA Privacy Rule only permits an HIE which is a business associate of the covered entity or another business associate to disclose ePHI to a PHA for public health purposes if it is expressly stated that they can do so in the business associate agreement (BAA) with the covered entity. However, earlier this year in response to the COVID-19 public health emergency, OCR issued a notice of enforcement discretion stating no action will be taken against a business associate for good faith disclosures of ePHI to a PHA for public health purposes if they are not expressly permitted to disclose ePHI to a PHA in their BAA. In such cases, the business associate must inform the covered entity within 10 calendar days of the disclosure. The notice of enforcement discretion is only valid for the duration of the COVID-19 public health emergency. When the Secretary of the HHS declares the COVID-19 public health emergency over, such disclosures will no longer be permitted unless expressly permitted in the BAA.
Disclosures of ePHI by an HIE to a PHA should be limited to the minimum necessary information to achieve the purpose for the disclosure. A covered entity can rely on a PHA’s request to disclose a summary record to the PHA or HIE as being the minimum necessary PHI to achieve the public health purpose of the disclosure.
A covered entity is permitted by the HIPAA Privacy Rule to disclose ePHI to a PHA through an HIE, even if a direct request for the PHI is not received from the PHA, provided the covered entity knows that the PHA is using the HIE to collect such information, or that the HIE is acting on behalf of the PHA.
While the above disclosures of ePHI for public health purposes do not require authorizations to be obtained from the individuals whose PHI is being disclosed, those individuals must be notified about such disclosures. That can be achieved by stating disclosures of ePHI will occur for public health purposes in the organization’s Notice of Privacy Practices.
You can view the OCR guidance, which includes several examples related to COVID-19, on the HHS website, which can be accessed on this link (PDF).
The post OCR Issues Guidance on Disclosures of PHI to Health Information Exchanges under HIPAA appeared first on HIPAA Journal.