For the past two months, healthcare data breaches have been reported at a rate of 1.5 per day – Well above the typical rate of one per day. In June, data breaches returned to more normal levels with 30 breaches of more than 500 healthcare records reported in June – 31.8% fewer than May 2019.
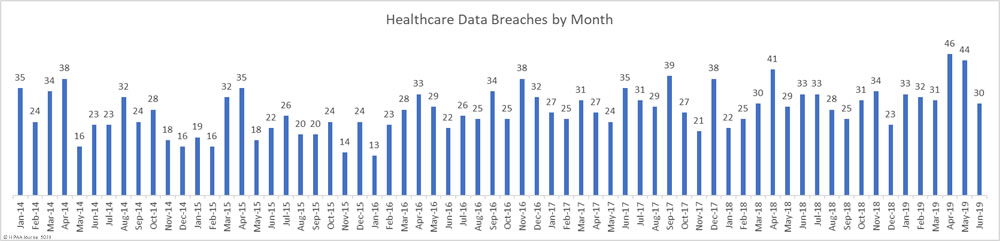
While the number of reported data breaches fell, June saw a 73.6% increase in the number of health records exposed in data breaches. 3,452,442 healthcare records were exposed in the 30 healthcare data breaches reported in June.
Largest Healthcare Data Breaches in June 2019
The increase in exposed records is due to a major breach at the dental health plan provider Dominion Dental Services (Dominion National Insurance Company). Dominion discovered an unauthorized individual had access to its systems and patient data for 9 years. During that time, the protected health information of 2,964,778 individuals may have been stolen. That makes it the largest healthcare data breach to be reported to the Office for Civil Rights so far in 2019 – At least for a month until entities affected by the breach at American Medical Collection Agency report the breach.
9 of the ten largest healthcare data breaches in June were hacking/IT incidents and the top six breaches involved network servers. Three email security breaches and one improper disposal incident round out the top ten.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Location of Breached Information |
| Dominion Dental Services, Inc., Dominion National Insurance Company, and Dominion Dental Services USA, Inc. |
Health Plan |
2,964,778 |
Hacking/IT Incident |
Network Server |
| Inform Diagnostics, Inc. |
Healthcare Provider |
173,617 |
Hacking/IT Incident |
Network Server |
| EyeCare Partners, LLC [on behalf of affiliated covered entities] |
Healthcare Provider |
141,165 |
Hacking/IT Incident |
Network Server |
| TenX Systems, LLC d/b/a ResiDex Software |
Business Associate |
90,000 |
Hacking/IT Incident |
Network Server |
| Shingle Springs Health and Wellness Center |
Healthcare Provider |
21,513 |
Hacking/IT Incident |
Network Server |
| Desert Healthcare Services, LLC |
Healthcare Provider |
8,000 |
Hacking/IT Incident |
Network Server |
| Summa Health |
Healthcare Provider |
7,989 |
Hacking/IT Incident |
Email |
| Community Physicians Group |
Healthcare Provider |
5,400 |
Hacking/IT Incident |
Email |
| Community Healthlink |
Healthcare Provider |
4,598 |
Hacking/IT Incident |
Email |
| Adventist Health Physician Services |
Healthcare Provider |
3,797 |
Improper Disposal |
Paper/Films |
The Year So Far
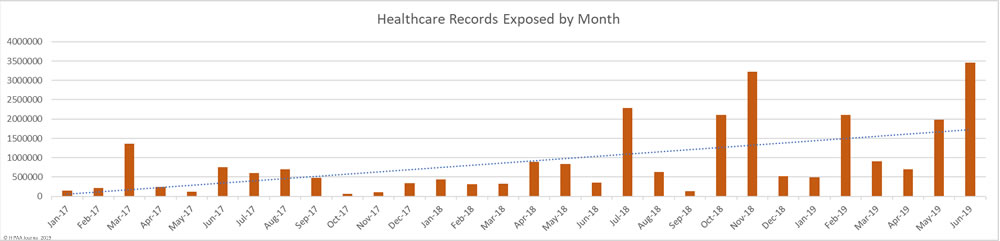
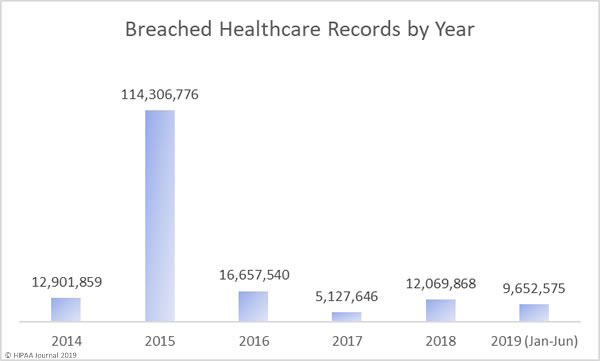
As you can see in the graph below, 2019 is shaping up to be a bad year for healthcare data breaches. In the first 6 months of 2019, the records of 9,652,575 Americans were exposed, impermissibly disclosed, or stolen. That is already almost double the records exposed in 2017 and last year’s total will soon be exceeded. The data breach at American Medical Collection Agency has yet to appear in the figures below. That breach alone will raise the 2019 total to almost 35 million healthcare records. That’s more healthcare records than were breached in 2016, 2017, and 2018 combined.
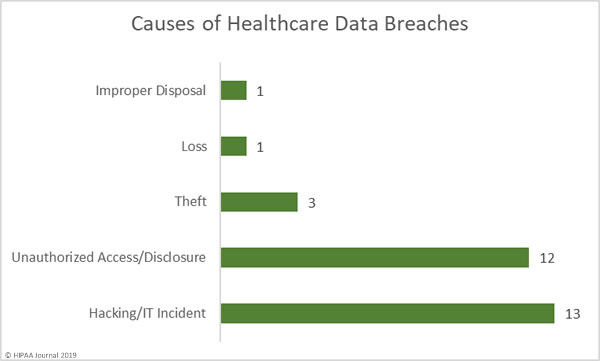
Causes of June 2019 Healthcare Data Breaches
There was a fairly even split between hacking/IT incidents and unauthorized access/disclosure incidents in June, which accounted for 83% of all breaches reported. There were 12 unauthorized access/disclosure incidents reported in June, but they typically involved small numbers of records. Unauthorized access/disclosure incidents impacted 18,165 patients. The mean breach size was 1,813 records and the median breach size was 1,502 records.
There were 13 hacking/IT incidents reported in June. While these breaches only accounted for 43% of all incidents reported in June, 3,424,422 healthcare records were compromised in those breaches – 99.19% of all records breached in June. The mean breach size was 263,417 records and the median breach size was 7,995 records.
There were three theft incidents reported involving 3,424 records. The mean breach size was 1,141 records and the median breach size was 1,282 records. One loss incident was reported that impacted 2,634 patients and one improper disposal incident exposed the PHI of 3,797 patients.
Location of Breached Protected Health Information
Phishing attacks are continuing to cause problems for healthcare providers, but so too is ransomware. There was a sharp increase in ransomware attacks in Q1 and the trend continued in Q2. Ransomware may have fallen out of favor with cybercriminals in 2018, but it appears to be back in vogue in 2019. Email is usually the most common location of breached PHI, but there was a fairly even split between networks server and email incidents in June. The rise in ransowmare and malware attacks in June account for the increase in network server incidents.

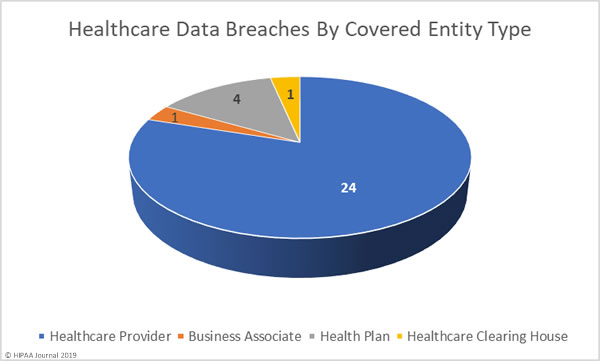
June 2019 Healthcare Data Breaches by Covered Entity Type
Healthcare providers reported 24 data breaches in June, one breach was reported by a health plan and one by a healthcare clearinghouse. While only one data breach was reported by a business associate, a further 7 data breaches had some business associate involvement.
June 2019 Healthcare Data Breaches by State
June’s 30 healthcare data breaches affected covered entities in 20 states. Arizona and California were the worst affected with three reported breaches. Florida, Massachusetts, Maryland, Minnesota, Missouri, and Ohio each experienced two breaches, and one breach was reported in each of Arkansas, Iowa, Illinois, Indiana, Kentucky, Michigan, Nevada, Pennsylvania, Texas, Virginia, Vermont, and Wyoming.
HIPAA Enforcement Actions in June 2019
One HIPAA enforcement action came to a conclusion in June. Premera Blue Cross agreed to settle a multi-state lawsuit over its 10.4-million-record data breach in 2017.
Premera Blue Cross is one of the nations largest health insurers. In early 2018, Premera discovered hackers had gained access to its network by exploiting an unpatched software vulnerability. The investigation into the breach revealed there had been basic security failures. The case, led by Washington State Attorney General Bob Ferguson, was settled for $10,000,000.
Alabama, Alaska, Arizona, Arkansas, California, Connecticut, Florida, Hawaii, Idaho, Indiana, Iowa, Kansas, Kentucky, Louisiana, Massachusetts, Minnesota, Mississippi, Montana, Nebraska, Nevada, New Jersey, North Carolina, North Dakota, Ohio, Oklahoma, Oregon, Rhode Island, Utah, Vermont and Washington all participated in the lawsuit.
The Department of Health and Human Services’ Office for Civil Rights did not issue any financial penalties for HIPAA violations in June.
The post June 2019 Healthcare Data Breach Report appeared first on HIPAA Journal.





