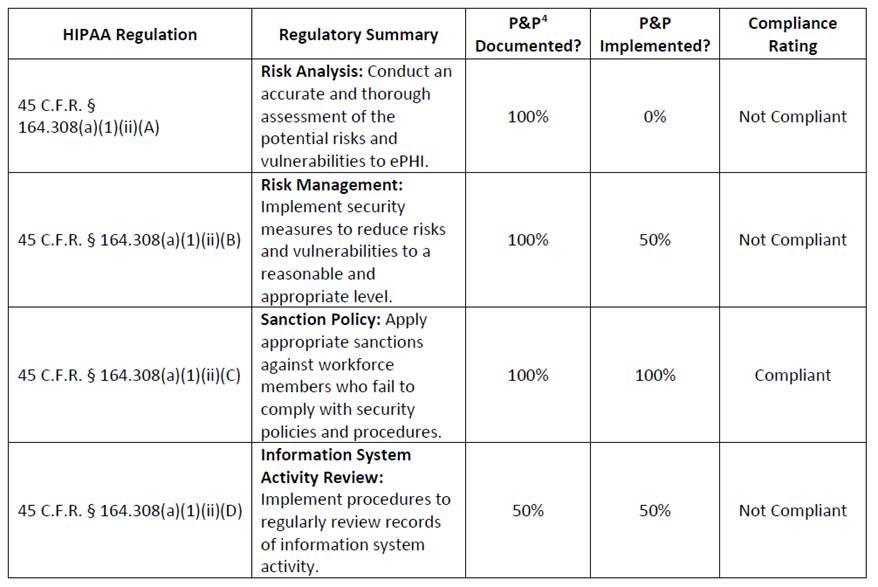
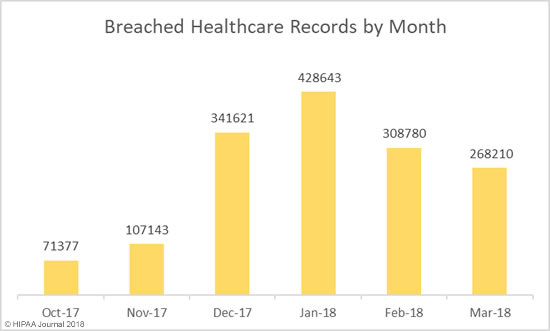
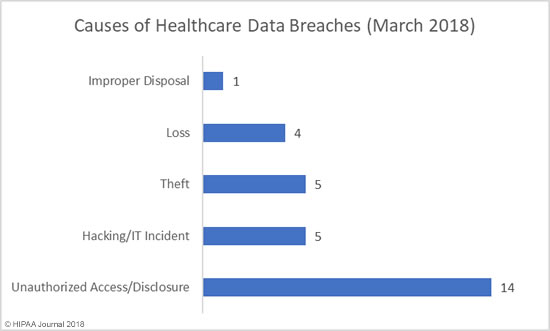
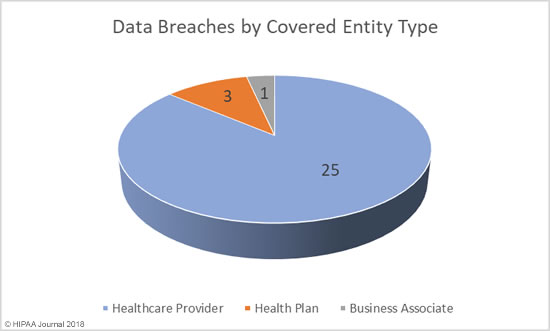
If you discover a HIPAA violation in the workplace, what you should do depends on the nature of the violation, whether or not unsecured PHI has been impermissibly disclosed, and what the potential consequences are.
You suspect there has been a HIPAA violation in the workplace, should you report the violation? If so, how should you report the potential violation and who needs to be told?
Is it Necessary to Report a HIPAA Violation in the Workplace?
If you think you have accidentally violated HIPAA Rules or you believe a work colleague or your employer is failing to comply with the HIPAA Rules, the potential violation(s) should be reported.
Since the publication of the HIPAA Enforcement Rule, HIPAA-covered entities can be financially penalized for HIPAA violations. If an uncorrected HIPAA violation is discovered during an investigation of a complaint, a data breach, or HIPAA audit, HHS’ Office for Civil Rights (OCR) may choose to pursue a financial settlement to resolve the violation. Such actions are far less likely when a violation has been discovered internally and corrected to prevent a recurrence.
If a patient’s privacy has been violated, by reporting the violation internally you will allow your employer to take steps to reduce the potential for further harm and will be helping to ensure that similar incidents do not occur in the future.
Who Should be Notified About a Potential HIPAA Violation?
Healthcare employees who discover a HIPAA violation in the workplace should report the incident to their supervisor or their HIPAA Privacy Officer in the first instance. The HIPAA Privacy Officer will need to be notified of any HIPAA compliance failure as an investigation will need to be conducted, which should include a risk assessment.
The risk assessment will help the Privacy Officer determine whether the violation is a reportable incident. Not all internal violations of HIPAA Rules need to be reported, but the failure to notify the patient and OCR of a reportable breach of unsecured PHI could result in a financial penalty.
Action should also be taken to ensure that the cause of the breach is corrected. That may require updates to policies and procedures and/or further staff training.
There have been cases of employees reporting HIPAA violations internally only for no actions to appear to be taken to address the issue. In such cases, the matter can be escalated and a complaint filed with the HHS’ Office for Civil Rights – the main enforcer of the HIPAA Rules.
How long do you have to report a HIPAA violation?
HIPAA violations should be reported internally immediately. Employees and patients have the option to bypass notifying the Covered Entity and directly file a HIPAA complaint with the Office for Civil Rights (OCR) under the Department of Health and Human Services (HHS) if they believe that a Covered Entity has violated the HIPAA Privacy, Security, or Breach Notification Rules. This is especially applicable in cases of serious violations, potential criminal violations, willful/widespread neglect of HIPAA Rules, or multiple suspected violations. The OCR provides various channels for submitting HIPAA complaints, including their Complaint Page, fax, mail, or email. When filing a complaint, it is important to provide details such as the reason for the complaint, the potential violation, information about the Covered Entity or Business Associate involved, the suspected date and location of the violation, and the date when the complainant became aware of the possible violation. Complaints should generally be submitted within 180 days of discovering the violation, although extensions may be granted with good cause. While anonymous complaints are accepted, it is important to note that OCR requires name and contact information for investigation purposes. All complaints will be reviewed, and investigations will be initiated if there are suspected violations of HIPAA Rules and the complaint is filed within the designated timeframe.
Do HIPAA violations have to be reported?
While HIPAA does not explicitly require individuals or organizations to report every single HIPAA violation they encounter, there are certain circumstances where reporting is mandatory or strongly encouraged. Covered entities, such as healthcare providers, health plans, and healthcare clearinghouses, are required to report breaches of unsecured protected health information (PHI) to the affected individuals, the Department of Health and Human Services (HHS), and in some cases, the media. Additionally, business associates, who are third-party entities that handle PHI on behalf of covered entities, are required to report breaches of PHI to the covered entity. Apart from breach reporting, it is generally recommended that individuals and organizations report HIPAA violations to the appropriate authorities. This helps to ensure compliance with HIPAA regulations, protect patient privacy and security, and prevent further violations. Reporting can be done to the covered entity’s privacy officer or the Office for Civil Rights (OCR) within HHS, which is responsible for enforcing HIPAA. Certain states may have additional reporting requirements or regulations that apply in conjunction with HIPAA. Therefore, it is advisable to consult state-specific laws and regulations to determine the reporting obligations in a particular jurisdiction.
Examples of HIPAA Violations by Employers
| HIPAA Violation |
Description |
| Improper Access to Employee Health Information |
Employers accessing and reviewing the medical records or health information of their employees without a legitimate need or proper authorization. |
| Inadequate Safeguards for Employee Health Information |
Employers failing to implement appropriate security measures to protect the confidentiality and integrity of employee health information, such as storing health records in an insecure location or failing to secure electronic health systems. |
| Unauthorized Disclosure of Employee Health Information |
Employers sharing an employee’s medical condition, treatment details, or other sensitive health information with individuals who are not involved in the employee’s healthcare or have a legitimate reason to access that information. |
| Retaliation against Employees |
Employers retaliating against employees for exercising their rights under HIPAA, such as filing a complaint or reporting a violation. |
| Insufficient Employee Training |
Employers neglecting to provide adequate training and education to employees on HIPAA regulations and the proper handling of employee health information, leading to unintentional violations. |
| Improper Use of Employee Health Information |
Employers using employee health information for purposes unrelated to healthcare, such as making employment decisions based on an employee’s health condition or sharing health information for non-work-related reasons. |
| Lack of Written Policies and Procedures |
Employers failing to establish and maintain written policies and procedures outlining how employee health information should be handled, safeguarded, and disclosed, as required by HIPAA. |
Filing a Complaint with the HHS’ Office for Civil Rights
OCR investigates complaints about potential HIPAA violations, but only if the complainant provides their name and contact details. Complaints can be submitted anonymously, although it is unlikely any further action will be taken. While many employees may be reluctant to provide such information, healthcare organizations are not permitted to take retaliatory action against individuals who report a HIPAA violation in the workplace.
Financial penalties for HIPAA violations are typically only issued when there has been a willful violation of the HIPAA Rules, although penalties are possible for violations that have occurred through negligence or ongoing compliance failures. However, in many cases, HIPAA violations are resolved through voluntary compliance or by OCR providing technical assistance.
FAQs about Reporting a HIPAA Violation in the Workplace
What happens if I am not an employee, but I see a HIPAA violation in the workplace?
If you are not an employee, but you see a HIPAA violation in the workplace, what happens depends on whether you are a member of a covered entity´s or business associate´s workforce (see definition of workforce in §160.103), or if you are a member of the public (i.e., patient, visitor, etc.).
If you are a member of a covered entity´s or business associate´s workforce, you should report the violation to your immediate manager or supervisor. If you feel your report is not acted on, you can escalate it to the organization´s HIPAA Privacy Officer or HHS´ Office for Civil Rights.
If you are a member of the public, you can raise the issue with the organization´s HIPAA Privacy Officer or HHS´ Office for Civil Rights. The contact details of the organization’s Privacy Officer is on the organization´s Notice of Privacy Practices and website, or you can contact HHS´ Office for Civil Rights via any of the methods explained on this link.
When I raised a violation concern with my supervisor, I was told HIPAA did not apply. Can this be true?
If you have raised a violation concern with your supervisor and been told HIPAA does not apply, there could be several reasons for this. HIPAA may not apply due to the nature of the organization’s operations. For example, not all healthcare providers qualify as HIPAA covered entities; and, even when they do, other federal and state laws may preempt HIPAA (i.e., FERPA, Texas HB300, etc.).
HIPAA may not apply because the nature of information disclosed is not covered by HIPAA (not all patient information is “protected”) or because the disclosure is permitted by the HIPAA Rule even though it appears it shouldn’t be – for example, to an employer who needs information about a patient’s illness or injury to comply with OSHA reporting requirements.
Your best course of action is to ask your supervisor why HIPAA doesn´t apply to the suspected violation and use a third party source to confirm the supervisor´s response. It may be the case your supervisor is misinformed about when HIPAA applies, and your violation concern may have to be escalated to the HIPAA Privacy Officer.
Should reporting violations be included in HIPAA training?
The process for reporting violations should be included in HIPAA training when the organization you work for is subject to any of the HIPAA Privacy, Security, or Breach Notification Rules. This not only means covered entities (who are required to provide training on “policies and procedures with respect of PHI”) but also business associates (to whom the Security Rule applies) and vendors of personal health apps who are required to comply with the Breach Notification Rule.
Why doesn´t HHS´ Office for Civil Rights investigate anonymous reports?
HHS´ Office for Civil Rights does not investigate anonymous reports because it could lead to an increase in false reports and unjustified or malicious complaints – stretching the agency’s resources and potentially reducing the amount of technical assistance available for organizations that need it.
Additionally, the Privacy Rule protects genuine complainants from retaliation. Under §160.316, a covered entity or business associate “may not threaten, intimidate, coerce, harass, discriminate against, or take any other retaliatory action against any individual or other person” who:
- Files a complaint or reports a HIPAA violation,
- Assists in an investigation into the complaint/report, or
- Refuses to take an action that would violate HIPAA.
How do I go about reporting a whole team that is not compliant with HIPAA?
Reporting a whole team that is not compliant with HIPAA can be complicated because sometimes teams take short cuts with HIPAA compliance “to get the job done” and when the short cuts are allowed to continue, a “culture of non-compliance” can develop. In such circumstances, it is a good idea to initially report your concerns to a supervisor or escalate them to the Privacy Officer if you have concerns reporting them to a supervisor may affect your standing among your colleagues.
What is a HIPAA violation in the workplace?
A HIPAA violation in the workplace is any failure to comply with the standards and implementation specifications of the HIPAA Administrative Simplification Rules (i.e., the Privacy, Security, and Breach Notification Rules) when the workplace is controlled by an entity subject to the Health Insurance Portability and Accountability Act of 1996.
Entities subject to HIPAA include – but are not limited to – health plans, health care clearinghouses, and most healthcare providers (collectively known as “Covered Entities”), third-party businesses that provide a service for or on behalf of a Covered Entity (collectively known as “Business Associates”), subcontractors of Business Associates, and vendors of some personal health devices.
Is HIPAA violation reporting mandatory in all workplaces?
Whether HIPAA violation reporting is mandatory in all workplaces depends on the policies developed and implemented by the Covered Entity or Business Associate in control of the workplace. Generally, HIPAA violation reporting to an organization’s Privacy Officer is mandatory for certain types of violation, while minor violations that do not result in an impermissible disclosure of PHI or breach of unsecured PHI might be dealt with by a manager or supervisor.
When a HIPAA violation does result in an impermissible disclosure of PHI or a breach of unsecured PHI, Covered Entities and Business Associates are required to report the breach to affected individuals and to HHS´ Office for Civil Rights. Some states also have mandatory HIPAA violation reporting requirements; and, in these states, reports have to be made to the state Attorney General. Additionally. HIPAA requires Business Associates to report all “security events” to the Covered Entity whether they result in an impermissible disclosure/breach of PHI or not.
Are there any examples of HIPAA violations by employers?
There are many examples of HIPAA violations by employers when the word “employer” relates to a Covered Entity or Business Associate and the “employer” has failed to train staff on HIPAA-compliant privacy policies or implement appropriate safeguards to protect the confidentiality, integrity, and availability of electronic PHI. You will find a wide selection on HHS´ Breach Report.
However, when the word “employer” relates to a business in its role as an employer, it is important to be aware that HIPAA does not apply (other than when an employer administers a self-sponsored health plan). Therefore, when an employer maintains health information about employees (for example, in an HR role), Privacy Rule protections do not apply; and, if the health information is disclosed without an employee’s authorization, it is not a violation of HIPAA.
If you believe a privacy violation has taken place, who should you report it to?
If you believe a privacy violation has taken place, you should report it to your organization’s Compliance Officer. If the privacy violation involves an impermissible disclosure of health information, and the organization you work for is covered by the HIPAA Privacy Rule, it is important to make the Compliance Officer aware of this because it is a notifiable breach of PHI.
How long do you have to report a HIPAA violation?
How long you have to report a HIPAA violation depends on the nature of the violation, organizational policies, whether or not the violation involves the impermissible disclosure of PHI or a breach of unsecured PHI, and – if so – the state the violation occurred in.
All Covered Entities (and some Business Associates) are required to develop and implement policies and procedures to comply with the Privacy Rule. The policies and procedures will determine whether a HIPAA violation is reportable and how long a member of the workforce has to report it.
Some organizations may choose to limit which violations are reported to reduce the workload on Privacy Officers. Therefore, an innocuous violation (i.e., the failure to document a patient’s consent to notify family members of their hospitalization) might be dealt with at supervisor level.
If the HIPAA violation involves an impermissible disclosure of PHI or a breach of unsecured PHI, the violation should be reported to the Privacy and/or Security Officer as quickly as possible to mitigate the impact of the violation (regardless of any time limits stipulated in an organizational policy).
Thereafter, the Privacy Officer has 60 days to notify the affected individual(s) and – if a breach affects more than 500 individuals – HHS´ Office for Civil Rights. However, some states have much shorter notification periods; and although many states exempt HIPAA Covered Entities from their Breach Notification laws, they do not always exempt breaches attributable to a Business Associate.
If you witness a HIPAA violation at work, what should you do?
If you witness a HIPAA violation at work, you should report it to your supervisor or manager; or, if this is impractical, to your organization’s Privacy Officer. Many workplaces have implemented anonymous channels of communication for reporting HIPAA violations, and this may save you the embarrassment of being confronted by a work colleague who has been sanctioned for the violation.
How do you report HIPAA violations?
How you report HIPAA violations can depend on whether you are a member of a Covered Entity´s workforce, or a patient or plan member. This is because some Covered Entity´s implement policies stipulating that HIPAA violations in the workplace must be reported by staff members to a specific individual – often the organization’s Privacy Officer.
If such policies apply, you should only contact HHS´ Office for Civil Rights if the Privacy Officer fails to act on the report or you are retaliated against for making a report. HIPAA´s General Administrative Requirements prohibit Covered Entities from intimidation, discrimination, and retaliation if a member of the workforce files a complaint or supports a compliance investigation.
Patients and plan members also have this option, but can – if they wish – report HIPAA violations to their state Attorney General or HHS´ Office for Civil Rights without first reporting a HIPAA violating to the Privacy Officer. Again, the Covered Entity is prohibited from intimidation, discrimination, and retaliation for filing a complaint with HHS´ Office for Civil Rights.
Is there a HIPAA violation reporting reward?
There is no HIPAA violation reporting reward available from HHS´ Office for Civil Rights. However, nothing in the text of HIPAA prevents Covered Entities and Business Associates from implementing a reward system. Indeed, a HIPAA violation reporting reward system could encourage members of the workforce to report HIPAA violations and help support a compliant workforce.
What should you do if you think your policies conflict with HIPAA?
What you should do if you think your policies conflict with HIPAA depends on whether you represent a Covered Entity (i.e., a Privacy Officer) or are a member of a Covered Entity´s workforce. If you represent a Covered Entity, you should seek professional compliance advice and amend your policies to align with HIPAA or any state laws that preempt HIPAA.
If you are a member of a Covered Entity’s workforce, you should raise your concerns with your organization’s Privacy Officer. In such cases, you are not required to comply with organizational policies that conflict with HIPAA (although it may be in your professional best interest to do so), and your employer is not allowed to sanction you for non-compliance with conflicting policies.
Section 45 CFR §160.316 of the General Administrative Requirements states:
“A covered entity may not threaten, intimidate, coerce, harass, discriminate against, or take any other retaliatory action against any individual or other person for […] opposing any act or practice made unlawful by this subchapter, provided the individual has a good faith belief that the practice opposed is unlawful, and the manner of opposition is reasonable and does not involve a disclosure of protected health information in violation of subpart E of part 164 [the Privacy Rule].”
What is a medical assistant’s responsibility if they witness a violation of HIPAA?
A medical assistant’s responsibility if they witness a violation of HIPAA depends on the content of the HIPAA violation reporting policy implemented by their employer. Depending on the nature of the violation, the medical assistant may be required to report the violation of HIPAA to a supervisor or manager, or to their organization´s HIPAA Privacy Officer.
The post What to Do if You Discover a HIPAA Violation in the Workplace appeared first on HIPAA Journal.