On Wednesday, September 12, 2018, President Trump approved a request for a federal emergency declaration in the state of Virginia and made FEMA resources available for the state.
The Secretary of the U.S. Department of Health and Human Services, Alex Azar, has also declared a Public Health Emergency in Virginia, North Carolina, and South Carolina.
The Secretarial declaration eases certain HIPAA restrictions and helps Centers for Medicare & Medicaid Services’ (CMS) beneficiaries and their healthcare providers prepare for the possible impact of Hurricane Florence and provides greater flexibility to meet emergency health needs.
During severe disasters and public emergencies healthcare providers face increased challenges and may struggle to continue to meet all requirements of the HIPAA Privacy Rule.
In emergency situations, such as during hurricanes, the HIPAA Privacy Rule still applies; however, Alex Azar’s declaration of a Public Health Emergency means certain provisions of the Privacy Rule have been relaxed under the Project Bioshield Act of 2004 (PL 108-276) and section 1135(b) of the Social Security Act.
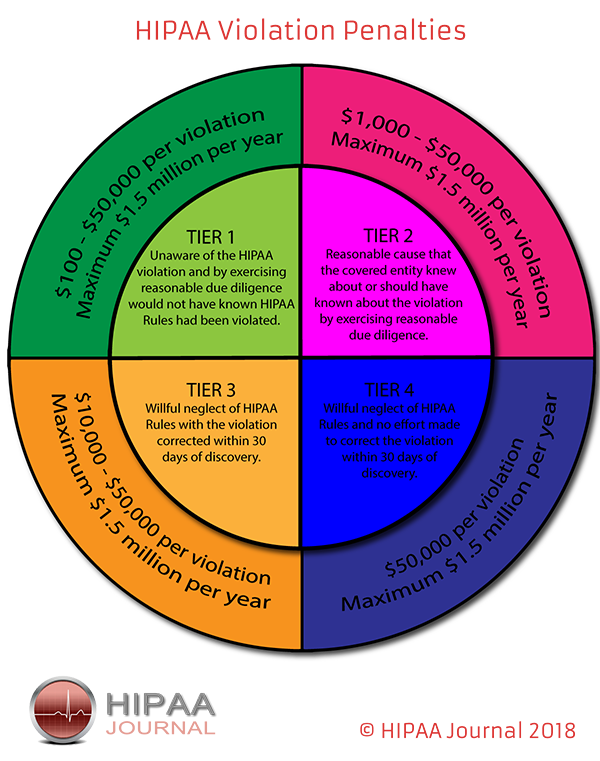
During the period of the Public Health Emergency, sanctions and penalties against healthcare providers are waived for the following provisions of the HIPAA Privacy Rule.
- 45 CFR 164.510(b) – The requirement to obtain authorization from a patient to speak with family members or friends involved in the patient’s care
- 45 CFR 164.510(a) – The requirement to honor requests to opt out of the facility directory
- 45 CFR 164.520 – The requirement to distribute a notice of privacy practices
- 45 CFR 164.522(a) – The patient’s right to request privacy restrictions
- 45 CFR 164.522(b) – The patient’s right to request confidential communications
Sanctions and penalties for healthcare organizations have not been waived for all other requirements of the HIPAA Privacy, Security, and Breach Notification Rules.
The waiver only exists in the areas covered by the public health emergency declaration for the period identified in the declaration, and only when hospitals have initiated their disaster protocol. The waiver only lasts for 72 hours following the declaration of the emergency.
When the Presidential or Secretarial declaration terminates, the waiver no longer applies, even to those patients still in the care of a hospital and even if the 72-hour time period has not elapsed.
The HHS’ Office for Civil Rights has responded to the declaration by issuing guidance on appropriate sharing of health information in emergency situations, confirming how the HIPAA Privacy Rule applies to healthcare providers in the disaster emergency zone.
OCR has also made a HIPAA Emergency Preparedness Decision Tool available to help healthcare providers determine how the HIPAA Privacy Rule applies.
The post Hurricane Florence: OCR Issues Guidance on Appropriate Sharing of Health Information appeared first on HIPAA Journal.