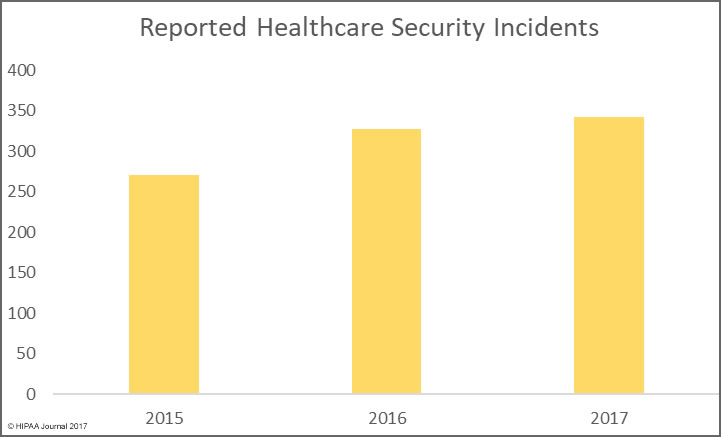
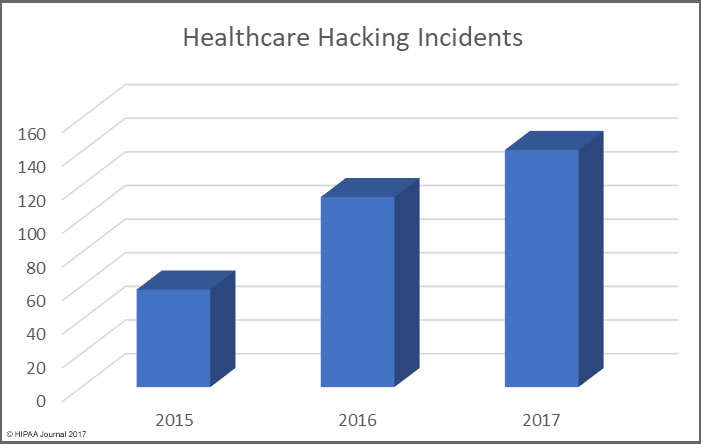
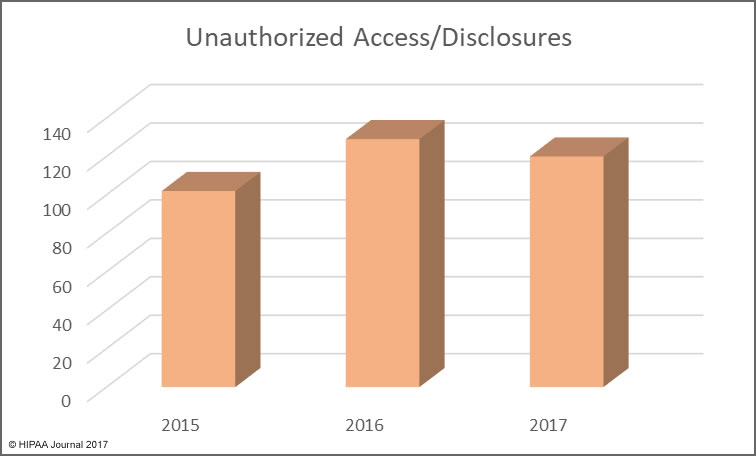
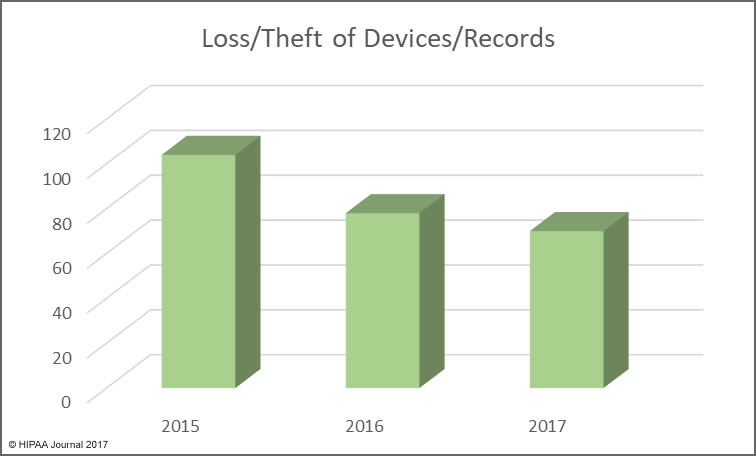
Health, treatment, or payment information, and any identifiers maintained with this information, is considered Protected Health Information under HIPAA if the information is created, received, maintained, or transmitted by a “covered entity” or by a “business associate”.
However, because there are times when a covered entity might not maintain identifying information with health, treatment, or payment information, there is no definitive list of what is considered Protected Health Information under HIPAA.
A lack of understanding about what is considered Protected Health Information under HIPAA is one of the primary reasons for HIPAA-related complaints to HHS´ Office for Civil Rights.
 This is not surprising, as there are times when the same information can be both protected and non-protected depending on how it is maintained.
This is not surprising, as there are times when the same information can be both protected and non-protected depending on how it is maintained.
This article aims to provide you with the full and correct definition of Protected Health Information.
HIPAA rules and regulations are substantially about protecting PHI and we recommend you use our Protected Health Information Checklist to understand what is required for the protection of PHI.
What is Considered Protected Health Information under HIPAA?
To best understand what is considered Protect Health Information under HIPAA it is necessary to review not only the definition of Protected Health Information under HIPAA in 45 CFR §160.103, but also the definitions of “health information”, individually identifiable health information”, and “designated record set”.
This is because, when taking the four HIPAA PHI definitions into account, it is easier to determine what information is protected under HIPAA and when.
Starting with health information, this is defined as any information, including genetic information, whether oral or recorded in any form or medium, that:
- Is created or received by a health care provider, health plan, public health authority, employer, life insurer, school or university, or health care clearinghouse; and
- Relates to the past, present, or future physical or mental health or condition of an individual; the provision of health care to an individual; or the past, present, or future payment for the provision of health care to an individual.
Thereafter, the definition of individually identifiable health information is much the same, other than the definition only applies to health care providers, health plans, employers (in the role of an administrator of a self-insured health plan), and health care clearinghouses, and only relates to information that identifies or could be used to identify the individual who is the subject of the health information or the individual´s family, employer, or members of their household.
 The Protected Health Information definition is similar to that for individually identifiable health information when maintained or transmitted by a Covered Entity other than PHI excludes health information maintained in students´ educational records (as these are protected by the Family Educational Rights and Privacy Act) and health information maintained by a Covered Entity in its role as an employer (i.e., health information relating to an employee´s absence from work).
The Protected Health Information definition is similar to that for individually identifiable health information when maintained or transmitted by a Covered Entity other than PHI excludes health information maintained in students´ educational records (as these are protected by the Family Educational Rights and Privacy Act) and health information maintained by a Covered Entity in its role as an employer (i.e., health information relating to an employee´s absence from work).
It is important to note these HIPAA PHI definitions only apply to health care providers, health plans, and health care clearing houses that qualify as HIPAA Covered Entities, and only to Business Associates while they are performing a service for or on behalf of a Covered Entity. For more information about when the Protected Health Information definition may not apply to a health care provider or health plan, please see “The HIPAA Definition of Covered Entities Explained”.
Compliance Issues Regarding Protected Health Information under HIPAA
HHS´ Office for Civil Rights updates an Enforcement Highlights webpage on which it lists the compliance issues most often alleged in complaints in order of frequency. Because a single data breach can affect many thousands of individuals, it is not surprising to see impermissible uses and disclosures at the top of the list. However, the next four items imply a lack of understanding about what is considered Protected Health Information under HIPAA:
- Impermissible uses and disclosures of PHI
- Lack of safeguards for (non-electronic) PHI
- Failures to provide patient access to PHI
- Lack of Administrative Safeguards for electronic PHI
- Violations of the minimum necessary standard
It is worth noting that, other than mandatory breach notifications, the most likely source of a complaint to HHS´ Office for Civil Rights is a patient. It is not necessarily be the case that Covered Entities, Business Associates, and members of their respective workforces have a lack of understanding about what is considered Protected Health Information under HIPAA, but rather that patients need better educating about what HIPAA Protected Health Information is.
In a perfect world, an explanation of what HIPAA Protected Health Information is would be covered in the Notice of Privacy Practices. However, most Notices of Privacy Practices already contain more information than most patients are prepared to read; and, as will become evident in later sections of this article, explaining what is covered under HIPAA – and what is not – will likely raise more questions than answers for patients wishing to exercise their Privacy Rule rights.
In order to reduce the number of complaints to HHS´ Office for Civil Rights, it is advisable for Covered Entities and Business Associates to ensure all members of the workforce have a thorough understanding of what is considered Protected Health Information under HIPAA – not only to answer patients´ questions, but also to carry out their functions within the Covered Entity or Business Associate in compliance with HIPAA.
Designated Record Sets and What Information is Protected by HIPAA
 The definition of designated record sets appears in the introduction to the Privacy Rule in 45 CFR §164.501. This standard defines designated record sets as “a group of records maintained by or for a Covered Entity that is the medical records and billing records about individuals […] or the enrollment, payment, and claims information maintained by or for a health plan that is used in whole or in part by or for the Covered Entity to make decisions about individuals.”
The definition of designated record sets appears in the introduction to the Privacy Rule in 45 CFR §164.501. This standard defines designated record sets as “a group of records maintained by or for a Covered Entity that is the medical records and billing records about individuals […] or the enrollment, payment, and claims information maintained by or for a health plan that is used in whole or in part by or for the Covered Entity to make decisions about individuals.”
This definition is followed by a footnote that explains a record can be “any item, collection, or grouping of information that includes Protected Health Information and is maintained, collected, used, or disseminated by or for a Covered Entity.” While this may be a little confusing to follow – and likely difficult to make clear to patients unfamiliar with the terminology of HIPAA – an explanation of what information is protected by HIPAA could be explained thus:
- Protected Health Information is health information (i.e., a diagnosis, a test result, an x-ray, etc.) that is maintained in the same record set as individually identifiable information (i.e., a name, an address, a phone number, etc.).
- Any other non-health information included in the same record set assumes the same protections as the health information. However, when non-health information is maintained outside the record set, the protections do not apply.
- A Covered Entity may maintain multiple record sets about an individual (i.e., a patient or plan member), but individuals only have the right to access and request amendments to information maintained in designated record sets.
This explanation of what information is protected by HIPAA can help reduce patients´ misunderstandings about what is considered Protected Health Information under HIPAA and reduce the volume of complaints to HHS´ Office for Civil Rights. It can also accelerate the flow of information within a health care facility when members of the workforce understand that not every piece of information relating to a patient has to be locked down behind access controls.
Examples of Protected Health Information and Why There is No List of Protected Health Information
Many examples of Protected Health Information refer to the PHI identifiers listed under the safe harbor method of de-identification in 45 CFR §164.514. It is now more than twenty years since this Protected Health Information list was compiled and it is very out of date. For example, in many cases Social Security Numbers have been replaced by Medicare Beneficiary Identifiers, social media handles did not exist when the list of PHI identifiers was compiled, and few people had Emotional Support Animals.
Indeed, Emotional Support Animals are a good example of when non-health information can be both protected and non-protected depending on how information is maintained. If information relating to a patient´s Emotional Support Animal is maintained in a record set, it assumes the same protections as the patient´s health information. However, if it is maintained in a separate database that does not contain health information (i.e., to accommodate transport requirements) it is not protected.
It is because of scenarios such as this that there is no list of Protected Health Information. Protected Health Information can be any information relating to an individual that is maintained in the same record set as the individual´s health information. To include non-health information that is not maintained in a record set in a list of Protected Health Information (i.e., license plate numbers, device identifiers, URLs, etc.) is unnecessary and not the objective of the Privacy Rule.
In conclusion, there is no doubt that understanding what is considered Protected Health Information under HIPAA can be complicated; but, by identifying what is Protected Health Information – and what isn´t – and knowing when protections are applied to non-health information – and when they are not – Covered Entities and Business Associates can accelerate the flow of information and reduce the number of unjustified complaints by patients to HSS´ Office for Civil Rights.
FAQs
What does HIPAA protect?
HIPAA protects the privacy of individually identifiable health information via the provisions of the Privacy Rule. However, it is important to be aware that HIPAA provides a “federal floor” of privacy protections. In many locations, states have passed privacy laws with more stringent protections than HIPAA and, in these locations, state law preempts HIPAA.
What information is protected by HIPAA?
The information protected by HIPAA is all health information relating to an individual´s past, present, or future physical or mental health or condition, the provision of health care to the individual; or the past, present, or future payment for the provision of health care to the individual. Any information that can identify – or be used to identify – the subject of the information is also protected by HIPAA when it is maintained in the same designated record set as an individual’s health information.
What is considered HIPAA information?
What is considered HIPAA information is any health information or connected identifier “created or received by a health care provider, health plan, public health authority, employer, life insurer, school or university, or health care clearinghouse”. Many of these organizations are not HIPAA covered entities and not required to comply with HIPAA.
What is considered PHI under HIPAA?
What is considered PHI under HIPAA is any combination of health information and identifiers created, received, maintained, or transmitted by a covered entity. However, although the term combination is used in this definition, PHI can be a single item – for example, a picture of a baby sent to a pediatrician.
When maintained in the same designated record set as information relating to health, treatment, or payment, PHI covered under HIPAA includes any item of information that could be used to identify the subject of the health, treatment, or payment information.
Using this HIPAA definition of PHI, examples of Protected Health Information include an individual’s LGBTQ status, information about their emotional support animal, and contact information for a family member, friend, or support group – if this information could be used to identify the subject of the health, treatment, or payment information.
What is not considered PHI under HIPAA?
There are numerous examples of what is not considered PHI under HIPAA. One of the most common is students´ health information when it is created, received, maintained, or transmitted by a public school or college; for although the school or college may qualify as a partial covered entity, students´ medical records are considered to be part of their educational records under FERPA.
What information can be shared without violating HIPAA?
All information can be shared without violating HIPAA provided it is shared for a permissible use or disclosure or the entity sharing the information has obtained a written authorization from the subject of the information. With regards to written authorizations, it is important to be aware that individuals have the right to revoke their authorizations at any time.
What is not included in PHI?
What is not included in PHI depends on where information is maintained. PHI is any combination of health information and identifiers when they are maintained in the same designated record set. However, when health information and individual identifiers are maintained separately from each other, the identifiers alone are not considered protected health information under HIPAA. For example, jdoe@yahoo.com, Stillwater MN, and auto registration AYP 197 are not included in PHI when they are not maintained with health information in the same designated record set.
What is the difference between PII, PHI, and IIHA?
The difference between PII, PHI, and IIHA is that PII is Personally Identifiable Information used outside a healthcare context, while PHI (Protected Health Information) and IIHA (Individually Identifiable Health Information) is the same information used within a healthcare context. Although PHI is the more commonly used acronym in HIPAA, both PHI and IIHI are protected by the Privacy and Security Rules because they mean exactly the same thing.
Would patient information such as “Mr. Brown from New York” be considered PHI?
Patient information such as “Mr. Brown from New York” could be considered PHI if the information is maintained in a designated record set with either Mr. Brown´s health information or the health information of a family member, employee, or close personal friend.
Are email addresses that don´t reveal a person’s name considered identifiers for PHI purposes?
Email addresses that don’t reveal a person’s name are considered identifiers for PHI purposes if the email address is maintained in the same designated record set as an individual’s health information. This is because it is quite simple to find out who an email address such as “anonymous@xyz.com“ belongs to by doing a little research on social media or using a reverse email lookup tool on the Internet. Even if social media or a reverse lookup tool does not give you the individual´s name, you will still be able to find enough information about the individual for the email address – when maintained with health information – to be considered PHI.
What is the difference between an allowable disclosure of PHI and an incidental disclosure?
The difference between an allowable disclosure of PHI and an incidental disclosure is that covered entities are allowed to disclose PHI for treatment, payment, and health care operations. An incidental disclosure is a secondary, accidental disclosure that cannot reasonably be prevented, is limited in nature, and that occurs as a result of another disclosure permitted by the Privacy Rule – for example, if a physician invites a health plan employee to his office to discuss payments, and the health plan employee passes a patient he or she recognizes in the waiting room.
How do you determine what a reasonably anticipated threat to PHI is?
You determine what a reasonably anticipated threat to PHI is by conducting frequent risk analyses in order to identify threats to the integrity of PHI. If the threats could be reasonably anticipated, covered entities and business associates are required to implement measures to protect against the threats occurring, or mitigate the consequences if the threats occur.
What information does HIPAA protect?
The information HIPAA protects is all individually identifiable health information that relates to an individual´s past, present, or future medical condition, treatment for medical conditions, and payment for treatments. As well as medical, treatment, and payment information, any information maintained in the same designated record set as the individually identifiable health information that could be used to identify the individual is also protected.
Who can access information under HIPAA?
The answer to the question of who can access information under HIPAA has three parts. 1. The subject of the information and representatives of HHS´ Office of Civil Rights must have access to information when requested. 2. Authorized personnel and certain organizations can have access to information under HIPAA if it involves a permissible use or disclosure as defined by the Privacy Rule. 3. All other requests for access to information under HIPAA must be accompanied by a written authorization from the patient.
Is gender a HIPAA identifier?
Gender is a HIPAA identifier if the information could be used to identify the subject of health information maintained or transmitted by a Covered Entity – or by a Business Associate acting on a Covered Entity´s behalf. The gender of an individual – and their LGBTQ status – is always Protected Health Information when it is maintained or transmitted in the same designated record set as an individual’s health information.
What health information is protected by federal law?
What health information is protected by federal law depends on the federal law and whether it is preempted by state law. For example, HIPAA laws protect health information relating to an individual’s past, present, or future physical or mental health condition, treatment for the condition, and payment for treatment.
However other federal laws exist that also protect health information in certain circumstances. For example, the amended Confidentiality of Alcohol and Drug Abuse Patient Records Regulations protect the confidentiality of substance use disorder patient records and is enforced by the Substance Abuse and Mental Health Services Administration (an agency within HHS).
Under the Public Health Service Act, any health information provided to a family planning agency is protected even if the family planning agency is not a HIPAA Covered Entity. Similarly, any health information provided to any federal government agency is protected by the Privacy Act, while any health information maintained about a student by a school is protected by FERPA.
With regards to state law, Illinois is one of many states that has introduced regulations that preempt HIPAA in specific areas. In this case, Illinois’ Biometric Information Privacy Act regulates the collection, use, and handling of biometric identifiers and information by private companies. Texas has similar regulations included in its Medical Records Privacy Act.
What is considered HIPAA information?
The term HIPAA information can relate to any standard in the text of the Health Insurance Portability and Accountability Act inasmuch as the term could mean information about a pre-existing condition for insurance purposes, information contained in a Medicare claims transaction, or the right to withhold information from an insurance provider when treatment has been paid for privately.
What is HIPAA protected information?
HIPAA protected information is most often considered to be the contents of a designated record set – i.e., both the health information in the designated record set and any non-health information that identifies or could be used to identify the subject of the health information. This description can also include any data relating to a family member, friend, or employer that could identify the individual.
How should you explain the definition of PHI under HIPAA to a patient?
To explain the definition of PHI under HIPAA to a patient, it is a good idea to create a web page with a full explanation of what is protected under HIPAA and under what circumstances it is protected. A link to the web page could be included in the Notice of Privacy Practices with a note asking patients to review the web page prior to making a complaint.
When is the disclosure of HIPAA data a HIPAA violation?
Any disclosure of HIPAA data is a HIPAA violation if it is permitted by the Privacy Rule or authorized by the individual to whom the data relates. A HIPAA violation of this nature is usually considered to be a data breach; and, depending on the consequences of the violation, may have to be reported to HHS´ Office for Civil Rights and the affected individual(s).
The post What is Considered Protected Health Information Under HIPAA? appeared first on HIPAA Journal.
 This is not surprising, as there are times when the same information can be both protected and non-protected depending on how it is maintained.
This is not surprising, as there are times when the same information can be both protected and non-protected depending on how it is maintained. The Protected Health Information definition is similar to that for individually identifiable health information when maintained or transmitted by a Covered Entity other than PHI excludes health information maintained in students´ educational records (as these are protected by the Family Educational Rights and Privacy Act) and health information maintained by a Covered Entity in its role as an employer (i.e., health information relating to an employee´s absence from work).
The Protected Health Information definition is similar to that for individually identifiable health information when maintained or transmitted by a Covered Entity other than PHI excludes health information maintained in students´ educational records (as these are protected by the Family Educational Rights and Privacy Act) and health information maintained by a Covered Entity in its role as an employer (i.e., health information relating to an employee´s absence from work). The definition of designated record sets appears in the introduction to the Privacy Rule in
The definition of designated record sets appears in the introduction to the Privacy Rule in