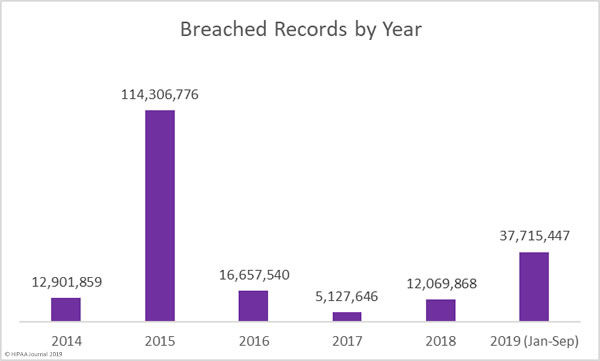
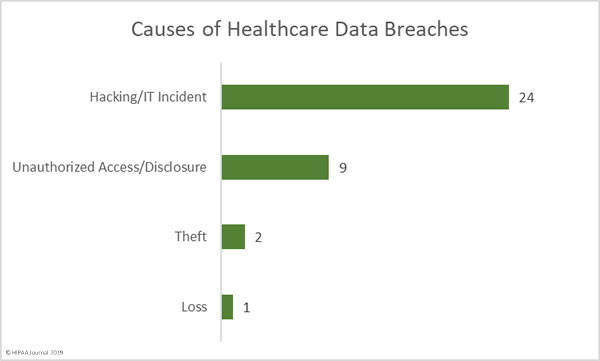
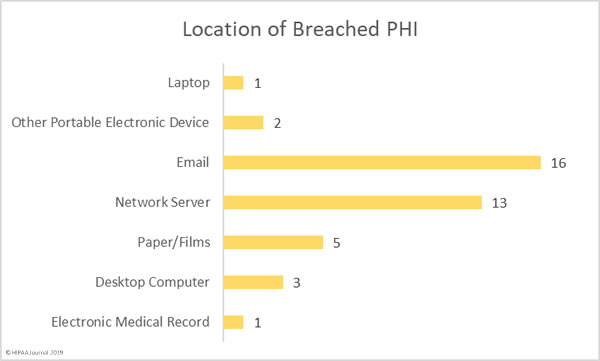
The Department of Health and Human Services’ Office for Civil Rights has imposed a $2.15 million civil monetary penalty against the Miami, FL-based nonprofit academic medical system, Jackson Health System (JHS), for a slew of violations of HIPAA Privacy Rule, Security Rule, and Breach Notification Rule.
In July 2015, OCR became aware of several media reports in which the PHI of a patient was impermissibly disclosed. The individual was a well-known NFL football player. Photographs of an operating room display board and schedule had also been shared on social media by a reporter. OCR launched an investigation in October 2015 and opened a compliance review in relation to the impermissible disclosure.
JHS investigated and submitted a report confirming a photograph was taken in which two patients PHI was visible, including the PHI of a well-known person in the community. The internal investigation revealed an employee had been accessing patient information without authorization since 2011. During that time, the employee had accessed the records of 24,188 patients without any legitimate work reason for doing so and had been selling that information.
HIPAA requires covered entities to implement policies and procedures to prevent, contain, and correct security violations – 45 C.F.R. § 164.308(a)(l) – however, before risks can be managed and reduced to a reasonable and acceptable level, a covered entity must conduct a comprehensive risk analysis – 45 C.F .R. §164.308(a)(l)(ii){A) – to ensure that all risks to the confidentiality, integrity, and availability of PHI are identified.
On several occasions, OCR requested documentation on risk analyses at JHS. JHS supplied documentation on internal assessments from 2009, 2012, and 2013, and risk analyses conducted by third parties in 2014, 2015, 2016, and 2017.
OCR discovered that prior to 2017, JHS had erroneously marked several aspects of the HIPAA Security Rule as non-applicable in the risk analyses. A risk analysis failure occurred in 2014 as it had failed to cover all ePHI and did not identify all risks to ePHI contained within JHS systems. JHS had also failed to provide documentation confirming measures had been implemented to reduce all risk to ePHI to a reasonable and appropriate level, even though recommendations had been made by the company that performed the 2014 risk analysis.
Similar risk analysis failures occurred in 2015. Some sections of the risk analysis conducted by a third party had not been completed, the risk analysis failed to cover all ePHI, and documentation could not be supplied confirming risk management efforts had taken place. It was a similar story in 2016, and the 2017 risk analysis was not comprehensive.
OCR investigators also discovered reviews of information system activity such as audit logs had not been regularly reviewed, in violation of 45 C.F.R. § 164.308(l)(ii)(D).
OCR also determined that between July 22, 2013 and January 27, 2016, policies and procedures had not been implemented to prevent, detect, contain, and correct security violations. The HIPAA Privacy Rule had also been violated, as reasonable efforts were not made to limit certain employees’ access to PHI, which had led to unauthorized access and impermissible disclosures. Access to PHI was also not limited to the minimum necessary information, in violation of 45 C.F.R. §164.308(a)(4) and 45 C.F.R. § 164.514(d).
On multiple occasions employees had accessed records without authorization when there was no treatment relationship with a patient, and also after a treatment relationship had come to an end.
JHS had also violated the HIPAA Breach Notification Rule by failing to report a breach within 60 days of discovery in violation of 45 C.F.R. § 164.408(b). The loss of boxes of files in 2013 was not reported for 160 days. JHS also admitted that it did not have policies in place covering PHI breaches prior to October 2013.
OCR attempted to resolve the HIPAA violations via informal means, but JHS failed to comply, which led to OCR issuing a Notice of Proposed Determination. JHS waived its right to a hearing and OCR issued a Notice of Final Determination, which was not contested and JHS paid the full financial penalty of $2,154,000.
“OCR’s investigation revealed a HIPAA compliance program that had been in disarray for a number of years,” explained OCR Director Roger Severino. “This hospital system’s compliance program failed to detect and stop an employee who stole and sold thousands of patient records; lost patient files without notifying OCR as required by law; and failed to properly secure PHI that was leaked to the media.”
This is the second financial penalty for a HIPAA covered entity to be announced this month and the fifth penalty to be issued in 2019. Earlier this month, Elite Dental Associates settled its HIPAA case with OCR for $10,000 following disclosures of patients’ PHI on the Yelp review site.
Settlements were also agreed with Bayfront Health St Petersburg ($85,000), Medical Informatics Engineering ($100,000), and Touchstone Medical Imaging ($3,000,000) earlier in the year.
The post Slew of HIPAA Violations Leads to $2.15 Million Civil Monetary Penalty for Jackson Health System appeared first on HIPAA Journal.