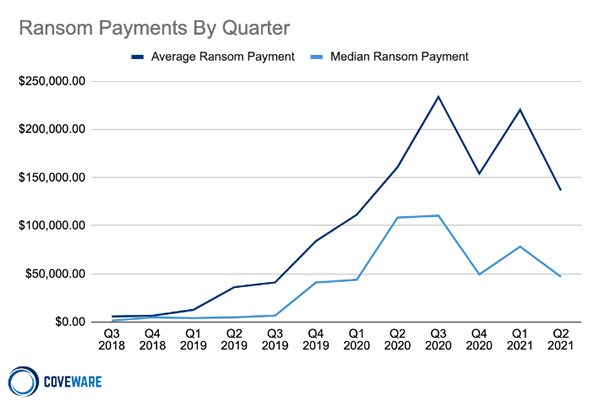
Ransomware attacks dramatically increased in 2020 and cyberattacks using the file-encrypting malware are showing no sign of abating. Attacks have continued to increase this year to the point where there were almost half the number of attempted ransomware attacks in Q2, 2021 as there were all of 2019.
Most threat actors conducting ransomware attacks are now using double extortion tactics, where ransoms must be paid to obtain the keys to decrypt files but also to prevent the publication of data stolen in the attacks. The theft of data prior to file encryption has not only helped ransomware gangs demand huge ransom payments, but the threat of leaking data has greatly increased to probability of the ransom being paid. Many victims end up paying the ransom to prevent data leakage, even though they have valid backups that will allow them to restore the encrypted data for free.
To help public and private sector organizations deal with the threat of these double-extortion ransomware attacks, the Cybersecurity and Infrastructure Security Agency (CISA) has published new guidance, which includes best practices for preventing cyber threat actors from gaining access to networks, steps that can be taken to ensure sensitive data are protected, and procedures that should be followed when responding to a ransomware attack.
“Ransomware is a serious and increasing threat to all government and private sector organizations, including critical infrastructure organizations,” explained CISA in the guidance. “All organizations are at risk of falling victim to a ransomware incident and are responsible for protecting sensitive and personal data stored on their systems.”
There are several measures outlined in the document that are important not only preventing ransomware attacks but also limiting their severity. It is essential to maintain offline, encrypted backups of data and to regularly test the backups to make sure file recovery is actually possible. It is also vital that a basic cyber incident response plan, resiliency plan, and associated communications plan are created and maintained, and exercises are conducted to ensure that a rapid response to an attack is possible. To block attacks, steps must be taken to address the key attack vectors, which are phishing, RDP compromises, and the exploitation of internet-facing vulnerabilities and misconfigurations. Naturally, all organizations should also ensure good cyber hygiene practices are followed.
In order to protect sensitive data, organizations must know where sensitive data reside and who has access to those data repositories. It is also important to ensure that sensitive data are only retained for as long as is strictly necessary. Physical and cybersecurity best practices must be implemented, including restricting access to physical IT assets, encrypting sensitive data at rest and in transit, and to implement firewall and network segmentation to hamper attempts at lateral movement within networks. CISA also recommends ensuring the cyber incident response and communications plans include response and notification procedures for data breach incidents.
A rapid and effective response to a ransomware attack is critical for limiting the harm caused and keeping costs down. The cyber incident response plan should detail all the steps that need to be taken, and the order that they should be taken. The first step is determining which systems have been impacted and immediately isolating them to secure network operations and stop additional data loss. The next step should only be taken if affected devices cannot be removed from the network or the network cannot be temporarily shut down, and that is to power down infected devicesto avoid further spread of the ransomware infection.
Then, triage impacted systems for restoration and recovery, confer with the security team to develop and document an initial understanding of what has occurred, then engage internal and external teams and stakeholders and provide instructions on how they can assist with the response and recovery processes. Organizations should then follow the notification requirements outlined in their cyber incident response plan.
The guidance document – Protecting Sensitive and Personal Information from Ransomware-Caused Data Breaches – can be found on this link.
The post CISA Publishes Guidance on Protecting Sensitive Data and Responding to Double-Extortion Ransomware Attacks appeared first on HIPAA Journal.