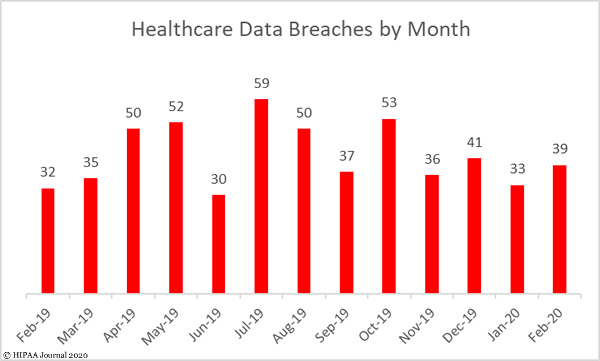
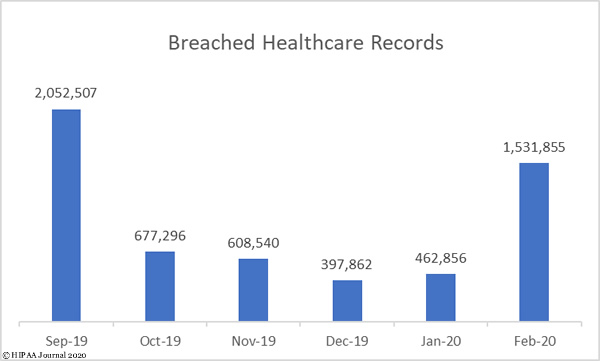
There were 39 reported healthcare data breaches of 500 or more records in February and 1,531,855 records were breached, which represents a 21.9% month-over-month increase in data breaches and a 231% increase in breached records. More records were breached in February than in the past three months combined. In February, the average breach size was 39,278 records and the mean breach size was 3,335 records.
Largest Healthcare Data Breaches in February 2020
The largest healthcare data breach was reported by the health plan, Health Share of Oregon. An unencrypted laptop computer containing the records of 654,362 plan members was stolen from its transportation vendor in an office break in.
The second largest breach was a ransomware attack on the accounting firm BST & Co. CPAs which saw client records encrypted, including those of the New York medical group, Community Care Physicians. Aside from the network server breach at SOLO Laboratories, the cause of which has not been determined, the remaining 7 breaches in the top 10 were all email security incidents.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Location of Breached PHI |
| Health Share of Oregon |
Health Plan |
654,362 |
Theft |
Laptop |
| BST & Co. CPAs, LLP |
Business Associate |
170,000 |
Hacking/IT Incident |
Network Server |
| Aveanna Healthcare |
Healthcare Provider |
166,077 |
Hacking/IT Incident |
Email |
| Overlake Medical Center & Clinics |
Healthcare Provider |
109,000 |
Hacking/IT Incident |
Email |
| Tennessee Orthopaedic Alliance |
Healthcare Provider |
81,146 |
Hacking/IT Incident |
Email |
| Munson Healthcare |
Healthcare Provider |
75,202 |
Hacking/IT Incident |
Email |
| NCH Healthcare System, Inc. |
Healthcare Provider |
63,581 |
Hacking/IT Incident |
Email |
| SOLO Laboratories, Inc. |
Business Associate |
60,000 |
Hacking/IT Incident |
Network Server |
| JDC Healthcare Management |
Healthcare Provider |
45,748 |
Hacking/IT Incident |
Email |
| Ozark Orthopaedics, PA |
Healthcare Provider |
15,240 |
Hacking/IT Incident |
Email |
Causes of February Healthcare Data Breaches
Hacking/IT incidents dominated the breach reports, accounting for two thirds (66.67%) of all breaches reported in February and 54.78% of breached records (839,226 records). The average breach size was 32,277 records and the median breach size was 4,126 records. 80.76% of those incidents involved hacked email accounts.
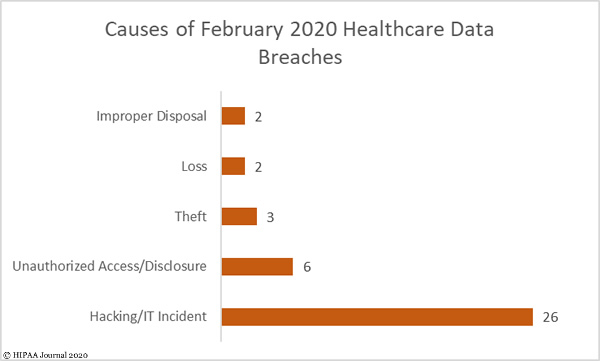
There were 6 unauthorized access/disclosure incidents, four of which involved paper/films, one was an email incident and one involved a portable electronic device. 15,826 records were impermissibly disclosed in those incidents. The average breach size was 3,126 records and the median breach size was 2,548 records.
While there were only three theft incidents reported, they accounted for 42.78% of breached records. The average breach size was 327,696 records and the median breach size was 530 records.
There were two incidents involving lost paperwork containing the PHI of 5,904 patients and two improper disposal incidents involving paper files containing the PHI of 15,507 patients.
Location of Breached Protected Health Information
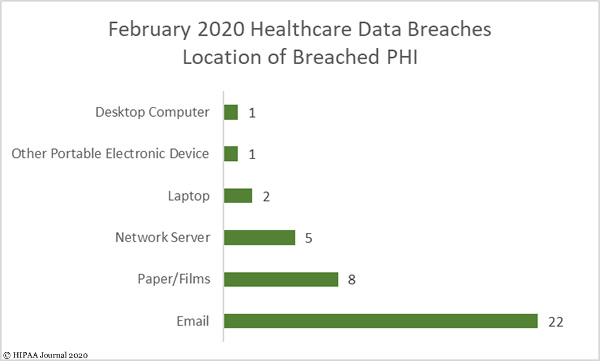
As the bar chart below shows, the biggest problem area for healthcare organizations is protecting email accounts. All but one of the email incidents were hacking incidents that occurred as a result of employees responding to phishing emails. The high total demonstrates how important it is to implement a powerful email security solution and to provide regular training to employees to teach them how to recognize phishing emails.
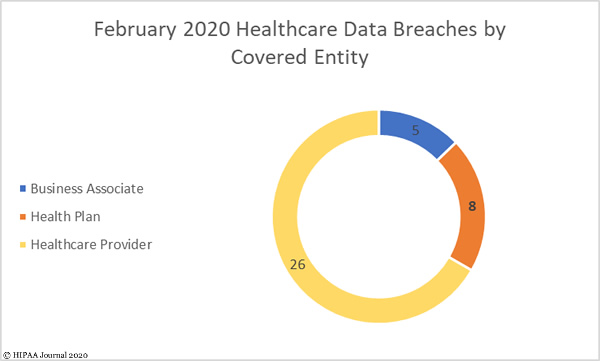
Breaches by Covered Entity Type
26 data breaches were reported by HIPAA-covered entities in February. The average breach size was 23,589 records and the median breach size was 3,229 records. Data breaches were reported by 8 health plans, with an average breach size of 83,490 records and a median breach size of 2,468 records.
There were 5 data breaches reported by business associates and a further 5 breaches that were reported by the covered entity but had some business associate involvement. The average breach size was 50,124 records and the median breach size was 15,010 records.
Healthcare Data Breaches by State
The data breaches reported in February were spread across 24 states. Texas was the worst affected with 4 breaches. Three data breaches were reported in Arkansas, California, and Florida. There were two reported breaches in each of Georgia, Indiana, Michigan, North Carolina, Virginia, and Washington. One breach was reported in each of Arizona, Hawaii, Illinois, Iowa, Maine, Massachusetts, Minnesota, Missouri, New Mexico, New York, Oregon, Pennsylvania, Tennessee, and Wisconsin.
HIPAA Enforcement Activity in February 2020
There was one HIPAA enforcement action reported in February. The HHS’ Office for Civil Rights announced that Steven A. Porter, M.D had agreed to pay a financial penalty of $100,000 to resolve a HIPAA violation case. The violations came to light during an investigation of a reported breach involving the practice’s medical records company, which Dr. Porter claimed was impermissibly using patient medical records by preventing access until payment of $50,000 was received.
OCR found that Dr. Porter had never conducted a risk analysis to identify risks to the confidentiality, integrity, and availability of ePHI. The practice had also not reduced risks to a reasonable and appropriate level, and policies and procedures to prevent, detect, contain, and correct security violations had not been implemented.
The post February 2020 Healthcare Data Breach Report appeared first on HIPAA Journal.




