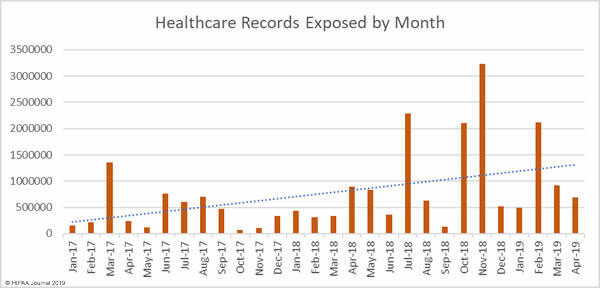
April was the worst ever month for healthcare data breaches. More data breaches reported than any other month since the Department of Health and Human Services’ Office for Civil Rights started publishing healthcare data breach reports in October 2009. In April, 46 healthcare data breaches were reported, which is a 48% increase from March and 67% higher than the average number of monthly breaches over the past 6 years.
While breach numbers are up, the number of compromised healthcare records is down. In April 2019, 694,710 healthcare records were breached – A 23.9% reduction from March. While the breaches were smaller in March, the increase in breaches is of great concern, especially the rise in the number of healthcare phishing attacks.
Largest Healthcare Data Breaches in April 2019
Two 100,000+ record data breaches were reported in April. The largest breach of the month was reported by the business associate Doctors Management Services – A ransomware attack that exposed the records of 206,695 patients.
The ransomware was deployed 7 months after the attacker had first gained access to its systems. The initial access was gained via Remote Desktop Protocol (RDP) on a workstation.
The second largest data breach was reported by the healthcare provider Centrelake Medical Group. The breach resulted in the exposure of 197,661 patients’ PHI and was also a ransomware attack that prevented patient information from being accessed. While the delay between access to the servers being gained and the ransomware being deployed was not as long, it also appeared that the attacker had been exploring the network prior to deploying the malicious software. Access to the server was gained 6 weeks prior to the ransomware being deployed. Ransomware was also used in the attack on ActivYouth Orthopaedics.
| Covered Entity | Entity Type | Records Exposed | Breach Type | Location of Breached PHI |
| Doctors Management Services, Inc. | Business Associate | 206695 | Hacking/IT Incident | Network Server |
| Centrelake Medical Group, Inc. | Healthcare Provider | 197661 | Hacking/IT Incident | Network Server |
| Gulf Coast Pain Consultants, LLC d/b/a Clearway Pain Solutions Institute | Healthcare Provider | 35000 | Unauthorized Access/Disclosure | Electronic Medical Record |
| EmCare, Inc. | Healthcare Provider | 31236 | Hacking/IT Incident | |
| Kim P. Kornegay, DMD | Healthcare Provider | 27000 | Theft | Desktop Computer, Electronic Medical Record, Paper/Films |
| Pediatric Orthopedic Specialties, PA, dba ActivYouth Orthopaedics | Healthcare Provider | 24176 | Hacking/IT Incident | Network Server |
| Health Recovery Services, Inc. | Healthcare Provider | 20485 | Unauthorized Access/Disclosure | Network Server |
| Baystate Health | Healthcare Provider | 11658 | Hacking/IT Incident | |
| Riverplace Counseling Center, Inc. | Healthcare Provider | 11639 | Hacking/IT Incident | Network Server |
| Minnesota Department of Human Services | Healthcare Provider | 10263 | Hacking/IT Incident |
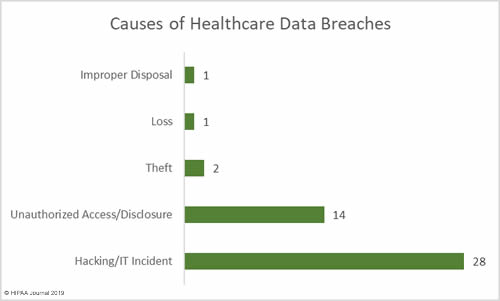
Causes of April 2019 Healthcare Data Breaches
Hacking/IT incidents outnumbered unauthorized access/disclosure incidents by 2 to 1 in April. 28 of the reported breaches of 500 or more records were due to hacking/IT incidents. There were 14 unauthorized access/disclosure incidents, two cases of theft of PHI, one reported case of loss of paperwork, and one case of improper disposal of PHI.
While 2018 saw a decline in the number of ransomware attacks across all industry sectors, the number of ransomware attacks is increasing once again, and healthcare is the most attacked industry. Remote Desktop Protocol often exploited to gain access to servers and workstations to deploy ransomware.
In May, a Forescout study revealed that the use of vulnerable protocols is common in the healthcare industry. Risk can be reduced by disabling these protocols, and if RDP must be used, to only use RDP with a VPN.
Phishing attacks also increased considerably in April, which highlights just how vulnerable healthcare organizations are to this type of attack. Advanced anti-phishing and anti-spam solutions can reduce the volume of malicious emails that reach inboxes and combined with regular security awareness training, risk can be reduced.
The use of multi-factor authentication is also important. In the event of credentials being compromised, MFA will prevent those credentials from being used to gain access to PHI. MFA is not infallible, but it can ensure risk is reduced to a reasonable and acceptable level. According to Verizon, most credential theft incidents would not have resulted in a data breach if MFA been implemented.
Hacking/IT incidents resulted in the highest number of compromised records in April 2019 – 384,219 records or 55% of all compromised records in April. The mean breach size was 13,722 records and the median breach size was 4,008 records.
Unauthorized access/disclosure incidents resulted in the exposure of 264,016 records or 38% of the month’s total. While hacking incidents usually result in more records being compromised, these incidents were more severe and had a mean breach size of 18,858 records. The median breach size was 3,193 records.
31,810 records were exposed to loss or theft – 4.6% of the month’s total. The mean breach size was 10,603 records and the median breach size was 4,000 records.
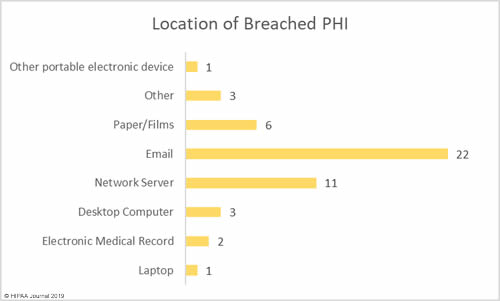
Location of Breached Protected Health Information
Email was the most common location of breached PHI in April. Email was involved in 22 data breaches – 47.8% of all breaches in April 2019. While this category includes misdirected emails, the majority of email breaches were due to phishing attacks.
Network servers were involved in 11 breaches – 23.9% of the month’s breaches – which include malware and ransomware attacks.
Physical records such as paperwork, charts, and films were involved in 6 breaches – 13% of the month’s total.
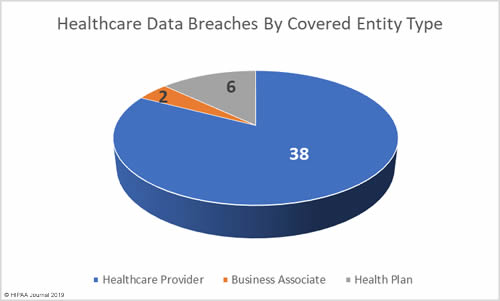
April Breaches by Covered Entity Type
April was a relatively good month for business associates of covered entities with only two breaches reported and one further breach having some business associate involvement, although a business associate breach was the largest breach of the month.
6 health plans reported breaches in April and the remaining 38 breaches were reported by healthcare providers.
April 2019 Healthcare Data Breaches by State
Data breaches were reported by entities based in 21 states in April. California and Texas were the worst affected, with each state having 5 breaches. Florida, Minnesota, and Ohio each had four breaches, and there were 3 breaches reported by entities in Illinois.
Idaho, Massachusetts, New York, Oregon, Tennessee, and Washington each had 2 breaches and one breach was reported in each of Alabama, Delaware, Louisiana, North Carolina, New Jersey, Pennsylvania, South Dakota, Utah, and West Virginia.
HIPAA Enforcement Activity in April 2019
There were no financial penalties issued by the HHS’ Office for Civil Rights or state Attorneys General in 2019. The first OCR financial penalty of 2019 was issued in May – A $3,000,000 penalty for Touchstone Medical Imaging for the delayed response to a data breach in which the records of 307,839 patients were exposed.
In addition to the delayed response, there was a failure to issue breach notifications in a reasonable time frame, a failure to notify the media about the breach, two BAAs failures, insufficient access rights, and a risk analysis failure.
The post April 2019 Healthcare Data Breach Report appeared first on HIPAA Journal.