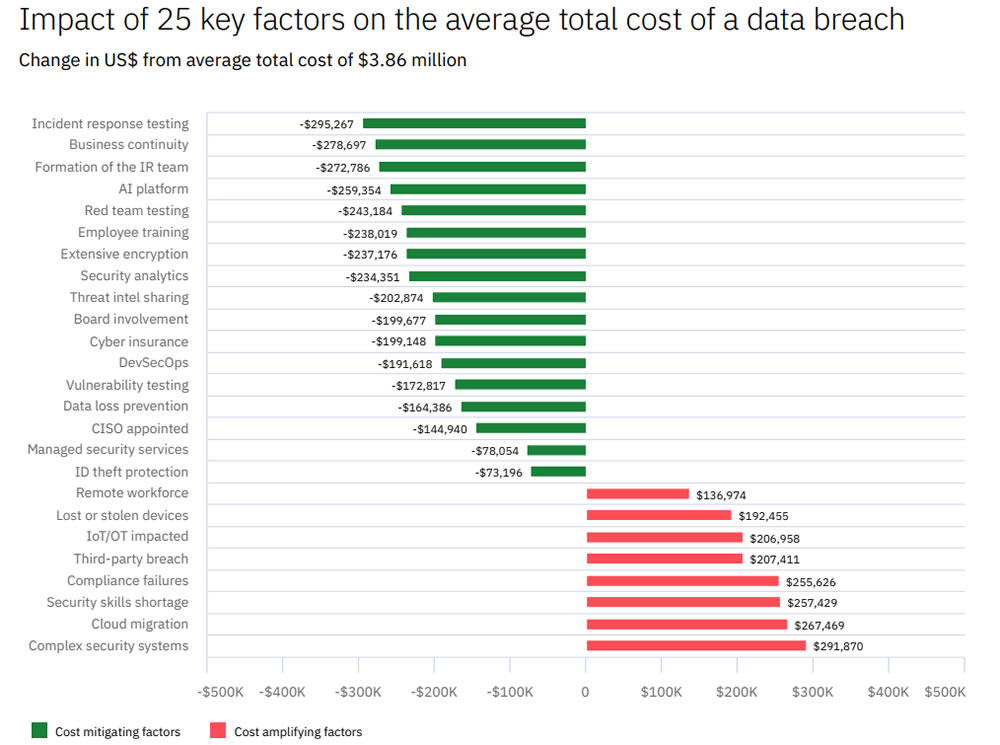
The FBI Cyber Division has issued a Private Industry Notification advising enterprises still using Windows 7 within their infrastructure to upgrade to a supported operating system due to the risk of security vulnerabilities in the Windows 7 operating system being exploited.
The FBI has observed an increase in cyberattacks on unsupported operating systems once they reach end-of-life status. Any organization that is still using Windows 7 on devices faces an increased risk of cybercriminals exploiting vulnerabilities in the operating system to remotely gain network access. “As time passes, Windows 7 becomes more vulnerable to exploitation due to lack of security updates and new vulnerabilities discovered,” warned the FBI.
The Windows 7 operating system reached end-of-life on January 14, 2020 and Microsoft stopped releasing free patches to correct known vulnerabilities. Microsoft is only providing security updates for Windows 7 Professional, Windows 7 Enterprise, and Windows 7 Ultimate if users sign up for the Extended Security Update (ESU) program. The ESU program will only run until January 2023, and the cost of continued support increases the longer a customer participates in the program. While security updates are being released for customers that have signed up for the ESU program, the FBI and Microsoft strongly advise users of Windows 7 to upgrade to Windows 10 or a fully supported operating system.
Updating an operating system is not without its challenges. New devices may need to be purchased and new software comes at a cost, but the cost will be negligible compared to the cost of the loss of intellectual properly and threats to an organization from the continued use of an operating system that is no longer supported.
Many organizations around the world are still using Windows 7 on at least some of their Windows devices. Data from Statcounter indicates around 20% of all Windows devices are still running Windows 7, even though free security updates are no longer being issued. An open source report published in May 2019 found that 71% of Windows devices used in healthcare were using Windows 7 or other operating systems that became unsupported in January 2020.
The FBI warned that increases in successful cyberattacks have been observed in healthcare when operating systems have reached end of life. When support for Windows XP ended on April 28, 2014, the industry saw a large increase in the number of exposed and compromised healthcare records the following year.
The FBI explained that cybercriminals are continuing to search for entry points into legacy Windows operating systems in order to leverage Remote Desktop Protocol (RDP) exploits. In May 2019, following the discovery of the BlueKeep vulnerability, Microsoft released patches for all supported operating systems and also a patch for Windows XP and other unsupported operating systems in order to prevent a WannaCry-style attack. Since the vulnerability was discovered, working exploits have been developed to exploit the flaw and are still being used to attack unpatched Windows devices.
Vulnerabilities will be found and exploited on unpatched systems. When Microsoft released the MS17-010 patch to address several SMBv1 vulnerabilities in March 2017, many organizations were slow to apply the patch, even though there was a high risk exploitation. The WannaCry ransomware attacks exploiting the flaws started in May 2017. 98% of systems infected with WannaCry were running Windows 7.
“With fewer customers able to maintain a patched Windows 7 system after its end of life, cybercriminals will continue to view Windows 7 as a soft target” warned the FBI.
When organizations use an actively supported operating system, patches are automatically made available to fix newly discovered security vulnerabilities. Upgrading to a supported operating system is one of the most important steps to take to improve security.
“Defending against cyber criminals requires a multilayered approach, including validation of current software employed on the computer network and validation of access controls and network configurations,” explained the FBI in the alert.
In addition to upgrading the operating system and applying patches promptly, organizations should ensure antivirus software is installed, spam filters are used, and firewalls should be implemented, properly configured, and kept up to date.
Network configurations should be audited and any computer systems that cannot be updated should be isolated. The FBI also recommends auditing the network for systems using RDP and closing unused RDP ports. 2-factor authentication should be implemented as widely as possible and all RDP login attempts should be logged.
If there are reasons why Windows 7 devices cannot be updated and devices cannot be completely isolated, they should not be accessible over the internet and organizations should enroll in Microsoft’s ESU program.
The post FBI Urges Enterprises to Upgrade Windows 7 Devices to a Supported Operating System appeared first on HIPAA Journal.