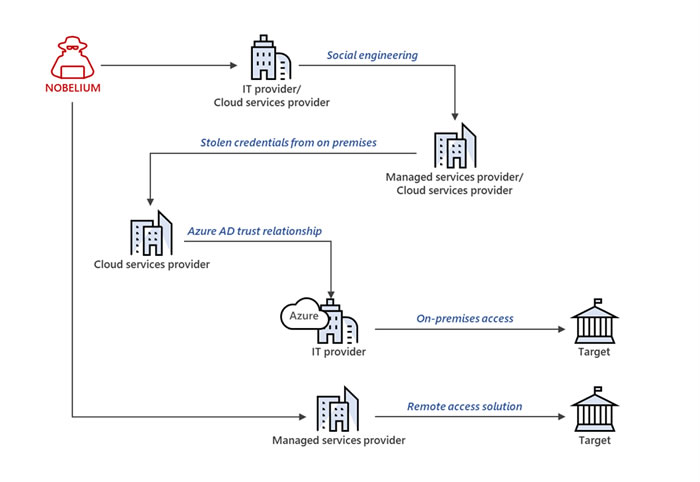
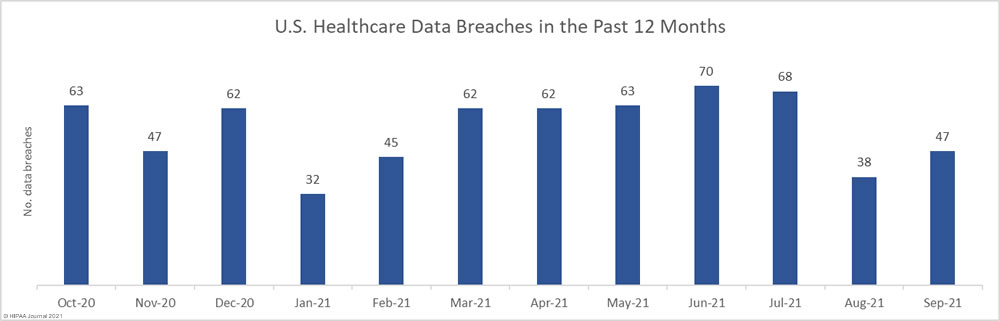
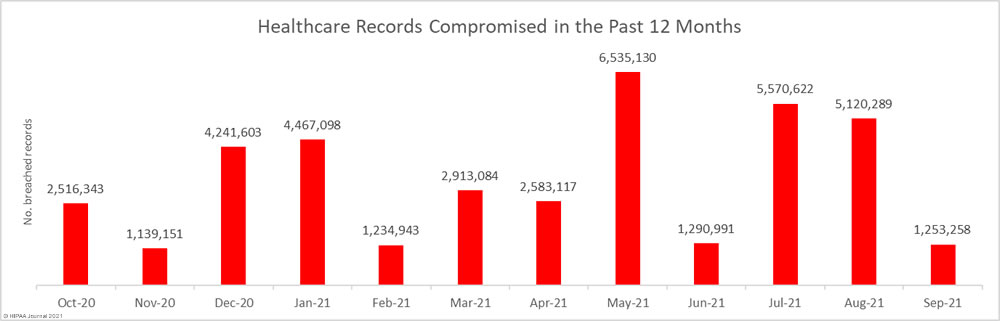
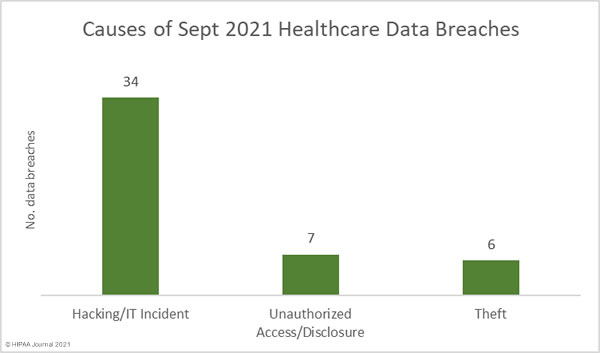
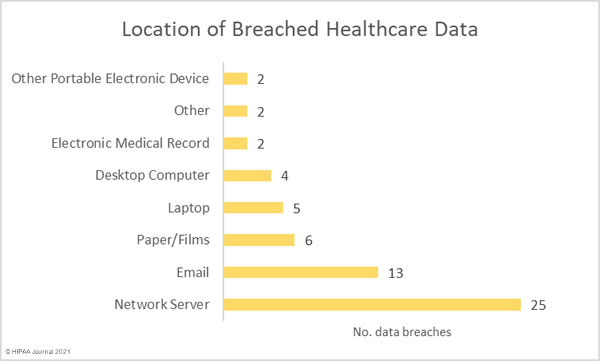
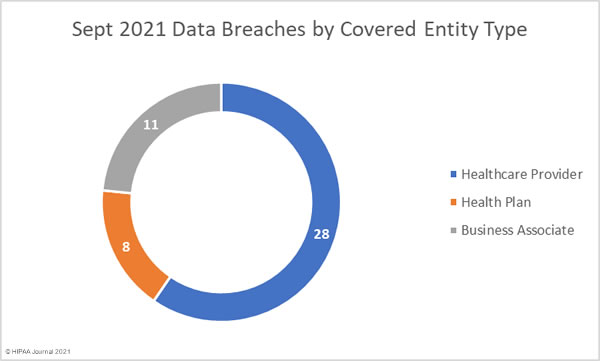
The United States Department of Justice (DoJ) has unsealed indictments charging two individuals for their roles in multiple REvil/Sodinokibi ransomware attacks on organizations in the United States.
Ukrainian national, Yaroslav Vasinskyi, 22, has been indicted on multiple charges related to the ransomware attacks, including the supply chain attack that saw Kaseya’s Virtual System/Server Administrator (VSA) platform compromised. That attack involved ransomware being deployed on the systems of around 40 managed service providers and 1,500 downstream businesses.
Russian national, Yevgeniy Igoryevich Polyanin, 28, has been indicted for his role in multiple ransomware attacks, including attacks on government entities in Texas. The DoJ says it seized $6.1 million in ransom payments that were paid to cryptocurrency wallets linked to Polyanin.
The DoJ has indicted several individuals believed to have been involved in cyberattacks in the United States; however, those individuals can only face trial if they are located, arrested, and extradited to the United States. Many ransomware threat actors are believed to reside in Russia, where there is no extradition treaty, so there is little chance of them facing justice unless they leave Russia.
International arrest warrants have been issued for both individuals and Vasinskyi was arrested in October at the Polish border. Poland signed an extradition treaty with the United States in 1996 and the U.S. is currently seeking Vasinskyi’s extradition. Polyanin has yet to be apprehended.
“Ransomware can cripple a business in a matter of minutes. These two defendants deployed some of the internet’s most virulent code, authored by REvil, to hijack victim computers,” said Acting U.S. Attorney Chad E. Meacham for the Northern District of Texas. “In a matter of months, the Justice Department identified the perpetrators, effected an arrest, and seized a significant sum of money. The Department will delve into the darkest corners of the internet and the furthest reaches of the globe to track down cybercriminals.”
State Department Offers $10 Million Reward for Information on Leaders of REvil and DarkSide Ransomware Operations
Individuals with information about Polyanin, other leaders of the REvil and DarkSide ransomware groups, or affiliates who conducted attacks, are being encouraged to come forward. The U.S. State Department has announced a reward of up to $10 million for information about that leads to the identification or location of leaders of the REvil/DarkSide ransomware groups, with up to $5 million paid for information that leads to the arrest and conviction of any individual who conspired to participate or attempted to participate in a REvil/DarkSide ransomware attacks. The size of the rewards being offered for information clearly shows how focused the United States is on bringing ransomware threat actors to justice.
The pressure being put on ransomware gangs appears to be having some effect. Chris Inglis, U.S. National Cyber Director, recently told House lawmakers that there has been a discernable decrease in Russia-based cyberattacks. and the DoJ says it expects there to be several more arrests in relation to the REvil and DarkSide ransomware attacks in the coming weeks.
Global Law Enforcement Effort Results in Multiple Arrests
The United States is not the only country to be laser-focused on bringing ransomware threat actors to justice. An international law enforcement operation dubbed GoldDust involving 17 nations has recently resulted in the arrest of 7 hackers believed to be involved in the REvil and GandCrab ransomware operations. The Europol, Eurojust, and INTERPOL-coordinated operation saw three individuals arrested in South Korea, two in Romania, one in Kuwait, and one in an unnamed European country, with the latest takedown occurring on November 4 in Romania and Kuwait.
The three individuals in South Korea were previously arrested in February, April, and October for their role in the GandCrab ransomware attacks, which is believed to be the predecessor of REvil/Sodinokibi. The GoldDust operation has been active since 2018 and was launched in response to the GandCrab ransomware attacks.
The previous week, Europol announced 12 individuals had been arrested in raids in Ukraine and Switzerland over their suspected involvement in ransomware attacks involving LockerGoga and other ransomware attacks. Those individuals are believed to have had specialist roles in various stages of the attacks, from infiltration to cashing out and laundering millions in ransom payments.
In September, a French National Gendarmerie, Ukrainian National Police, Europol, and INTERPOL operation resulted in the arrest of 2 individuals suspected to be members of two prolific ransomware operations. That operation also saw $375,000 in cash and luxury vehicles seized, and the asset freezing of $1.3 million in cryptocurrency.
In addition, a 30-month operation, dubbed Operation Cyclone, which involved law enforcement agencies in multiple countries resulted in the arrest of 6 individuals believed to be involved in the Clop ransomware operation, with those arrests occurring in June 2021. The operation saw searches conducted at 20 locations and resulted in the seizure of $185,00 in cash and computer equipment suspected of having been used to conduct the attacks. The Clop ransomware gang had conducted many attacks in the United States, including those on the University of Colorado, Stanford Medicine, University of California, and the University of Maryland Baltimore.
While these arrests will cause some disruption to the activities of ransomware gangs, they represent just a fraction of the individuals involved in ransomware attacks, many of whom can be easily replaced. The core members of the ransomware operations are believed to reside in Russia where they remain untouchable.
The post DOJ Indicts 2 REvil Ransomware Gang Members: State Department Now Offering $10 Million Reward for Information appeared first on HIPAA Journal.