In April, more healthcare data breaches were reported than in any other month to date. The high level of data breaches has continued in May, with 44 data breaches reported. Those breaches resulted in the exposure of almost 2 million individuals’ protected health information.
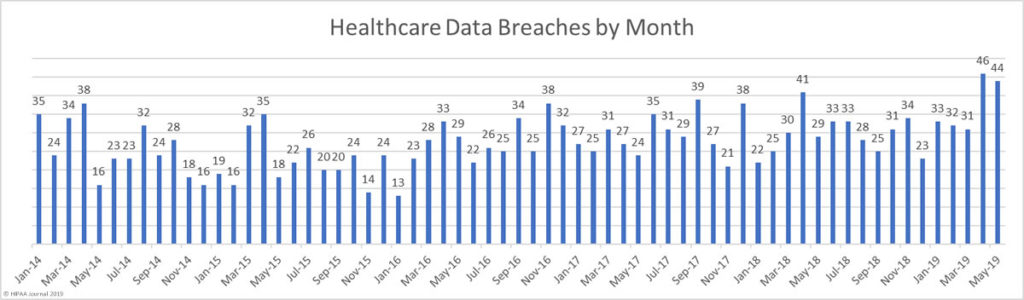
On average, 2018 saw 29.5 healthcare data breaches reported to the HHS’ Office for Civil Rights each month – a rate of more than one a day.
From January 2019 to May 2019, an average of 37.2 breaches have been reported each month. Up until May 31, 2019, 186 healthcare data breaches had been reported to OCR, which is more than half (52%) the number of breaches reported last year.
It remains to be seen whether the increase in data breaches is just a temporary blip or whether 40+ healthcare data breaches a month will become the new norm.
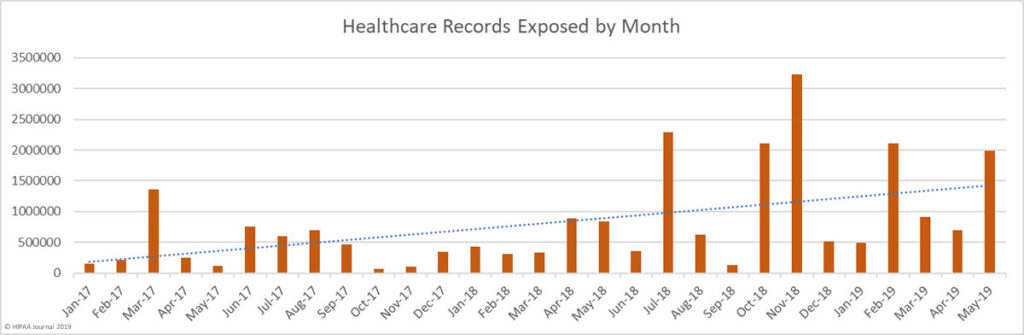
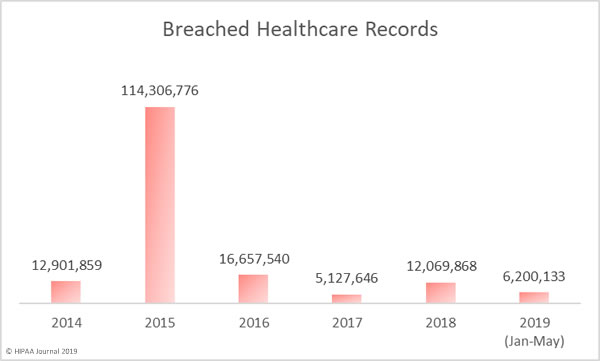
May saw a 186% increase in the number of exposed records compared to April. Across the 44 breaches, 1,988,376 healthcare records were exposed or compromised in May. So far this year, more than 6 million healthcare records have been exposed, which is more than half of the number of records exposed in 2018.
In terms of the number of records exposed, May would have been similar to April were it not for a massive data breach at the healthcare clearinghouse Inmediata Health Group. The breach was the largest of the year to date and resulted in the exposure of 1,565,338 records.
A web page which was supposed to only be accessible internally had been misconfigured and the page could be accessed by anyone over the internet.
| Rank |
Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| 1 |
Inmediata Health Group, Corp. |
Healthcare Clearing House |
1,565,338 |
Unauthorized Access/Disclosure |
| 2 |
Talley Medical Surgical Eyecare Associates, PC |
Healthcare Provider |
106,000 |
Unauthorized Access/Disclosure |
| 3 |
The Union Labor Life Insurance Company |
Health Plan |
87,400 |
Hacking/IT Incident |
| 4 |
Encompass Family and internal medicine group |
Healthcare Provider |
26,000 |
Unauthorized Access/Disclosure |
| 5 |
The Southeastern Council on Alcoholism and Drug Dependence |
Healthcare Provider |
25,148 |
Hacking/IT Incident |
| 6 |
Cancer Treatment Centers of America® (CTCA) at Southeastern Regional Medical Center |
Healthcare Provider |
16,819 |
Hacking/IT Incident |
| 7 |
Takai, Hoover, and Hsu, P.A. |
Healthcare Provider |
16,542 |
Unauthorized Access/Disclosure |
| 8 |
Hematology Oncology Associates, PC |
Healthcare Provider |
16,073 |
Hacking/IT Incident |
| 9 |
Acadia Montana Treatment Center |
Healthcare Provider |
14,794 |
Hacking/IT Incident |
| 10 |
American Baptist Homes of the Midwest |
Healthcare Provider |
10,993 |
Hacking/IT Incident |
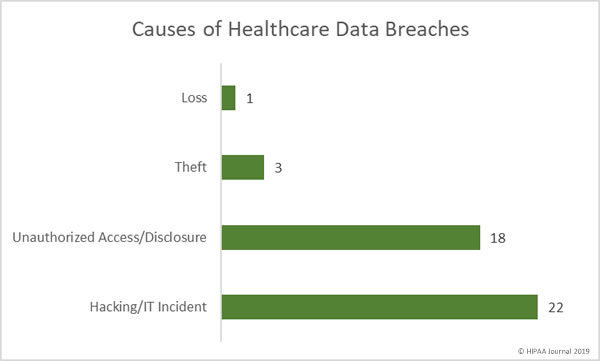
Causes of May 2019 Healthcare Data Breaches
Hacking/IT incidents were the most numerous in May with 22 reported incidents. In total, 225,671 records were compromised in those breaches. The average breach size was 10,258 records with a median of 4,375 records.
There were 18 unauthorized access/disclosure incidents in May, which resulted in the exposure of 1,752,188 healthcare records. The average breach size was 97,344 records and the median size was 2,418 records.
8,624 records were stolen in three theft incidents. The average breach size 2,875 records and the median size was 3,578 records. There was one loss incident involving 1,893 records.
Location of Breached PHI
Email continues to be the most common location of breached PHI. 50% of the month’s breaches involved at least some PHI stored in email accounts. The main cause of these types of breaches is phishing attacks.
Network servers were the second most common location of PHI. They were involved in 11 breaches, which included hacks, malware infections and ransomware attacks. Electronic medical records were involved in 7 breaches, most of which were unauthorized access/disclosure breaches.

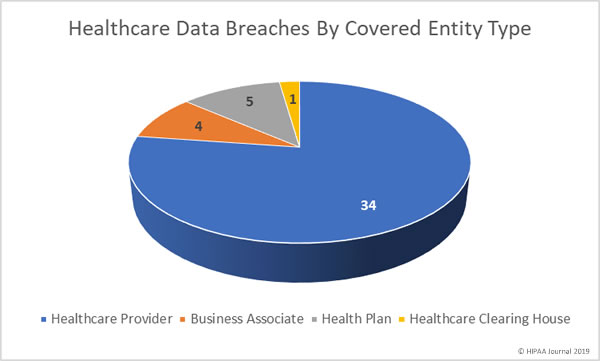
May 2019 Healthcare Data Breaches by Covered Entity Type
Healthcare providers were the worst affected covered entity type in May with 34 breaches. 5 breaches were reported by health plans and 4 breaches were reported by business associates of HIPAA-covered entities. A further two breaches had some business associate involvement. One breach involved a healthcare clearinghouse.
May 2019 Healthcare Data Breaches by State
May saw healthcare data breaches reported by entities in 17 states. Texas was the worst affected state in May with 7 reported breaches. There were 4 breaches reported by covered entities and business associates in California and 3 breaches were reported in each of Indiana and New York.
2 breaches were reported by entities base in Connecticut, Florida, Georgia, Maryland, Minnesota, North Carolina, Ohio, Oregon, Washington, and Puerto Rico. One breach was reported in each of Colorado, Illinois, Kentucky, Michigan, Missouri, Montana, and Pennsylvania.
HIPAA Enforcement Actions in May 2019
OCR agreed two settlements with HIPAA covered entities in May and closed the month with fines totaling $3,100,000.
Touchstone Medical Imaging agreed to settle its HIPAA violation case for $3,000,000. The Franklin, TN-based diagnostic medical imaging services company was investigated after it was discovered that an FTP server was accessible over the internet in 2014.
The settlement resolves 8 alleged HIPAA violations including the lack of a BAA, insufficient access rights, a risk analysis failure, the failure to respond to a security incident, a breach notification failure, a media notification failure, and the impermissible disclosure of the PHI of 307,839 individuals.
Medical Informatics Engineering settled its case with OCR and agreed to pay a financial penalty of $100,000 to resolve alleged HIPAA violations uncovered during the investigation of its 2015 breach of 3.5 million patient records. Hackers had gained access to MIE servers for 19 days in May 2015.
OCR determined there had been a failure to conduct a comprehensive risk analysis and, as a result of that failure, there was an impermissible disclosure of 3.5 million individuals’ PHI.
It did not end there for MIE. MIE also settled a multi-state lawsuit filed by 16 state attorneys general. A multi-state investigation uncovered several HIPAA violations. MIE agreed to pay a penalty of $900,000 to resolve the case.
The post May 2019 Healthcare Data Breach Report appeared first on HIPAA Journal.





