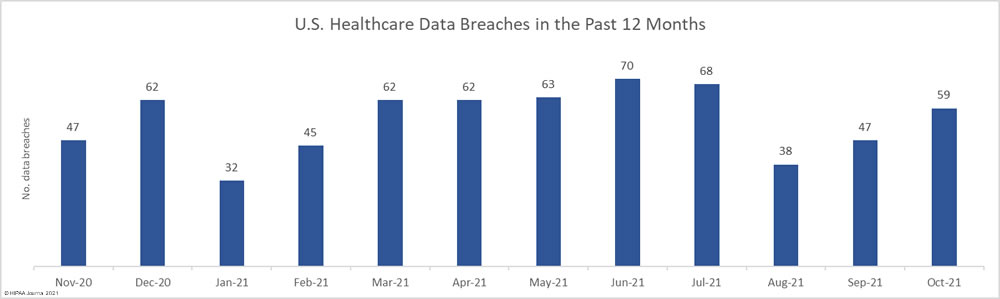
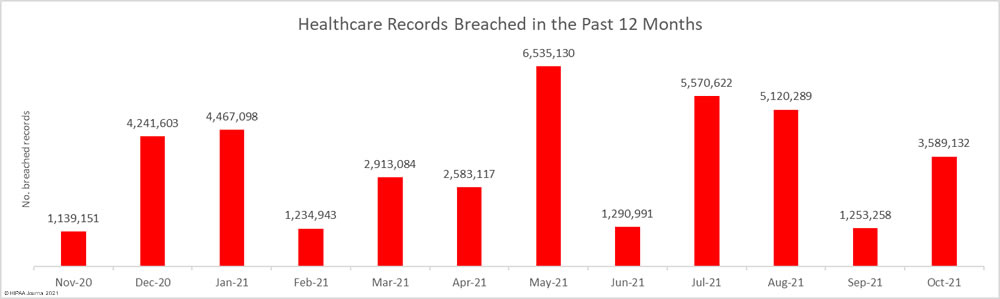
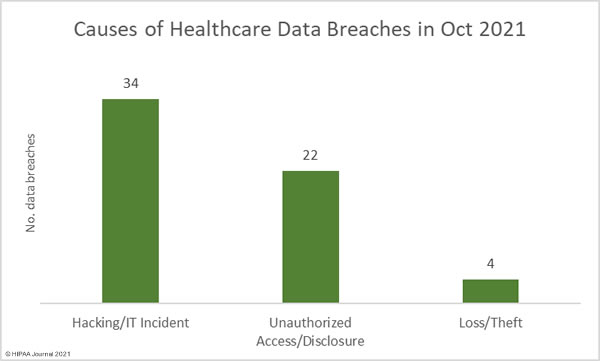
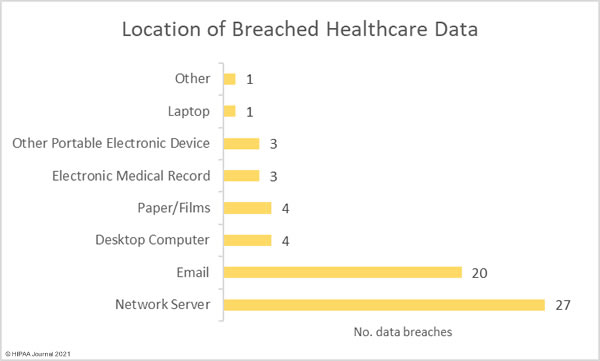
The HHS’ Office for Civil Rights (OCR) is continuing with its enforcement of compliance with the HIPAA Right of Access and has recently announced a further 5 financial penalties. The HIPAA Right of Access enforcement initiative was launched in the fall of 2019 in response to a significant number of complaints from patients who had not been provided with timely access to their medical records.
The HIPAA Privacy Rule requires covered entities to provide individuals with access to their medical records. A copy of the requested information must be provided within 30 days of the request being received, although an extension of 30 days may be granted in limited circumstances. HIPAA-covered entities are permitted to charge patients for exercising this important Privacy Rule right, but may only charge a reasonable, cost-based fee. Labor costs are only permitted for copying or otherwise creating and delivering the PHI after it has been identified.
The enforcement actions to date have not been imposed for charging excessive amounts, only for impermissibly refusing to provide a copy of the requested records or for unnecessary delays. In some cases, patients have had to wait many months before they were provided with a copy of their records.
The latest announcement by OCR brings the total number of HIPAA Right of Access enforcement actions under the 2019 enforcement initiative up to 25.
In all of the new cases below, OCR determined the healthcare providers were in violation of 45 C.F.R. § 164.524 and had not provided timely access to protected health information about the individual after receiving a request.
Advanced Spine & Pain Management, a provider of chronic pain-related medical services in Cincinnati and Springboro, OH, agreed to settle OCR’s investigation and paid a $32,150 financial penalty and will be monitored by OCR for compliance with its corrective action plan for 2 years. The investigation stemmed from a complaint from a patient who requested his medical records on November 25, 2019, but was not provided with the records until March 19, 2020.
Denver Retina Center, a Denver, CO-based provider of ophthalmological services, settled its investigation with OCR and paid a $30,000 financial penalty and will be monitored for compliance with its corrective action plan for 12 months. A patient alleged she had requested her records in December 2018 but did not receive a copy of her records until July 26, 2019. OCR had provided technical assistance to the healthcare provider following receipt of a previous HIPAA Right of Access complaint from the same patient and closed the case. When evidence was received of continued non-compliance the case was reopened. OCR determined that in addition to the delay, Denver Retina Center’s access policies and procedures were not compliant with the HIPAA Privacy Rule, as required by 45 C.F.R. § 164.530(i).
Rainrock Treatment Center LLC (dba Monte Nido Rainrock), a Eugene, OR-based provider of residential eating disorder treatment services, settled OCR’s investigation and paid a $160,000 financial penalty and will be monitored for compliance with the corrective action plan for 12 months. OCR had received three complaints from a patient who had not been provided with a copy of her medical records. The patient had requested a copy of her records on October 1, 2019, and November 21, 2019, and did not receive the requested records until May 22, 2020.
Wake Health Medical Group, a Raleigh, NC-based provider of primary care and other health care services, settled OCR’s investigation and paid a $10,000 financial penalty and has agreed to take corrective action to prevent further HIPAA Right of Access violations. OCR had received a complaint from a patient who requested a copy of her medical records on June 27, 2019 and paid a $25 flat fee, which is the standard fee charged by Wake Health Medical Group for providing copies of medical records. As of the date of the settlement, the patient has still not been provided with the requested records.
Dr. Robert Glaser, a New Hyde Park, NY-based cardiovascular disease and internal medicine doctor, did not cooperate with OCR during the investigation, although did not contest the findings and waived his right to a hearing. A civil monetary penalty of $100,000 was imposed by OCR. An investigation was launched following receipt of a complaint from a former patient who alleged he had made several written and verbal requests for a copy of his medical records between 2013 and 2014. The complaint was filed with OCR on November 9, 2017, and the case was closed by OCR on December 15, 2017, after advising Dr. Glaser to investigate the complaint and provide the requested records if the requests were in line with the HIPAA Right of Access. The patient filed a further complaint with OCR on March 20, 2018, and provided evidence of further written requests. OCR tried to contact Dr. Glaser on multiple occasions by letter and phone, but he repeatedly failed to respond, hence the decision to impose a civil monetary penalty.
“Timely access to your health records is a powerful tool in staying healthy, patient privacy and it is your right under law,” said OCR Director Lisa J. Pino. “OCR will continue its enforcement actions by holding covered entities responsible for their HIPAA compliance and pursue civil money penalties for violations that are not addressed.”
The post HHS’ Office for Civil Rights Imposes Further 5 Financial Penalties for HIPAA Right of Access Violations appeared first on HIPAA Journal.