There was a 38.8% increase in reported healthcare data breaches in March. 62 breaches of 500 or more records reported to the HHS’ Office for Civil Rights, with hacking incidents dominating the breach reports. The high number of reported breaches is largely due to an increase in data breaches at business associates.
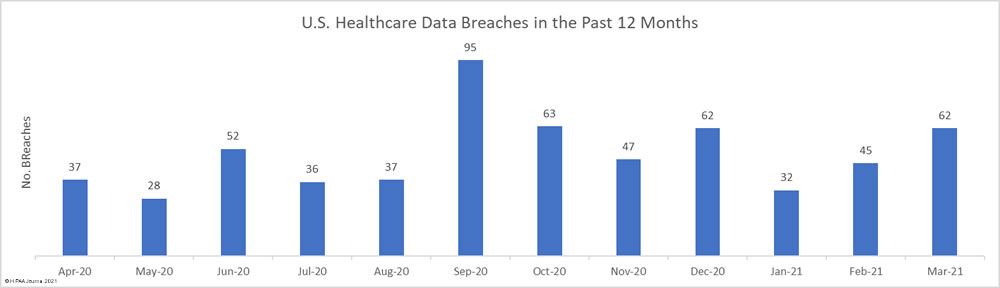
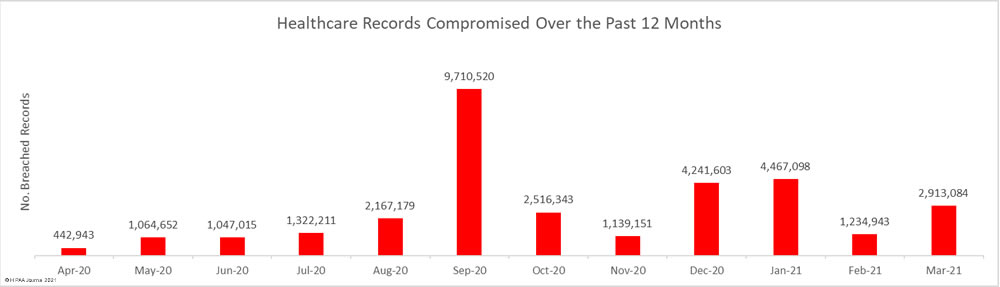
The number of breached records also increased sharply with 2,913,084 healthcare records exposed or impermissibly disclosed across those 62 incidents; an increase of 135.89% from February.
Largest Healthcare Data Breaches Reported in March 2021
The table below shows the 25 largest healthcare data breaches to be reported in March, all of which were hacking/IT incidents. 76% involved compromised network servers with the remaining 24% involving breaches of email accounts. 60% of these breaches involved business associates.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Location of Breached Information |
| Health Net Community Solutions |
Health Plan |
686,556 |
Hacking/IT Incident |
Network Server |
| Health Net of California |
Health Plan |
523,709 |
Hacking/IT Incident |
Network Server |
| Woodcreek Provider Services LLC |
Business Associate |
207,000 |
Hacking/IT Incident |
Network Server |
| Trusted Health Plans, Inc. |
Health Plan |
200,665 |
Hacking/IT Incident |
Network Server |
| Apple Valley Clinic |
Healthcare Provider |
157,939 |
Hacking/IT Incident |
Network Server |
| Saint Alphonsus Health System |
Healthcare Provider |
134,906 |
Hacking/IT Incident |
Email |
| The Centers for Advanced Orthopaedics |
Healthcare Provider |
125,291 |
Hacking/IT Incident |
Email |
| Cancer Treatment Centers of America at Midwestern Regional Medical Center |
Healthcare Provider |
104,808 |
Hacking/IT Incident |
Email |
| SalusCare |
Healthcare Provider |
85,000 |
Hacking/IT Incident |
Email |
| California Health & Wellness |
Health Plan |
80,138 |
Hacking/IT Incident |
Network Server |
| Mobile Anesthesiologists |
Healthcare Provider |
65,403 |
Hacking/IT Incident |
Network Server |
| Trillium Community Health Plan |
Health Plan |
50,000 |
Hacking/IT Incident |
Network Server |
| PeakTPA |
Business Associate |
50,000 |
Hacking/IT Incident |
Network Server |
| Sandhills Medical Foundation, Inc. |
Healthcare Provider |
39,602 |
Hacking/IT Incident |
Network Server |
| ProPath Services, LLC |
Healthcare Provider |
39,213 |
Hacking/IT Incident |
Email |
| BioTel Heart |
Healthcare Provider |
38,575 |
Hacking/IT Incident |
Network Server |
| Healthgrades Operating Company, Inc. |
Business Associate |
35,485 |
Hacking/IT Incident |
Network Server |
| The New London Hospital Association, Inc. |
Healthcare Provider |
34,878 |
Hacking/IT Incident |
Network Server |
| La Clinica de La Raza, Inc. (La Clinica) |
Healthcare Provider |
31,132 |
Hacking/IT Incident |
Network Server |
| Arizona Complete Health |
Health Plan |
27,390 |
Hacking/IT Incident |
Network Server |
| Health Net Life Insurance Company |
Health Plan |
26,637 |
Hacking/IT Incident |
Network Server |
| Colorado Retina Associates, P.C. |
Healthcare Provider |
26,609 |
Hacking/IT Incident |
Email |
| Haven Behavioral Healthcare |
Business Associate |
21,714 |
Hacking/IT Incident |
Network Server |
| Health Prime International |
Business Associate |
17,562 |
Hacking/IT Incident |
Network Server |
| CalViva Health |
Health Plan |
15,287 |
Hacking/IT Incident |
Network Server |
Causes of March 2021 Healthcare Data Breaches
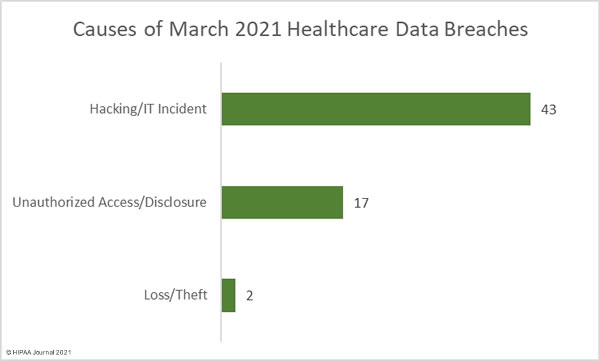
43 breaches – 69.35% of the month’s total – were the result of hacking/IT incidents such as compromised network servers and email accounts. Hacking incidents accounted for 98.43% of all records breached in March – 2,867,472 records. The average breach size was 66,685 records and the median breach size was 26,609 records. 17 unauthorized access/disclosure incidents were reported in March (27.42% of breaches) and 44,395 records were breached in those incidents – 1.52% of the month’s total. The average breach size was 2,611 records and the median breach size was 1,594 records. There was one theft incident reported involving 500 healthcare records and one loss incident that affected 717 individuals.
Many of the reported breaches occurred at business associates of HIPAA covered entities, with those breaches impacting multiple healthcare clients. Notable business associate data breaches include a cyberattack on Accellion that affected its file transfer appliance. Hackers exploited vulnerabilities in the appliance and stole client files. A ransom was demanded by the attackers and threats were issued to publish the stolen data if payment was not made. The two largest data breaches of the month were due to this incident.
Several healthcare organizations were affected by a ransomware attack on business associate Netgain Technology LLC, including the 3rd and 5th largest breaches reported in March. Med-Data suffered a breach that affected at least 5 covered entities. This incident involved an employee uploading files containing healthcare data to a public facing website (GitHub).
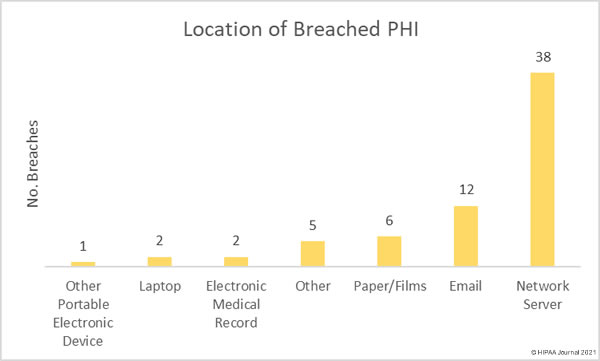
The most common location of breached protected health information was network servers, many of which were due to ransomware attacks or other malware infections. Email accounts were the second most common location of breached PHI, which were mostly accessed following responses to phishing emails.
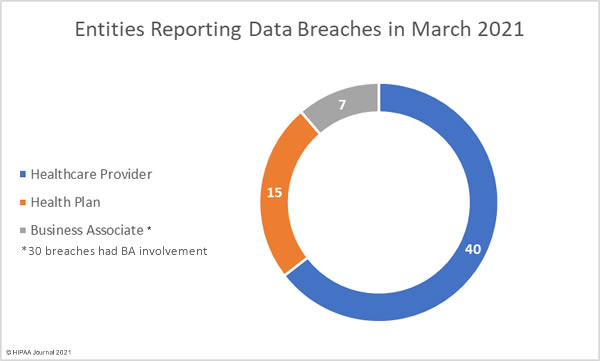
Covered Entities Reporting Data Breaches in March 2021
Healthcare providers were the worst affected covered entity with 40 reported breaches and 15 breaches were reported by health plans, with the latter increasing 200% from the previous month. While only 5 data breaches were reported by business associates of covered entities, 30 of the month’s breaches – 48.39% – involved business associates but were reported by the covered entity. That represents a 200% increase from February.
Distribution of March 2021 Healthcare Data Breaches
There was a large geographical spread of data breaches, with covered entities and business associates in 30 states affected. California was the worst affected state with 11 data breaches reported. There were 5 breaches reported in Texas, 4 in Florida and Massachusetts, 3 in Illinois and Maryland, 2 in each of Arkansas, Arizona, Michigan, Minnesota, Missouri, Ohio, and Pennsylvania, and one breach was reported in each of Alabama, Colorado, Connecticut, Georgia, Idaho, Kansas, Louisiana, Montana, New Hampshire, Nevada, Oregon, South Carolina, Tennessee, Utah, Washington, Wisconsin, and West Virginia.
HIPAA Enforcement Activity in March 2021
The HHS’ Office for Civil Rights announced two further settlements to resolve HIPAA violations in March, both of which involved violations of the HIPAA Right of Access. These two settlements bring the total number of financial penalties under OCR’s HIPAA Right of Access enforcement initiative to 18.
Arbour Hospital settled its case with OCR and paid a $65,000 financial penalty and Village Plastic Surgery settled its case and paid OCR $30,000. Both cases arose from complaints from patients who had not been provided with timely access to their medical records.
The post March 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.





