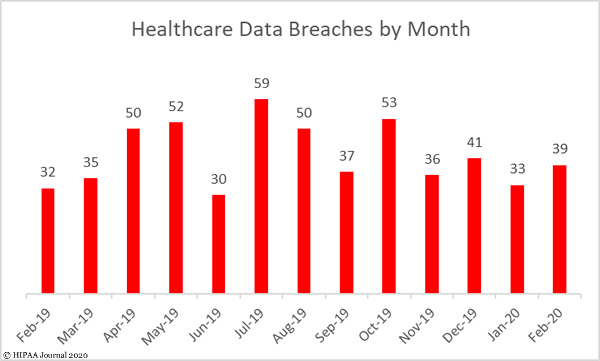
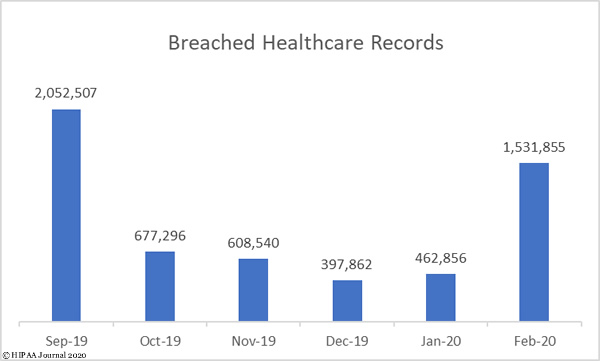
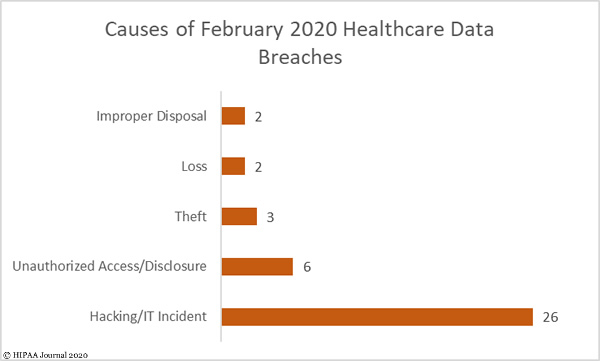
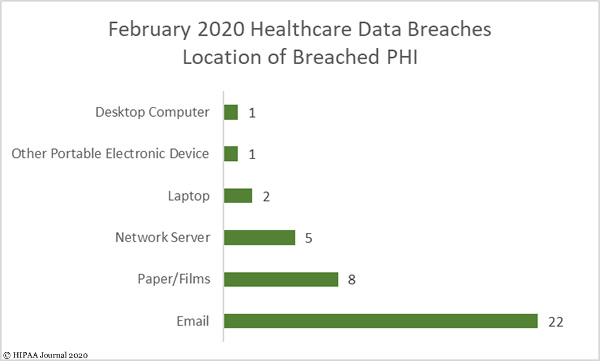
Teleconferencing platforms such as Zoom have proven popular with businesses and consumers for maintaining contact while working from home during the COVID-19 crisis, but a slew of Zoom security problems have been identified in the past few days that have raised concerns about the suitability of the platform for medical use.
Zoom Security Problems Uncovered by Researchers
Several Zoom security problems and privacy issues have been discovered in the past few days. The macOS installer was discovered to use malware-like methods to install the Zoom client without final confirmation being provided by users. This method could potentially be hijacked and could serve as a backdoor for malware delivery.
Two zero-day vulnerabilities were identified in the macOS client version of Zoom’s teleconferencing platform, which would allow a local user to escalate privileges and gain root privileges, even without an administrator password, and gain access to the webcam and microphone and intercept and record Zoom meetings.
A feature of the platform that is intended to make it easier for business users to find other individuals within the company was discovered to be leaking users’ email addresses, profile photos, and statuses. The Company Directory feature adds other people to a user’s contact list if their email address in on the same domain. Several consumers reported that strangers had been added to their contact lists when they signed up with a personal email address.
There have also been many reported cases of Zoom-bombing, which is where uninvited individuals join meetings using brute force tactics to guess meeting IDs. The FBI recently published a warning following a rise in hijacking attacks. There have been cases of people hacking Zoom meetings, abusing participants, and using the screen sharing feature to display pornography.
There have also been revelations that Zoom has been sharing background data on users with Facebook via the Facebook SDK, even when users do not have Facebook accounts.
Zoom Platform Does Not Offer End-to-End Encryption
A report published in The Intercept revealed the end-to-end encryption that Zoom claims to implement does not extend to video meetings. When The Intercept contacted Zoom for comment, a spokesperson for the company explained that “Currently, it is not possible to enable E2E encryption for Zoom video meetings.” Instead, “Zoom video meetings use a combination of TCP and UDP. TCP connections are made using TLS and UDP connections are encrypted with AES using a key negotiated over a TLS connection.”
The method of encrypting data is similar to that used to secure communications between a web browser and an HTTPS website. This “transport encryption” protects data in transit from one client to the other and means that communications between meeting participants is encrypted, but Zoom has access to unencrypted audio and video content.
Zoom explained to The Intercept that while unencrypted users’ data can be accessed, “Zoom has layered safeguards in place to protect our users’ privacy, which includes preventing anyone, including Zoom employees, from directly accessing any data that users share during meetings, including—but not limited to—the video, audio and chat content of those meetings. Importantly, Zoom does not mine user data or sell user data of any kind to anyone.”
Answers Sought About Recently Disclosed Zoom Security Problems
Sen. Richard Blumenthal (D-Conn) has written to Zoom CEO and founder Eric S. Yuan seeking answers about the company’s response to the massive increase in users, the growing list of Zoom security problems, and Zoom’s handling of personal user data.
In December 2019, there were around 10 million Zoom meeting participants every day. In March 2020, the number had expanded to an astonishing 200 million a day. The company has been working to continue to provide support for users to ensure there is an uninterrupted service, but the massive increase in consumers using a platform that was designed for business users has been a challenge.
“Zoom is increasingly being used by schools and healthcare providers that have shut down or limited their operations to stop the spread of Coronavirus, raising questions about how its services comply with federal and state privacy laws protecting students, patients, and consumers,” wrote Sen. Blumenthal in the letter.
Sen. Blumenthal also expressed concern about Zoom’s “troubling history of software design practices and security lapses,” referencing the slow response to the vulnerability in the Mac client, which was not fully addressed and took months before it was finally resolved, and then only due to the intervention of Apple.
Sen. Blumenthal seeks answers about the steps being taken to detect and stop Zoom-bombing, the level of encryption used to protect users’ privacy, and the data that is collected, used, and shared with third parties such as Facebook.
New York Attorney General Letitia James is also concerned about the recent Zoom security problems and the company’s response to the massive increase in users. In the letter, Attorney General James expressed concern that the existing security practices at Zoom may no longer be sufficient given the sudden surge in the number of users and the sensitivity of data that is now passing through the platform. She also wants to know whether a broader review of Zoom security practices has been undertaken considering the massive increase in popularity.
CEO Responds to Criticism of Zoom Security Problems
In an April 1, 2020 blog post, Zoom CEO Eric S. Yuan explained that the company is experiencing some growing pains as a result of the massive rise in popularity of the platform this year. In response to criticism of Zoom security problems, Yuan said, “we recognize that we have fallen short of the community’s – and our own – privacy and security expectations. For that, I am deeply sorry, and I want to share what we are doing about it.”
The massive rise in popularity of the platform was not anticipated, neither having a quarter of the world’s population in lockdown and working and socializing from home. “We now have a much broader set of users who are utilizing our product in a myriad of unexpected ways, presenting us with challenges we did not anticipate when the platform was conceived,” said Yuan.
It should be noted that all software solutions have vulnerabilities and some of the recently disclosed Zoom vulnerabilities have been made public without giving Zoom much time to respond and fix the issues. Zoom has responded quickly and addressed some of the issues that have come to light in recent days, although several privacy and security issues remain.
Zoom has publicly committed to fix privacy and security issues and proactively assess the platform for other vulnerabilities. Over the next 90 days, Zoom will cease all regular development work and will shift all engineering resources to focus on the biggest trust, safety, and privacy issues. The bug bounty program is being enhanced and penetration tests are being conducted to assess the security of the platform.
Use of Zoom for Healthcare Communications
Enterprise-class communication solutions require enterprise-grade privacy and security protections. This is especially important in healthcare to ensure HIPAA compliance. Zoom offers an enterprise package for healthcare organizations – Zoom for Healthcare – which has been developed to incorporate the necessary safeguards to comply with the HIPAA Privacy and Security Rules; however, the latest security vulnerabilities and privacy issues cast doubt on the level of protection provided.
During the COVID-19 public health emergency, the HHS’ Office for Civil Rights has stated it will be exercising enforcement discretion and will not impose sanctions or penalties for the good faith provision of telehealth services and that applications that may not satisfy all requirements of HIPAA Rules can be used. While there is nothing to suggest OCR would make an exception for Zoom – it is not a public-facing platform – healthcare providers should exercise caution.
There are other teleconferencing solutions available for use by healthcare organizations for the provision of telehealth services, many of which do offer true end-to-end encryption and do not have the security issues that have been uncovered in Zoom. Many of those solutions are also available free of charge, and even the HIPAA-compliant secure messaging platform provider, TigerConnect, has made its platform available to healthcare organizations free of charge following the declaration of the COVID-19 public health emergency.
Since more secure videoconferencing and communications platforms are available, it is strongly advisable to use an alternative solution for telehealth and other healthcare communication during the COVID-19 crisis, and certainly until Zoom addresses its privacy and security issues and completes its platform review.
The post Zoom Security Problems Raise Concern About Suitability for Medical Use appeared first on HIPAA Journal.