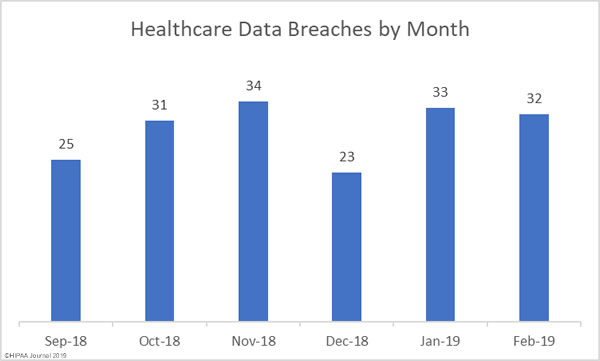
Healthcare data breaches continued to be reported at a rate of more than one a day in February. February saw 32 healthcare data breaches reported, one fewer than January.
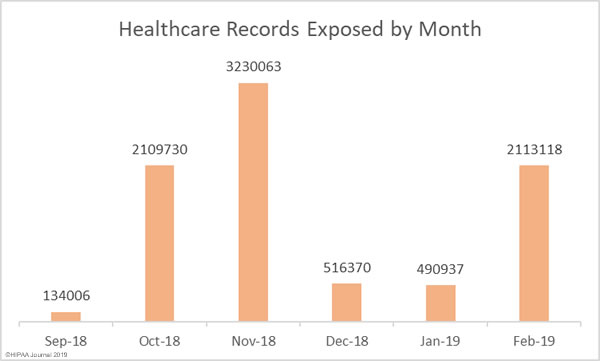
The number of reported breaches may have fell by 3%, but February’s breaches were far more severe. More than 2.11 million healthcare records were compromised in February breaches – A 330% increase from the previous month.
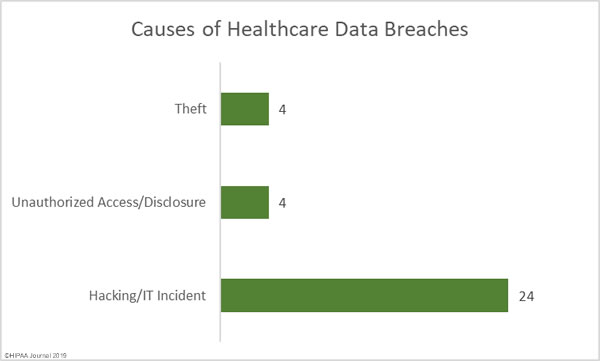
Causes of Healthcare Data Breaches in February 2019
Commonly there is a fairly even split between hacking/IT incidents and unauthorized access/disclosure incidents; however, in February, hacking and IT incidents such as malware infections and ransomware attacks dominated the healthcare data breach reports.
75% of all reported breaches in February (24 incidents) were hacking/IT incidents and those incidents resulted in the theft/exposure of 96.25% of all records that were breached. All but one of the top ten healthcare data breaches in February were due to hacks and IT incidents.
There were four unauthorized access/disclosure incidents and 4 cases of theft of physical or electronic PHI. The unauthorized access/disclosure incidents involved 3.1% of all compromised records and 0.65% of records were compromised in the theft incidents.
Largest Healthcare Data Breaches in February 2019
The largest healthcare data breach reported in February involved the accidental removal of safeguards on a network server, which allowed the protected health information of more than 973,000 patients of UW Medicine to be exposed on the internet. Files were indexed by the search engines and could be found with simple Google searches. Files stored on the network server were accessible for a period of more than 3 weeks.
The second largest data breach was due to a ransomware attack on Columbia Surgical Specialist of Spokane. While patient information may have been accessed, no evidence was found to suggest any ePHI was stolen by the attackers.
The 326,629-record breach at UConn Health was due to a phishing attack that saw multiple employees’ email accounts compromised, and one email account was compromised in a phishing attack on Rutland Regional Medical Center that contained the ePHi of more than 72,000 patients.
| Rank | Name of Covered Entity | Covered Entity Type | Individuals Affected | Type of Breach |
| 1 | UW Medicine | Healthcare Provider | 973,024 | Hacking/IT Incident |
| 2 | Columbia Surgical Specialist of Spokane | Healthcare Provider | 400,000 | Hacking/IT Incident |
| 3 | UConn Health | Healthcare Provider | 326,629 | Hacking/IT Incident |
| 4 | Rutland Regional Medical Center | Healthcare Provider | 72,224 | Hacking/IT Incident |
| 5 | Delaware Guidance Services for Children and Youth, Inc. | Healthcare Provider | 50,000 | Hacking/IT Incident |
| 6 | Rush University Medical Center | Healthcare Provider | 44,924 | Unauthorized Access/Disclosure |
| 7 | AdventHealth Medical Group | Healthcare Provider | 42,161 | Hacking/IT Incident |
| 8 | Reproductive Medicine and Infertility Associates, P.A. | Healthcare Provider | 40,000 | Hacking/IT Incident |
| 9 | Memorial Hospital at Gulfport | Healthcare Provider | 30,642 | Hacking/IT Incident |
| 10 | Pasquotank-Camden Emergency Medical Service | Healthcare Provider | 20,420 | Hacking/IT Incident |
Location of Breached Protected Health Information
Email is usually the most common location of compromised PHI, although in February there was a major rise in data breaches due to compromised network servers. 46.88% of all breaches reported in February involved ePHI stored on network servers, 25% involved ePHI stored in email, and 12.5% involved ePHI in electronic medical records.
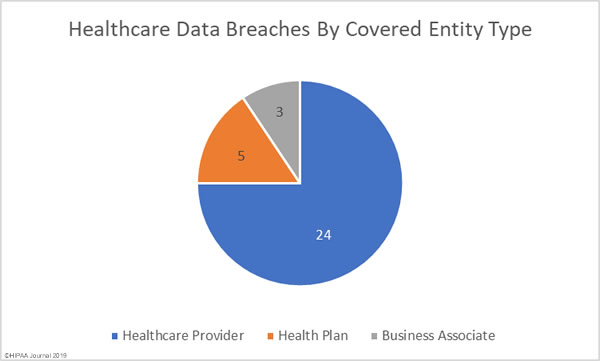
Healthcare Data Breaches by Covered Entity Type
Healthcare providers were the worst affected by data breaches in February 2019 with 24 incidents reported. There were five breaches reported by health plans, and three breaches reported by business associates of HIPAA-covered entities. A further seven breaches had some business associate involvement.
Healthcare Data Breaches by State
The healthcare data breaches reported in February were spread across 22 states. California and Florida were the worst affected states with three breaches apiece. Two breaches were reported in each of Illinois, Kentucky, Maryland, Minnesota, Texas, and Washington, and one breach was reported in each of Arizona, Colorado, Connecticut, Delaware, Georgia, Kansas, Massachusetts, Mississippi, Montana, North Carolina, Virginia, Wisconsin, and West Virginia.
HIPAA Enforcement Actions in February 2019
2018 was a record year for HIPAA enforcement actions, although 2019 has started slowly. The HHS’ Office for Civil Rights has not issued any fines nor agreed any HIPAA settlements so far in 2019.
There were no enforcement actions by state attorneys general over HIPAA violations in February. The only 2019 penalty to date is January’s $935.000 settlement between California and Aetna.
The post February 2019 Healthcare Data Breach Report appeared first on HIPAA Journal.