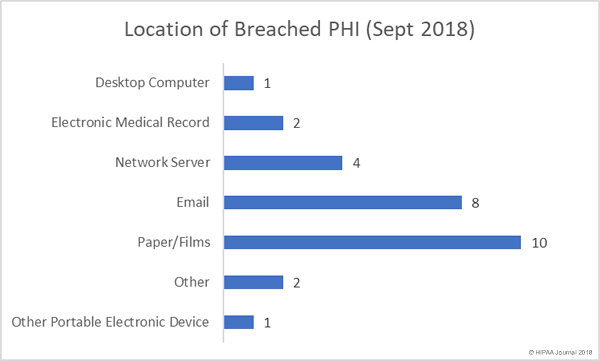
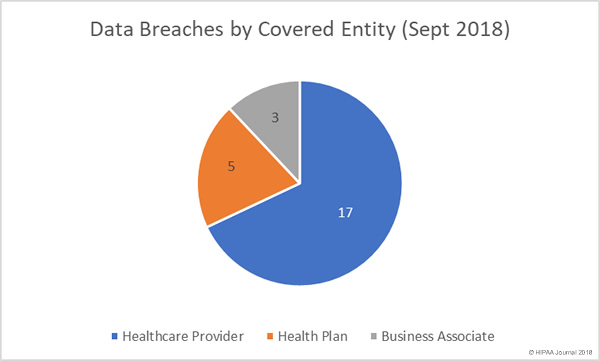
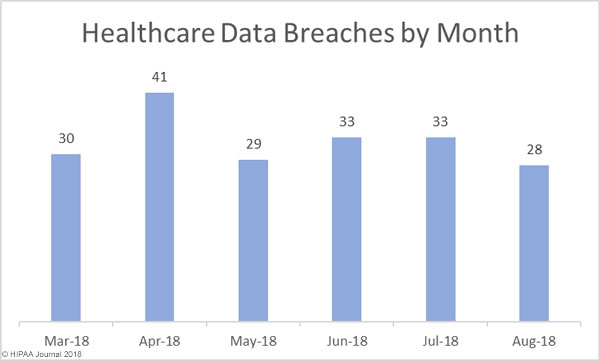
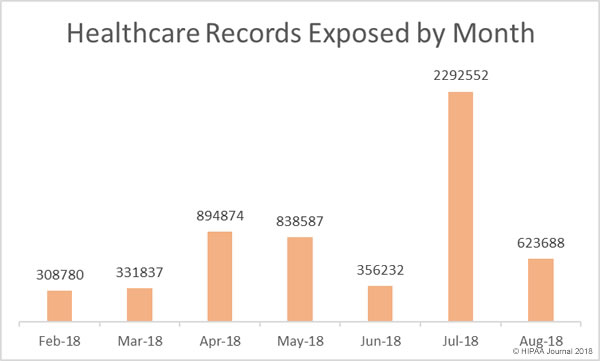
The HHS has drafted a Request for Information (RFI) to discover how HIPAA Rules are hampering patient information sharing and are making it difficult for healthcare providers to coordinate patient care.
HHS wants comments from the public and healthcare industry stakeholders on any provisions of HIPAA Rules which are discouraging or limiting coordinated care and case management among hospitals, physicians, patients, and payors.
The RFI is part of a new initiative, named Regulatory Sprint to Coordinated Care, the aim of which is to remove barriers that are preventing healthcare organizations from sharing patient information while retaining protections to ensure patient and data privacy are protected.
The comments received through the RFI will guide the HHS on how HIPAA can be improved, and which policies should be pursued in rulemaking to help the healthcare industry transition to coordinated, value-based health care.
The RFI was passed to the Office of Management and Budget for review on November 13, 2018. It is currently unclear when the RFI will be issued.
Certain provisions of HIPAA Rules are perceived to be barriers to information sharing. The American Hospital Association has spoken out about some of these issues and has urged the HHS to take action.
While there are certainly elements of HIPAA Rules that would benefit from an update to improve the sharing of patient health information, in some cases, healthcare organizations are confused about the restrictions HIPAA places on information sharing and the circumstances under which PHI can be shared with other entities without the need to obtain prior authorization from patients.
The feedback HHS is seeking will be used to assess what aspects of HIPAA are causing problems, whether there is scope to remove certain restrictions to facilitate information sharing, and areas of misunderstanding that call for further guidance to be issued on HIPAA Rules.
HIPAA does permit healthcare providers to share patients’ PHI with other healthcare providers for the purposes of treatment or healthcare operations without authorization from patients. However, there is some confusion about what constitutes treatment/healthcare operations in some cases, how best to share PHI, and when it is permissible to share PHI with entities other than healthcare providers. Simplification of HIPAA Rules could help in this regard, as could the creation of a safe harbor for good faith disclosures of PHI for the purposes of case management and care co-ordination.
While the HHS is keen to create an environment where patients’ health information can be shared more freely, the HHS has made it clear is that there will not be any changes made to the HIPAA Security Rule. Healthcare providers, health plans, and business associates of HIPAA-covered entities will still be required to implement controls to ensure risks to the confidentiality, integrity, and availability of protected health information are managed and reduced to a reasonable and acceptable level.
In addition to a general request for information, the HHS will specifically be seeking information on:
- The methods of accounting of all disclosures of a patient’s protected health information
- Patients’ acknowledgment of receipt of a providers’ notice of privacy practices
- Creation of a safe harbor for good faith disclosures of PHI for purposes of care coordination or case management
- Disclosures of protected health information without a patient’s authorization for treatment, payment, and health care operations
- The minimum necessary standard/requirement.
While the RFI is likely to be issued, there are no guarantees that any of the comments submitted will result in HIPAA rule changes.
The post Do HIPAA Rules Create Barriers That Prevent Information Sharing? appeared first on HIPAA Journal.