May 2019 was the worst ever month for healthcare data breaches with 46 reported breaches of more than 500 records. More breaches were reported in May than any other month since the HHS’ Office for Civil Rights started publishing breach summaries on its website in 2009. That record of 44 breaches was broken in July.
July saw 50 healthcare data breaches of more than 500 records reported to the Department of Health and Human Services’ Office for Civil Rights, which is 13 more breaches than the monthly average for 2019 and 20.5 more breaches than the monthly average for 2018.

July 2019 was the second worst month in terms of the number of healthcare records exposed. 25,375,729 records are known to have been exposed in July.

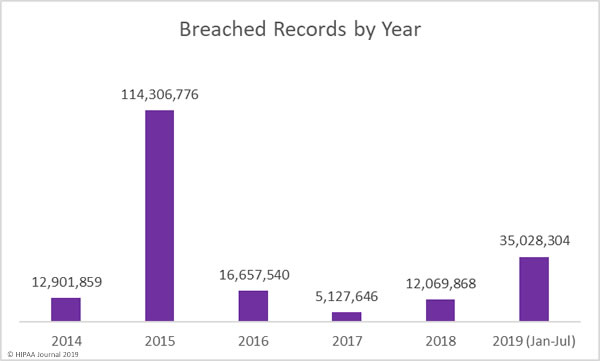
There are still 5 months left of 2019, yet more healthcare records have been breached this year than in all of 2016, 2017, and 2018 combined. More than 35 million individuals are known to have had their healthcare records compromised, exposed, or impermissibly disclosed this year.
Causes of July 2019 Healthcare Data Breaches
The main reason for the increase in reported data breaches in July is the colossal data breach at American Medical Collection Agency (AMCA). AMCA provides medical billing and collection services and its clients included some of the largest medical testing laboratories in the United States. Those clients have now been lost as a result of the breach.
The final victim count is not yet known, nor the number of records compromised in the breach. To date, 22 healthcare organizations have confirmed they have been affected and more than 24 million records are known to have been exposed. At least 8 healthcare organizations have not yet submitted their breach reports to OCR.
Healthcare Providers Impacted by the American Medical Collection Agency Data Breach
| |
Healthcare Organization |
Estimated Records Exposed |
Confirmed Victim Count |
| 1 |
Quest Diagnostics/Optum360 |
11,900,000 |
11,500,000 |
| 2 |
LabCorp |
7,700,000 |
10,251,784 |
| 3 |
Clinical Pathology Associates |
2,200,000 |
1,733,836 |
| 4 |
Carecentrix |
500,000 |
467,621 |
| 5 |
American Esoteric Laboratories |
541,900 |
409,789 |
| 6 |
Inform Diagnostics |
173,617 |
173,617 |
| 7 |
Laboratory Medicine Consultants |
147,600 |
140,590 |
| 8 |
Integrated Regional Laboratories |
29,644 |
29,644 |
| 21 |
Penobscot Community Health Center |
13,000 |
13,299 |
| 9 |
West Hills Hospital and Medical Center / United West Labs |
10,650 |
10,650 |
| 10 |
Seacoast Pathology, Inc |
10,000 |
8,992 |
| 11 |
Arizona Dermatopathology |
7,000 |
5,903 |
| 12 |
Western Pathology Consultants |
4,550 |
4,079 |
| 13 |
Natera |
3,000 |
3,035 |
| 14 |
Sunrise Medical Laboratories |
427,000 |
TBC |
| 15 |
BioReference Laboratories/Opko Health |
422,600 |
TBC |
| 16 |
CBLPath Inc. |
148,900 |
TBC |
| 17 |
CompuNet Clinical Laboratories |
111,000 |
TBC |
| 18 |
Austin Pathology Associates |
46,500 |
TBC |
| 19 |
South Texas Dermatopathology PLLC |
16,100 |
TBC |
| 20 |
Pathology Solutions |
13,300 |
TBC |
| 22 |
Laboratory of Dermatology ADX, LLC |
4,240 |
TBC |
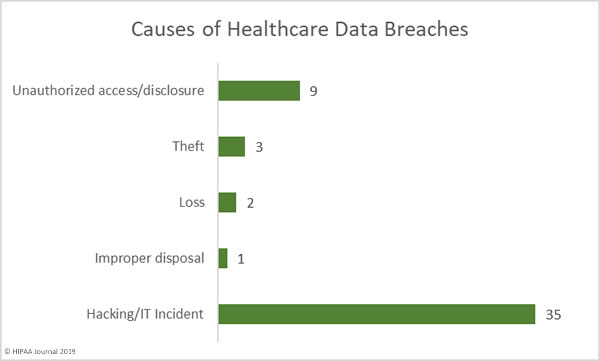
Hacking and IT incidents dominated the breach reports in July with 35 incidents reported. Those breaches resulted in the exposure of 23,203,853 healthcare records. The average breach size was 662,967 records and the mean breach size was 4,559 records.
There were 9 unauthorized access/disclosure incidents in July involving 2,160,699 healthcare records. The average breach size was 240,077 records and the mean breach size was 3,881 records.
There were three theft incidents reported that involved 3,584 records, 2 loss incidents that exposed 4,593 records, and one improper disposal incident that exposed 3,000 records.
Largest Healthcare Data Breaches in July 2019
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Location of Breached PHI |
| Optum360, LLC |
Business Associate |
11,500,000 |
Hacking/IT Incident |
Network Server |
| Laboratory Corporation of America Holdings dba LabCorp |
Healthcare Provider |
10,251,784 |
Hacking/IT Incident |
Network Server |
| Clinical Pathology Laboratories, Inc. |
Healthcare Provider |
1,733,836 |
Unauthorized Access/Disclosure |
Network Server |
| CareCentrix, Inc. |
Healthcare Provider |
467,621 |
Hacking/IT Incident |
Network Server |
| Bayamon Medical Center Corp. |
Healthcare Provider |
422,496 |
Hacking/IT Incident |
Network Server |
| Memphis Pathology Laboratory d/b/a American Esoteric Laboratories |
Healthcare Provider |
409,789 |
Unauthorized Access/Disclosure |
Network Server |
| Laboratory Medicine Consultants, Ltd. |
Healthcare Provider |
140,590 |
Hacking/IT Incident |
Network Server |
| Imperial Health, LLP |
Healthcare Provider |
116,262 |
Hacking/IT Incident |
Desktop Computer, Network Server |
| Puerto Rico Women And Children’s Hospital, LLC |
Healthcare Provider |
99,943 |
Hacking/IT Incident |
Network Server |
| Ameritas Life Insurance Corp. |
Health Plan |
39,675 |
Hacking/IT Incident |
Email |
Location of Breached Protected Health Information
There was a major increase in network server incidents in July. The rise was due to the AMCA breach but also an uptick in ransomware attacks on healthcare providers. Phishing also continues to pose problems for healthcare organizations. 21 of the breaches reported in July involved PHI stored in email accounts.
The number of reported phishing attacks strongly suggests multi-factor authentication has not yet been implemented by many healthcare organizations. If credentials are compromised, MFA can help prevent the email account from being remotely accessed.

July 2019 Healthcare Data Breaches by Covered Entity Type
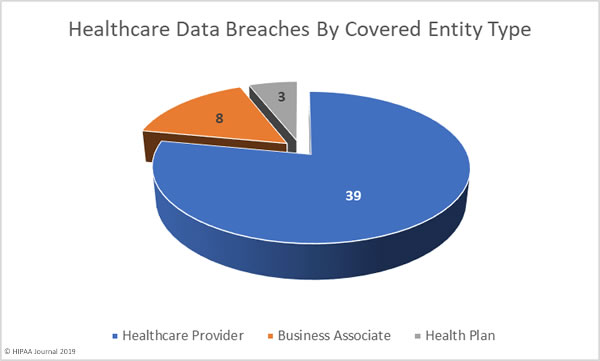
Healthcare providers were the worst affected covered entity in July with 39 breaches reported. Three health plans reported breaches and there were 8 breaches reported by business associates of HIPAA covered entities. A further 18 healthcare data breaches had some business associate involvement.
July 2019 Healthcare Data Breaches by State
July’s 50 data breaches were spread across 26 states and Puerto Rico. Typically, California experiences the most data breaches in any given month due to the number of healthcare organizations based in California; however, California only saw one healthcare data breach reported in July.
Minnesota was the worst affected state with 6 reported breaches. Four breaches were reported by healthcare organizations based in Michigan, Pennsylvania, and Texas. Three breaches were reported in Nevada and Tennessee, two breaches were reported in each of North Carolina, Ohio, Wisconsin, and Puerto Rico.
One breach was reported in each of Alabama, Arkansas, Arizona, California, Connecticut, Georgia, Kentucky, Louisiana, Massachusetts, Maryland, Maine, Missouri, Nebraska, New Hampshire, New York, Oregon, and South Carolina.
HIPAA Enforcement Activity in July 2019
It has been a relatively quiet year for HIPAA enforcement by the HHS’ Office for Civil Rights. While there were two settlements agreed in May 2019 to resolve HIPAA violations, no further financial penalties have been announced.
State Attorneys General also have the authority to take action against healthcare organizations that have violated HIPAA Rules. July saw one settlement reached between Premera Blue Cross and 30 state attorneys general over its 10.4 million-record data breach in 2014.
Under the terms of the settlement agreement, Premera Blue Cross is required to pay a financial penalty of $10,000,000 to resolve the HIPAA violations discovered during the Washington Attorney General-led investigation.
In addition to the $10 million penalty, Premera Blue Cross settled a class action lawsuit for $74 million. $32 million will cover claims from breach victims and $42 million will be directed toward improving cybersecurity.
The post July 2019 Healthcare Data Breach Report appeared first on HIPAA Journal.





