This post summarizes the largest healthcare data breaches of 2018: Healthcare data breaches that have resulted in the loss, theft, unauthorized accessing, impermissible disclosure, or improper disposal of 100,000 or more healthcare records.
2018 has seen 18 data breaches that have exposed 100,000 or more healthcare records. 8 of those breaches saw more than half a million healthcare records exposed, and three of those breaches exposed more than 1 million healthcare records.
A Bad Year for Healthcare Data Breaches
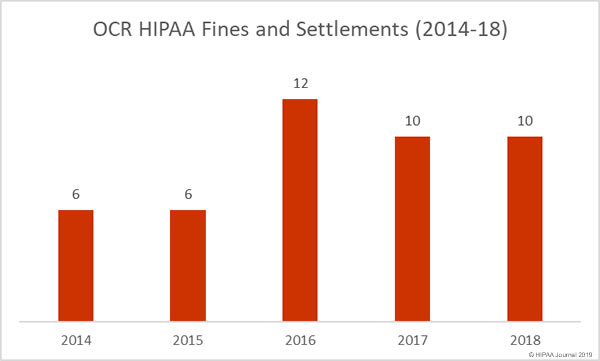
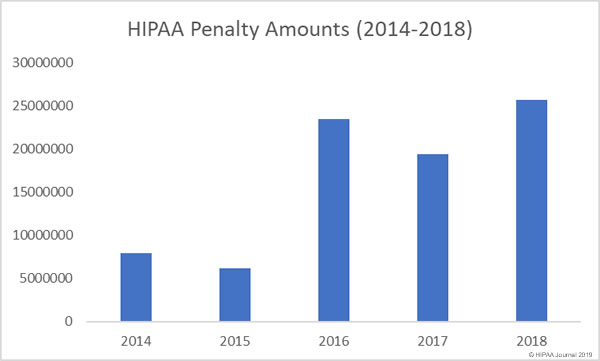
As of December 27, 2018, the Department of Health and Human Services’ Office for Civil Rights (OCR) has received notifications of 351 data breaches of 500 or more healthcare records. Those breaches have resulted in the exposure of 13,020,821 healthcare records.
It is likely that the year will finish on a par with 2017 in terms of the number of reported healthcare data breaches; however, more than twice as many healthcare records have been exposed in 2018 than in 2017.
In 2017, there were 359 data breaches of 500 or more records reported to OCR. Those breaches resulted in the exposure of 5,138,179 healthcare records.
The Largest Healthcare Data Breaches of 2018
Listed below is a summary of the largest healthcare data breaches of 2018. A brief description of those breaches has been listed below.
At the time of writing, OCR is still investigating all but one of the breaches listed below. Only the LifeBridge Health breach investigation has been closed.
| Rank
|
Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| 1 |
AccuDoc Solutions, Inc. |
Business Associate |
2,652,537 |
Hacking/IT Incident |
| 2 |
UnityPoint Health |
Business Associate |
1,421,107 |
Hacking/IT Incident |
| 3 |
Employees Retirement System of Texas |
Health Plan |
1,248,263 |
Unauthorized Access/Disclosure |
| 4 |
CA Department of Developmental Services |
Health Plan |
582,174 |
Theft |
| 5 |
MSK Group |
Healthcare Provider |
566,236 |
Hacking/IT Incident |
| 6 |
CNO Financial Group, Inc. |
Health Plan |
566,217 |
Unauthorized Access/Disclosure |
| 7 |
LifeBridge Health, Inc |
Healthcare Provider |
538,127 |
Hacking/IT Incident |
| 8 |
Health Management Concepts, Inc. |
Business Associate |
502,416 |
Hacking/IT Incident |
| 9 |
AU Medical Center, INC |
Healthcare Provider |
417,000 |
Hacking/IT Incident |
| 10 |
SSM Health St. Mary’s Hospital – Jefferson City |
Healthcare Provider |
301,000 |
Improper Disposal |
| 11 |
Oklahoma State University Center for Health Sciences |
Healthcare Provider |
279,865 |
Hacking/IT Incident |
| 12 |
Med Associates, Inc. |
Business Associate |
276,057 |
Hacking/IT Incident |
| 13 |
Adams County |
Healthcare Provider |
258,120 |
Unauthorized Access/Disclosure |
| 14 |
MedEvolve |
Business Associate |
205,434 |
Unauthorized Access/Disclosure |
| 15 |
HealthEquity, Inc. |
Business Associate |
165,800 |
Hacking/IT Incident |
| 16 |
St. Peter’s Surgery & Endoscopy Center |
Healthcare Provider |
134,512 |
Hacking/IT Incident |
| 17 |
New York Oncology Hematology, P.C. |
Healthcare Provider |
128,400 |
Hacking/IT Incident |
| 18 |
Boys Town National Research Hospital |
Healthcare Provider |
105,309 |
Hacking/IT Incident |
Causes of the Largest Healthcare Data Breaches of 2018
Further information on the causes of the largest healthcare breaches of 2018.
AccuDoc Solutions, Inc.
Morrisville, NC-based AccuDoc Solutions, a billing company that operates the online payment system used by Atrium Health’s network of 44 hospitals in North Carolina, South Carolina and Georgia, discovered that some of its databases had been compromised between September 22 and September 29, 2018. The databases contained the records of 2,652,537 patients. While data could have been viewed, AccuDoc reports that the databases could not be downloaded. Not only was this the largest healthcare data breach of 2018, it was the largest healthcare data breach to be reported since September 2016.
UnityPoint Health
A UnityPoint Health phishing attack was detected on May 31, 2018. The forensic investigation revealed multiple email accounts had been compromised between March 14 and April 3, 2018 as a result of employees being fooled in a business email compromise attack. A trusted executive’s email account was spoofed, and several employees responded to the messages and disclosed their email credentials. The compromised email accounts contained the PHI of 1,421,107 individuals.
Employees Retirement System of Texas
The Employees Retirement System of Texas discovered a flaw in its ERS OnLine portal that allowed certain individuals to view the protected health information of other members after logging into the portal. The breach was attributed to a coding error. Up to 1,248,263 individuals’ PHI was potentially viewed by other health plan members.
CA Department of Developmental Services
The California Department of Developmental Services experienced a break in at its offices. During the time the thieves were in the offices they potentially accessed the sensitive information of approximately 15,000 employees, contractors, job applicants, and parents of minors who receive DDS services, in addition to the PHI of 582,174 patients.
MSK Group
Tennessee-based MSK Group, P.C, a network of orthopedic medical practices, discovered in May 2018 that hackers had gained access to its network. Certain parts of the network had been accessed by the hackers over a period of several months. The records of 566,236 patients, which included personal, health and insurance information, may have been viewed or copied by the hackers.
CNO Financial Group, Inc.
Chicago-based health insurer Bankers Life, a division of CNO Financial Group Inc., discovered hackers gained access to its systems between May 30 and September 13, 2018 and potentially stole the personal information of 566,217 individuals.
LifeBridge Health, Inc
The Baltimore-based healthcare provider LifeBridge Health discovered malware had been installed on a server that hosted the electronic medical record system used by LifeBridge Potomac Professionals and LifeBridge Health’s patient registration and billing systems. Those systems contained the PHI of 538,127 patients.
Health Management Concepts, Inc.
Health Management Concepts discovered hackers gained access to a server used for sharing files and installed ransomware. The ransom demand was paid to unlock the encrypted files; however, HMC reported that the hackers were ‘inadvertently provided’ with a file that contained the PHI of 502,416 individuals. It is suspected that the file was unwittingly sent to the attackers to prove they could decrypt files.
AU Medical Center, INC
An Augusta University Medical Center phishing attack resulted in an unauthorized individual gaining access to the email accounts of two employees. The compromised email accounts contained the PHI of 417,000 patients.
SSM Health St. Mary’s Hospital – Jefferson City
St. Mary’s Hospital moved to new premises and all patients’ medical records were transferred to the new facility; however, on June 1, 2018, the hospital discovered administrative documents containing the protected health information of 301,000 patients had been left behind. In the most part, the breach was limited to names and medical record numbers.
Oklahoma State University Center for Health Sciences
Oklahoma State University Center for Health Sciences discovered an unauthorized individual gained access to parts of its computer network and potentially accessed files containing billing information of Medicaid patients. The breach affected 279,865 patients, although only a limited amount of PHI was accessible.
Med Associates, Inc.
The Latham, NY-based health billing company Med Associates, which provides claims services to more than 70 healthcare providers, discovered an employee’s computer has been accessed by an unauthorized individual. It is possible that the attacker gained access to the PHI of up to 276,057 patients.
Adams County
Adams County, WI, discovered hackers gained access to its network and potentially accessed the PHI and PII of 258,102 individuals. The compromised systems were used by the departments of Health and Human Services, Child Support, Veteran Service Office, Extension Office, Adams County Employees, Solid Waste, and the Sheriff’s Office.
MedEvolve
MedEvolve, a provider of electronic billing and record services to healthcare providers, discovered an FTP server had been left unsecured between March 29, 2018 and May 4, 2018. A file on the FTP server contained the PHI of 205,434 patients of Premier Immediate Medical Care.
HealthEquity, Inc.
HealthEquity, a Utah-based company that provides services to help individuals gain tax advantages to offset the cost of healthcare, experienced a phishing attack that resulted in hackers gaining access to the email accounts of two employees. Those accounts contained the PHI of 165,800 individuals.
St. Peter’s Surgery & Endoscopy Center
St. Peter’s Surgery & Endoscopy Center in New York discovered malware had been installed on one of its servers which potentially allowed hackers to view the PHI of 134,512 patients. The malware was discovered the same day it was installed. The fast detection potentially prevented patients’ data from being viewed or copied.
New York Oncology Hematology, P.C.
A phishing attack on New York Oncology Hematology in Albany, NY, resulted in hackers gaining access to the email accounts of 15 employees. Those accounts contained the PHI of 128,400 current and former patients and employees.
Boys Town National Research Hospital
Boys Town National Research Hospital, an Omaha, NE hospital specializing in pediatric deafness, visual and communication disorders, experienced a phishing attack that allowed hackers to gain access to a single email account. The email account contained the PHI of 105,309 patients.
The post Largest Healthcare Data Breaches of 2018 appeared first on HIPAA Journal.