HIPAA violations most often occur when covered entities, business associates, or members of either’s workforces fail to comply with the Privacy, Security, or Breach Notification Rules. There are many different types of HIPAA violations, and the ten most common HIPAA violations that have resulted in financial penalties are:
- Snooping on Healthcare Records
- Failure to Perform an Organization-Wide Risk Analysis
- Failure to Manage Security Risks / Lack of a Risk Management Process
- Denying Patients’ Access to Health Records/Exceeding Timescale for Providing Access
- Failure to Enter into a HIPAA-Compliant Business Associate Agreement
- Insufficient ePHI Access Controls
- Failure to Use Encryption or an Equivalent Measure to Safeguard ePHI on Portable Devices
- Exceeding the 60-Day Deadline for Issuing Breach Notifications
- Impermissible Disclosures of Protected Health Information
- Improper Disposal of PHI
In this article we outline how you can avoid these common HIPAA violations.
You can also use the article in conjunction with our free HIPAA Violations Checklist to understand what is required to ensure full compliance. Use any form on this page to arrange for your copy of the checklist.
What are the 10 Most Common HIPAA Violations?
Listed below are 10 of the most common HIPAA violations, together with examples of HIPAA-covered entities and business associates that have been discovered to be in violation of HIPAA Rules.
These example cases have had to settle those violations with the Department of Health and Human Services’ Office for Civil Rights (OCR) and state attorneys general. In many cases, investigations have uncovered multiple HIPAA violations.
The settlements pursued by OCR are for egregious violations of HIPAA Rules. Settlements are also pursued to highlight common HIPAA violations to raise awareness of the need to comply with specific aspects of HIPAA Rules.
The settlement amounts reflect the seriousness of the violation, the length of time the violation has been allowed to persist, the number of violations identified, and the financial position of the covered entity/business associate.
1. Snooping on Healthcare Records
 Accessing the health records of patients for reasons other than those permitted by the Privacy Rule is a violation of patient privacy. Snooping on healthcare records of family, friends, neighbors, co-workers, and celebrities is one of the most common HIPAA violations committed by employees. When discovered, these violations can result in termination of employment but could also result in criminal charges for the employee concerned. Financial penalties for healthcare organizations that have failed to prevent snooping are relatively uncommon, but they are possible – as the University of California Los Angeles Health System discovered.
Accessing the health records of patients for reasons other than those permitted by the Privacy Rule is a violation of patient privacy. Snooping on healthcare records of family, friends, neighbors, co-workers, and celebrities is one of the most common HIPAA violations committed by employees. When discovered, these violations can result in termination of employment but could also result in criminal charges for the employee concerned. Financial penalties for healthcare organizations that have failed to prevent snooping are relatively uncommon, but they are possible – as the University of California Los Angeles Health System discovered.
University of California Los Angeles Health System was fined $865,000 for failing to restrict access to medical records. The healthcare provider was investigated following the discovery that a physician had accessed the medical records of celebrities and other patients without authorization. Dr. Huping Zhou accessed the records of patients without authorization 323 times after learning that he would soon be dismissed. Dr. Zhou became the first healthcare employee to be jailed for a HIPAA violation and was sentenced to four months in federal prison.
2. Failure to Perform an Organization-Wide Risk Analysis
The failure to perform an organization-wide risk analysis is one of the most common HIPAA violations to result in a financial penalty. If the risk analysis is not performed regularly, organizations will not be able to determine whether any vulnerabilities to the confidentiality, integrity, and availability of PHI exist. Risks are likely to remain unaddressed, leaving the door wide open for violations to occur.
HIPAA settlements with covered entities for the failure to conduct an organization-wide risk assessment include:
- Premera Blue Cross– $6,850,000 settlement for risk analysis and risk management failures, and other potential HIPAA violations
- Excellus Health Plan – $5,100,000 settlement for risk analysis and risk management failures, and other potential HIPAA violations
- Oregon Health & Science University– $2.7 million settlement for the lack of an enterprise-wide risk analysis.
- Cardionet – $2.5 million settlement for an incomplete risk analysis and lack of risk management processes.
- Cancer Care Group – $750,000 settlement for the failure to conduct an enterprise-wide risk analysis.
- Lahey Hospital and Medical Center – $850,000 settlement for the failure to conduct an organization-wide risk assessment and other HIPAA violations.
- Steven A. Porter, M.D – $100,000 penalty for risk analysis and risk management failures.
- iHealth Solutions (dba Advantum Health) – $75,000 penalty for the failure to conduct an accurate and thorough risk analysis.
3. Failure to Manage Security Risks / Lack of a Risk Management Process
 Performing a risk analysis is essential, but it is not just a checkbox item for compliance. Risks that are identified must then be subjected to a risk management process. They should be prioritized and addressed in a reasonable time frame. Knowing about risks to PHI and failing to address them is one of the most common HIPAA violations penalized by the Office for Civil Rights.
Performing a risk analysis is essential, but it is not just a checkbox item for compliance. Risks that are identified must then be subjected to a risk management process. They should be prioritized and addressed in a reasonable time frame. Knowing about risks to PHI and failing to address them is one of the most common HIPAA violations penalized by the Office for Civil Rights.
HIPAA settlements with covered entities for the failure to manage identified risks include:
4. Denying Patients Access to Health Records/Exceeding Timescale for Providing Access
The HIPAA Privacy Rule gives patients the right to access their medical records and obtain copies on request. This allows patients to check their records for errors and share them with other entities and individuals. Denying patients access to health records, overcharging for copies, or failing to provide records within 30 days is a violation of HIPAA. OCR made HIPAA Right of Access violations one of its key enforcement objectives in late 2019.
HIPAA settlements with covered entities for denying patients access to their records or unnecessary delays in providing access include:
- Great Expressions Dental Center of Georgia, P.C. – $80,000 penalty for excessive charges for a copy of PHI and delay in providing records.
- Cignet Health of Prince George’s County – $4,300,000 penalty for denying patients access to their medical records.
- Banner Health – $200,000 penalty for the delayed response to a patient’s request for a copy of their medical records.
- Dignity Health, dba St. Joseph’s Hospital and Medical Center – $160,000 penalty for a delayed response to a patient’s request for a copy of their medical records.
- NY Spine – $100,000 penalty for the delayed response to a patient’s request for a copy of their medical records.
- Beth Israel Lahey Health Behavioral Services – $70,000 penalty for the delayed response to a patient’s request for a copy of their medical records.
- University of Cincinnati Medical Center – $65,000 penalty for the delayed response to a patient’s request for a copy of their medical records.
- Housing Works Inc – $38,000 penalty for the delayed response to a patient’s request for a copy of their medical records.
- Peter Wrobel, M.D., P.C., dba Elite Primary Care – $36,000 penalty for a delayed response to a patient’s request for a copy of their medical records.
- Riverside Psychiatric Medical Group – $25,000 penalty for a delayed response to a patient’s request for a copy of their medical records.
- Dr. Rajendra Bhayani – $15,000 penalty for the delayed response to a patient’s request for a copy of their medical records.
- All Inclusive Medical Services Inc – $15,000 penalty for the delayed response to a patient’s request for a copy of their medical records.
- Wise Psychiatry, PC – $10,000 penalty for the delayed response to a patient’s request for a copy of their medical records.
- King MD – $3,500 penalty for the delayed response to a patient’s request for a copy of their medical records.
- OCR Announces 11 Enforcement Actions – One CMP and 10 settlements were announced by OCR in July 2021 to resolve Right of Access violations.
5. Failure to Enter into a HIPAA-Compliant Business Associate Agreement
The failure to enter into a HIPAA-compliant business associate agreement with all vendors that are provided with or given access to PHI is another of the most common HIPAA violations. Even when business associate agreements are held for all vendors, they may not be HIPAA compliant, especially if they have not been revised after the Omnibus Final Rule.
Notable settlements for these common HIPAA violations include:
6. Insufficient ePHI Access Controls
The HIPAA Security Rule requires covered entities and their business associates to limit access to ePHI to authorized individuals. The failure to implement appropriate ePHI access controls is also one of the most common HIPAA violations and one that has attracted several financial penalties.
Financial penalties issued to covered entities for ePHI access control failures include:
- Anthem Inc. – $16,000,000 penalty for access control failures and other serious HIPAA violations.
- Memorial Healthcare System – $5,500,000 penalty for insufficient ePHI access controls.
- Texas Department of Aging and Disability Services – $1,600,000 penalty for risk analysis failures, access control failures, and information system monitoring failures.
- University of California Los Angeles Health System – $865,500 penalty for the failure to restrict access to medical records.
- Pagosa Springs Medical Center – $111,400 penalty for the failure to terminate access to ePHI after an employee termination and a lack of a business associate agreement.
7. Failure to Use Encryption or an Equivalent Measure to Safeguard ePHI on Portable Devices
One of the most effective methods of preventing data breaches is to encrypt PHI. Breaches of encrypted PHI are not reportable security incidents unless the key to decrypt data is also accessed. Encryption is not mandatory under HIPAA Rules, but it cannot be ignored. If the decision is taken not to use encryption, an alternative, equivalent security measure must be used in its place.
Recent settlements for the failure to safeguard PHI include:
8. Exceeding the 60-Day Deadline for Issuing Breach Notifications
The HIPAA Breach Notification Rule requires covered entities to issue notifications of breaches without unnecessary delay, and certainly no later than 60 days following the discovery of a data breach. Exceeding that time frame is one of the most common HIPAA violations, which has seen several recent penalties issued:
9. Impermissible Disclosures of Protected Health Information
Any disclosure of protected health information that is not permitted under the HIPAA Privacy Rule can attract a financial penalty. This violation category includes disclosing PHI to a patient’s employer for a purpose not permitted by the Privacy Rule, potential disclosures following the theft or loss of unencrypted laptop computers, careless handling of PHI, disclosing PHI unnecessarily, not adhering to the ‘minimum necessary’ standard, and disclosures of PHI after patient authorizations have expired.
Settlements for impermissible disclosures of PHI include:
- Dr. U. Phillip Igbinadolor, D.M.D. & Associates, P.A. – $50,000 civil monetary penalty for impermissible disclosures of PHI on social media websites
- Northcutt Dental-Fairhope – $62,500 settlement for unauthorized use of PHI for marketing, an insufficient notice of privacy practices, and no HIPAA Privacy Officer
- New Vision Dental – $23,000 settlement for disclosing PHI in responses to patient reviews on the Yelp review platform
- Memorial Hermann Health System – $2.4 million settlement for disclosing a patient’s PHI in a press release.
- New York Presbyterian Hospital – $2,200,000 penalty for filming patients without consent.
- Massachusetts General Hospital– $515,000 penalty for filming patients without consent.
- Luke’s-Roosevelt Hospital Center – $387,000 settlement for careless handling of PHI/Disclosure of a patient’s HIV status to their employer.
- Brigham and Women’s Hospital– $384,000 penalty for filming patients without consent.
- Boston Medical Center – $100,000 penalty for filming patients without consent.
10. Improper Disposal of PHI
When physical PHI and ePHI are no longer required and retention periods have expired, HIPAA Rules require the information to be securely and permanently destroyed. For paper records this could involve shredding or pulping and for ePHI, degaussing, securely wiping, or destroying the electronic devices on which the ePHI is stored to prevent impermissible disclosures.
Financial penalties issued to covered entities for improper disposal of PHI/ePHI include:
Non-Financial HIPAA Violation Examples
HIPAA violations do not always result in financial penalties. Many violations of HIPAA investigated by OCR are resolved by guidance, technical assistance, and/or a corrective action plan depending on the nature of the violation and the harm caused, the covered entity’s previous history of violations, and their willingness to cooperate with an OCR investigation.
Because violations resolved by guidance, technical assistance, and/or a corrective action plan rarely attract headlines, some of the work done by OCR to promote compliance with HIPAA can be overlooked. However, as of March 2022, OCR has investigated and resolved 29,478 cases without issuing a financial penalty. Non-financial HIPAA violation examples include:
- A hospital was required to implement new minimum necessary policies for telephone messages after an employee left a telephone message with the daughter of a patient that detailed both her medical condition and treatment plan.
- A mental health center was required to correct its process for providing Notices of Privacy Practices prior to an intake assessment after the center failed to provide the father of a minor patient with an NPP prior to a mental health evaluation.
- A covered entity was required to withdraw a $100 “records review fee” charged to a patient for providing the patient with copies of his medical records. Under the Privacy Rule, covered entities are only allowed to charge a reasonable cost-based fee.
- A private practice was required to implement policies on the verbal communication of PHI after a staff member discussed HIV testing procedures with a patient in the practice´s waiting room – thereby disclosing PHI to others in the waiting room.
- A radiology practice was required to revise its processes for workers´ compensation disclosures after a patient´s imaging tests were sent to the patient´s employer to support a claim for which the employer´s program was not responsible for payment.
- A health plan was required to correct a flaw in its computer system, review transactions for a six-month period, and correct corrupted patient information after PHI was included in an explanation of benefits letter mailed to an unauthorized family member.
Examples of HIPAA Violations by Healthcare Employees
Snooping on healthcare records is a fairly obvious HIPAA violation and one that all healthcare employees who have received HIPAA training should know is a violation of their employer’s policies and HIPAA Rules.
Other examples of HIPAA violations often come about as a result of misunderstandings about HIPAA requirements. While each of these common HIPAA violations affect far fewer numbers of patients than the above violations, they can still cause a significant amount of harm to the patient(s) involved and their employer. They can also result in disciplinary action against the employee responsible – including termination.
Listed below are some of the common HIPAA violations committed by healthcare employees. These common HIPAA violations should be covered as part of the HIPAA training given to employees to raise awareness of these frequent areas of noncompliance.
Emailing ePHI to Personal Email Accounts and Removing PHI from a Healthcare Facility
It can be difficult to find the time to complete all the necessary tasks within working hours and it can be tempting to take work home to complete. Removing protected health information from a healthcare facility places that information at risk of exposure. This is a common employee HIPAA violation and may even be routine practice at a healthcare facility that is understaffed. That does not mean it is an acceptable practice.
The same applies to emailing ePHI to personal email accounts. Regardless of the intentions, whether it is to get help with spreadsheets, complete work at home to get ahead for the next day, or to catch up on a backlog, it is a violation of HIPAA Rules. Further, any emailing of ePHI to a personal email account could be considered theft – the repercussions of which could be far more severe than the termination of an employment contract.
Leaving Portable Electronic Devices and Paperwork Unattended
The HIPAA Security Rule requires PHI and ePHI to be secured at all times. If paperwork is left unattended it could be viewed by an unauthorized individual, be that a member of staff, patient, or visitor to the healthcare facility. Were that to happen it would be considered an impermissible disclosure of PHI.
Electronic devices that contain ePHI must similarly be secured at all times. Electronic devices are portable and valuable. Opportunistic thieves could easily steal an unattended device and gain access to ePHI. There have been many cases of healthcare employees removing unencrypted devices from healthcare facilities, only for them to be stolen from vehicles or homes. Theft can also easily occur within a healthcare facility if devices are not secured. Healthcare employees must ensure that their employer’s policies are followed, and HIPAA Rules are not violated by leaving devices and paperwork unattended.
Releasing Patient Information to an Unauthorized Individual
An authorization form must be obtained from a patient before any of their PHI can be disclosed to a third party for a purpose other than one expressly permitted by the HIPAA Privacy Rule. Disclosing PHI for purposes other than treatment, payment for healthcare, or healthcare operations (and limited other cases) is a HIPAA violation if authorization has not been received from the patient in advance.
Healthcare employees must ensure that, prior to disclosing PHI to a third party, authorization has been obtained from the patient, and information is not disclosed to any individual or company not included on the authorization form. Authorization forms are only valid if they have been signed by the patient or their nominated representative.
Releasing Patient Information Without Authorization
In a similar vein to the previous point, healthcare employees must also exercise caution about the types of information that are released to third parties, even if an authorization form has been received allowing a specific individual, company, or organization to receive PHI.
The authorization form should include what types of information have been authorized to be released. Any information not detailed on the authorization form must remain private and confidential and should not be shared. The disclosure of additional information would violate the HIPAA Privacy Rule.
Disclosures of PHI to Third Parties After the Expiry of an Authorization
All HIPAA authorization forms must include the names or classes of individuals who are being authorized to receive PHI, the types of PHI that will be disclosed, and the reasons for the disclosures. They must also include an expiry date for the authorization.
PHI must not be disclosed to any individual listed on the authorization form after the expiry date has passed, even if authorization has previously been given to that entity to receive PHI. A new authorization form is required before any further disclosure takes place. It should also be noted that an authorization form without an expiry date is not HIPAA compliant.
Impermissible Disclosures of Patient Health Records
The HIPAA Privacy Rule permits patients to obtain a copy of their health records on request or have their records provided to a nominated third party such as a personal representative or other individual. If not collected in person by the patient, the third party must have been given authorization by the patient – on a HIPAA authorization form – to receive the records before they can be released.
Prior to providing copies of patient health records, healthcare employees must verify the identity of the patient or the person collecting the records and must ensure records are only released to an individual authorized to receive them. Care must also be taken to ensure that the correct patient records are released.
Downloading PHI onto Unauthorized Devices
It can be difficult for healthcare IT departments to keep track of all devices that connect to the network, given how many different devices have network access. Ensuring those devices are secured can be an even bigger problem, yet this is a requirement for HIPAA compliance.
Employees need to be aware that there are privacy and security risks associated with downloading ePHI to unauthorized portable electronic devices. Not only does this increase the risk of the accidental disclosure of ePHI – in the event that the device is lost or stolen – it could also be viewed as theft and a HIPAA violation.
Providing Unauthorized Access to Medical Records
It is the responsibility of the covered entity to ensure that access to patient health information and medical records is only given to authorized individuals. This is achieved by implementing access controls via unique logins.
Employees have a responsibility to ensure that they do not give access to health information to co-workers who may not have the same access rights. The sharing of login credentials could not only result in an impermissible disclosure of ePHI but any actions taken by that employee would also be attributed to the individual whose login credentials were used to gain access.
Actual Examples of HIPAA Violations by Employees
There are not very many examples of HIPAA violations by employees because most are dealt with internally according to the organization´s sanction policy. However, in a few cases, employees´ contracts are terminated and examples of HIPAA violations by employees are brought to the attention of the outside world. The following is a small selection of those we have reported on:
In May 2013, Dianna Hereford was terminated from her position as a staff nurse at the Norton Audubon Hospital for improperly disclosing the condition of a patient with Hepatitis C. Hereford claimed she was wrongfully dismissed for an incidental disclosure; but her claim was dismissed by Jefferson Circuit Court and by Kentucky´s Court of Appeals when she appealed the decision.
In March 2017, an employee of New Jersey-based BioReference Laboratories was terminated from their position for failing to securely dispose of documents containing the PHI of 1,772 patients. Rather than following the company´s policy for disposing of PHI, which involved shredding the documents before disposing of them, the employee threw the documents into a dumpster.
Also in 2017, an employee of Lowell General Hospital in Massachusetts was fired for snooping on the healthcare records of 769 patients. As mentioned above, snooping on healthcare records is one of the most common HIPAA violations; but whereas it normally impacts patients who are known to the employee, this was an extreme example of a HIPAA violation by an employee.
Uncommon HIPAA Violations
The common HIPAA violations described above are frequently cited in OCR’s enforcement actions and are common root causes of data breaches; however, there are many types of HIPAA violations. The violations listed below are less common, and in some cases, harder to detect, and do not get reported so frequently.
|
Uncommon HIPAA Violations
|
Description
|
|
Filming Patients without Consent
|
Filming patients without their consent is a HIPAA violation if it results in the unauthorized disclosure of protected health information, compromising patient privacy and failing to adhere to HIPAA’s requirements for patient consent and privacy protection.
New York Presbyterian Hospital – $2,200,000 penalty for filming patients without consent.
Massachusetts General Hospital– $515,000 penalty for filming patients without consent.
Brigham and Women’s Hospital– $384,000 penalty for filming patients without consent.
Boston Medical Center – $100,000 penalty for filming patients without consent.
|
|
Impermissible Data Sharing During Medical Research
|
Inadequate protection of patient data during collaborative medical research, potentially exposing sensitive information. Researchers must ensure that data sharing adheres to strict privacy safeguards and obtain proper patient consent, when required, to avoid HIPAA violations. Effective safeguards are essential when conducting research that involves patient data that has not been de-identified to prevent unintended exposure.
Huntington Medical Research Institutes Discovers Two HIPAA Breaches
Hospital Researchers Jailed for Stealing and Selling Research Data to China
|
|
Non-Secure File Sharing
|
Sharing patient records through non-secure methods such as personal email accounts or unencrypted file-sharing services is a HIPAA violation. This can occur if proper policies and procedures are not in place and is often the result of insufficient training. Using secure (encrypted) communications tools is necessary to prevent these breaches, and there must be a business associate agreement in place with the provider of a communication platform.
11K Dental Patients’ PHI Uploaded to File Sharing Website
|
|
Exposure of Patient Data in Home-Based Care
|
Lack of adequate data security measures in home-based healthcare settings can lead to unauthorized access to patient records in private residences. Ensuring patient data privacy is essential, even in non-traditional care settings. Secure practices must be used for accessing and transmitting patient information.
Data Issue Arises From Home Diabetes Test
|
|
Data Exposure when Working from Home
|
Exposure of patient data to unauthorized individuals when working from home. When taking paperwork home or working on portable devices, PHI must be protected. While family members and other individuals in the same household may be trusted, they are not authorized to view any patient data. Care must be taken not to leave devices or paperwork unattended with patient data visible.
Potential PHI Disclosure After Employee Works from Home with Hospital Data
|
|
Medical Records Sent to Incorrect Patients
|
Sending medical records to incorrect patients is a HIPAA violation as it constitutes an unauthorized disclosure of protected health information (PHI), compromising patient privacy and failing to safeguard their confidential medical information.
Mailing Error Affects 19,570 Missouri Care Members
|
|
Mailing Correspondence with PHI Visible
|
When PHI is visible on the outside of an envelope or package, it can be easily seen by unauthorized individuals who handle or come into contact with the mail, leading to an unauthorized disclosure of sensitive health information. Patients have the right to expect that their health information will be kept private. Mailing correspondence with visible PHI breaches patient privacy and can cause distress and concern for patients who discover that their sensitive information is exposed. HIPAA mandates that appropriate safeguards, such as physical and administrative safeguards, be in place to protect PHI from unauthorized access or disclosure. Mailing correspondence with visible PHI demonstrates a lack of these safeguards.
Amida Care Mailing Potentially Revealed HIV Status of its Members
Third-Party Mailing Error Sees Aetna Plan Members’ HIV Status Disclosed
|
|
Unauthorized Photographs/Sharing of Photographs
|
Taking photographs of patients without authorization and unauthorized sharing of images is a HIPAA violation. It is not permitted to share photographs of patients with unauthorized individuals, even with other healthcare professionals if the file is shared for reasons other than for treatment, payment, or healthcare operations purposes.
Hospital Staff Shared Photographs of Patient’s Genital Injury
Scrub Nurse Fired for Photographing Employee-Patient’s Genitals
|
|
Workplace Sabotage
|
Deliberate sabotage of healthcare systems, data alteration, or introduction of malware by disgruntled employees is a HIPAA violation. Robust security measures must be implemented, employees should be monitored, and access to data and systems should be promptly revoked when employees are terminated or otherwise leave employment.
Former IT Consultant Charged with Intentionally Causing Damage to Healthcare Company’s Server
|
|
Providing Family Members, Friends, and Partners with Access to PHI
|
Allowing family members, friends, and partners to access a patient’s medical records without proper authorization or accessing records on their behalf and disclosing PHI. Individuals requesting access to patient data must be authorized to access that information, and PHI may only be disclosed to individuals authorized to receive it. Employees must be made aware of their responsibilities under HIPAA.
Criminal HIPAA Violation Case Sees Healthcare Worker Arraigned on 430 Counts
$853,000 Awarded to Patient Whose PHI Was Impermissibly Disclosed to Former Boyfriend
|
|
Data Exposure During Telehealth Visits
|
Inadequate protection of patient data when conducting telehealth visits. While OCR issued a Notice of Enforcement Discretion covering the good faith provision of telehealth services during the pandemic and allowed non-public-facing communication tools for telehealth, the period of enforcement discretion is over. Only HIPAA-compliant communications tools can be used, that encrypt or otherwise secure communications, and there must be a business associate agreement in place.
OCR’s COVID-19 Telehealth Enforcement Discretion Transition Period Ends
|
|
Unauthorized Use of Medical Illustrations
|
Unauthorized use of medical illustrations or images containing patient information in presentations, publications, or websites. Consent must be obtained before any images that have not been de-identified according to HIPAA standards can be used in presentations, publications, or for training purposes.
Student Sues Hospital for Unauthorized Use of PHI as Teaching Tool
Radiology Groups Issue Warning About PHI Exposure in Online Medical Presentations
|
|
Medical Students Tracking Patients on EHRs
|
Medical students tracking former patients on EHRs to view outcomes and progress is a HIPAA violation unless patient consent has been obtained. Accessing the medical records of former patients on EHRs out of curiosity violates patient privacy.
Med Students Violating HIPAA by Tracking Patients on EHRs
|
Examples of Unintentional HIPAA Violations
Unintentional HIPAA violations can occur when healthcare professionals or organizations inadvertently access or disclose protected health information (PHI) without proper authorization, or when the HIPAA Rules are violated due to a lack of training.
| Unintentional HIPAA Violation |
Description of HIPAA Violation |
| Accidental Disclosure in Conversation |
Healthcare professionals may inadvertently discuss patient information in public areas, like elevators or cafeterias, without realizing that others can overhear, potentially violating HIPAA confidentiality rules. Such disclosures may occur due to a lack of awareness or caution in maintaining patient privacy.
Careless Talk Sees University of Iowa Worker Fired for HIPAA Privacy Violation |
| Email Errors |
Sending an email containing protected health information (PHI) to the wrong recipient due to an email address autocomplete mistake or selecting the incorrect recipient. This can lead to unauthorized access to sensitive patient data when the email recipient is not authorized to view the information.
Email Error Exposed the PHI of 8,000 Members of FirstCare Health Plans
Email Error Results in Impermissible Disclosure of the PHI of 900 Campbell County Health Patients
Email Error Impacts 6,500 Saliba’s Extended Care Pharmacy Patients
Dermatologist Email Error Exposes 14,910 Patients’ SSNs
University of Cincinnati Email Errors Result in 1,064-Patient Data Breach
Email Error Exposed the PHI of 8,000 Members of FirstCare Health Plans |
| Faxing Errors |
Mistakenly sending a fax with PHI to the wrong fax number or faxing PHI when it may be viewed by unauthorized individuals. Such errors can result in unintended access to patient information by individuals who should not have access to it.
Even HHS Involvement Did Not Stop Months of Fax Privacy Breaches
Faxing Error Sees PHI Sent to Local Media Outlet
Protected Health Information Sent to Incorrect Fax Recipient Over Several Months
New York Hospital Sued for Disclosing Patient’s HIV Status to Employer |
| Lost or Stolen Devices |
Losing electronic devices, such as laptops, smartphones, or tablets, that contain unencrypted patient data, or leaving them in areas where they can easily be stolen. If these devices are lost or stolen, it can inadvertently expose PHI to unauthorized individuals who may gain access to the device’s contents.
Lost Blackberry Device Results in $3.2 Million HIPAA Civil Monetary Penalty for Children’s Medical Center of Dallas
CardioNet Fined $2.5 Million for Laptop Theft and Data Breach
Lack of Encryption Leads to $3 Million HIPAA Penalty for New York Medical Center
Conn. OIG Reaches $90K Settlement with Hartford Hospital and BA Over 2012 Laptop Theft
Lifespan Laptop Theft Exposes ePHI of 20,000 Patients |
| Improper Disposal of Records |
Incorrectly disposing of paper records, like medical charts or billing documents, by placing them in regular trash bins without shredding or using other secure methods to render PHI unreadable, or disposing of electronic devices without securely wiping them. This can lead to unauthorized individuals accessing patient data by retrieving discarded records.
Kaiser Pays $49 Million to Settle Improper Disposal Investigation
Improper Disposal of PHI Results in $300,640 HIPAA Penalty
Improper Disposal Nets Small Pharmacy $125K OCR HIPAA Penalty
HealthReach Community Health Centers Reports Improper Disposal Incident Affecting Almost 117,000 Patients
Improper Disposal Incident at Smith’s Food & Drug Affects Almost 58,000 Patients |
| Misdirected Mail |
Mailing patient records or billing statements to the wrong address due to clerical errors or inaccuracies in patient information. Such mistakes can inadvertently share sensitive patient information with individuals who should not have access to it.
Kaiser Permanente Fined $450,000 for Mailing Error
Mailing Error Sees Inmediata Breach Notification Letters Sent to Incorrect Addresses
Email Error Exposed the PHI of 8,000 Members of FirstCare Health Plans
Mailing Error at CMS Vendor Affects 10,000 Medicare Beneficiaries
Mailing Error by State of Colorado Affects 12,230 Individuals
St. Vincent Breast Center Breaches HIPAA with 63K-Patient Mailing |
| Access by Unauthorized Personnel |
Allowing healthcare employees without the necessary access permissions to view or handle patient records, and failing to terminate access rights when employees are terminated or leave the company. This oversight can result in unintentional breaches of patient confidentiality.
Failure to Terminate Former Employee’s Access Rights Results in $202,400 HIPAA Fine for New Haven, CT
Failure to Terminate Former Employee’s PHI Access Costs Colorado Hospital $111,400
Pharma Sales Rep Pleads Guilty to Healthcare Fraud and Criminal HIPAA Violations
Survey Reveals Sharing EHR Passwords is Commonplace |
| Accessing PHI Out of Curiosity |
Healthcare professionals accessing patient records out of curiosity or without a legitimate medical reason. This action violates patient privacy and confidentiality unintentionally when healthcare workers access PHI without a valid need for patient care or treatment.
$240,000 HIPAA Penalty After Security Guards Access Medical Records
Med Students Violating HIPAA by Tracking Patients on EHRs
Ohio Hospital Worker Snooped on 7,300 Patient Records over 12 Years
Medical Center FacingLegal Action Over Snooping on George Floyd’s Medical Records
Dozens of Northwestern Memorial Hospital Employees Fired for Accessing Jussie Smollett’s Medical Records
Henry Mayo Newhall Hospital Fires Employees for Snooping on Medical Records
Hawaii Pacific Health Discovers 5-Year Insider Data Breach |
Are Data Breaches HIPAA Violations?
Data breaches are now a fact of life. Even with multi-layered cybersecurity defenses, data breaches are still likely to occur from time to time. OCR understands that healthcare organizations are being targeted by cybercriminals and that it is not possible to implement impregnable security defenses.
Being HIPAA compliant is not about making sure that data breaches never happen. HIPAA compliance is about reducing risk to an appropriate and acceptable level. Just because an organization experiences a data breach, it does not mean the breach was the result of a HIPAA violation.
The OCR breach portal now reflects this more clearly. Many data breaches are investigated by OCR and are found not to involve any violations of HIPAA Rules. When this happens, the investigations are closed without any action being taken.
How are Common HIPAA Violations Discovered?
Common HIPAA violations can continue for many months, or even years before they are discovered. The longer they are allowed to persist, the greater the penalty will be when they are eventually discovered. It is important for HIPAA-covered entities to conduct regular HIPAA compliance reviews (this is required by the HIPAA law) to make sure common HIPAA violations are discovered and corrected before they are identified by regulators.
There are three main ways that common HIPAA violations are discovered:
- Investigations into a data breach by OCR (or state attorneys general)
- Investigations into complaints about covered entities and business associates
- HIPAA compliance audits
Even when a data breach does not involve a HIPAA violation, or a complaint proves to be unfounded, OCR may uncover unrelated HIPAA violations that could warrant a financial penalty.
FAQs
What does it mean to “reduce risk to an appropriate and acceptable level”?
What reducing risk to an appropriate and acceptable level means is that, when potential risks and vulnerabilities are identified, Covered Entities and Business Associates have to decide what measures are reasonable to implement according to the size, complexity, and capabilities of the organization, the existing measures already in place, and the cost of implementing further measures in relation to the likelihood of a data breach and the scale of injury it could cause.
How is it possible to prevent employees from snooping on healthcare records?
To prevent employees from snooping on healthcare records, Covered Entities should implement a program of training, ensure access privileges comply with the Minimum Necessary Standard, activate audit logs, and enforce sanctions. It is also important that employees are made aware during HIPAA training that, although many cases of healthcare snooping are attributable to curiosity rather than malicious intent, all cases of healthcare snooping are HIPAA violations.
If encryption is not mandatory, how can it be a HIPAA violation if records are unencrypted?
Although encryption is not mandatory, it can be a HIPAA violation if records are unencrypted and no other measure that is equally as effective has been implemented. Encryption is an addressable implementation specification of the Security Rule. This means organizations can only avoid implementing the requirement if it is not reasonable and appropriate in the circumstances, or if an alternative security measure is equally as effective. If organizations fail to encrypt records, they have to document the reasons why.
Why was the fine for denying patients access to health records so high?
The fine for denying patients access to health records was so high in the event mentioned in the article because, in this particular case, the non-cooperation of the Covered Entity contributed to the size of the fine (you can read about the case here). Since this case, the CMS´ Meaningful Use program has evolved into the Promoting Interoperability program, and – in addition to being sanctioned for a HIPAA violation – any covered entity failing to provide health records in a timely manner could now also lose a percentage of their Medicare payments.
What are the consequences of accessing a patient chart without reason?
The consequences of accessing a patient chart without reason vary depending on the reason for the impermissible access and the organization´s sanctions policy. If it was an employee’s first violation and no harm was caused by the violation, it is likely the employee will receive a warning and have to undergo additional training. If the violation was a repeat offense, caused harm to the patient or organization, and was done with malicious intent, the likely consequences are termination of contract, a report to a licensing authority, and the possible involvement of law enforcement.
Are HIPAA violations common?
Nobody knows if HIPAA violations are common because, although HHS´ Office for Civil Rights publishes an “Enforcement Highlights” webpage, the statistics on this page only relate to reports and complaints received by the agency. HIPAA violations can also be reported to the Centers for Medicare and Medicaid (CMS), the Federal Trade Commission (FTC), State Attorneys General, the Covered Entity at which the HIPAA violation occurred, or not reported at all.
How do HIPAA violations affect patients?
HIPAA violations affect patients in different ways depending on the nature of the violation. If a hospital has failed to enter into a Business Associate Agreement with a company that provides data analysis services, the violation will not affect patients at all. Conversely, if a HIPAA violation results in the exposure of patients’ personal information, which is then used to conduct identity theft, this will significantly affect patients. For these reasons, there is no one-size-fits-all answer to this question.
What are examples of HIPAA violations?
In addition to the examples of HIPAA violations listed above, Covered Entities can violate HIPAA by failing to comply with the Administrative Requirements of HIPAA. These include the Transaction, Code Sets, and Identifier Standards published by the Department of Health and Human Services; and although Covered Entities are not fined for violations of this nature, they can be excluded from the Medicare program by CMS – which will substantially affect their income.
What is considered a HIPAA violation by the Federal Trade Commission?
An event considered a HIPAA violation by the Federal Trade Commission (FTC) is a failure to comply with the Breach Notification Rule by an organization that has access to PHI, but which does not qualify as a Covered Entity or Business Associate – for example, vendors of Personal Health Records.
Organizations that are not Covered Entities or Business Associates do not have to comply with the Privacy or Security Rule, but they do have to comply with the Breach Notification Rule, and the failure to notify individuals and the FTC of a data breach is considered a HIPAA violation by the FTC – which has the authority to issue substantial fines for non-compliance.
What counts as a HIPAA violation by employees?
What counts as a HIPAA violation by employees is the failure to comply with employers’ HIPAA-related policies and procedures – provided employees have received adequate training on the policies and procedures. In such cases, the employee will be subject to the sanctions listed in their employer’s sanctions policy (verbal warning, written warning, suspension, termination, etc.).
Employees can also violate HIPAA by knowingly and wrongfully disclosing PHI. In such cases, employers are required to notify HHS´ Office for Civil Rights, who will refer the case to the Department of Justice. If there is evidence of criminal wrongdoing, the Department of Justice can pursue fines of up to $250,000 for HIPAA violations by employees and custodial sentences of up to ten years.
What constitutes a HIPAA violation by Business Associates?
What constitutes a HIPAA violation by Business Associates is the failure to comply with any parts of the Security Rule, the requirement to notify Covered Entities of any security incident (not only breaches of unsecured ePHI), or any other requirement stipulated in a Business Associate Agreement.
Generally, Business Associates are required to comply with all provisions of the HIPAA Security Rule and several sections of the Breach Notification Rule. Additionally, depending on the service they provide for or on behalf of a Covered Entity – and the content of Business Associate Agreements – Business Associates may also be required to comply with parts of the Administrative Requirements and the Privacy Rule.
What are the 3 types of HIPAA violations?
There are many “3 types of HIPAA violations”. For example, there are criminal, civil, and accidental violations of HIPAA; Privacy Rule, Security Rule, and Breach Notification Rule violations of HIPAA; and violations of HIPAA reportable to the Centers for Medicare and Medicaid (CMS), HHS´ Office for Civil Rights, and the Federal Trade Commission.
Is it possible for there to be an intentional but acceptable HIPAA violation?
It is possible for there to be an intentional but acceptable HIPAA violation, but only when HHS’ Office for Civil Rights issues a Notice of Enforcement Discretion. These Notices allow Covered Entities to intentionally violate certain HIPAA provisions in certain circumstances for the period of time a Notice of Enforcement Discretion is in force.
It is important to be aware that disclosing PHI in an emergency situation to a Covered Entity with whom no treatment relationship exists is not an intentional but acceptable HIPAA violation. This scenario is permitted by §164.510 of the Privacy Rule provided that any PHI disclosed is limited and relevant to an individual´s care.
Who is responsible for the most common HIPAA violations?
It is not known who is responsible for most common HIPAA violations because it is highly likely most common HIPAA violations are reported to the organization where the violation occurred and this information is not released into the public domain. Additionally, Business Associates are required to report “security incidents” to Covered Entities who then notify affected individuals and HHS’ Office for Civil Rights if the security incident constitutes a breach of unsecured PHI.
Why are there no examples of HIPAA violations by employers?
There are no examples of HIPAA violations by employers because employers are not Covered Entities under HIPAA. Even if a healthcare organization qualifies as a Covered Entity, it is not required to comply with HIPAA in its role as an employer – just in its role as a healthcare organization.
An exception to this explanation exists if an employer administers a self-sponsored health plan. However, because this is a rare scenario – and because employers in this situation are only subject to partial compliance – there are no examples of HIPAA violations by employers publicly reported.
What are the consequences of accessing a patient chart without reason?
The consequences of accessing a patient chart without reason depend on multiple factors. If the person who accessed the chart was a member of a Covered Entity’s workforce, if they did not have the authorization to access the chart, and if they had received training on the Covered Entity’s policies, the event is a violation of the Covered Entity’s policies.
Therefore, the consequences of accessing a patient chart without reason depend on the content of the Covered Entity’s sanctions policy. This may mean the person is given a verbal warning and required to undergo refresher training; or, if the person has received previous verbal warnings, the consequences could be a written warning, final warning, or termination of a contract.
What are HIPAA violations?
HIPAA violations are the failure to comply with the provisions and implementation specifications of the HIPAA Administrative Simplification provisions (45 CFR Parts 160,162, and 164). Most HIPAA violations are civil incidents committed by Covered Entities and Business Associates. It is rare that an individual violates HIPAA because individuals are most often members of a Covered Entity’s or Business Associate’s workforce and subject to their employer’s policies.
Are all violations of HIPAA resolved by financial penalties?
Very few violations of HIPAA are resolved by financial penalties. In most cases, violations of HIPAA are resolved by voluntary compliance, technical assistance, or corrective action plans. However, these “secondary” resolutions also have a financial cost in terms of revising policies and procedures, implementing safeguards, retraining members of the workforce, and other business disruptions.
Are lost medical records a HIPAA violation?
Lost medical records are a HIPAA violation – even if the records are subsequently found – because there has been a failure to ensure the availability of PHI when the records were lost. Additionally, while the medical records were lost, they may have been viewed or altered by an unauthorized person, so there has also been a failure to ensure the confidentiality and integrity of PHI.
What is considered a HIPAA violation punishable by a custodial sentence?
A HIPAA violation punishable by a custodial sentence is considered to be when a person knowingly and wrongfully obtains or discloses individually identifiable health information without authorization. Depending on the motive and whether the act was committed under false pretenses, the person can be fined up to $250,000 and given a custodial sentence of up to ten years.
Who can violate HIPAA?
Who can violate HIPAA is limited to Covered Entities, Business Associates, and members of their workforces. If an organization is not a Covered Entity or Business Associate, or an individual is not a member of either’s workforce, it is not possible to violate HIPAA because HIPAA will not apply to the organization/individual.
What is a HIPAA violation of the Breach Notification Rule?
A HIPAA violation of the Breach Notification Rule is the failure to comply with any provision of 45 CFR 164 Subpart D when Protected Health Information has been acquired, accessed, used, or disclosed in a manner not permitted by the Privacy Rule, and the impermissible acquisition, access, use, or disclosure compromises the security or privacy of the Protected Health Information.
Is it a HIPAA violation to say someone is in the hospital?
It can be a HIPAA violation to say someone is in the hospital, but only in a limited number of circumstances. For example, the person making the statement must be a member of a Covered Entity’s workforce, the statement must be made to somebody with whom there is no direct treatment or familial relationship, and when the subject of the statement has not been given an opportunity to object to the statement being made.
Is inappropriate access to medical records a HIPAA violation example or a HIPAA breach example?
Inappropriate access to medical records is certainly a HIPAA violation example regardless of who the individual accessing the medical records is. Whether or not it constitutes a HIPAA breach example depends on whether the inappropriate access compromises the security or privacy of the Protected Health Information maintained in the medical records.
Is there a list of HIPAA violations?
There is no list of HIPAA violations because many HIPAA violations are reported to the organization at which they occurred, and they never become public knowledge. What you can find a list of is a list of HIPAA data breaches affecting more than 500 individuals that have been reported to HHS’ Office for Civil Rights. This list can be found on the HHS’ Breach Report web page.
Can you sue someone for disclosing medical information?
You cannot sue someone for disclosing medical information under HIPAA because HIPAA has no private right of action. However, if you believe someone has disclosed your medical information – and because of the disclosure you have suffered harm – you may be able to file a civil action under a state law. Because some states have privacy and security laws that include a private right or action and others don´t, it is best to seek legal advice from a local attorney.
How can I find out who has accessed my medical records?
You can find out who has accessed your medical records by requesting an Accounting of Disclosures from your healthcare provider. The healthcare provider has to reply to your request within 30 days and provide you with a list of every time you’re your medical records have been accessed for uses other than those permitted by the Privacy Rule (i.e., treatments, payments, etc.).
Who can access my medical records without my permission?
Your medical records can be accessed without your permission by any member of a Covered Entity’s or Business Associate’s workforce provided they have the authority to access your records and the reason why they are accessing your medical records is permitted by the Privacy Rule. If your medical records are accessed by somebody without the authority to do so, or for a reason not permitted by the Privacy Rule, this would be a violation of HIPAA.
Can a family member violate HIPAA?
A family member can violate HIPAA if, for example, they are also your dentist and they disclose your health information impermissibly. However, if the family member is not a member of the medical profession – or a member of a Covered Entity´s or Business Associate’s workforce – it is not possible for them to violate HIPAA because only Covered Entities, Business Associates, and members of their workforces are required to comply with HIPAA
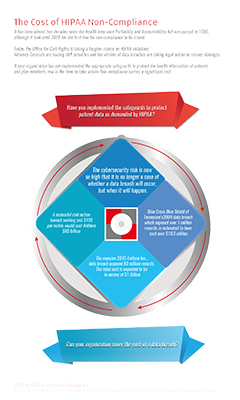
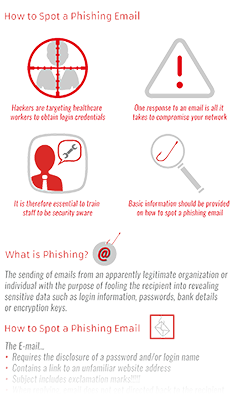
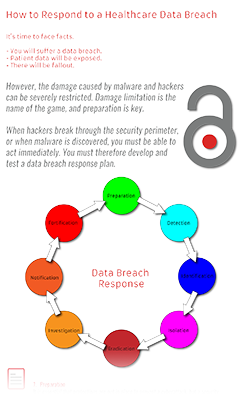
HIPAA Compliance Infographics
The post The 10 Most Common HIPAA Violations You Should Avoid appeared first on HIPAA Journal.

 Accessing the health records of patients for reasons other than those permitted by the Privacy Rule is a violation of patient privacy. Snooping on healthcare records of family, friends, neighbors, co-workers, and celebrities is one of the most common HIPAA violations committed by employees. When discovered, these violations can result in termination of employment but could also result in criminal charges for the employee concerned. Financial penalties for healthcare organizations that have failed to prevent snooping are relatively uncommon, but they are possible – as the University of California Los Angeles Health System discovered.
Accessing the health records of patients for reasons other than those permitted by the Privacy Rule is a violation of patient privacy. Snooping on healthcare records of family, friends, neighbors, co-workers, and celebrities is one of the most common HIPAA violations committed by employees. When discovered, these violations can result in termination of employment but could also result in criminal charges for the employee concerned. Financial penalties for healthcare organizations that have failed to prevent snooping are relatively uncommon, but they are possible – as the University of California Los Angeles Health System discovered. Performing a risk analysis is essential, but it is not just a checkbox item for compliance. Risks that are identified must then be subjected to a risk management process. They should be prioritized and addressed in a reasonable time frame. Knowing about risks to PHI and failing to address them is one of the most common HIPAA violations penalized by the Office for Civil Rights.
Performing a risk analysis is essential, but it is not just a checkbox item for compliance. Risks that are identified must then be subjected to a risk management process. They should be prioritized and addressed in a reasonable time frame. Knowing about risks to PHI and failing to address them is one of the most common HIPAA violations penalized by the Office for Civil Rights.


 You can use our free Protected Health Information Guide to learn how to de-identify and anonymize PHI. If you de-identify PHI so that the identity of individuals cannot be determined, and re-identification of individuals is not possible, PHI can be freely shared.
You can use our free Protected Health Information Guide to learn how to de-identify and anonymize PHI. If you de-identify PHI so that the identity of individuals cannot be determined, and re-identification of individuals is not possible, PHI can be freely shared. The first HIPAA compliant way to de-identify protected health information is to remove specific identifiers from the data set. The identifiable data that must be removed according to
The first HIPAA compliant way to de-identify protected health information is to remove specific identifiers from the data set. The identifiable data that must be removed according to  The expert determination method carries a small risk that an individual could be identified, although the risk is so low that it meets HIPAA Privacy Rule requirements.
The expert determination method carries a small risk that an individual could be identified, although the risk is so low that it meets HIPAA Privacy Rule requirements.