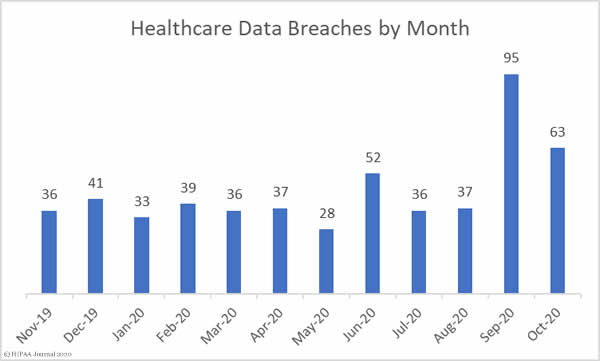
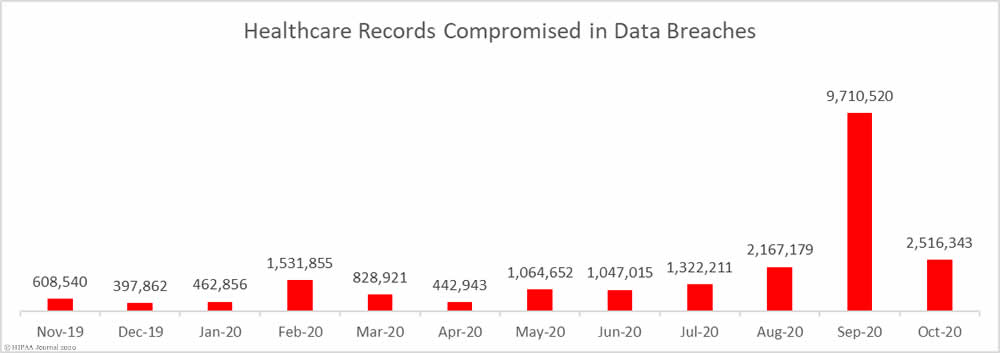
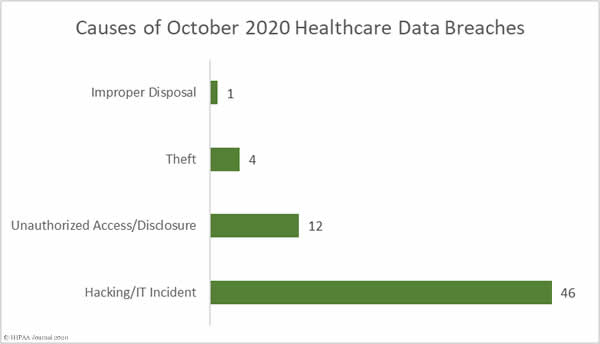
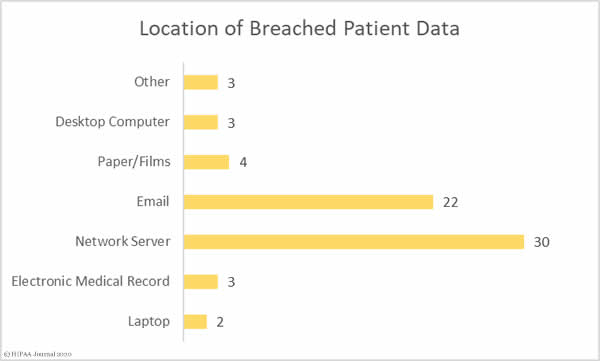
The Department of Health and Human Services has issued a notice of proposed rulemaking detailing multiple HIPAA Privacy Rule changes that are intended to remove regulatory burdens, improve care coordination, and give patients better access to their protected health information (PHI).
OCR issued a request for public input on potential HIPAA Privacy Rule changes in December 2018 under the HHS’ Regulatory Sprint to Coordinated Care. The regulatory sprint was intended to accelerate transformation of the healthcare system and remove some of the barriers that have hampered the coordination of care, were making it difficult for healthcare providers to share patient information and placed an unnecessary burden on patients and their families who were trying to get their health information exchanged. In response to the request for information, the HHS received around 1,300 comments spanning 4,000 pages. The HHS has had to strike a balance between providing more flexibility to allow health information to be shared easily and ensuring the privacy and security of healthcare data.
“Our proposed changes to the HIPAA Privacy Rule will break down barriers that have stood in the way of commonsense care coordination and value-based arrangements for far too long,” said HHS Secretary Alex Azar. “As part of our broader efforts to reform regulations that impede care coordination, these proposed reforms will reduce burdens on providers and empower patients and their families to secure better health.”
HIPAA was initially signed into law in 1996 and the Privacy Rule took effect in 2003, prior to widespread adoption of electronic medical records and before many online and mobile services were available. The proposed updates are intended to remove some of the barriers to digital health, with definitions added for terms such as electronic health records and personal health applications.
Strengthening Patients’ Rights to their Own Healthcare Data
The HIPAA Privacy Rule gave patients the right to access their own healthcare data. The proposed changes will see those rights strengthened with regard to electronic protected health information (ePHI) and inspecting PHI in person. Individuals will be permitted to take notes and use personal resources to view and capture images of their own PHI, such as taking photographs of their own medical records and medical images. The time frame for providing patients with access to their own PHI has been shortened from 30 days to 15 days from the date of request and the identity verification burden on individuals has been eased.
Disclosures to Telecommunication Relay Services (TRS), which are used by the deaf and hard of hearing, are expressly permitted and TRS providers have been excluded from the definition of business associate.
The HHS has specified when ePHI must be provided to individuals at no cost – such as when ePHI is provided through online patient portals – and the permissible fee structure has been amended for responding to requests to direct healthcare records to a third party.
The HHS has also created a pathway for individuals to direct the sharing of ePHI in an EHR among covered health care providers and health plans. Covered entities will also be required to publish estimated fee structures on their websites for providing access to PHI and copies of PHI, as well as provide individuals with itemized bills for completed requests.
Improving Coordination of Care and Reducing the Administrative Burden
Several changes have been proposed to improve information sharing for care coordination and case management for individuals, which will make it easier for hospitals and physician practices to share patient information with other healthcare providers and social service and caregiving agencies.
If patients give their authorization for their healthcare provider or doctor to see their medical records from another healthcare provider, it will be the healthcare provider or doctor’s office that will be responsible for getting that information rather than the patient.
The privacy standard that permitted covered entities to make disclosures based on their professional judgement has been changed to permit uses and disclosures based on a covered entity’s good faith belief that a use or disclosure is in the best interests of the patient, which is more permissive.
Changes have also been proposed to remove the administrative burden on healthcare providers, such as long-awaited removal of the requirement to have patients sign a notice of privacy practices, instead they will only need to be provided with a notice of privacy practices. This change alone is expected to save the healthcare industry an estimated $3.2 billion over five years.
Changes have been proposed to improve the sharing of healthcare data in crises and emergencies. Currently, the HIPAA Privacy Rule permits covered entities to disclose patient health information to avert a serious and imminent threat to health or patient safety. The wording has been changed to avert threats when harm is ‘serious and reasonably foreseeable’. The change would make it easier for healthcare providers to share information when individuals have stated they are contemplating suicide, for instance, and would improve care coordination in emergencies such as the opioid and COVID-19 public health emergencies.
Commonsense, Bipartisan HIPAA Privacy Rules Changes
“Today’s announcement is a continuation of our ongoing work under my Regulatory Sprint to Coordinated Care to eliminate unnecessary regulatory barriers blocking patients from getting better care,” said HHS Deputy Secretary Eric Hargan. “These proposed changes reduce burden on providers and support new ways for them to innovate and coordinate care on behalf of patients, while ensuring that we uphold HIPAA’s promise of privacy and security.”
The HHS is accepting comments from all healthcare industry stakeholders, including patients and their families, healthcare providers, health plans, business associates, health IT vendors and government entities. Comments must be submitted within 60 days of the publication of the notice of proposed rulemaking in the Federal Register.
With President-Elect Biden due to take office in January, it is likely there will be significant amendments to the proposed HIPAA Privacy Rule changes; however, many of the updates have been proposed to address issues that have been proving problematic for hospitals, doctors, and patients for many years and are non-partisan, commonsense changes. HHS officials hope the incoming administration will understand the need for these HIPAA Privacy Rule changes and will provide the support to ensure they are implemented.
You can view the proposed 2020 HIPAA Privacy Rule changes on this link (PDF).
The post HIPAA Privacy Rule Changes Proposed to Improve Care Coordination and Patient Rights appeared first on HIPAA Journal.