In October 2017, there were 27 healthcare data breaches reported to the Department of Health and Human Services’ Office for Civil Rights. Those data breaches resulted in the theft/exposure of 71,377 patient and plan member records. October saw a significant fall in the number of reported breaches compared to September, and a major fall in the number of records exposed.

October saw a major reduction in the number of breached records, with the monthly total almost 85% lower than September and almost 88% lower than the average number of records breached over the preceding three months.

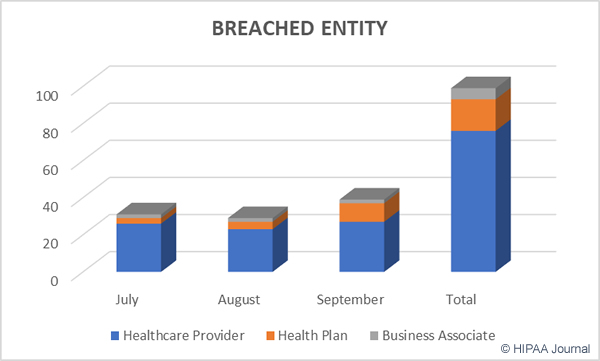
Healthcare providers were the worst hit in October with 19 reported data breaches. There were six data breaches reported by health plans and at least two incidents involved business associates of HIPAA-covered entities.
October 2017 Healthcare Data Breaches by Covered Entity Type

Main Causes of October 2017 Healthcare Data Breaches
Unauthorized access/disclosures were the biggest causes of healthcare data breaches in October. There were 14 breaches reported involving unauthorized access/disclosures, 8 hacking incidents, four cases of theft, and one unencrypted laptop computer was lost.

Unauthorized access/disclosures were the leading causes of October 2017 healthcare data breaches, although hacking/IT incidents exposed more records – Over twice the number of records exposed by unauthorized access/disclosures and hacking/IT incidents exposed more records than all other breach types combined.

Location of Exposed and Stolen Protected Health Information
Email was the most common location of breached PHI in October. Five of the nine incidents involving email were the result of hacking/IT incidents such as phishing. The remaining four incidents were unauthorized access/disclosures such as healthcare employees sending emails containing PHI to incorrect recipients. Five incidents involved paper records, highlighting the importance of securing physical records as well as electronic protected health information.

October 2017 Healthcare Data Breaches by State
In October, healthcare organizations based in 22 states reported data breaches. The state that experienced the most data breaches was Florida, with 3 reported breaches. Maryland, Massachusetts, and New York each had two breaches.
Alabama, Arizona, California, Connecticut, Georgia, Iowa, Illinois, Kansas, Kentucky, Louisiana, Missouri, North Carolina, Ohio, Rhode Island, Tennessee, Texas, Virginia, and Washington each had one reported breach.
Largest Healthcare Data Breaches in October 2017
| Breached Entity | Entity Type | Breach Type | Individuals Affected |
| Chase Brexton Health Care | Healthcare Provider | Hacking/IT Incident | 16,562 |
| East Central Kansas Area Agency on Aging | Business Associate | Hacking/IT Incident | 8,750 |
| Brevard Physician Associates | Healthcare Provider | Theft | 7,976 |
| MHC Coalition for Health and Wellness | Healthcare Provider | Theft | 5,806 |
| Catholic Charities of the Diocese of Albany | Healthcare Provider | Hacking/IT Incident | 4,624 |
| MGA Home Healthcare Colorado, Inc. | Healthcare Provider | Hacking/IT Incident | 2,898 |
| Orthopedics NY, LLP | Healthcare Provider | Unauthorized Access/Disclosure | 2,493 |
| Mann-Grandstaff VA Medical Center | Healthcare Provider | Theft | 1,915 |
| Arch City Dental, LLC | Healthcare Provider | Unauthorized Access/Disclosure | 1,716 |
| John Hancock Life Insurance Company (U.S.A.) | Health Plan | Unauthorized Access/Disclosure | 1,715 |
The post October 2017 Healthcare Data Breaches appeared first on HIPAA Journal.





 Imperial Valley Family Care Medical Group is a multi-specialty physician’s group with 16 facilities spread throughout California. IVFCMG was not selected for a desk audit, although following the theft of a laptop computer, OCR investigated the breach. IVFCMG was required to demonstrate compliance with HIPAA Rules and provide documentation to show the breach was not caused by the failure to follow HIPAA Rules.
Imperial Valley Family Care Medical Group is a multi-specialty physician’s group with 16 facilities spread throughout California. IVFCMG was not selected for a desk audit, although following the theft of a laptop computer, OCR investigated the breach. IVFCMG was required to demonstrate compliance with HIPAA Rules and provide documentation to show the breach was not caused by the failure to follow HIPAA Rules.