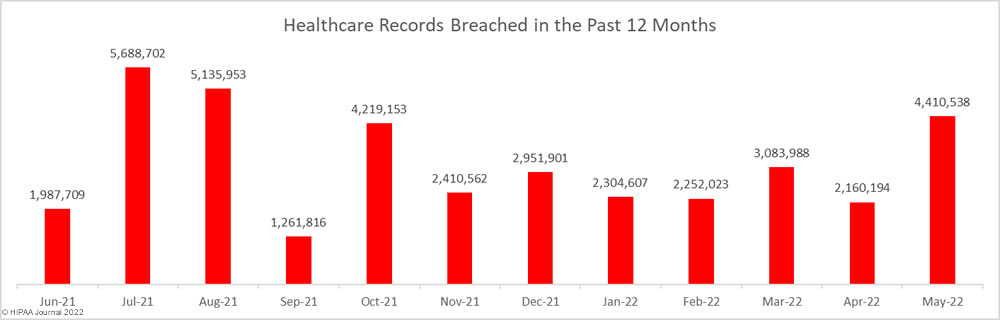
May 2022 saw a 25% increase in healthcare data breaches of 500 or more records. 70 data breaches of 500 or more records were reported to the Department of Health and Human Services’ Office for Civil Rights (OCR) in May 2022, which is the highest monthly total this year and well above the 12-month average of 56.75 data breaches per month. This level of reported data breaches has not been seen since June 2021.

Across those data breaches, the records of 4,410,538 individuals were exposed, stolen, or impermissibly disclosed, which is more than twice the number of records that were breached in April, and almost 40% higher than the average number of records breached each month over the past 12 months.
Largest Healthcare Data Breaches Reported in May 2022
In May 2022, there were 31 reports of healthcare data breaches that involved the records of more than 10,000 individuals. The largest breach to be reported affected the HIPAA business associate, Shields Health Care Group, which provides MRI and other imaging services in New England. The exact nature of the attack was not disclosed, but Shields said hackers accessed its network and exfiltrated files containing patient data. The breach affected 2 million patients who received medical services at 52 facilities in New England.
Partnership HealthPlan of California also reported a major data breach, in this case, a ransomware attack. Hackers gained access to systems containing the records of 854,913 current and former health plan members. The Hive ransomware gang claimed responsibility for the attack and allegedly stole 400GB of data.
The number of eye care providers affected by a hacking incident at the electronic health record vendor Eye Care Leaders continued to grow throughout May (and June). While they are not all reflected in the May data, as of June 21, at least 23 eye care providers are known to have been affected, and the data breach has affected at least 2,187,383 patients.
Data Breaches of over 10,000 Records Reported in May 2022
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Business Associate Breach |
Cause of Data Breach |
| Shields Health Care Group, Inc. |
MA |
Business Associate |
2,000,000 |
Hacking/IT Incident |
Yes |
Hacking and data theft incident |
| Partnership HealthPlan of California |
CA |
Health Plan |
854,913 |
Hacking/IT Incident |
No |
Ransomware attack |
| SAC Health System |
CA |
Healthcare Provider |
149,940 |
Theft |
No |
Theft of documents in break-in at storage facility |
| Aon PLC |
IL |
Business Associate |
119,636 |
Hacking/IT Incident |
Yes |
Hacking and data theft incident |
| Parker-Hannifin Corporation Group Health Plans |
OH |
Health Plan |
119,513 |
Hacking/IT Incident |
No |
Hacking and data theft incident |
| Heidell, Pittoni, Murphy & Bach, LLP |
NY |
Business Associate |
114,979 |
Hacking/IT Incident |
Yes |
Ransomware attack |
| Schneck Medical Center |
IN |
Healthcare Provider |
92,311 |
Hacking/IT Incident |
No |
Hacking and data theft incident |
| Alameda Health System |
CA |
Healthcare Provider |
90,000 |
Hacking/IT Incident |
No |
Unauthorized access to email accounts |
| Val Verde Regional Medical Center |
TX |
Healthcare Provider |
86,562 |
Hacking/IT Incident |
No |
Ransomware attack |
| NuLife Med, LLC |
NH |
Healthcare Provider |
81,244 |
Hacking/IT Incident |
No |
Hacking and data theft incident |
| Comstar, LLC |
MA |
Business Associate |
68,957 |
Hacking/IT Incident |
Yes |
Unspecified hacking incident |
| Shoreline Eye Group |
CT |
Healthcare Provider |
57,047 |
Hacking/IT Incident |
Yes |
Eye Care Leaders hacking incident |
| AU Health |
GA |
Healthcare Provider |
50,631 |
Hacking/IT Incident |
Yes |
Eye Care Leaders hacking incident |
| Finkelstein Eye Associates |
IL |
Healthcare Provider |
48,587 |
Hacking/IT Incident |
Yes |
Eye Care Leaders hacking incident |
| Oklahoma City Indian Clinic |
OK |
Healthcare Provider |
38,239 |
Hacking/IT Incident |
No |
Ransomware attack |
| Moyes Eye Center, PC |
MO |
Healthcare Provider |
38,000 |
Hacking/IT Incident |
Yes |
Eye Care Leaders hacking incident |
| Family Health Care, Inc |
KS |
Healthcare Provider |
33,619 |
Hacking/IT Incident |
No |
Unspecified hacking incident |
| Allwell Behavioral Health Services |
OH |
Healthcare Provider |
29,972 |
Hacking/IT Incident |
No |
Hacking and data theft incident |
| Creative Hospice Care, Inc. dba Homestead Hospice & Palliative Care |
GA |
Healthcare Provider |
28,332 |
Hacking/IT Incident |
No |
Unauthorized access to email accounts |
| FPS Medical Center |
AZ |
Healthcare Provider |
28,024 |
Hacking/IT Incident |
No |
Ransomware attack |
| Capsule |
NY |
Healthcare Provider |
27,486 |
Hacking/IT Incident |
No |
Unauthorized access to user accounts |
| McKenzie Health System |
MI |
Healthcare Provider |
25,318 |
Hacking/IT Incident |
No |
Hacking and data theft incident |
| Sylvester Eye Care |
OK |
Healthcare Provider |
19,377 |
Hacking/IT Incident |
Yes |
Eye Care Leaders hacking incident |
| Aesto, LLC d/b/a Aesto Health |
AL |
Business Associate |
17,400 |
Hacking/IT Incident |
Yes |
Hacking and data theft incident |
| Vail Health Services |
CO |
Healthcare Provider |
17,039 |
Hacking/IT Incident |
No |
Ransomware attack |
| Motion Picture Industry Health Plan |
CA |
Health Plan |
16,838 |
Unauthorized Access/Disclosure |
No |
Mismailing incident |
| Bryan County Ambulance Authority |
OK |
Healthcare Provider |
14,273 |
Hacking/IT Incident |
No |
Ransomware attack |
| Associated Ophthalmologists of Kansas City, P.C. |
MO |
Healthcare Provider |
13,461 |
Hacking/IT Incident |
No |
Eye Care Leaders hacking incident |
| Allaire Healthcare Group |
NJ |
Healthcare Provider |
13,148 |
Hacking/IT Incident |
No |
Unauthorized access to user accounts |
| EmblemHealth Plan, Inc. |
NY |
Health Plan |
11,399 |
Unauthorized Access/Disclosure |
No |
Unconfirmed |
| Behavioral Health Partners of Metrowest, LLC |
MA |
Business Associate |
11,288 |
Hacking/IT Incident |
Yes |
Hacking and data theft incident |
Causes of May 2022 Healthcare Data Breaches
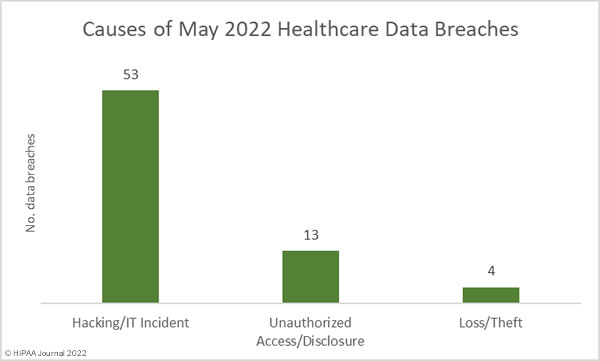
Hacking incidents continue to be reported in high numbers in May, with 53 (75.7%) of the month’s data breaches classed as hacking or other IT incidents. That represents a 77% increase in incidents compared to April. Those incidents accounted for 95.5% of the records breached in May (4,212,721 records), which is more than twice the number of records exposed in hacking incidents in April. The average breach size was 79,485 records and the median breach size was 13,148 records.
There were 13 unauthorized access/disclosure incidents reported in May – a slight increase from April. Across those incidents, 43,807 records were impermissibly disclosed. The average breach size was 3,370 records and the median breach size was 1,196 records.
There were three theft incidents reported and one incident involving the loss of paper/films. These breaches involved a total of 154,010 records, with an average breach size of 35,503 records and a median breach size of 1,771 records.
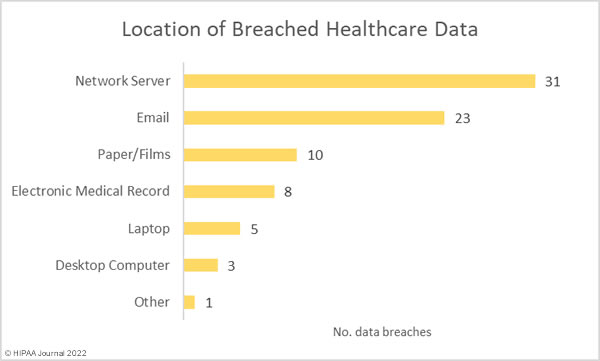
With so many hacking incidents, it is unsurprising that 31 of the month’s data breaches involved protected health information stored on network servers. The high number of breaches of electronic health records was due to the cyberattack on Eye Care Leaders. As the chart below shows, email account breaches were reported in high numbers in May, 70% more incidents than in April. While security awareness training for the workforce and multi-factor authentication will not prevent all email data breaches, they can significantly improve protection.
HIPAA-Regulated Entities Affected by Data Breaches
Healthcare providers were the hardest hit HIPAA-covered entity type in May, with 49 reported breaches. There were 11 data breaches reported by health plans, and business associates of HIPAA-covered entities reported 10 breaches; however, 8 data breaches occurred at business associates but were reported by the covered entity. The data breaches detailed in the chart below reflect where the data breach occurred.
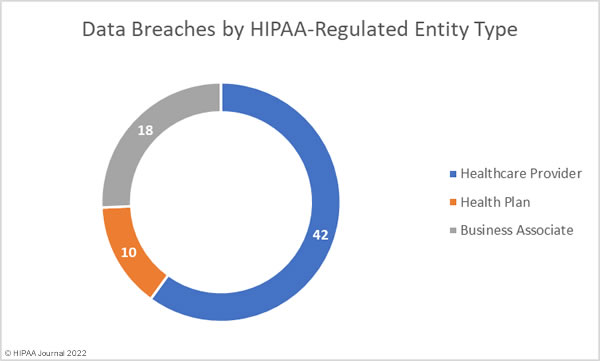
Healthcare providers suffered the highest number of data breaches, but business associates topped the list in terms of the number of exposed healthcare records.
|
HIPAA-Regulated Entity
|
Number of Reported Data Breaches |
Total Records Exposed |
|
Business Associate
|
18
|
2,554,789
|
|
Health Plan
|
10 |
1,014,150
|
| Healthcare Provider |
42 |
841,599
|
May 2022 Healthcare Data Breaches by State
Data breaches of 500 or more healthcare records were reported by HIPAA-regulated entities in 29 states. California was the worst affected state with 8 large healthcare data breaches reported, followed by New York with 6 reported breaches.
| State |
No. Reported Data Breaches |
| California |
8 |
| New York |
6 |
| Georgia, Missouri & Ohio |
4 |
| Alabama, Illinois, Massachusetts, North Carolina, Oklahoma & Texas |
3 |
| Arizona, Connecticut, Florida, Maryland, Michigan, New Hampshire, Virginia & Washington |
2 |
| Colorado, Indiana, Kansas, Minnesota, Mississippi, Montana, New Jersey, Nevada, Tennessee & Wisconsin |
1 |
HIPAA Enforcement Activity in May 2022
No HIPAA enforcement actions were announced by the HHS’ Office for Civil Rights or state Attorneys General in May. So far this year, 4 financial penalties totaling $170,000 have been imposed by OCR to resolve HIPAA violations.
The post May 2022 Healthcare Data Breach Report appeared first on HIPAA Journal.




