In August, healthcare data breaches continued to be reported at a rate of more than 1.5 per day, which is around twice the average monthly breaches in 2018 (29.5 per month). This is the second successive month when breaches have been reported at such an elevated level. While the number of breaches has not changed much since last month (49 compared to 50), there has been a substantial reduction in the number of exposed records.
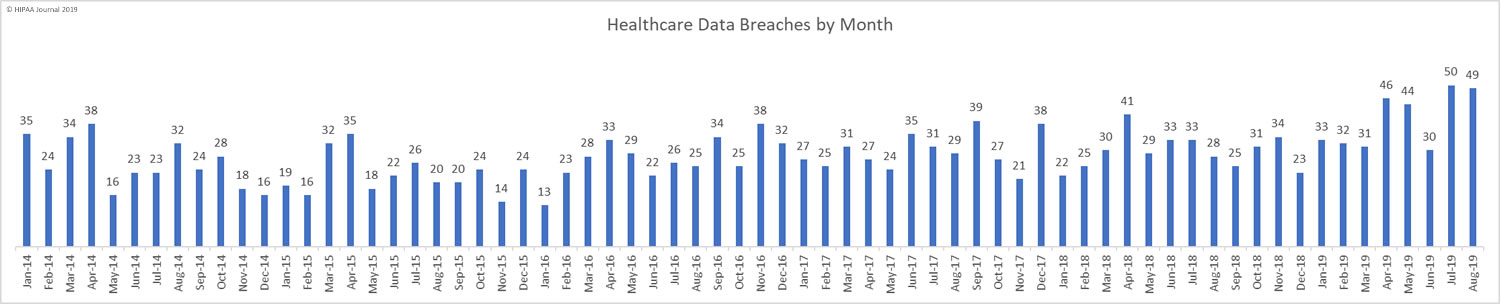
August saw 729,975 healthcare records breached compared to 25,375,729 records in July, 3,452,442 records in June, and 1,988,376 records in May. The exceptionally high breach total for July was mostly due to the massive data breach at American Medical Collection Agency (See below for an update on the AMCA breach total).
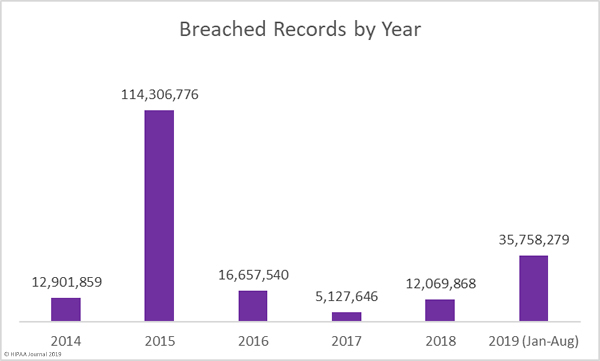
Causes of August 2019 Healthcare Data Breaches
Hacking and other IT incidents dominated the breach reports in August. 32 breaches were attributed to hacking/IT incidents, which is almost double the number of breaches from all other causes. Hacking/IT incidents breached 602,663 healthcare records – 82.56% of all records breached in August. The average breach size was 18,833 records and the median breach size was 5,248 records.
There were 12 unauthorized access/disclosure incidents reported in August which breached 77,316 healthcare records. Those incidents breached an average of 6,443 records and the mean breach size was 1,281 records. There were 3 loss incidents and 2 theft incidents. The theft incidents saw 17,650 records potentially compromised and 32,346 records were exposed due to the loss of paperwork or electronic devices. The mean loss breach size was 10,782 records and the mean theft breach size was 8,825 records.
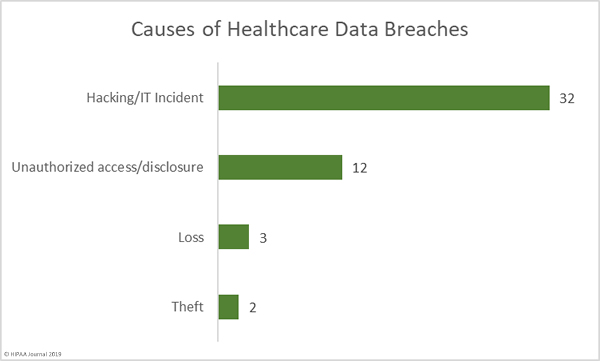
Location of Breached PHI
Phishing continues to pose serious problems for healthcare organizations. Out of the 49 reported breaches, 46.94% – 23 breaches – involved PHI stored in email accounts. The majority of those email breaches were due to phishing attacks.
There were 9 breaches reported that involved PHI stored on network servers, several of which involved ransomware. There were 7 breaches involving paper records/films, highlighting the need for enhanced physical security and administrative controls.
Four breaches involved portable electronic devices such as zip drives and laptop computers. These types of breaches have reduced considerably in recent years largely through the use of encryption, which should be implemented on all portable electronic devices used to store ePHI.
Defending against phishing attacks is a major challenge, and one that can only be solved through layered defenses and staff training. Technological solutions such as spam filters, web filters, firewall rules, multi-factor authentication, and DMARC should be implemented to block phishing attempts, but the sophisticated nature of many phishing campaigns means even layered defenses may be bypassed. End user training is therefore essential. Employees must be trained how to recognize email threats and conditioned how to respond when suspicious emails land in their inboxes.
An annual training session may have been sufficient to provide protection a few years ago, but the increased number of attacks and diverse nature of email threats means a single annual training session is no longer enough. Annual classroom-based training sessions should be augmented with more regular refresher training sessions, cybersecurity bulletins, and email alerts about new threats to watch out for. Phishing simulation exercises are also very beneficial for helping identify individuals who require further training and to find out how effective training has been at reducing susceptibility to phishing attacks.
Largest Healthcare Data Breaches in August 2019
Listed below are the top ten healthcare data breaches reported in August 2019. The largest breach of the month was a phishing attack on Presbyterian Healthcare Services, which saw 183,370 healthcare records breached. The Conway Regional Health System, NorthStar Anesthesia, and Source 1 Healthcare Solutions breaches were also due to phishing attacks.
The Wisconsin Diagnostic Laboratories breach, which affected 114,985 individuals, the 33,370-record breach at Mount Sinai Hospital, and the 29,644-record breach at Integrated Regional Laboratories were all due to the hacking of business associate AMCA.
The breach at Grays Harbor Community Hospital was due to a ransomware attack and the Renown Health breach was due to the loss of a portable storage device. The cause of the breach at Timothee T. Wilkin, D.O. has not been confirmed.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| Presbyterian Healthcare Services |
Healthcare Provider |
183370 |
Hacking/IT Incident |
| Wisconsin Diagnostic Laboratories |
Healthcare Provider |
114985 |
Hacking/IT Incident |
| Grays Harbor Community Hospital |
Healthcare Provider |
88399 |
Hacking/IT Incident |
| Conway Regional Health System |
Healthcare Provider |
37000 |
Unauthorized Access/Disclosure |
| Mount Sinai Hospital |
Healthcare Provider |
33730 |
Hacking/IT Incident |
| Integrated Regional Laboratories, LLC |
Healthcare Provider |
29644 |
Hacking/IT Incident |
| Renown Health |
Healthcare Provider |
27004 |
Loss |
| NorthStar Anesthesia, P.A. |
Healthcare Provider |
19807 |
Unauthorized Access/Disclosure |
| Source 1 Healthcare Solutions LLC |
Business Associate |
15450 |
Hacking/IT Incident |
| Timothee T. Wilkin, D.O. |
Healthcare Provider |
15113 |
Hacking/IT Incident |
August 2019 Healthcare Data Breaches by Covered Entity Type
42 of the month’s 49 data breaches were reported by healthcare providers and three incidents were reported by health plans. Business associates reported 4 breaches and a further 8 incidents had some business associate involvement.

August 2019 Healthcare Data Breaches by State
August’s healthcare data breaches affected entities based in 26 states. Texas was the worst affected with 5 reported breaches. 4 breaches were reported by entities based in Washington state, and three breaches were suffered by entities based in Arkansas, New York, and Pennsylvania.
California, Georgia, Illinois, Massachusetts, Minnesota, Missouri, New Mexico, Ohio, Oregon, and Wisconsin each experienced 2 breaches and one breach was reported by an entity based in each of Connecticut, Florida, Iowa, Kansas, Michigan, Nevada, New Jersey, Oklahoma, Rhode Island, Tennessee, and Virginia.
HIPAA Enforcement Activity in August 2019
There were no civil monetary penalties or settlements between the HHS and HIPAA-covered entities/business associates in August, and also no HIPAA-related enforcement activities by state attorneys general.
AMCA Data Breach Update
The AMCA data breach affected at least 24 healthcare organizations, 23 of which have now submitted breach reports to the Department of Health and Human Service’ Office for Civil Rights. The confirmed breach total currently stands at 26,043,743 records with a further 16,100 records expected to be added to that total. These breaches were mostly reported to OCR in July and August.
|
Healthcare Organization |
Confirmed Victim Count |
| 1 |
Quest Diagnostics/Optum360 |
11,500,000 |
| 2 |
LabCorp |
10,251,784 |
| 3 |
Clinical Pathology Associates |
1,733,836 |
| 4 |
Carecentrix |
467,621 |
| 5 |
Laboratories/Opko Health |
425,749 |
| 6 |
American Esoteric Laboratories |
409,789 |
| 7 |
Sunrise Medical Laboratories |
401,901 |
| 8 |
Inform Diagnostics |
173,617 |
| 9 |
CBLPath Inc. |
141,956 |
| 10 |
Laboratory Medicine Consultants |
140,590 |
| 11 |
Wisconsin Diagnostic Laboratories |
114,985 |
| 12 |
CompuNet Clinical Laboratories |
111,555 |
| 13 |
Austin Pathology Associates |
43,676 |
| 14 |
Mount Sinai Hospital |
33,730 |
| 15 |
Integrated Regional Laboratories |
29,644 |
| 16 |
Penobscot Community Health Center |
13,299 |
| 17 |
Pathology Solutions |
13,270 |
| 18 |
West Hills Hospital and Medical Center / United WestLabs |
10,650 |
| 19 |
Seacoast Pathology, Inc |
8,992 |
| 20 |
Arizona Dermatopathology |
5,903 |
| 21 |
Laboratory of Dermatology ADX, LLC |
4,082 |
| 22 |
Western Pathology Consultants |
4,079 |
| 23 |
Natera |
3,035 |
| 24 |
South Texas Dermatopathology LLC |
TBC (Est. 16,100) |
|
Total Records Breached |
26,043,743 |
The post August 2019 Healthcare Data Breach Report appeared first on HIPAA Journal.




