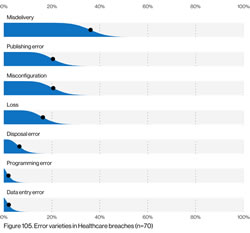
April was another particularly bad month for healthcare data breaches with 62 reported breaches of 500 or – the same number as March 2021. That is more than 2 reported healthcare data breaches every day, and well over the 12-month average of 51 breaches per month.
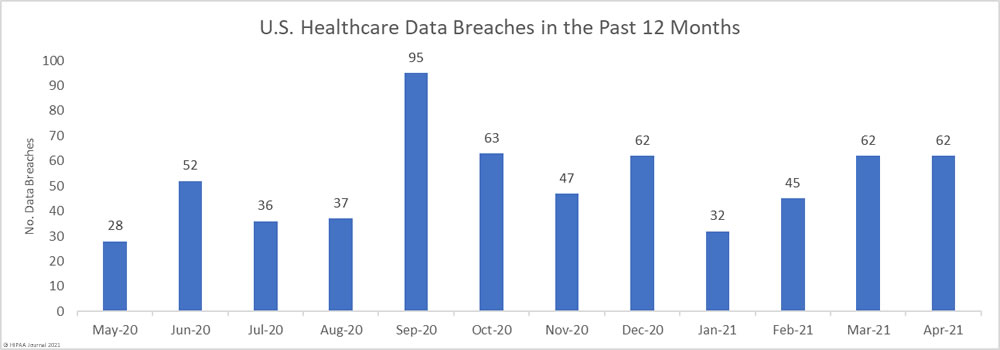
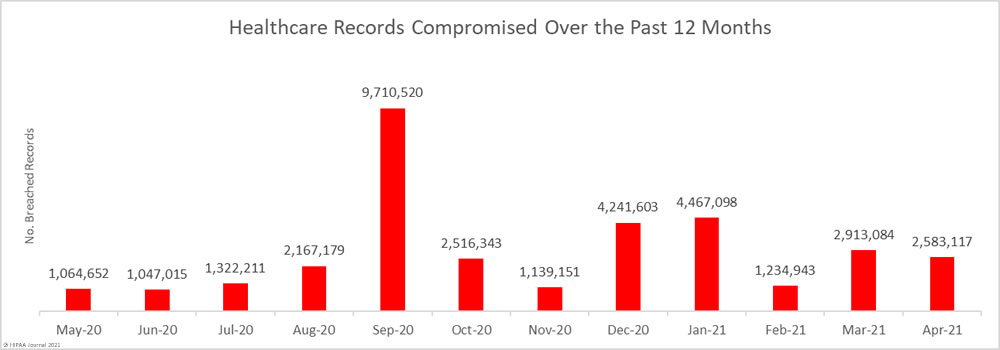
High numbers of healthcare records continue to be exposed each month. Across the 62 breaches, 2,583,117 healthcare records were exposed or compromised; however, it is below the 12-month average of 2,867,243 breached records per month. 34.4 million healthcare records have now been breached in the past 12 months, 11.2 million of which were breached in 2021.
Largest Healthcare Data Breaches Reported in April 2021
There were 19 reported data breaches in April that involved more than 10,000 records, including 7 that involved more than 100,000 records with all but one of the top 10 data breaches due to hacking incidents.
Ransomware attacks continue to occur at high levels, with many of the reported attacks affecting business associates of HPAA-covered entities. These incidents, which include attacks on Netgain Technologies, Accellion, and CaptureRX, have affected multiple healthcare provider clients.
The majority of ransomware attacks now involve data theft prior to file encryption, with the stolen data used as leverage to get breach victims to pay. Large quantities of data are stolen in the attacks. The top three data breaches of the month all involved the use of ransomware and involved 1.3 million healthcare records.
There has been some positive news this month. In the wake of the ransomware attack on Colonial Pipeline, multiple ransomware gangs appear to have ceased operations and at least two have now taken the decision not to attack healthcare organizations. This news should naturally be taken with a large pinch of salt, as similar promises were made by certain ransomware gangs at the start of the pandemic and attacks continued at high levels.
| Name of Covered Entity |
Covered Entity Type |
Business Associate Involvement |
Individuals Affected |
Type of Breach |
Reported Cause of Breach |
| Trinity Health |
Business Associate |
Yes |
586,869 |
Hacking/IT Incident |
Ransomware (Accellion) |
| Bricker & Eckler LLP |
Business Associate |
Yes |
420,532 |
Hacking/IT Incident |
Ransomware |
| Health Center Partners of Southern California |
Business Associate |
Yes |
293,516 |
Hacking/IT Incident |
Ransomware (Netgain Technologies) |
| Total Health Care Inc. |
Health Plan |
No |
221,454 |
Hacking/IT Incident |
Phishing |
| Wyoming Department of Health |
Health Plan |
No |
164,010 |
Unauthorized Access/Disclosure |
Exposure of PHI over Internet |
| Home Medical Equipment Holdco, LLC |
Healthcare Provider |
No |
153,013 |
Hacking/IT Incident |
Phishing |
| Health Aid of Ohio, Inc. |
Healthcare Provider |
No |
141,149 |
Hacking/IT Incident |
Unspecified hacking and data exfiltration attack |
| Woodholme Gastroenterology |
Healthcare Provider |
No |
50,000 |
Hacking/IT Incident |
Unspecified hacking and data exfiltration attack |
| Neighborhood Healthcare |
Healthcare Provider |
Yes |
45,200 |
Hacking/IT Incident |
Ransomware (Netgain Technologies) |
| Crystal Lake Clinic PC |
Healthcare Provider |
No |
37,331 |
Hacking/IT Incident |
Not confirmed |
| RiverSpring Health Plans |
Health Plan |
No |
31,195 |
Hacking/IT Incident |
Phishing |
| Middletown Medical Imaging |
Healthcare Provider |
No |
29,945 |
Hacking/IT Incident |
Exposure of PHI over Internet |
| St. John’s Well Child and Family Center, Inc. |
Healthcare Provider |
No |
29,030 |
Hacking/IT Incident |
Unspecified hacking and data exfiltration attack |
| MailMyPrescriptions.com Pharmacy Corporation |
Healthcare Provider |
No |
24,037 |
Hacking/IT Incident |
Phishing |
| Squirrel Hill Health Center |
Healthcare Provider |
No |
23,869 |
Hacking/IT Incident |
Malware |
| Eastern Shore Rural Health System Inc. |
Healthcare Provider |
Yes |
23,282 |
Unauthorized Access/Disclosure |
Not confirmed |
| Faxton St. Luke’s Healthcare |
Healthcare Provider |
Yes |
17,656 |
Hacking/IT Incident |
Ransomware (CaptureRX) |
| Midwest Transplant Network, Inc. |
Healthcare Provider |
No |
17,580 |
Hacking/IT Incident |
Ransomware |
| Baptist Health Arkansas |
Healthcare Provider |
Yes |
16,765 |
Hacking/IT Incident |
Hacking of business associate (Foley & Lardner, LLP) |
Causes of April 2021 Healthcare Data Breaches
Hacking/IT incidents, which include malware and ransomware attacks, dominated the breach reports in April 2021 and accounted for 67.74% of all reported breaches (42 incidents). These incidents involved 85.93% of all breached records in April. The mean breach size was 52,851 records and the median breach size was 6,563 records.
There were 17 incidents classed as unauthorized access/disclosures involving 358,870 records – 13.89% of all records breached in April. The mean breach size was 21,110 records and the median breach size was 2,704 records.
Loss and theft incidents continue but only at very low levels. There were just two reported cases of theft of devices containing PHI and one loss incident reported. 4,500 records were breached in these 3 incidents.
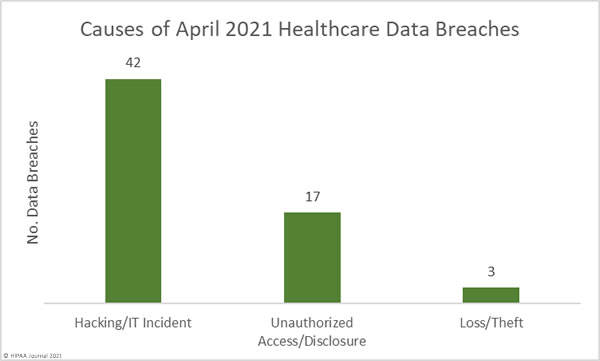
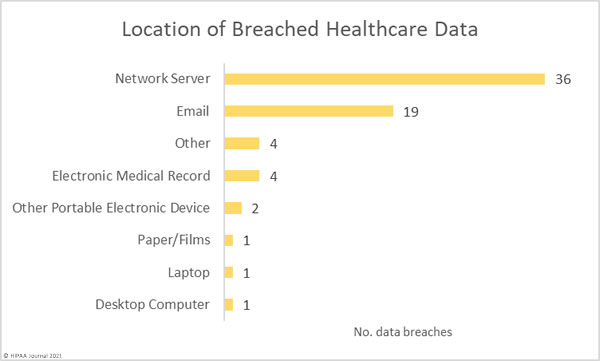
Network server incidents, most of which involved ransomware or malware, have overtaken phishing as the main cause of healthcare data breaches, although it should be noted that phishing emails are often the root cause of many ransomware attacks. There were 19 reported incidents involving PHI in email accounts, the majority of which were due to phishing or other forms of credential theft. One of the largest reported breaches in April was due to phishing and resulted in the exposure and potential theft of the PHI of 221,454 individuals.
According to the Verizon 2021 Data Breach Investigations Report, phishing attacks increased globally by 11% in 2020 and ransomware attacks increased by 6%. The report shows insider breaches in healthcare have continued to fall and are now not even in the top three breach causes. In 2020, 61% of healthcare data breaches were due to external threat actors and 39% were caused by insiders.
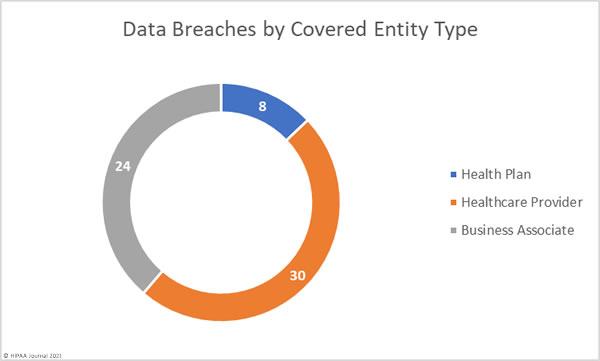
April 2021 Healthcare Data Breaches by Covered Entity Type
Healthcare providers were the worst affected covered entity with 30 data breaches of 500 or more records reported by the provider and a further 13 reported by a vendor. Business associate data breaches continue to be reported at high levels. There were 24 breaches involving business associates, with 10 of those breaches reported by the covered entity. 9 branches were reported by health plans in April, with one breach affecting a health plan reported by its business associate.
States Affected by Healthcare Data Breaches
HIPAA-covered entities and business associates based in 28 states reported breaches of protected health information in April. California was the worst affected state with 7 breaches reported followed by Michigan and Texas with 5 breaches. Florida, New York, and Wisconsin had 4 breaches, and there were 3 reported breaches in Massachusetts and Ohio.
Wyoming, the least populated U.S. state, only had one reported breach, but it affected a quarter of state residents.
| State |
No. Reported Data Breaches |
| California |
7 |
| Michigan and Texas |
5 |
| Florida, New York, & Wisconsin |
4 |
| Massachusetts & Ohio |
3 |
| Georgia, Illinois, Minnesota, Missouri, New Mexico, Pennsylvania, and Vermont |
2 |
| Alabama, Arkansas, Colorado, Kansas, Maryland, Montana, North Carolina, New Hampshire, New Jersey, Oregon, Tennessee, Virginia, & Wyoming |
1 |
HIPAA Enforcement Activity in April 2021
It has been a busy year of HIPAA enforcement by the HHS’ Office for Civil Rights with 6 financial penalties imposed to resolve violations of the HIPAA Rules; however, there were no new settlements or civil monetary penalties announced in April, nor any enforcement actions by state Attorneys General.
The post April 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.