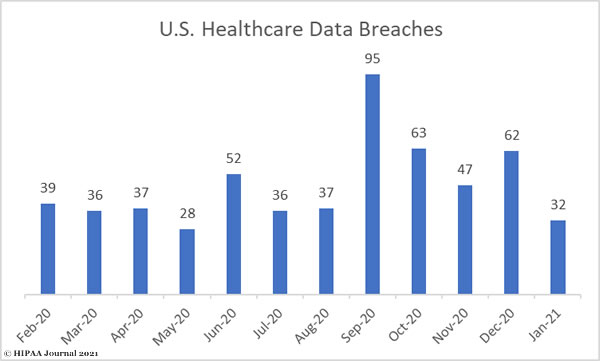
January saw a 48% month-over-month reduction in the number of healthcare data breaches of 500 or more records, falling from 62 incidents in December to just 32 in January. While this is well below the average number of data breaches reported each month over the past 12 months (38), it is still more than 1 data breach per day.
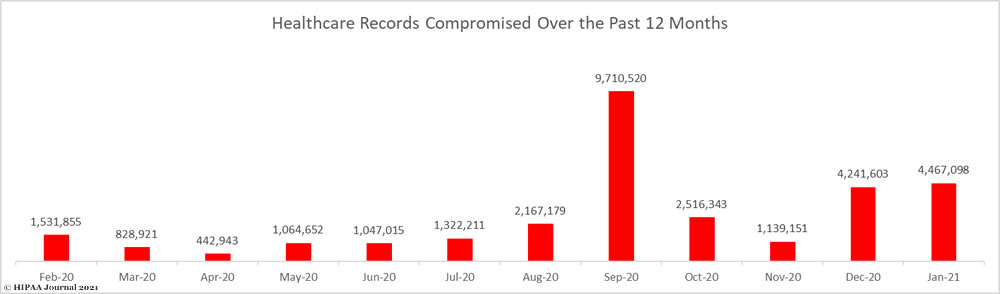
There would have been a significant decline in the number of breached records were it not for a major data breach discovered by Florida Healthy Kids Corporation that affected 3.5 million individuals. With that breach included, 4,467,098 records were reported as breached in January, which exceeded December’s total by more than 225,000 records.
Largest Healthcare Data Breaches Reported in January 2021
The breach reported by Florida Healthy Kids Corporation was one of the largest healthcare data breaches of all time. The breach was reported by the health plan, but actually occurred at one of its business associates. The health plan used an IT company for hosting its website and an application for applications for insurance coverage. The company failed to apply patches for 7 years, which allowed unauthorized individuals to exploit the flaws and gain access to sensitive data.
Hendrick Health had a major data breach due to a ransomware attack; one of many reported by healthcare providers since September 2020 when ransomware actors stepped up their attacks on the healthcare sector. The County of Ramsey breach was also due to a ransomware attack at one of its technology vendors.
Email-based attacks such as business email compromise (BEC) and phishing attacks were common in January, and were the cause of 4 of the top ten breaches.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Location of Breached Information |
| Florida Healthy Kids Corporation |
Health Plan* |
3,500,000 |
Hacking/IT Incident:
Website and Web Application Hack |
Network Server |
| Hendrick Health |
Healthcare Provider |
640,436 |
Hacking/IT Incident:
Ransomware |
Network Server |
| Roper St. Francis Healthcare |
Healthcare Provider |
189,761 |
Hacking/IT Incident:
Phishing attack |
Email |
| Precision Spine Care |
Healthcare Provider |
20,787 |
Hacking/IT Incident:
BEC attack |
Email |
| Walgreen Co. |
Healthcare Provider |
16,089 |
Unauthorized Access/Disclosure:
Unknown |
Email |
| The Richards Group |
Business Associate |
15,429 |
Hacking/IT Incident:
Phishing attack |
Email |
| Florida Hospital Physician Group Inc. |
Healthcare Provider |
13,759 |
Hacking/IT Incident:
EHR System |
Electronic Medical Record |
| Managed Health Services |
Health Plan* |
11,988 |
Unauthorized Access/Disclosure:
Unconfirmed |
Paper/Films |
| Bethesda Hospital |
Healthcare Provider |
9,148 |
Unauthorized Access of EMR by employee |
Electronic Medical Record |
| County of Ramsey |
Healthcare Provider* |
8,687 |
Hacking/IT Incident:
Ransomware |
Network Server |
*Breach reported by covered entity but occurred at a business associate.
Causes of January 2021 Healthcare Data Breaches
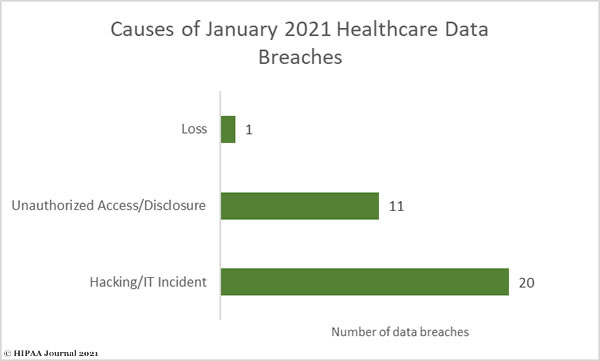
Hacking and other IT incidents continue to cause the majority of healthcare data breaches. January saw 20 hacking/IT incidents reported, which accounted for 62.5% of the month’s data breaches. The protected health information of 4,413,762 individuals was compromised or exposed in those breaches – 98.8% of all breached records in January. The average breach size was 220,688 records and the median breach size was 2,464 records.
There were 11 reported unauthorized access and disclosure incidents involving 50,996 records. The average breach size was 4,636 records and the median breach size was 1,680 records.
There was one reported incident involving the loss of an unencrypted laptop computer containing 2,340 records, but no theft or improper disposal incidents.
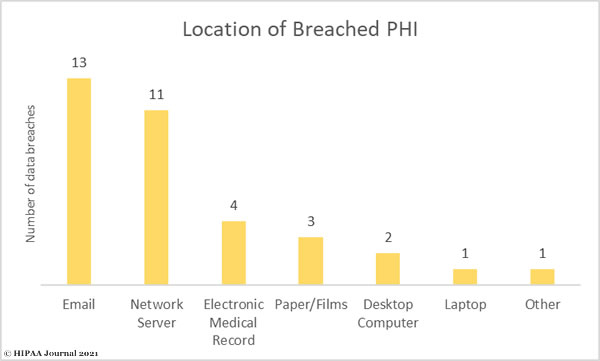
As the bar chart below shows, email is the most common location of breached PHI, mostly due to the high number of phishing attacks. This was closely followed by network server incidents, which mostly involve malware or ransomware.
January 2021 Healthcare Data Breaches by Entity Type
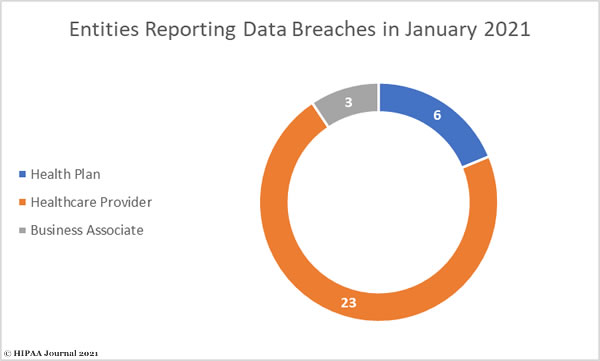
Healthcare providers were the worst affected covered entity type with 23 reported data breaches followed by health plans with 6 reported breaches. Three data breaches were reported by business associates of HIPAA covered entities, although a further 7 occurred at business associates but were reported by the covered entity, including the largest data breach of the month.
The number of breaches reported by business associates have been increasing in recent months. These incidents often involve multiple covered entities, such as the data breach at Blackbaud in 2020 which resulted involved the data of more than 10 million individuals across around four dozen healthcare organizations. A study by CI Security found 75% of all breached healthcare records in the second half of 2020 were due to data breaches at business associates.
Where Did the Data Breaches Occur?
January’s 32 data breaches were spread across 18 states, with Florida the worst affected with 6 reported breaches. There were 3 breaches reported by entities in Texas and Wyoming, and 2 reported in each of Louisiana, Massachusetts, and Minnesota.
Illinois, Indiana, Maryland, Missouri, Nevada, North Carolina, Ohio, Pennsylvania, South Carolina, Vermont, Virginia, and Washington each had 1 breach reported.
HIPAA Enforcement Activity in January 2021
2020 was a record year for HIPAA enforcement actions with 19 settlements reached to resolve HIPAA cases, and the enforcement actions continued in January with two settlements reached with HIPAA covered entities to resolve violations of the HIPAA Rules.
Excellus Health Plan settled a HIPAA compliance investigation that was initiated following a report of a breach of 9,358,891 records in 2015. OCR investigators identified multiple potential violations of the HIPAA Rules, including a risk analysis failure, risk management failure, lack of information system activity reviews, and insufficient technical policies to prevent unauthorized ePHI access. Excellus Health Plan settled the case with no admission of liability and paid a $5,100,000 financial penalty.
OCR continued with its crackdown of noncompliance with the HIPAA Right of Access with a $200,000 financial penalty for Banner Health. OCR found two Banner Health affiliated covered entities had failed to provide a patient with timely access to medical records, with both patients having to wait several months to receive their requested records.
The post January 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.