We have compiled healthcare data breach statistics from October 2009 when the Department of Health and Human Services’ Office for Civil Rights first started publishing summaries of healthcare data breaches on its website.
The healthcare data breach statistics below only include data breaches of 500 or more records as smaller breaches are not published by OCR. The breaches include closed cases and breaches still being investigated by OCR.
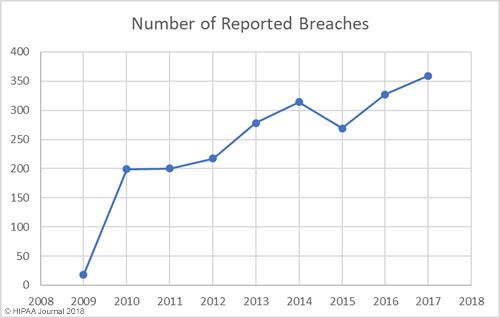
Our healthcare data breach statistics clearly show there has been an upward trend in data breaches over the past 9 years, with 2017 seeing more data breaches reported than any other year since records first started being published.
There have also been notable changes over the years in the main causes of breaches. The loss/theft of healthcare records and electronic protected health information dominated the breach reports between 2009 and 2015, although better policies and procedures and the use of encryption has helped reduce these easily preventable breaches. Our healthcare data breach statistics show the main causes of healthcare data breaches is now hacking/IT incidents, with unauthorized access/disclosures also commonplace.
Healthcare Data Breaches by Year
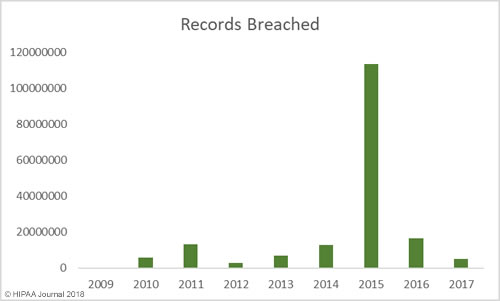
Between 2009 and 2017 there have been 2,181 healthcare data breaches involving more than 500 records. Those breaches have resulted in the theft/exposure of 176,709,305 healthcare records. That equates to more than 50% of the population of the United States (54.25%). Healthcare data breaches are now being reported at a rate of more than one per day.
Healthcare Records Exposed by Year
While there has been a general upward trend in the number of records exposed each year, there was a massive improvement in 2017 – the best year since 2012 in terms of the number of records exposed. However, while breaches were smaller in 2017, it was a record breaking year in terms of the number of healthcare data breaches reported – 359 incidents.
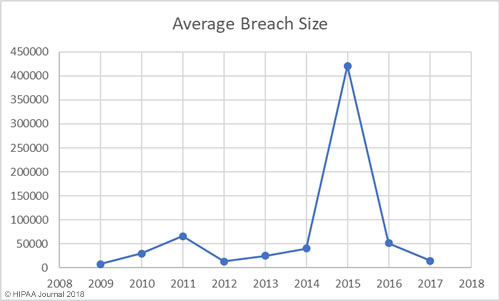
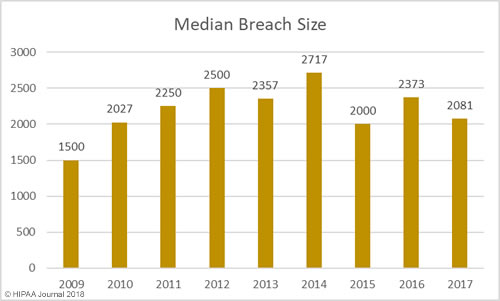
Average/Median Healthcare Data Breach Size by Year
Largest Healthcare Data Breaches (2009-2017)
| Rank |
Year |
Entity |
Entity Type |
Records Exposed/Stolen |
Cause of Breach |
| 1 |
2015 |
Anthem, Inc. Affiliated Covered Entity |
Health Plan |
78800000 |
Hacking/IT Incident |
| 2 |
2015 |
Premera Blue Cross |
Health Plan |
11000000 |
Hacking/IT Incident |
| 3 |
2015 |
Excellus Health Plan, Inc. |
Health Plan |
10000000 |
Hacking/IT Incident |
| 4 |
2011 |
Science Applications International Corporation |
Business Associate |
4900000 |
Loss |
| 5 |
2014 |
Community Health Systems Professional Services Corporation |
Business Associate |
4500000 |
Theft |
| 6 |
2015 |
University of California, Los Angeles Health |
Healthcare Provider |
4500000 |
Hacking/IT Incident |
| 7 |
2013 |
Advocate Medical Group |
Healthcare Provider |
4029530 |
Theft |
| 8 |
2015 |
Medical Informatics Engineering |
Business Associate |
3900000 |
Hacking/IT Incident |
| 9 |
2016 |
Banner Health |
Healthcare Provider |
3620000 |
Hacking/IT Incident |
| 10 |
2016 |
Newkirk Products, Inc. |
Business Associate |
3466120 |
Hacking/IT Incident |
| 11 |
2016 |
21st Century Oncology |
Healthcare Provider |
2213597 |
Hacking/IT Incident |
| 12 |
2014 |
Xerox State Healthcare, LLC |
Business Associate |
2000000 |
Unauthorized Access/Disclosure |
| 13 |
2011 |
IBM |
Business Associate |
1900000 |
Unknown |
| 14 |
2011 |
GRM Information Management Services |
Business Associate |
1700000 |
Theft |
| 15 |
2010 |
AvMed, Inc. |
Health Plan |
1220000 |
Theft |
| 16 |
2015 |
CareFirst BlueCross BlueShield |
Health Plan |
1100000 |
Hacking/IT Incident |
| 17 |
2014 |
Montana Department of Public Health & Human Services |
Health Plan |
1062509 |
Hacking/IT Incident |
| 18 |
2011 |
The Nemours Foundation |
Healthcare Provider |
1055489 |
Loss |
| 19 |
2010 |
BlueCross BlueShield of Tennessee, Inc. |
Health Plan |
1023209 |
Theft |
| 20 |
2011 |
Sutter Medical Foundation |
Healthcare Provider |
943434 |
Theft |
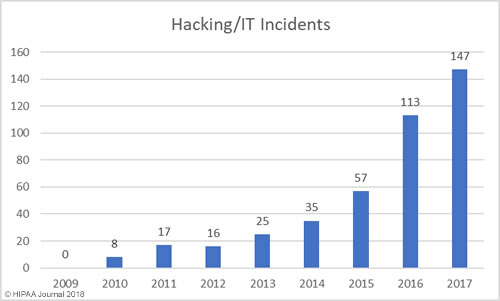
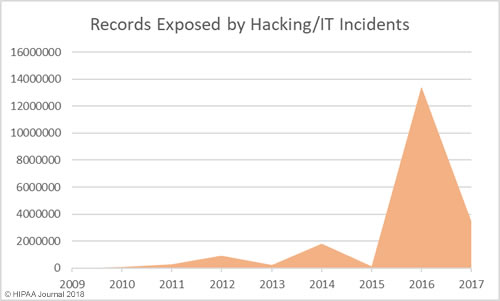
Healthcare Hacking Incidents by Year
Our healthcare data breach statistics show hacking is now the leading cause of healthcare data breaches, although healthcare organizations are now much better at detecting breaches when they do occur. The low hacking/IT incidents in the earlier years is likely to be due, in part, to the failure to detected hacking incidents and malware infections quickly. Many of the hacking incidents in 2014-2017 occurred many months, and in come cases years, before they were detected.
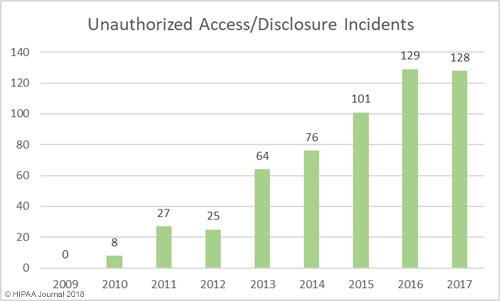
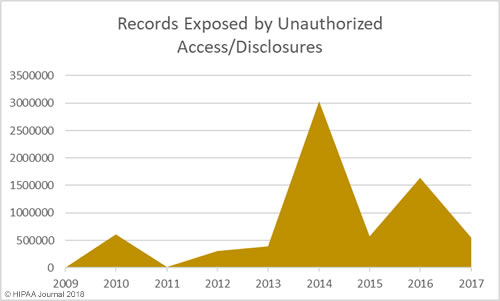
Unauthorized Access/Disclosures by Year
As with hacking, healthcare organizations are getting better at detecting internal breaches and also reporting those breaches to the Office for Civil Rights. While hacking is the main cause of breaches, unauthorized access/disclosure incidents are in close second.
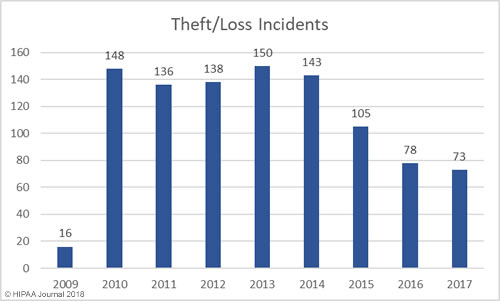
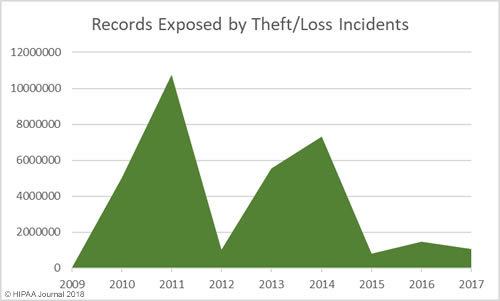
Loss/Theft of PHI and Unencrypted ePHI by Year
Our healthcare data breach statistics show HIPAA covered entities and business associates have got significantly better at protecting healthcare records with administrative, physical, and technical controls such as encryption, although unencrypted laptops and other electronic devices are still being left unsecured in vehicles and locations accessible by the public.
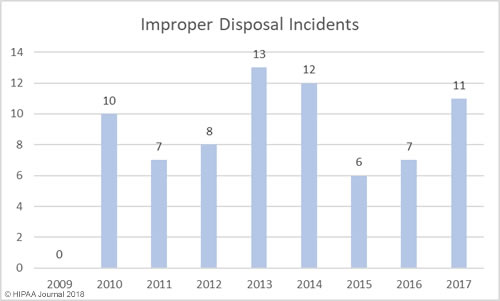
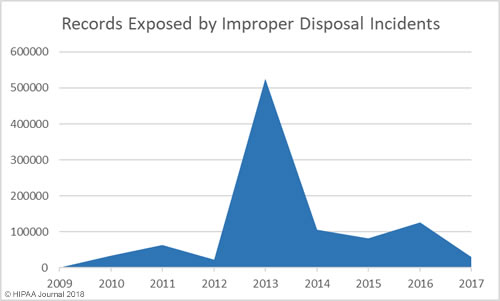
Improper Disposal of PHI/ePHI by Year
Breaches by Entity Type
| Year |
Provider |
Health Plan |
Business Associate |
Other |
Total |
| 2009 |
14 |
1 |
3 |
0 |
18 |
| 2010 |
134 |
21 |
44 |
0 |
199 |
| 2011 |
137 |
20 |
42 |
1 |
200 |
| 2012 |
155 |
22 |
36 |
4 |
217 |
| 2013 |
199 |
18 |
56 |
5 |
278 |
| 2014 |
202 |
71 |
41 |
0 |
314 |
| 2015 |
196 |
62 |
11 |
0 |
269 |
| 2016 |
257 |
51 |
19 |
0 |
327 |
| 2017 |
288 |
52 |
19 |
0 |
359 |
| Total |
1582 |
318 |
271 |
10 |
2181 |
OCR Settlements and Fines for HIPAA Violations
The penalties for HIPAA violations can be severe with multi-million-dollar fines possible when violations have been allowed to persist for several years or when multiple violations of HIPAA Rules have been allowed to occur.
The penalty structure for HIPAA violations is detailed in the infographic below:
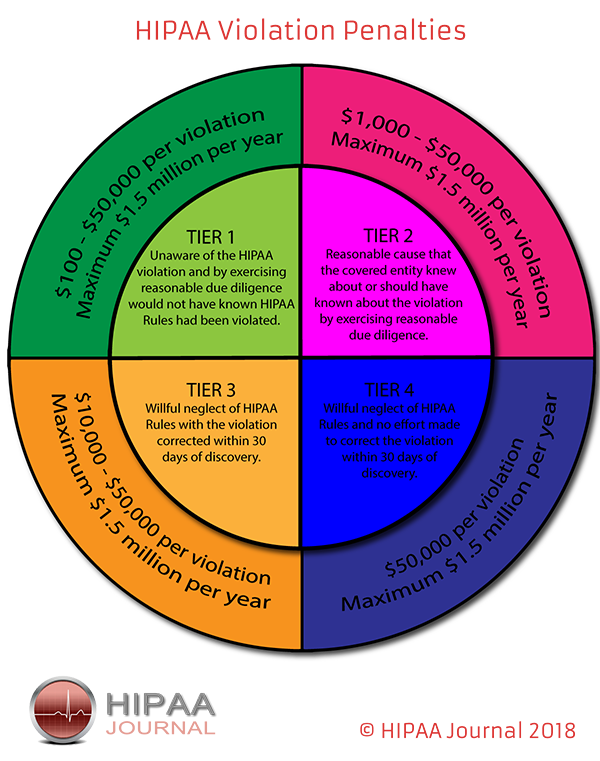
OCR Settlements and Fines Over the Years
The data for the healthcare data breach statistics on fines and settlements can be viewed on our HIPAA violation fines page, which details all HIPAA violation fines issued by OCR between 2008 and 2018. As the graph below shows, there has been a steady increase in HIPAA enforcement over the past 9 years.
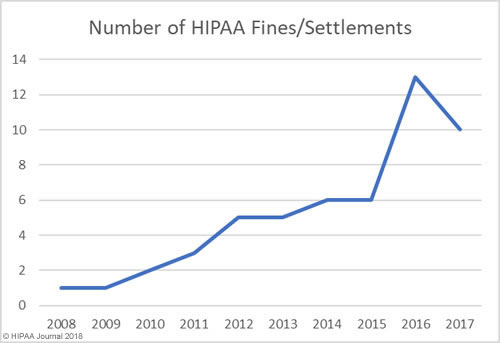
How Much Has OCR Fined HIPAA Covered Entities and Business Associates?
In addition to an increase in fines and settlements, the level of fines has increased substantially. Multi-million-dollar fines for HIPAA violations are now the norm.
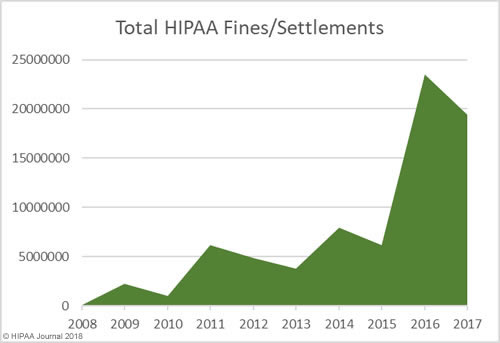
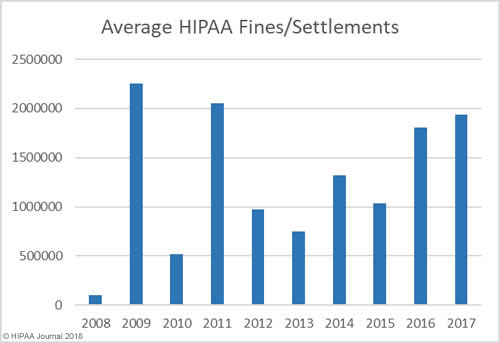
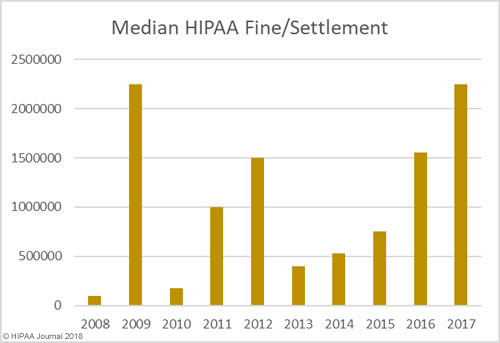
As the graphs above show, there has been a sizable increase in both the number of settlements and civil monetary penalties and the fine amounts in recent years. OCR’s budget has been cut so there are fewer resources to put into pursuing financial penalties in HIPAA violation cases. 2018 is likely to see fewer fines for HIPAA covered entities than the past two years, although settlement amounts are likely to remain high and even increase in 2018.OCR Director Roger Severino has indicated financial penalties are most likely to be pursued for particularly egregious HIPAA violations.
State Attorneys General HIPAA Fines and Other Financial Penalties for Healthcare Organizations
State attorneys general can issue fines ranging from $100 per HIPAA violation up to a maximum of $25,000 per violation category, per year.
Even when action is taken by state attorneys general over potential HIPAA violations, healthcare organizations are typically fined for violations of state laws. Only a handful of U.S. states have issued fines solely for HIPAA violations
Some of the major fines issued by state attorneys general for HIPAA violations and violations of state laws are listed below.
| Year |
State |
Covered Entity |
Amount |
Individuals affected |
Settlement/CMP |
Reason |
| 2018 |
NY |
EmblemHealth |
$575,000 |
81,122 |
Settlement |
Mailing error |
| 2018 |
NY |
Aetna |
$1,150,000 |
12,000 |
Settlement |
Mailing error |
| 2017 |
CA |
Cottage Health System |
$2,000,000 |
More than 54,000 |
Settlement |
Failure to adequately protect medical records |
| 2017 |
MA |
Multi-State Billing Services |
$100,000 |
2,600 |
Settlement |
Theft of unencrypted laptop containing PHI |
| 2017 |
NJ |
Horizon Healthcare Services Inc., |
$1,100,000 |
3.7 million |
Settlement |
Loss of unencrypted laptop computers |
| 2017 |
VT |
SAManage USA, Inc. |
$264,000 |
660 |
Settlement |
Spreadsheet indexed by search engines and PHI viewable |
| 2017 |
NY |
CoPilot Provider Support Services, Inc |
$130,000 |
221,178 |
Settlement |
Delayed breach notification |
| 2015 |
NY |
University of Rochester Medical Center |
$15,000 |
3,403 |
Settlement |
List of patients provided to nurse who took it to a new employer |
| 2015 |
CT |
Hartford Hospital/ EMC Corporation |
$90,000 |
8,883 |
Settlement |
Theft of unencrypted laptop containing PHI |
| 2014 |
MA |
Women & Infants Hospital of Rhode Island |
$150,000 |
12,000 |
Settlement |
Loss of backup tapes containing PHI |
| 2014 |
MA |
Boston Children’s Hospital |
$40,000 |
2,159 |
Settlement |
Loss of laptop containing PHI |
| 2014 |
MA |
Beth Israel Deaconess Medical Center |
$100,000 |
3,796 |
Settlement |
Loss of laptop containing PHI |
| 2013 |
MA |
Goldthwait Associates |
$140,000 |
67,000 |
Settlement |
Improper disposal |
| 2012 |
MN |
Accretive Health |
$2,500,000 |
24,000 |
Settlement |
Mishandling of PHI |
| 2012 |
MA |
South Shore Hospital |
$750,000 |
800,000 |
Settlement |
Loss of backup tapes containing PHI |
| 2011 |
VT |
Health Net Inc. |
$55,000 |
1,500,000 |
Settlement |
Loss of unencrypted hard drive/delayed breach notifications |
| 2011 |
IN |
WellPoint Inc. |
$100,000 |
32,000 |
Settlement |
Failure to report breach in a reasonable timeframe |
| 2010 |
CT |
Health Net Inc. |
$250,000 |
1,500,000 |
Settlement |
Loss of unencrypted hard drive/delayed breach notifications |
The post Healthcare Data Breach Statistics appeared first on HIPAA Journal.
















